Install Enhanced Mitigation Experience Toolkit EMET for better security
In this day and age of high profile exploits in the news involving businesses that we all know and use, digital security is more on the minds of everyone now than ever before. While there isn’t anything we as consumers can do to make the systems safe within corporations, we can all do more to improve our personal computer safety as well as safety within the enterprise environment. A lesser known tool developed by Microsoft does a good deal to improve security especially within the attack vectors that are being used more and more in today’s exploits such as Java vulnerabilities. The tool is a free download from Microsoft, and anyone can use Enhanced Mitigation Experience Toolkit EMET for better security.
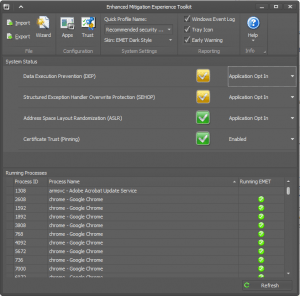
EMET can proactively anticipate attackers next moves so to speak and uses various techniques to squash the attackers attempts to exploit code on your computer. The really cool difference in EMET and your everyday virus scan for instance is that EMET can protect end users before these new “zero day” exploits come to light given that it proactively can anticipate and mitigate these attacks.
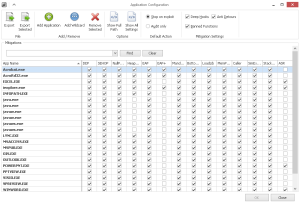
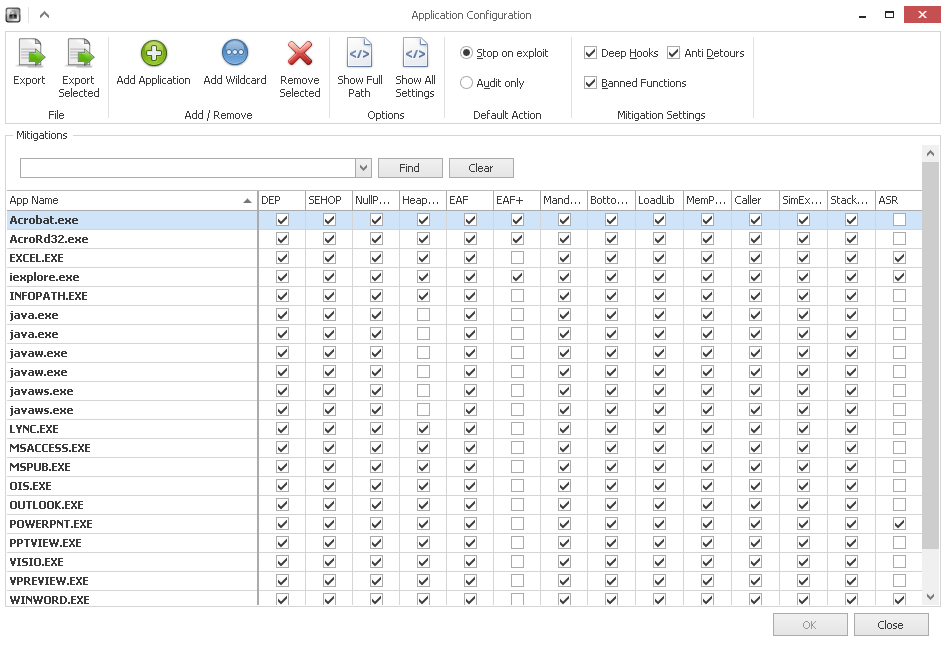
EMET is also very configurable and allows one to specify certain mitigation techniques based on a particular process and not a whole suite of applications just to cover one particular concern. SSL screening is also something EMET does really well in checking validity of SSL certs and mitigating certain attacks such as the “man in the middle” type attacks with spoofed SSL certs.
EMET uses various mitigation techniques such as:
- SEHOP – Structured Exception Handler Overwrite Protection
- Dynamic DEP – Data Execution Prevention
- Heapspray Allocation – prevents malicious copies of shellcode running in multiple memory locations
- Mandatory ASLR – Address Space Layout Randomization – this randomizes addresses where code processes are loaded to minimize chances of being used at predictable addresses
- EAF – Export Address Table Access Filtering – These filters screen accesses to the EAT table allowing or preventing access from the originating call
- EAF+ – Basically enhanced EAF
Supported OS’s:
- Windows Vista SP2
- Windows 7 SP1
- Windows 8
- Windows 8.1
- Windows Server 2003 SP2
- Windows Server 2008 SP2
- Windows Server 2008 R2 SP1
- Windows Server 2012
- Windows Server 2012 R2
Features compared to other Antiexploit software:
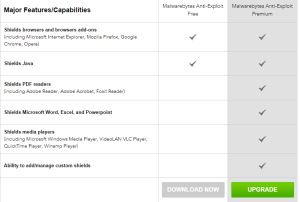
One nice thing about the EMET 5.0 product is that it includes these other modules for free. Unlike products such as the Malwarebytes AntiExploit product, you can mitigate any process you want via the EMET product. With Malwarebytes, to get such protection as PDF viewers you have to upgrade to the pay version as seen below from the Malwarebytes feature comparison.
Installation:
EMET version 5.0 can be downloaded from Microsoft here: https://www.microsoft.com/en-us/download/details.aspx?id=43714
Deployment methods include, sneakernet installs, System Center Configuration Manager, and of course Group Policy
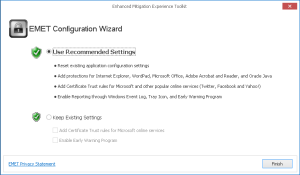
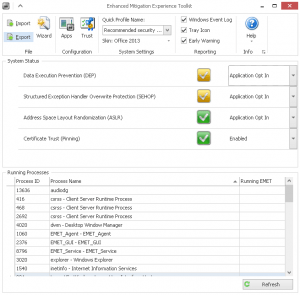
- The default recommended settings includes protection for Internet Explorer, Wordpad, Microsoft Office, Adobe Acrobat and Reader, and Oracle Java. It also adds default EAF+ rules and Certificate trust rules.
Customizing Rules, Look and Feel
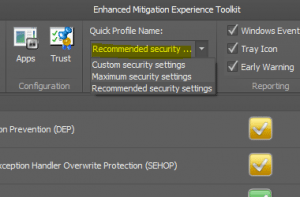
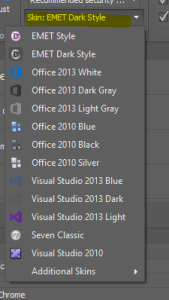
I really like the fact that the EMET software is very customizable in the way it operates as well as its look and feel. The software comes preinstalled with many different themes to changes things up. Also, you can customize the security level of the rules being applied with a simple dropdown box to up the security from the recommended settings to the maximum security levels the software provides.
The logging notifications with EMET 5.0 is also very impressive. By default the program notifies you via the tray icon if it blocks an application as well as the Windows Event Log picks up the event in the Application event log.
Final thoughts:
Exploit mitigation these days is an essential part of anyone’s personal computing security model. Enterprises also need to look into this aspect of security as these days the tradition firewalls and virus scans just simply don’t provide the level of protection needed by those browsing the Internet. Exploits can compromise anyone’s personal security and identity at any given time. The Microsoft Enhanced Mitigation Experience Toolkit is a great way to lessen one’s attack surface along with the appropriate firewall and virus scan protection. The nice thing about EMET 5.0 is that it provides extremely customizable protection for free.