Raspberry Pi Firewall Command Line Configuration Step-by-Step

Raspberry Pi OS is an extremely popular self-hosting platform many use for running services. Let’s set the tone for Raspberry Pi firewall configuration via the command line and see what we will learn.
What: A step-by-step how-to guide for UFW (Uncomplicated Firewall) on your Raspberry Pi
Where: You can use this on native Raspberry Pi devices or other platforms like virtual machines running on Raspberry Pi OS
Why:
Security: Better security for your Raspberry Pi to control network traffic
Control: Configure incoming and outgoing traffic to control who can connect to what
Optimization: Filter out unneeded or port scanning from attackers
How: Using UFW, along with understanding its core features and best practices
Raspberry Pi firewall contents
- Introduction to UFW firewall
- Installing UFW on Raspberry Pi OS and verifying with sudo ufw status
- Application profiles
- Basic Configuration and Enabling UFW Firewall Rules using sudo ufw
- Adding Firewall Rules for incoming traffic
- Monitoring and Adjusting UFW Rules
- Advanced UFW Features
- How to disable UFW firewall
- Permanently Disabling UFW using systemctl
- Troubleshooting Raspberry Pi Firewall
- Key Takeaways
Introduction to UFW firewall
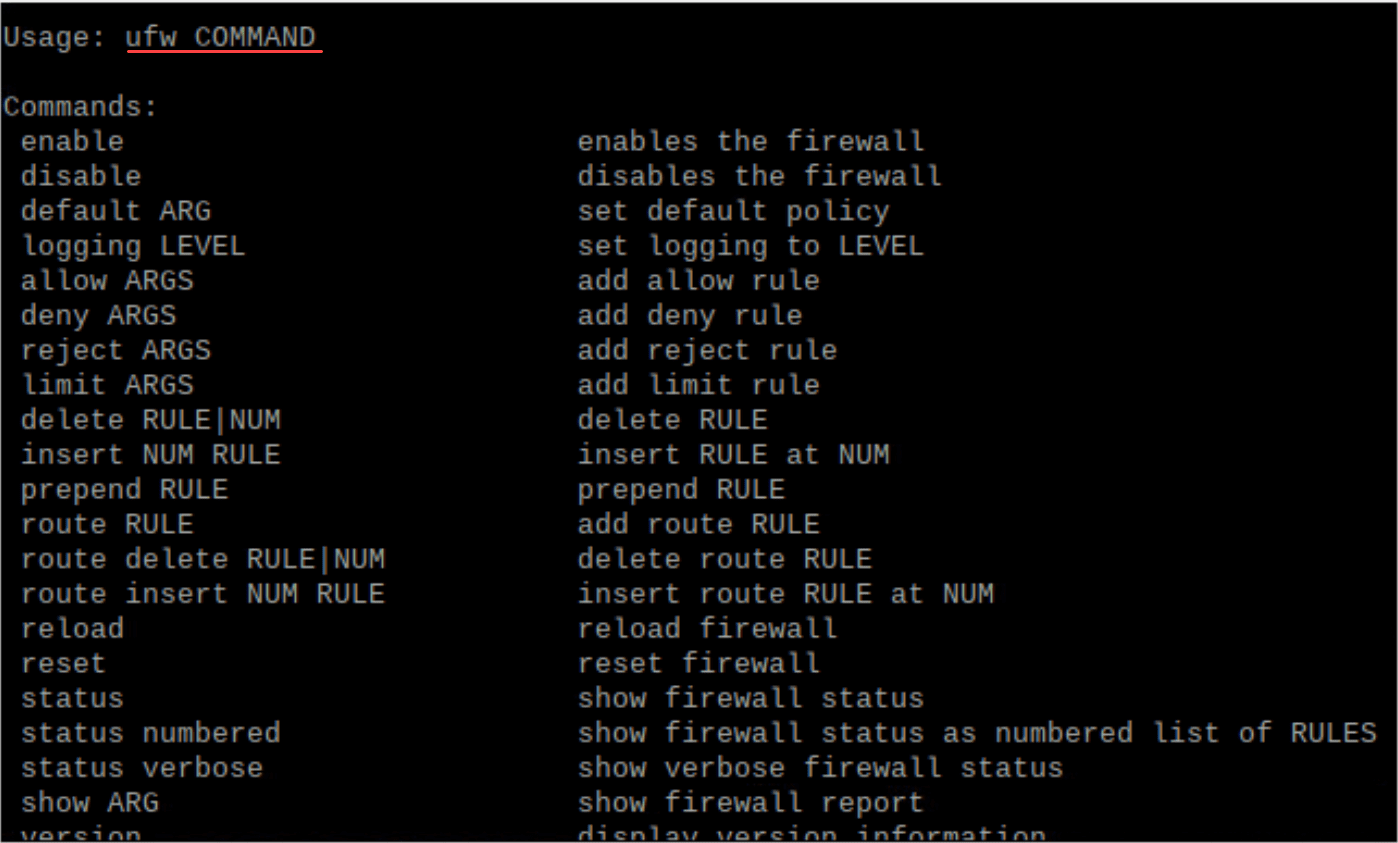
UFW firewall, which stands for Uncomplicated Firewall, is a user-friendly interface for managing iptables, the default tool for setting up firewalls on Linux kernel systems.
UFW provides a simpler way to configure the firewall on Linux systems, especially for those not well-versed in the intricacies of IPtables, and is an easy firewall on Raspberry Pi OS, which is a Debian-based operating system.
Note the different command line parameters in the screenshot below:
Installing UFW on Raspberry Pi OS and verifying with sudo ufw status
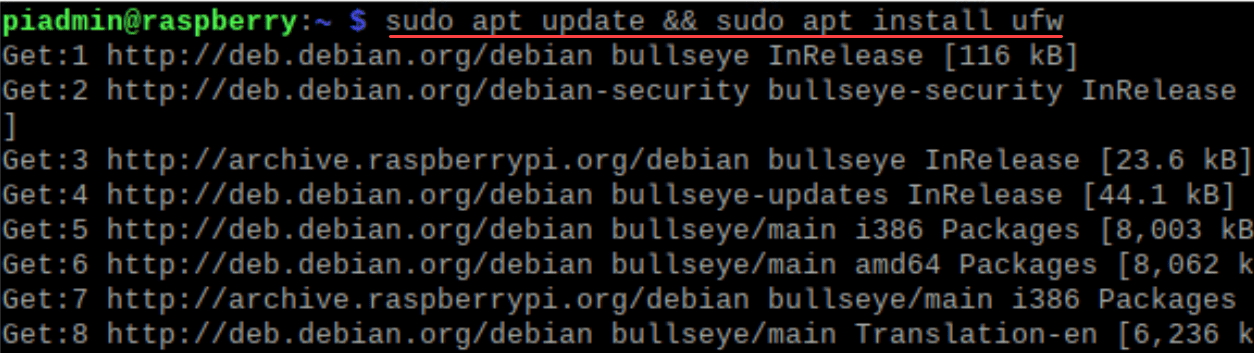
Before we can configure the Raspberry Pi firewall, we need to ensure it is installed. In Raspberry Pi OS, the installation of the ufw package is simple using the following command:
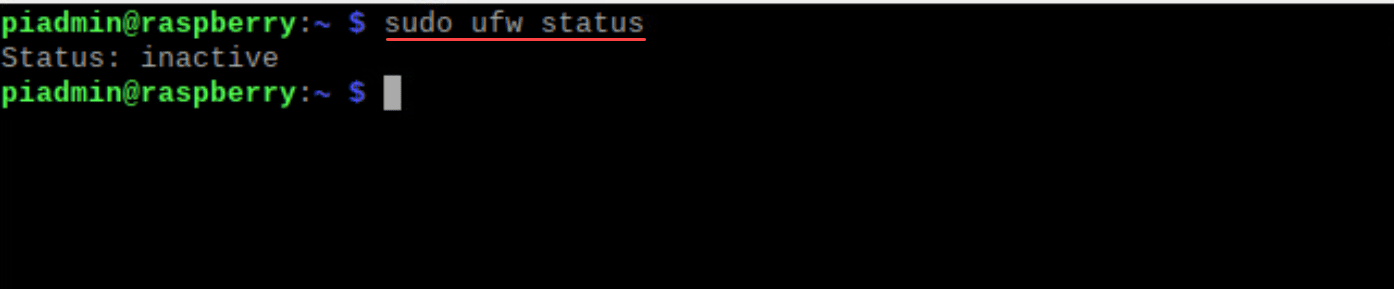
sudo apt update && sudo apt install ufwAfter installation, ensure UFW is inactive:
sudo ufw statusThe output should be “inactive”, indicating that UFW isn’t yet regulating your network traffic.
Application profiles
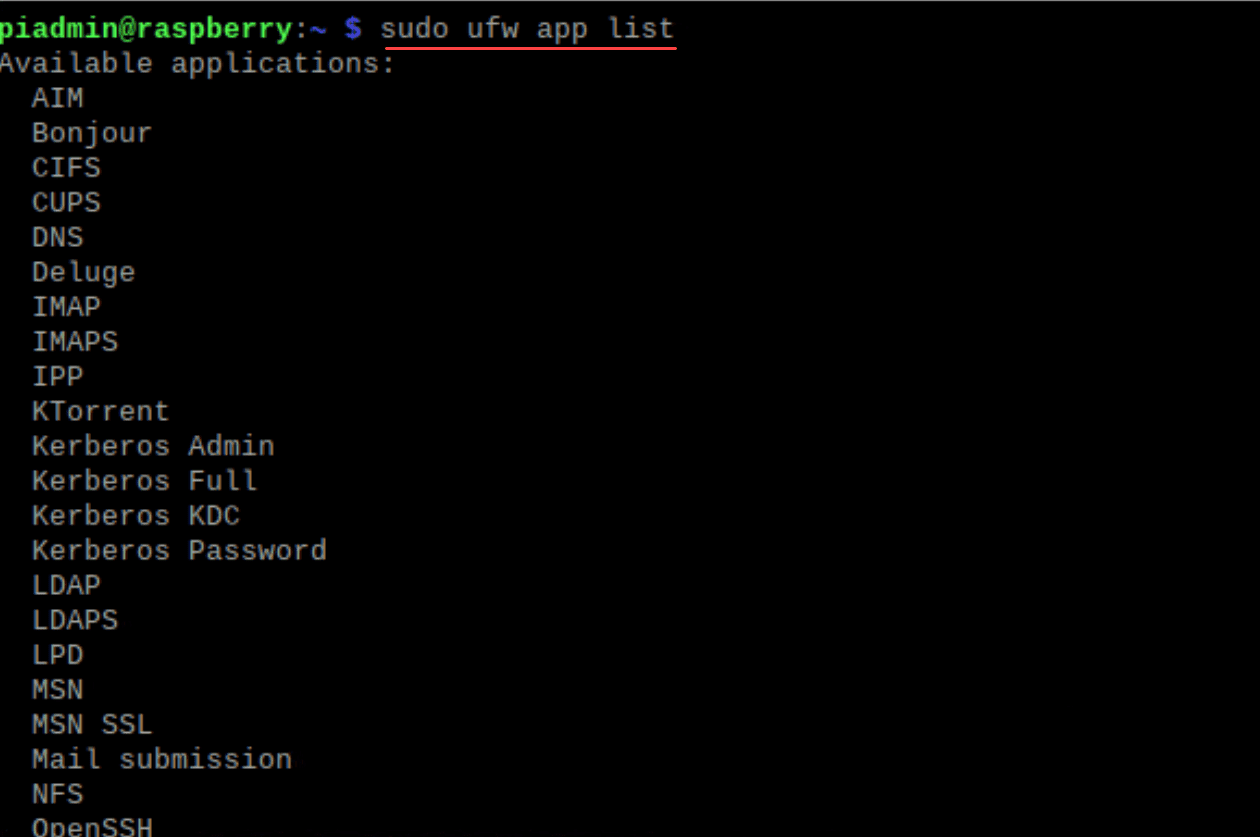
The UFW comes with application profiles that alow you to have a friendly and easy way to add firewall entries for default behavior of apps without having to know specific ports and protocols. If you want to see the default list of application profiles, you can use the command:
sudo ufw app listNow, you can use these apps in the list to add specific rules to your Raspberry Pi firewall entries.
Basic Configuration and Enabling UFW Firewall Rules using sudo ufw
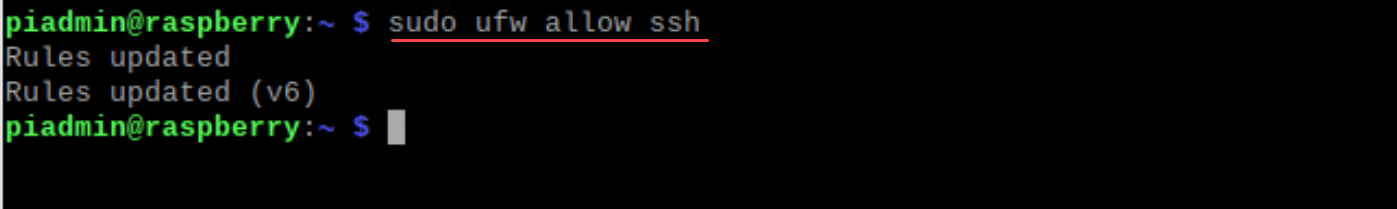
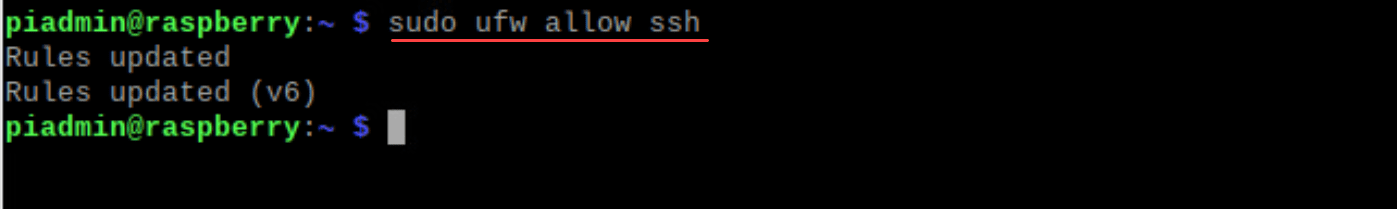
Once installed, the firewall needs to be properly set up to balance accessibility and protection. Before enabling UFW, make sure it’s properly configured to prevent disrupting existing ssh connections. To allow SSH and not disrupt existing SSH connections you may have, you can configure the following firewall rule for the SSH port.
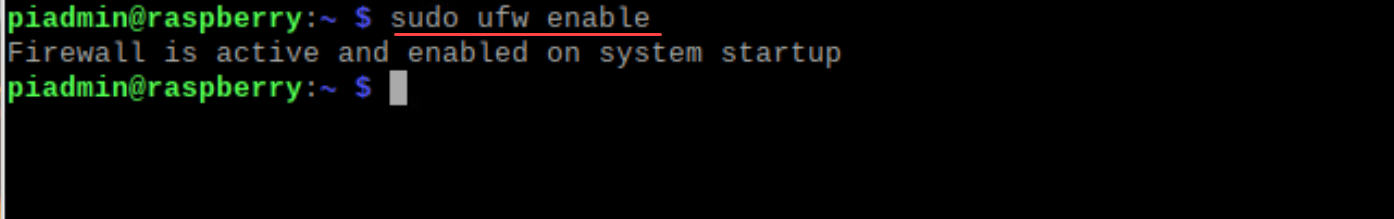
sudo ufw allow sshNow, with SSH access secured, enable UFW:
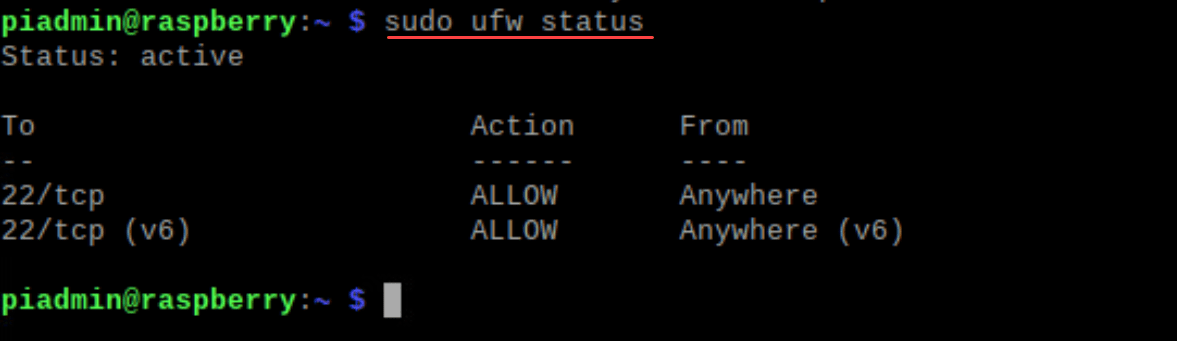
sudo ufw enableAfter this command, your Raspberry Pi firewall will become active. You can always check the status using:
sudo ufw statusAdding Firewall Rules for incoming traffic
Crafting firewall rules is at the heart of a firewall’s functionality. Here’s how to set basic rules:
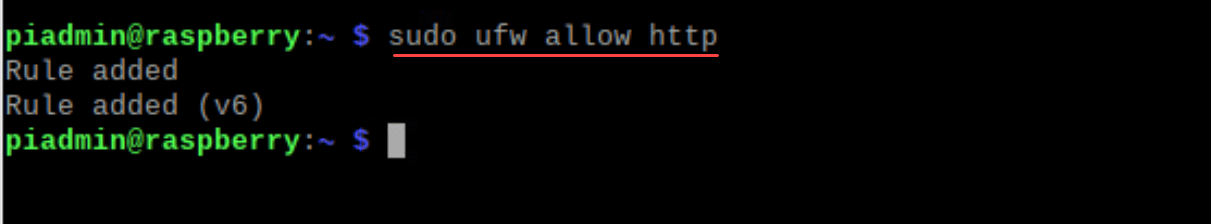
To allow HTTP traffic:
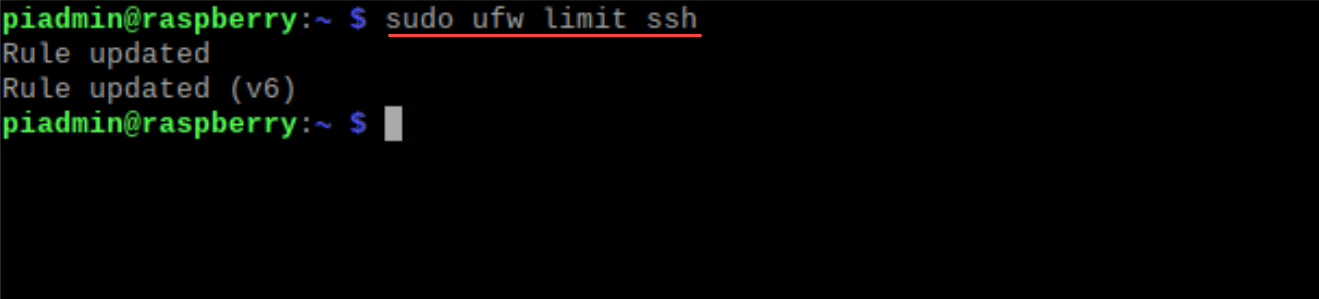
sudo ufw allow httpYou can limit connections using SSH, which is useful against brute force attacks:
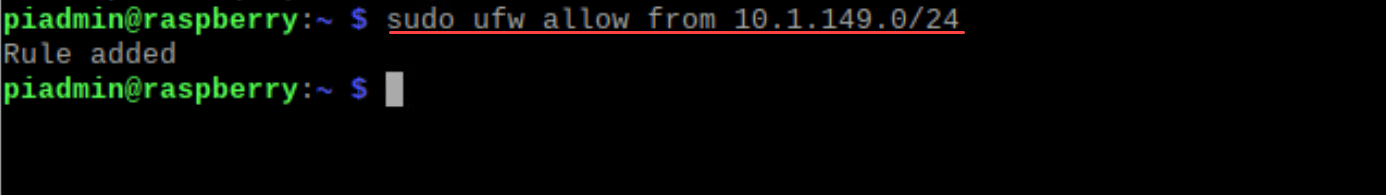
sudo ufw limit sshTo specify rules for a particular IP address, you can use the following command. Here, we are allowing access for a subnet.
sudo ufw allow from [specific ip]Monitoring and Adjusting UFW Rules
Keeping an eye on all the rules ensures your firewall remains robust and efficient.
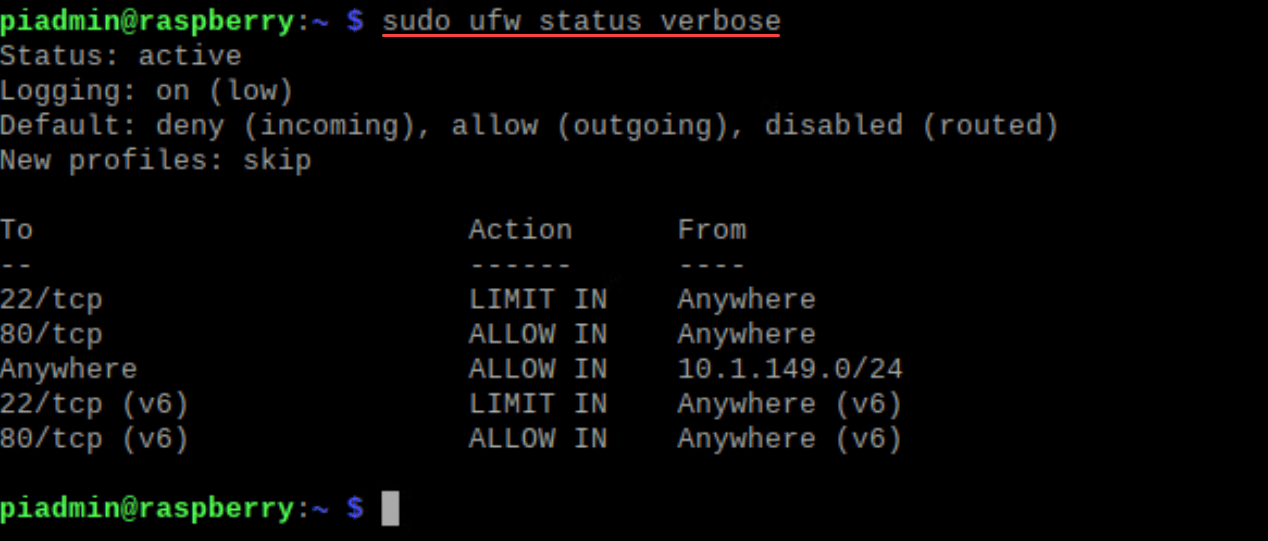
For a detailed view:
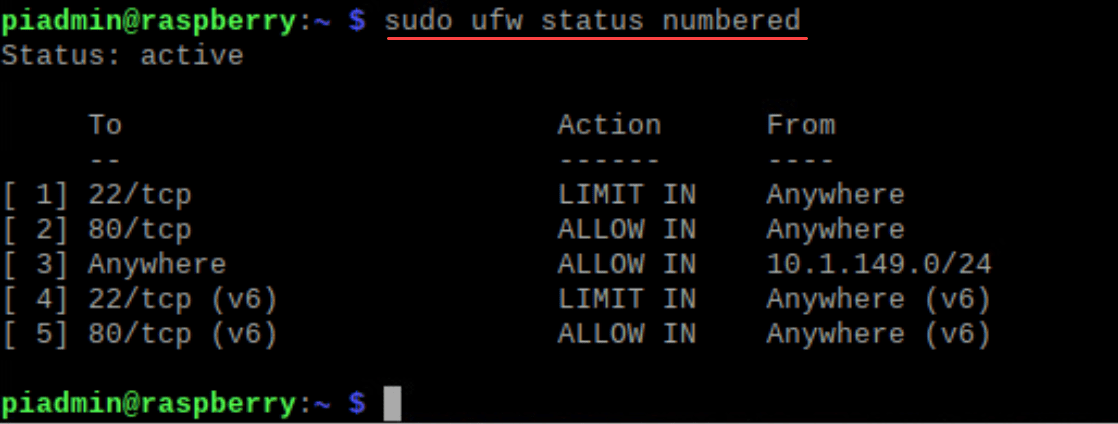
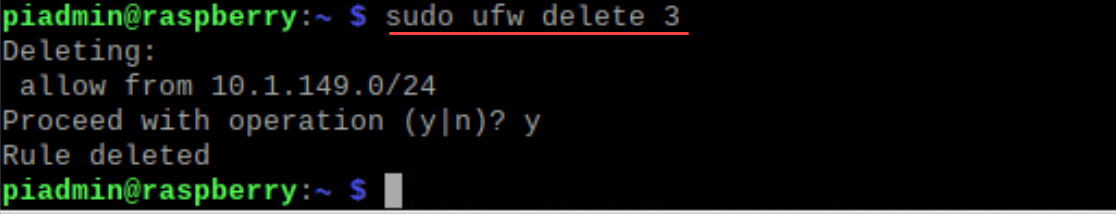
sudo ufw status verboseIf a rule needs removal, first list them with numbers:
sudo ufw status numberedThen, to delete a rule:
sudo ufw delete [rule number]Advanced UFW Features
The Uncomplicated Firewall goes beyond basic rule settings. Some advanced features can optimize your Raspberry Pi’s security system further:
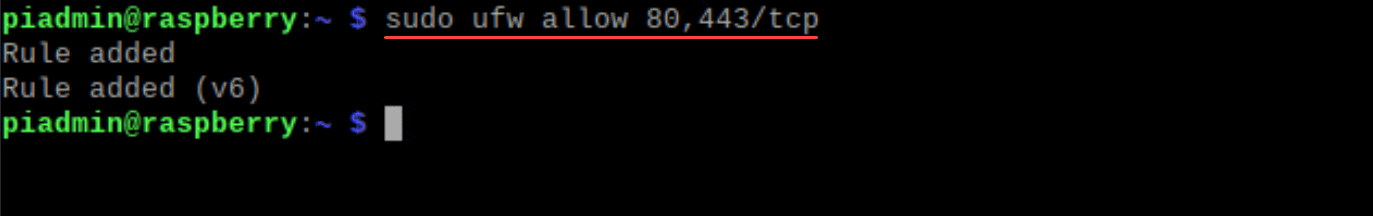
If you’re running a web server, you can specify which ports to open:
sudo ufw allow 80,443/tcpFor more granular control, setting default policies is crucial:
sudo ufw default deny incoming sudo ufw default allow outgoingThis ensures only outbound traffic is allowed by default, protecting your Raspberry Pi from unsolicited incoming connections.
The Virtual Private Network (VPN) Consideration
Integrating a VPN with your Raspberry Pi can further encrypt and secure your internet connection. When setting up UFW, it’s important to ensure VPN ports, such as the commonly used port 1194 for OpenVPN, are open.
How to disable UFW firewall
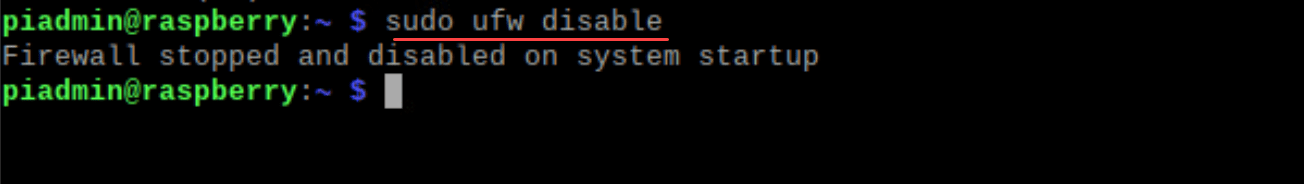
You may want to permanently turn off your UFW firewall. Let’s look at a few ways to do this. If you want to turn off the firewall and disable it the next time you boot up your Raspberry Pi, follow these steps:
Open the command line and enter the following command:
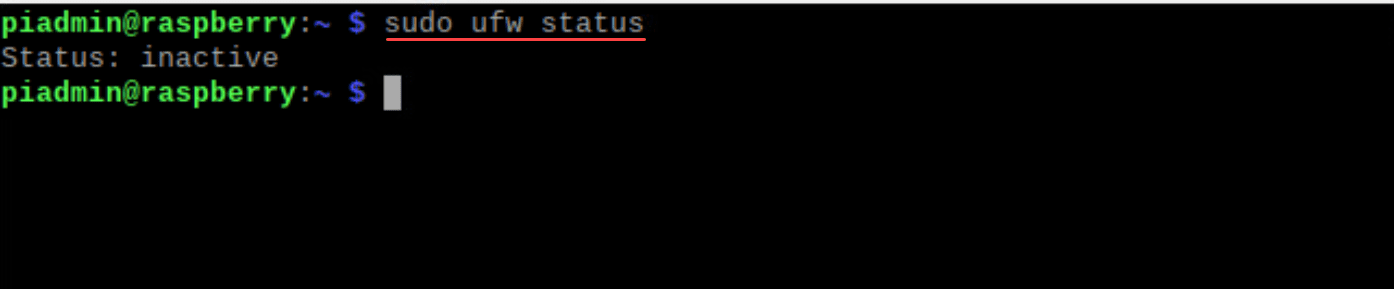
sudo ufw disableTo verify that UFW is indeed inactive, use:
sudo ufw statusThe response should be “inactive”, confirming that UFW is turned off.
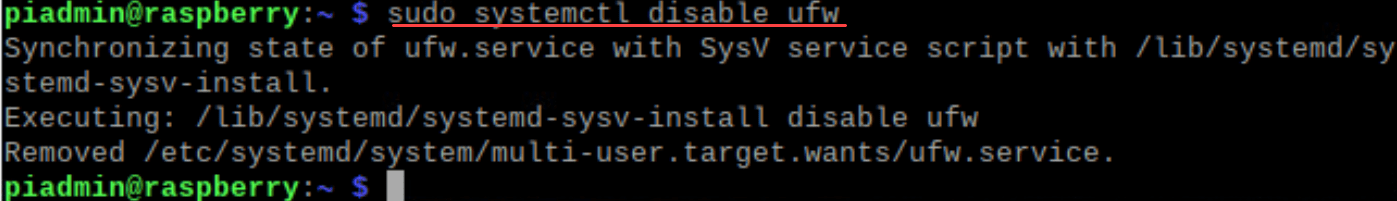
Permanently Disabling UFW using systemctl
To prevent UFW from starting on boot, disable the UFW service. The command might differ depending on your Raspberry Pi OS version and its services manager. If it uses systemctl, enter:
sudo systemctl disable ufwRemember to re-enable UFW or another firewall solution if you want to make sure of your Raspberry Pi’s security in the future. Always be cautious about the potential vulnerabilities when your firewall is off.
Troubleshooting Raspberry Pi Firewall
Encountering issues with your Raspberry Pi firewall? Here are some common problems and quick solutions:
Can’t Connect Remotely:
Make sure SSH is allowed in UFW: sudo ufw allow ssh.
Check your Raspberry Pi’s IP address; it might have changed on your local network.
Service Not Accessible:
Ensure the required port for the service is allowed in UFW.
Restart the service and check its binding port.
UFW Not Responding:
Restart the UFW service: sudo service ufw restart.
If persistent, consider reinstalling UFW: sudo apt install ufw –reinstall.
Unexpected Rule Behavior:
Check rules with sudo ufw status to confirm configurations.
Reset rules to default: sudo ufw reset.
UFW Installation Issues on Raspberry Pi OS:
Ensure your package list is updated: sudo apt update.
Try installing again: sudo apt install ufw.
Key Takeaways
Take note of the following key takeaways from this post as to why you benefit from knowing how to update your Raspberry Pi firewall from the command line:
Increased security: Treat your Raspberry Pi with the same security measures as any device. Especially if you are hosting services that are Internet-facing, having your Raspberry Pi firewall configured to only allow traffic that you want to allow helps to tighten down access and security.
Advantage of using UFW: It is a user-friendly tool to tweak and configure the IPtables firewall in Raspberry PI OS. Using it to your advantage is an easy way to add and remove rules to allow or disallow traffic.
Status Checks: Use sudo ufw status regularly to oversee your firewall’s activity and understand the status of whether your firewall is allowing or blocking traffic.
Rule Changes: Adjust UFW rules carefully. Blocking essential services can lead to issues or locking yourself out of the Raspberry Pi device. Especially if you are updating your UFW rules remotely, it is extremely important to understand your changes and ensure they won’t cause issues or disrupt your connection for management.
SSH Access: Ensure SSH is allowed if you’re using it for remote access. SSH is a common way to administer and remotely connect to Linux systems. Allow SSH access if you want to connect remotely using the protocol.
Granular rules: UFW lets you set rules for particular IP addresses or port ranges. You can allow or disallow connections by being specific in your rules. You can block a certain type of traffic in general and then allow that specific traffic for a certain host or client.
Port security: Only open necessary ports, like 80 or 443 for web servers.
UFW vs. iptables: UFW is a simpler interface to the Linux-native iptables.
Stay Updated: Periodically update UFW with sudo apt install ufw for security and enhancements.