Three Simple Things to Make VMware ESXi More Secure
If you are like me in production and home lab environments, I am always looking for low-hanging fruit to make things better, faster, more efficient, and more secure. There are three things that you can do in VMware ESXi to make your environment more secure. Let’s dive into what those are and how you can easily implement these using a PowerCLI script run from a scheduled task or even a CI/CD pipeline.
Table of contents
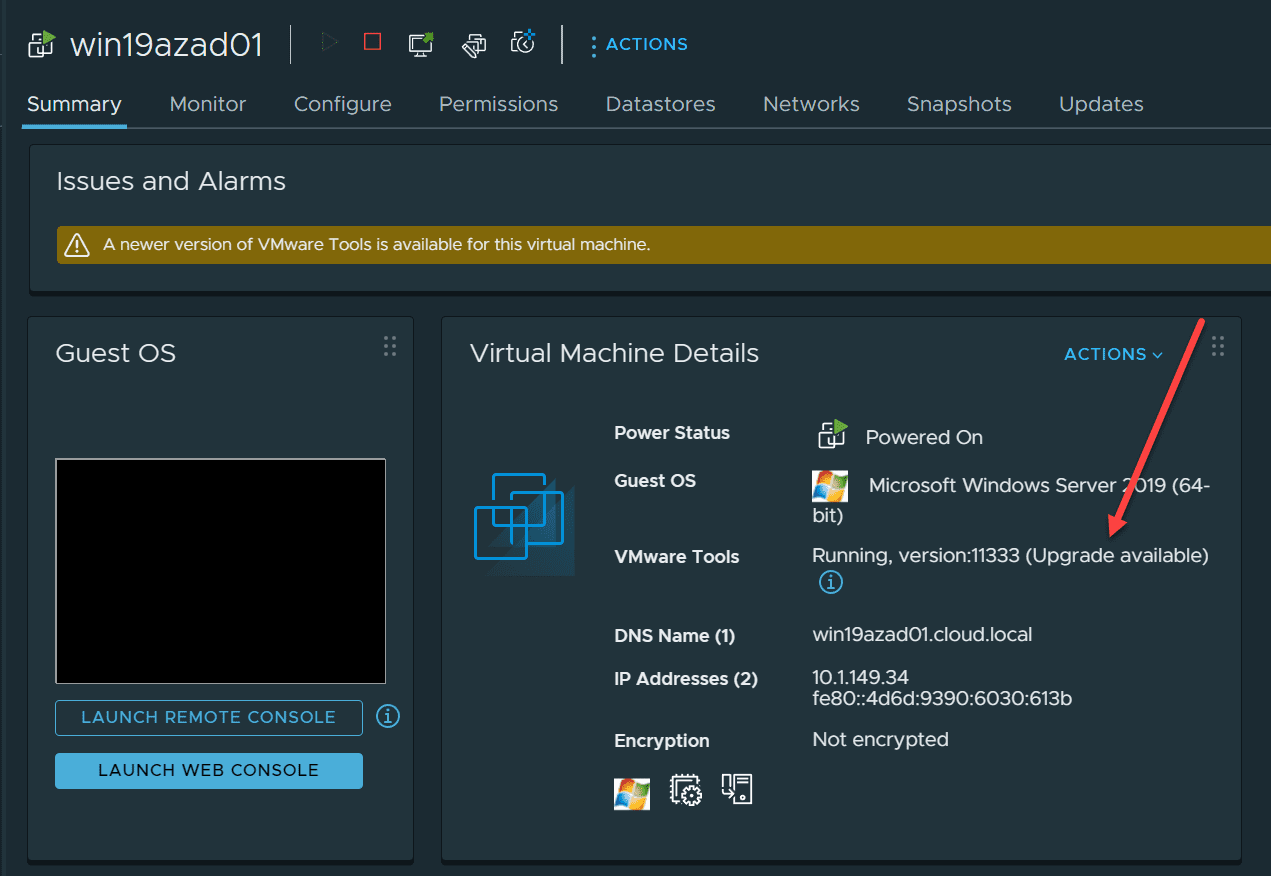
1. Keep VMware tools updated
Keeping VMware tools updated is extremely important from the standpoint of keeping the environment secure and your guest virtual machines performing as expected. VMware Tools is the special package you install in your guest operating system to allow ESXi to interact with the guest OS’es easily and effectively. It provides special functionality and allows for the extraction of information from the guest OS and presentation to ESXi or vCenter Server.
Backup solutions can also use the special hooks with VMware tools for backups. Automation solutions can use VMware tools for automation as well. With PowerCLI, we can easily run a script to iterate through VMs and update VMware tools.
# Upgrade VMware Tools on all VMs
Get-VM -location "Your VM folder" | Where-Object { $_.ExtensionData.Guest.ToolsVersionStatus -eq 'guestToolsNeedUpgrade' -and $_.PowerState -eq "PoweredOn" } | ForEach-Object {
Update-Tools -VM $_ -NoReboot
}You can use the -location directive to point at a specific folder in inventory, or you can take this out to target everything. As you can see with the Update-Tools directive, you can pass in the -NoReboot parameter to keep it from rebooting the VM.
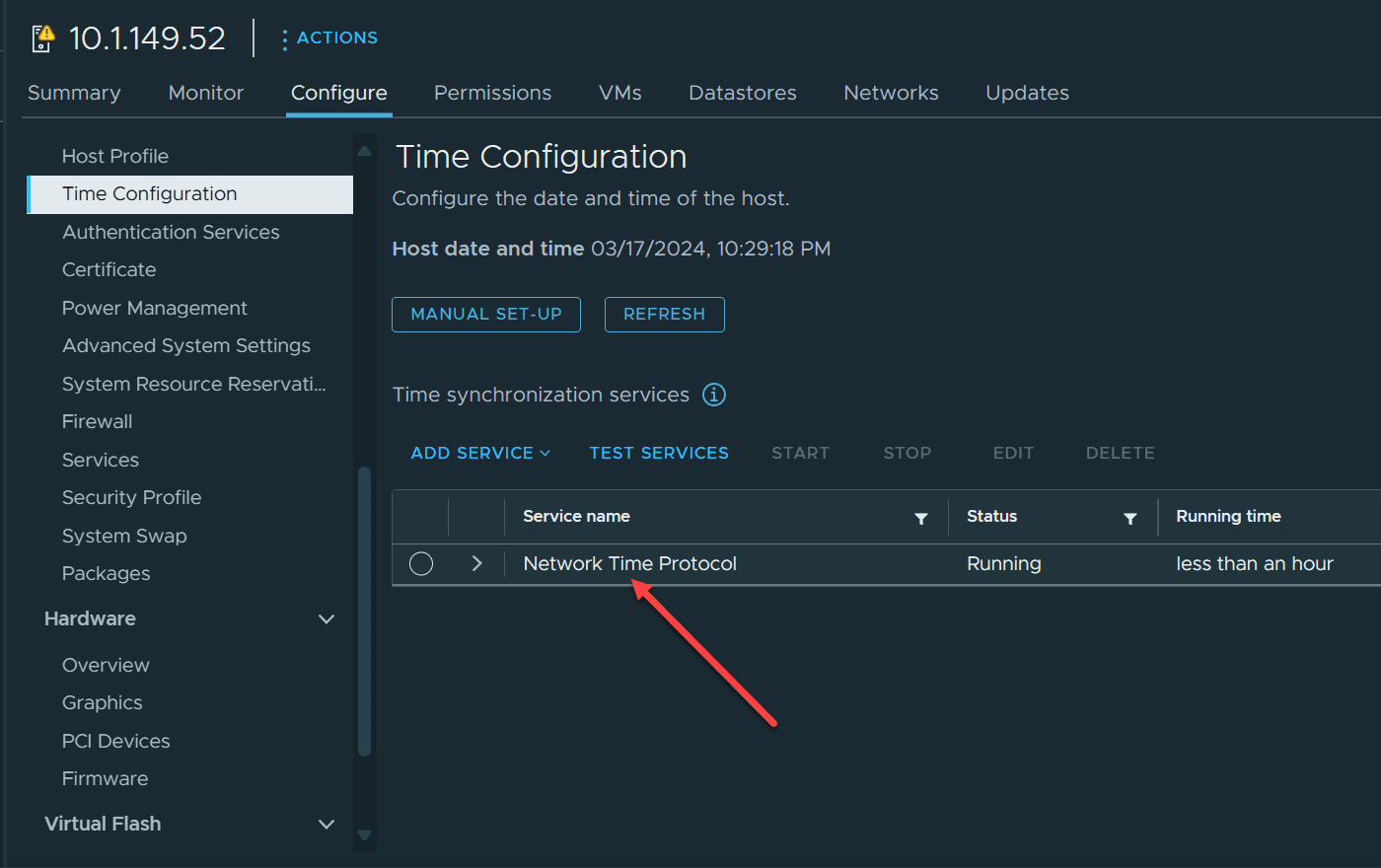
2. Set NTP servers and time configuration for VMware ESXi hosts
The next setting is NTP configuration for your VMware ESXi servers. Why is time configuration important for security? The following are just a few examples of why NTP configuration is important:
- Logs – Having accurate time is important since it will allow logs to be written with accurate timestamps to correlate events in the right way and sequence
- Authentication – Many authentication protocols rely on accurate time, including Kerberos. Large skews in time can cause authentication failures and might be exploited by an attacker to take advantage of the time skew and extend malicious authentication tokens.
- Certificate validity – SSL/TLS certificates will have issues if accurate time settings are not applied correctly. I have seen instances where due to large time skew, ESXi hosts can’t be added to vCenter Server or other issues related to the time, causing SSL certs to be invalid, incorrect, or broken.
Let’s see how you can configure NTP on all VMware ESXi hosts in inventory using PowerCLI:
# Configure NTP settings and ensure the NTP service is started and set to start with the host
Get-VMHost | ForEach-Object {
Add-VMHostNtpServer -VMHost $_ -NtpServer "us.pool.ntp.org" -Confirm:$false
Get-VMHostService -VMHost $_ | Where-Object {$_.key -eq "ntpd"} | Set-VMHostService -Policy "on" -Confirm:$false
Get-VMHostService -VMHost $_ | Where-Object {$_.key -eq "ntpd"} | Start-VMHostService -Confirm:$false
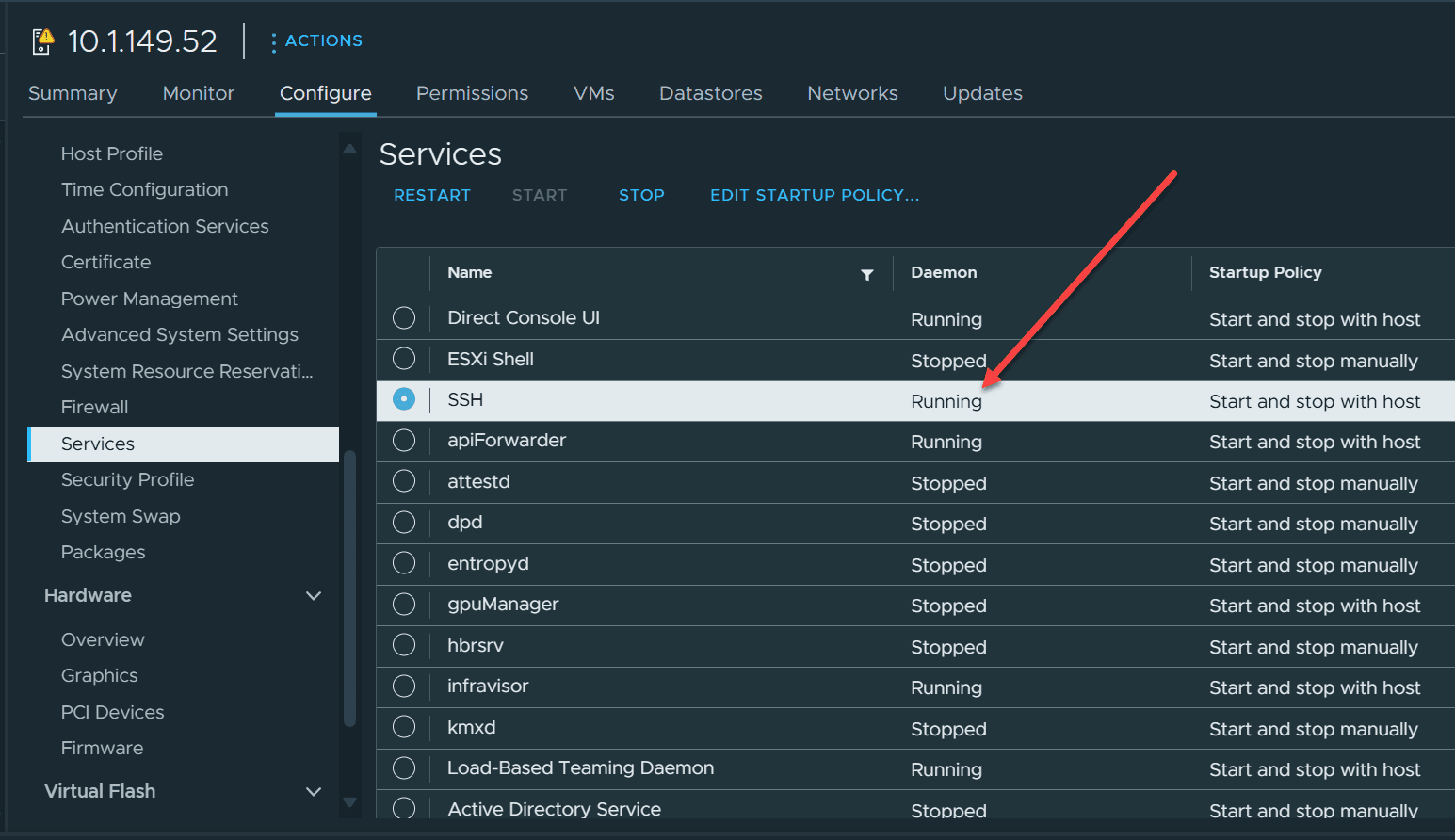
}3. Disable SSH
How many environments have you see with dozens of ESXi servers with SSH enabled? Scary right? SSH is fine to enable temporarily if you need it for a specific reason or for troubleshooting. However, do not leave SSH enabled on production ESXi hosts.
One of the problems I see with SSH enabled on ESXi servers is the intention is always to disable it, but this can be forgotten and usually is, especially if there are many hosts in the environment.
It is great to have some type of remediation process or task that automatically looks at your hosts and stops the SSH service if it is started.
With PowerCLI, you can do this with the following script:
# Disable SSH service on all ESXi hosts
Get-VMHost | ForEach-Object {
Get-VMHostService -VMHost $_ | Where-Object {$_.key -eq "TSM-SSH"} | Set-VMHostService -Policy "off" -Confirm:$false
Get-VMHostService -VMHost $_ | Where-Object {$_.key -eq "TSM-SSH"} | Stop-VMHostService -Confirm:$false
}Putting the scripts together
You can easily put the parts of the script all together and have them run in a single script as a task or CI/CD pipeline.
In the top of the script below, I am setting variables in the script that are getting pulled from the Gitlab variables in the CI/CD pipeline variables configuration.
$vsphereuser = $env:VSPHEREUSER
$vspherepassword = $env:VSPHEREPASSWORD
$vcenterserver = $env:VCENTERSERVER
##Setting CEIP options
Set-PowerCliConfiguration -InvalidCertificateAction Ignore -ParticipateInCeip $false -Confirm:$false
##Connect to vCenter
connect-viserver $vcenterserver -user $vsphereuser -password $vspherepassword
# Upgrade VMware Tools on all VMs
Get-VM -location "Blog Testing" | Where-Object { $_.ExtensionData.Guest.ToolsVersionStatus -eq 'guestToolsNeedUpgrade' -and $_.PowerState -eq "PoweredOn" } | ForEach-Object {
Update-Tools -VM $_ -NoReboot
}
# Configure NTP settings and ensure the NTP service is started and set to start with the host
Get-VMHost | ForEach-Object {
Add-VMHostNtpServer -VMHost $_ -NtpServer "us.pool.ntp.org" -Confirm:$false
Get-VMHostService -VMHost $_ | Where-Object {$_.key -eq "ntpd"} | Set-VMHostService -Policy "on" -Confirm:$false
Get-VMHostService -VMHost $_ | Where-Object {$_.key -eq "ntpd"} | Start-VMHostService -Confirm:$false
}
# Disable SSH service on all ESXi hosts
Get-VMHost | ForEach-Object {
Get-VMHostService -VMHost $_ | Where-Object {$_.key -eq "TSM-SSH"} | Set-VMHostService -Policy "off" -Confirm:$false
Get-VMHostService -VMHost $_ | Where-Object {$_.key -eq "TSM-SSH"} | Stop-VMHostService -Confirm:$false
}
# Disconnect from vCenter
Disconnect-VIServer -Server $vcenterserver -Confirm:$falseAre these the only things to worry about or possibly remediate? No, but these are easy things you can do to keep your environment configured with best practices and make sure that VMware tools are updated, NTP configured, and SSH is stopped.