Windows 10 RDP CredSSP Encryption Oracle Remediation Error Fix

For those of you who may have recently installed security updates on Windows 10 workstations in the past few days, you may notice that you receive a peculiar error when trying to establish a remote desktop connection to a server that worked before installing the updates manually or via Windows Server Update Services.
The initial March 13, 2018, release updates the CredSSP authentication protocol and the Remote Desktop clients for all affected platforms. The CVE-2018-0886 consists of installing the update on all eligible client and server operating systems and then using Group Policy or registry settings to configure the options on both clients and servers. Let’s take a look at Windows 10 RDP CredSSP encryption oracle remediation error fix.
Understanding the Oracle Remediation Vulnerability
The CredSSP (Credential Security Support Provider) protocol is used in Windows environments to securely transmit authentication information between clients and servers. The Oracle Remediation Vulnerability, identified as CVE-2018-0886, is a security flaw in the CredSSP protocol that allows an attacker to execute a man-in-the-middle (MITM) attack, potentially gaining unauthorized access to sensitive information or even taking control of the affected system.
How does the vulnerability work?
An attacker can exploit this vulnerability by intercepting and manipulating the authentication process between a client and a server. The attacker can then relay the client’s credentials to the server, effectively deceiving the server into believing that the connection is legitimate.
In an RDP scenario, this means that an attacker could gain unauthorized access to a remote system, execute arbitrary commands, and potentially access sensitive data. This vulnerability poses a significant risk to businesses, as it can lead to the compromise of critical systems and data.
Windows 10 RDP CredSSP Encryption Oracle Remediation Error Fix
Just a couple of days ago, the cumulative updates were released below for Windows 10 and Server 2016, etc. These cumulative updates include the fix for the CredSSP encryption vulnerability.
May 8, 2018 – KB4103721 (OS Build 1803)
May 8, 2018 – KB4103727 (OS Build 1709)
May 8, 2018 – KB4103731 (OS Build 1703)
May 8, 2018 – KB4103723 (OS Build 1609 & Server 2016)
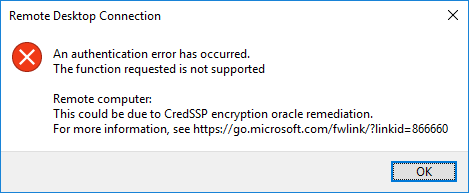
Once you have installed the patch on a “vulnerable” workstation and attempt to connect to a remote computer using remote desktop protocol, you will see the following error message that happens after you type in your password to authenticate to the RDP session to a Windows Server or computers running remote desktop.
RDP error message
The error details an rdp authentication error message and the function requested is not supported. The error occurs with machines that have the credSSP update installed. The KB referenced details a remote code execution vulnerability remediated with new policy settings. It denotes an insecure RDP connection.
A local policy setting is added with the installed security updates. You can find this by launching your local group policy editor. You can launch that by opening a command prompt window and typing gpedit.msc.
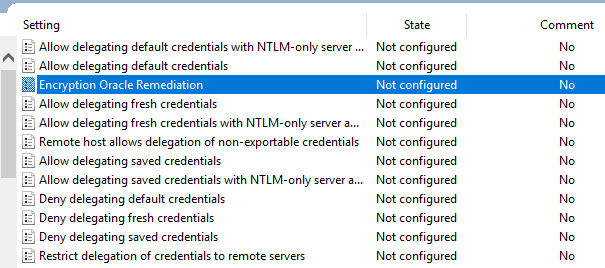
Navigate to Computer Configuration >> Administrative Templates >> System >> Credentials Delegation >> Encryption Oracle Remediation. By default this is set to Not configured in group policy settings.
Fix using Group Policy settings
To Fix the issue as a workaround, set the policy to Enabled and set the Protection Level to Vulnerable. Note – This is not recommended by Microsoft, as making sure both the client and server is patched is best practice.
However, setting the policy to Vulnerable allows your workstation to now connect to the remote desktop session that was previously blocked by the mitigation.
How to mitigate the Oracle Remediation Vulnerability?
Microsoft released security updates to address the Oracle Remediation Vulnerability in March and May 2018. These updates introduced new policy settings that allow administrators to control the behavior of CredSSP in their environments.
There are three policy settings available:
- Force Updated Clients: This setting requires both client and server to have the security update installed. Clients without the update will not be able to connect to updated servers, preventing the use of insecure CredSSP versions.
- Mitigated: This setting allows updated clients to connect to both patched and unpatched servers, but prevents clients from using insecure CredSSP versions. Unpatched clients can still connect to servers, but it’s crucial to update them as soon as possible to minimize risk.
- Vulnerable: This setting allows both updated and unpatched clients to use insecure CredSSP versions, effectively disabling the security update. This option is not recommended, as it leaves systems exposed to the vulnerability.
To fully mitigate the Oracle Remediation Vulnerability, it’s essential to apply the security updates on all client and server systems, and then configure the appropriate policy settings to ensure secure communication between them.
CredSSP Encryption Oracle Remediation Registry Setting
Alternatively, you can set this policy setting via the registry and a reboot.
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\CredSSP\ParametersAdd the following DWORD value:
AllowEncryptionOracle=dword:00000002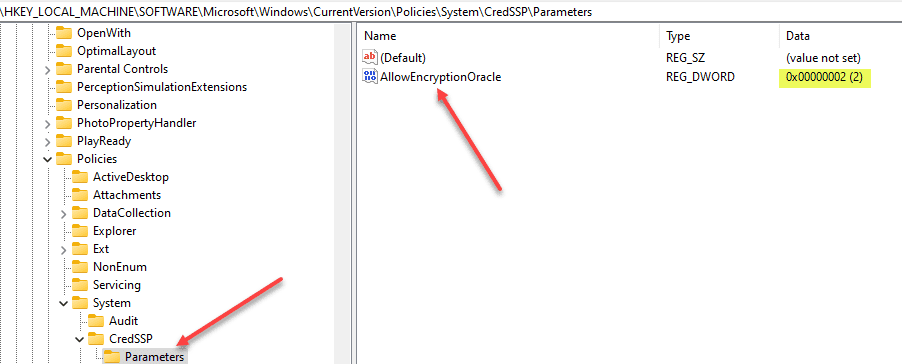
CredSSP Encryption Oracle Remediation Group Policy
These settings can be applied via a Group Policy Setting. For a great walk through of how to do this, check out this post here: https://www.mcbsys.com/blog/2018/03/updating-the-credssp-group-policy/
FAQs
- What is the CredSSP encryption oracle remediation error in Windows 10? The CredSSP encryption oracle remediation error occurs when trying to establish a remote desktop connection to a server after installing recent security updates on Windows 10 workstations.
- How can I fix the CredSSP encryption oracle remediation error in Windows 10? You can fix the error by setting the Encryption Oracle Remediation policy to Enabled and the Protection Level to Vulnerable, or by modifying the registry settings. However, it is best practice to ensure that both the client and server are patched according to Microsoft recommendations.
- What are the different policy settings available for CredSSP Encryption Oracle Remediation? There are three settings available: Force Updated Clients, Mitigated, and Vulnerable. Each setting determines the level of security and the types of clients that can connect to the server.
- Can I apply the CredSSP Encryption Oracle Remediation settings via Group Policy? Yes, you can apply these settings using Group Policy for a centralized configuration in your organization.
Troubleshooting
- I am still unable to connect to a remote desktop after updating Windows 10. What should I do? Make sure that you have set the Encryption Oracle Remediation policy correctly, and that both the client and server are patched as recommended by Microsoft.
- I’ve set the Encryption Oracle Remediation policy to Vulnerable, but I still can’t connect to the remote desktop. What could be the issue? Ensure that your workstation has the necessary updates installed, and that the remote server is configured to accept connections with the selected policy setting.
- I’m experiencing issues with remote desktop connections after applying registry settings. How can I resolve this? Verify that the registry settings have been applied correctly, and ensure that the DWORD value for AllowEncryptionOracle has been set to dword:00000002. If the issue persists, consider reverting the changes and using Group Policy settings instead.
RDP Security Best Practices
Protecting your remote desktop environment is crucial for maintaining system integrity and preventing unauthorized access. Here are some best practices for enhancing RDP security:
- Use Strong Authentication: Implement two-factor or multi-factor authentication (2FA/MFA) to add an extra layer of security, ensuring that only authorized users can access the remote desktop.
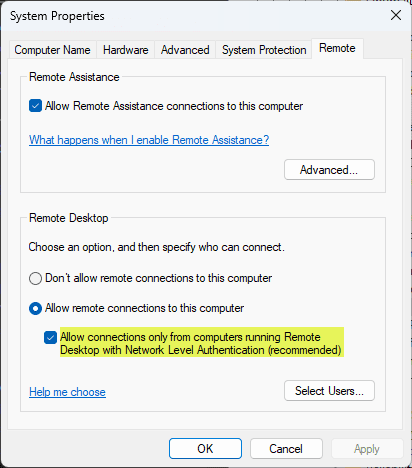
- Enable Network Level Authentication (NLA): NLA requires users to authenticate before establishing an RDP session, reducing the risk of unauthorized access and potential attacks.
- Keep Systems Updated: Regularly update both the client and server operating systems and RDP software to patch vulnerabilities and strengthen security.
- Limit User Privileges: Grant users the minimum necessary privileges to perform their tasks, and avoid giving administrative access to those who don’t require it.
- Use Encryption: Employ encryption technologies such as SSL/TLS to secure data transmission between the client and server during RDP sessions.
- Configure Security Policies: Set up and enforce security policies, including password policies, account lockout policies, and session timeout settings, to prevent unauthorized access and enhance overall security.
- Monitor and Audit: Regularly monitor RDP sessions and review logs to detect suspicious activities or potential security breaches, taking appropriate action when needed.
- Use a VPN or RD Gateway: Secure your RDP connections by using a Virtual Private Network (VPN) or Remote Desktop Gateway, which adds an additional layer of security and encrypts data transmission.
- Restrict RDP Access: Limit RDP access to specific IP addresses or subnets, and implement a firewall to block unauthorized traffic.
- Disable Unnecessary Services: Turn off unused features and services on both the client and server, reducing the potential attack surface.
Following these RDP security best practices, you can safeguard your remote desktop environment and minimize the risk of unauthorized access, ensuring a secure and reliable connection.
CredSSP Encryption Oracle Remediation Group Policy
These settings can be applied via a Group Policy Setting. For a great walk through of how to do this, check out this post here: https://www.mcbsys.com/blog/2018/03/updating-the-credssp-group-policy/
Takeaways
Patching is becoming ever more important with security vulnerabilities that are present today. Security is on the minds of everyone and it should be. Compromised systems can lead to data loss and data leak.
Keeping up with Microsoft patches and having a routine schedule of patch application is essential for enterprise datacenters running Microsoft server operating systems.
By mitigating known vulnerabilities the attack surface is drastically reduced and attacks become more difficult for the would be attacker.