Security is on everyone’s mind today. In fact, if you aren’t thinking about security, you most likely don’t work in technology. Security is no longer a “bolt on” affair or afterthought. It is part of the overall picture of today’s infrastructure. Since businesses today live and die by their access to business-critical data, they must keep that data secure and out of harms way from attackers and other malicious activities. VMware vSphere has gotten better and better from a security perspective with each new version of vSphere released. Starting with vSphere 6.5, VMware has made several major leaps forward from a security perspective, introducing major new features that allow protecting virtual machines and the underlying data that is contained in the virtual disks. Additionally, mechanisms have been introduced to protect the integrity of the guest operating system, helping to ensure the integrity of the operating system and other protected and critical components. Let’s take a look at securing VMware virtual machines with encryption VBS and vTPM to see how these new features are providing significant improvements in the overall security of environments running VMware vSphere.
Securing VMware Virtual Machines with Encryption VBS and vTPM
There are three features that we want to key in on that provide tremendous new security abilities in the latest versions of vSphere. They are:
- Encryption
- Virtualization Based Security
- vTPM or Virtual Trusted Platform Module
Let’s take a closer look at each of these new features one by one and see how they greatly enhance the overall security stance for your virtual machines running in VMware vSphere.
VMware vSphere Virtual machine Encryption
Encryption has been a longstanding and effective way to keep data private even if it falls into the hands of someone who is not authorized to have it. Encryption by its simplest definition makes data unreadable, gibberish, if you don’t have the key to decrypt the data that you possess. The encryption key is used to make the data unreadable or encrypted.
As of VMware vSphere 6.5, VMware introduced virtual machine encryption that allows encrypting virtual machines running inside of VMware vSphere. This includes the VM files, VM virtual disks or VMDKs, and host core dump files. A really cool component of this feature is the ability to apply encryption at a per VMDK level. The virtual machine encryption functionality piggy backs on top of the storage policy based management of vSphere or SPBM in that the virtual machine encryption is a type of storage policy that can be utilized.
Additional benefits include:
- No changes have to be made to the virtual machine guest operating system
- No special hardware is needed in the infrastructure
- Policy-based enforcement
What are the requirements of VMware vSphere virtual machine encryption?
- Key Management Server
- vCenter Server
- ESXi hosts
The first component, the Key Management Server or KMS, is most likely the component you will need to provision as most likely you already have a vCenter Server and ESXi hosts. What does the KMS server do? The KMS server generates and stores Key Management Keys or KEKs that are given to the vCenter Server for distribution. The vCenter Server becomes a KMIP client.
The vCenter Server uses the keys that are generated by the KMS server to transmit to the ESXi hosts which use these keys to perform the actual encrypting. The ESXi hosts perform the encryption of the VM disks and also verifies and enforces the data is encrypted for VMs and not sent over the network without encryption.
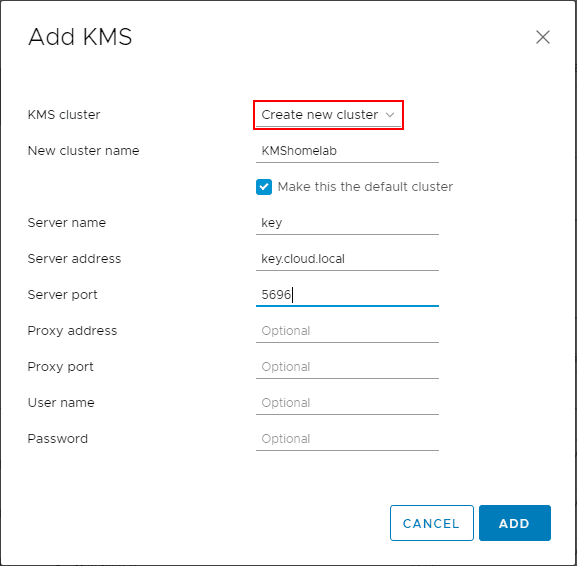
Below, are a few screens of adding a new Key Management Server or KMS server to vCenter Server.
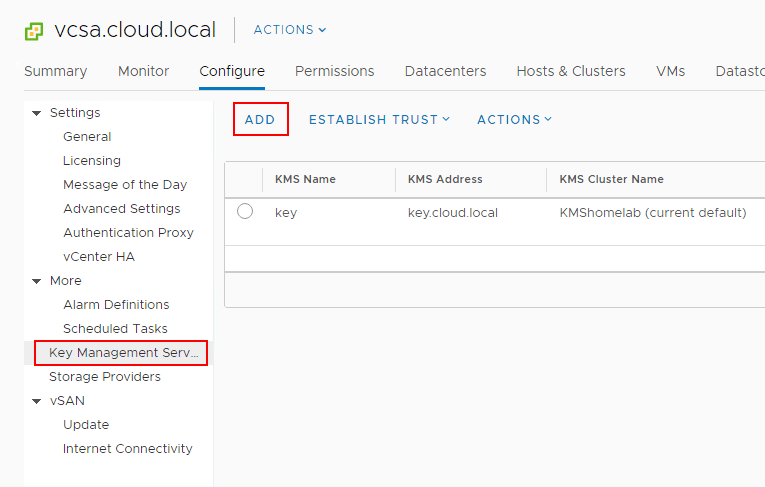
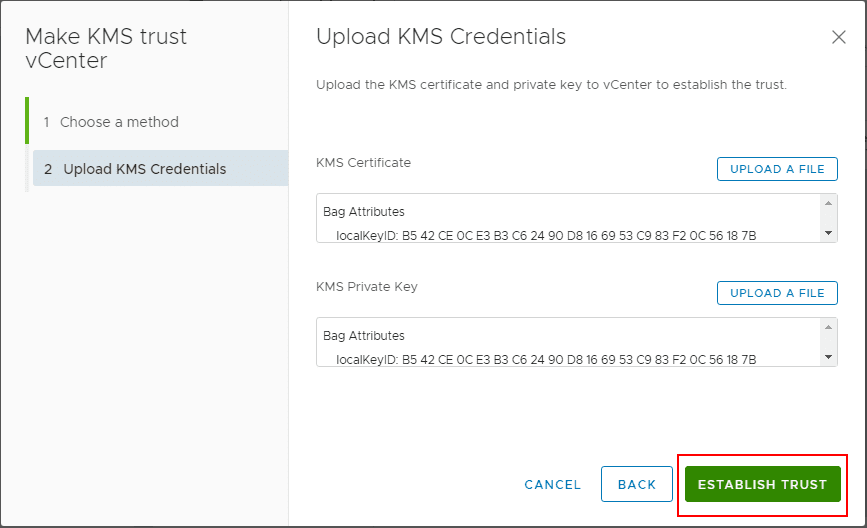
Skipping forward to the Make KMS trust vCenter wizard, trust between the KMS server and vCenter is being taken care of by way of uploading KMS certificate and KMS private key.
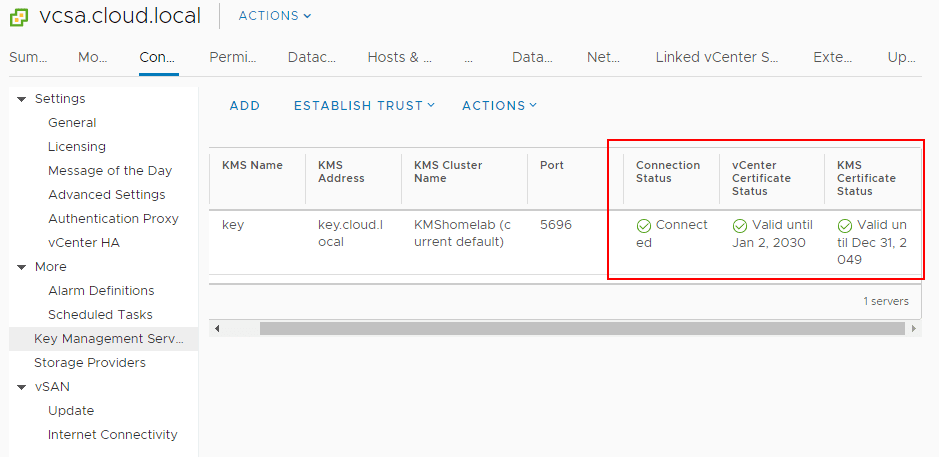
After going through the establishing of trust between the KMS server and vCenter Server, the KMS server is now trusted and ready to start issuing keys.
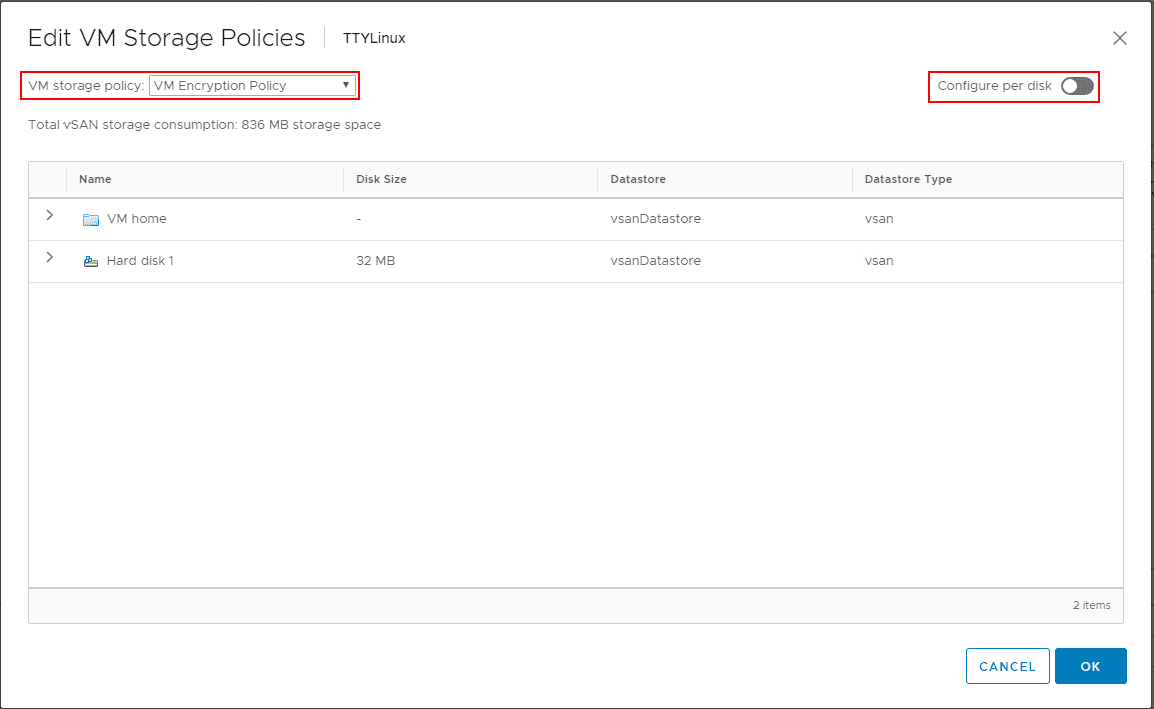
VMware vSphere virtual machine encryption policy is a great way to exponentially increase your security posture in a virtual environment. It does not require specialized hardware or a lot of complicated configuration. Aside from the KMS server configuration, the other components are already available natively in vSphere.
VMware vSphere Virtualization Based Security
Another great security feature that has been included with vSphere 6.7 and higher is the Virtualization Based Security or VBS that was introduced by Microsoft for Windows 10 and Windows Server 2016 and higher. So, this is a native Microsoft technology, but VMware has allowed the ability through additional virtual machine features to effectively implement this feature in guest operating systems running inside of VMware vSphere VMs. The VBS feature allows protecting sensitive credentials and other information from potential compromise of the guest operating system. It does this by utilizing the Hyper-V hypervisor to actually load the guest operating system. It creates a protected memory space for these sensitive pieces of information and locks down access to it.
The prerequisites for virtualization-based security are minimal.
- Windows 10 or Windows Server 2016 and higher
- VMware vSphere 6.7 and higher
- VM hardware version 14 and higher
- EFI Firmware
- Secure Boot
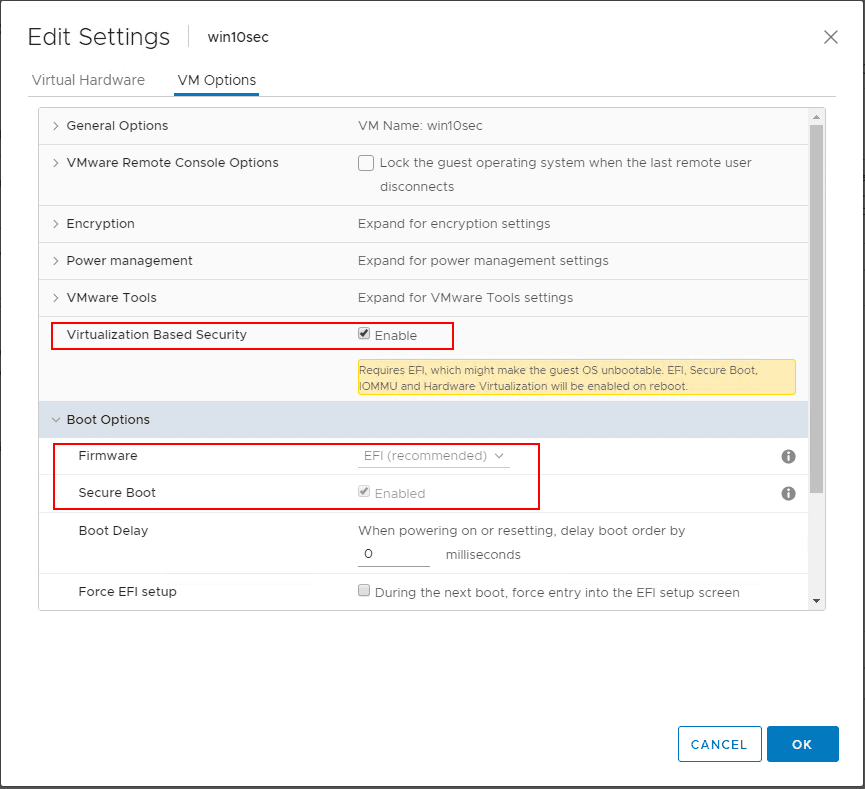
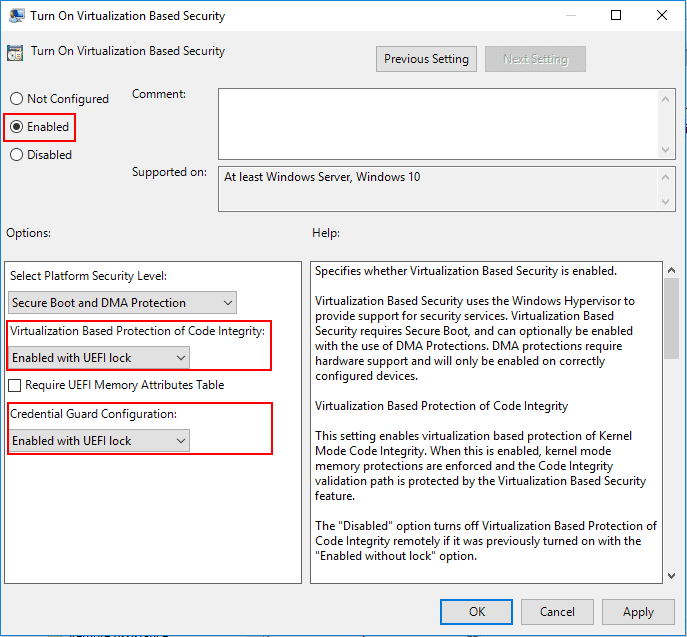
Virtual Trusted Platform Module
There are various hardware based security technologies that are being extended into the virtualized environment space. One of these is the hardware-based Trusted Platform Module or TPM device. The TPM is a hardware-based chip that stores encryption information, certificates, etc, that help to attest to or validate the integrity of systems. By extension, this technology has been extended into the virtualized space by way of the Virtual Trusted Platform Module or vTPM device. The vTPMs allow performing cryptographic coprocessor capabilities in the software layer. This allows extending the benefits of the TPM module into the virtualized environment and allows a way of checking the integrity of virtual machines and the software running inside them as you would a physical system.
Requirements for the vTPM virtual hardware:
Virtual machine requirements:
- EFI firmware
- Hardware version 14
Component requirements:
- vCenter Server 6.7 or 6.7 Update 1
- Virtual machine encryption (to encrypt the virtual machine home files).
- Key Management Server (KMS) configured for vCenter Server (virtual machine encryption depends on KMS).
Guest OS support:
- Windows Server 2019 (64 bit)
- Windows Server 2016 (64 bit)
- Windows 10 (64 bit)
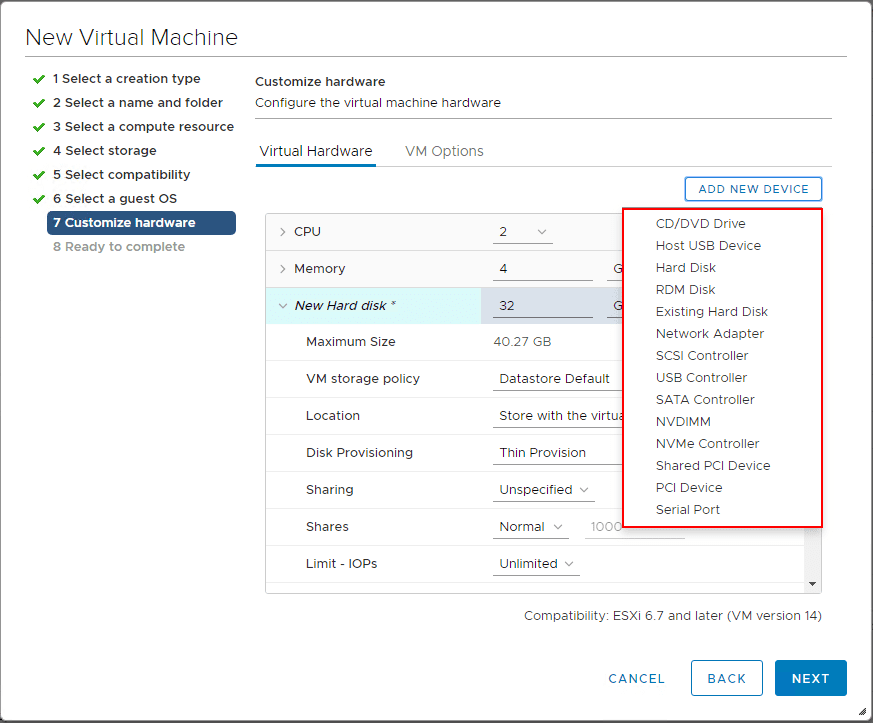
Below I have created a new Windows 10 test virtual machine and enabled EFI and secure boot.
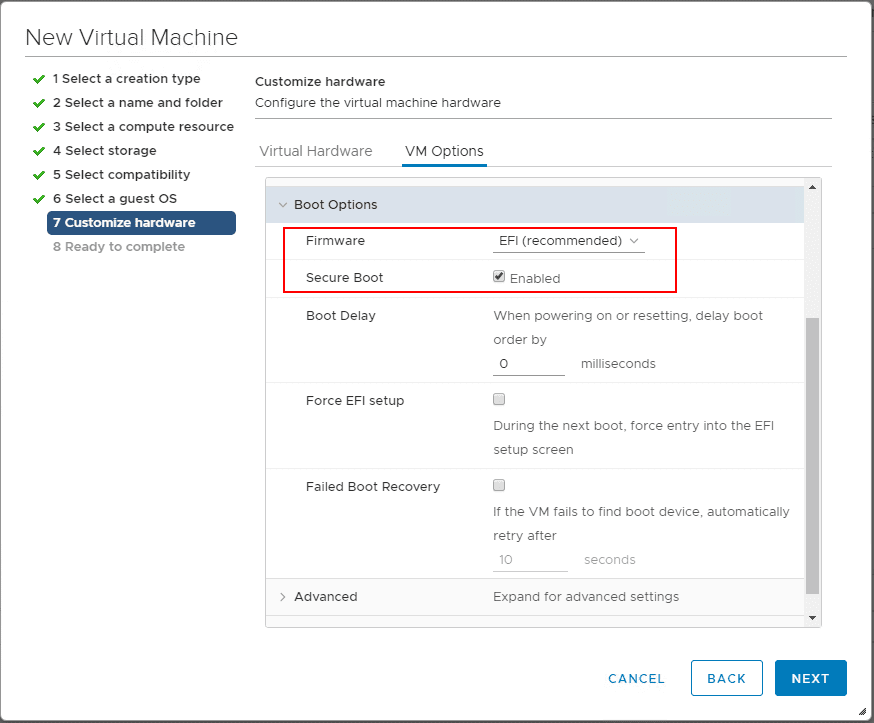
Go to Add New Device and choose the Trusted Platform Module to add the vTPM.
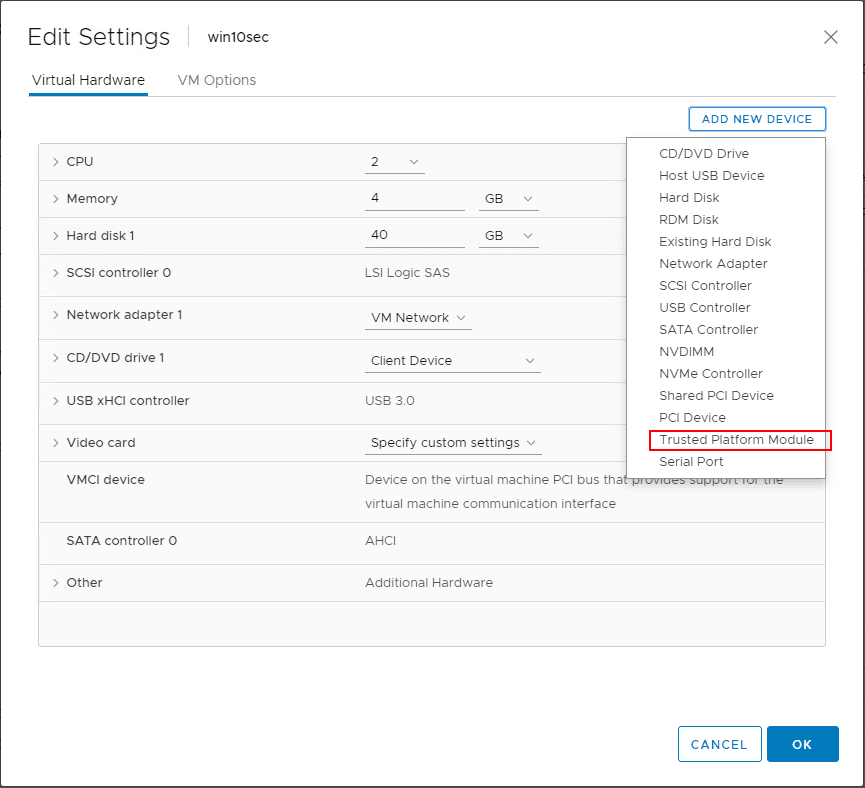
A note here, if you have no KMS Server added to vCenter Server, even with a new virtual machine that has EFI and secure boot enabled, you will not see the option to add the Trusted Platform Module.
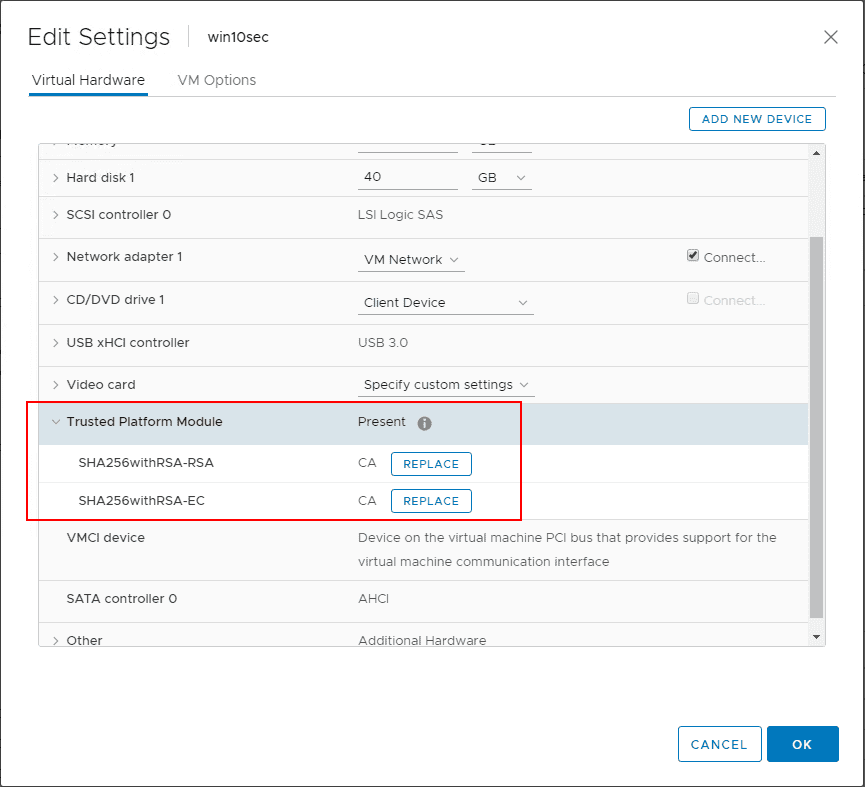
After adding the virtual Trusted Platform Module you will see the device along with the certificates in the properties of the virtual machine.
Takeaways
Securing VMware Virtual Machines with Encryption VBS and vTPM are three great ways to add additional security to a VMware vSphere virtual machine. The great thing about these three features is the simplicity with which they can be added to the virtual environment. No additional hardware is required and the processes to complete the configuration of the security mechanisms are all found in the vSphere client. The only additional outside component is the KMS server that will need to be configured. However, most of these I have seen and worked with are fairly intuitive and easily provisioned as OVA appliances in vSphere. By using the additional VMware vSphere features, you will ensure a much tighter and exponentially more difficult environment to compromise from a security perspective. Kudos to VMware in getting these new features included in vSphere and providing an easy way to get them implemented right from within vSphere.