Windows Server 2019 New Security Features
There is no doubt about it that security is on the minds of everyone today. With high profile breaches and data leaks reported in major news headlines, security is on the radar of both IT professionals and C-level executives alike. With each version of Windows Server, Microsoft has greatly improved the security stance by including new features, functionality, and tools that allows organizations to be more secure and have the ability to gain better visibility into their environments powered by Windows Server. With Windows Server 2019 soon to be released, let’s take a look at Windows Server 2019 New Security Features and how these will better equip businesses today to have better security and visibility to security events.
How Compromises in Security Happen
Before taking a look at the new Windows Server 2019 security features, let’s take a step back and see how compromise happens. When looking at attacks from the standpoint of an attacker, there is a research and preparation time which is typically 24-48 hours statistically before any malicious activity is carried out. A very common way that attackers gain control of an environment is by stealing credentials. Normally pass the hash attack is used to get unauthorized credentials from the system’s memory. Using domain credentials access can be granted by the attacker and give themselves access to the data they actually want. Generally, they can continue to move laterally across an environment stealing different types of credentials until they stumble upon a cached domain administrator credential. With this level of access, they can grant themselves access to the resources and data in the environment they truly want.
Often times, control is established of a particular device and then use credentials gained to gain control over additional devices.
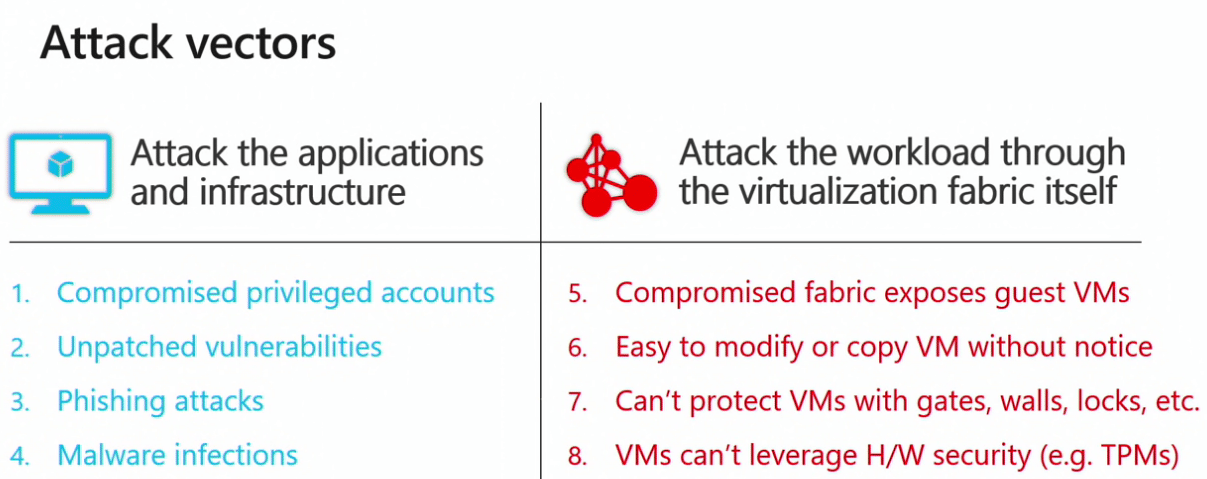
When looking at various security attacks, whether it be – phishing attacks, stolen creds, pass-the-hash, insider attacks, fabric attacks, all have in common administrative privileges. In fact, the goal of most attacks is to seek out privileged accounts. Privileged accounts have the keys to the kingdom and can easily be compromised via social engineering, bribery, coercion, private initiatives, etc.
Another layer of many security vulnerabilities were introduced with virtualization. Attacking the fabric of the virtualization technology can get an attacker highly privileged access to data.
Common principles found in Windows Server 2019 Security Architecture
Much of the information presented below was summarized from the Windows Server Summit event held this summer.
Four principles of security – protect, detect, respond, isolate.
- Protect – ongoing focus & innovation on preventative measures; block known attacks & known malware
- Detect – Comprehensive monitoring tools to help you spot abnormalities and respond to attacks faster
- Respond – Leading response and recovery technologies plus deep consulting expertise
- Isolate – Isolate OS components & secrets; limit admin privileges; rigorously measure host health
Security is an architectural principle not a bolt on.
Windows Server 2019 New Security Features
There are several new security features that are found in Windows Server 2019, many of which are extensions of current capabilities that were introduced in Windows Server 2016 and Windows 10.
- Shielded VM improvements – branch office support, simpler cloud-friendly attestation (3 commands to get a host to participate in Guarded Fabric – doesn’t supply as strong assurance as TPM but allows dipping toe into guarded fabric), Linux OSes, and troubleshooting capabilities by using enhanced virtual machine configuration consoles.
- Device Guard policy updates can now be applied without a reboot – New default policies ship in-box
- Kernel Control Flow Guard (CFG) – CFG ensures user and kernel-mode binaries stay on the rails/run as expected. Monitors the binaries to ensure it runs as it was designed to do.
- System Guard Runtime Monitor – Someone to keep an eye on everything else. Emits health assertions (claims) that can be consumed by downstream relying parties
- Virtual Network Encryption through SDN
- Windows Defender ATP agent is now in-box – no download required. all of the technologies are available as long as VBS is available.
Highlighting Windows Server 2019 Shielded VMs
Shielded VMs: Linux OS Support – Supports Ubuntu, Red Hat (RHEL), and SUSE Linux Enterprise Server inside shielded VMs – Host must be running Windows Server 2019
- Native protection of the root and boot volumes using dm-crypt – Boot passphrases sealed to the virtual TPM+
- Secure provisioning workflow fully supported – Ensures the template disk is safe and trusted
Shielded VMs: Host Key Attestation
With Windows Server 2016 Active Directory Attestation, and TPM based attestation were the options for host guardian service attestation with TPM being the most difficult but best security to configure for attestation. Now there is a new method added in Windows Server 2019 for host attestation called host key attestation with the following benefits.
- Uses asymmetric key pairs to authorize a host to run shielded VMs. No more AD trusts required; no certificates; similar to how SSH works
- Easier onboarding process with fewer requirements and less fragility – Very quick and simple to get a guarded fabric up and running
- Similar assurances to Active Directory attestation – Checks only the host identity, not its health. Best practices recommend the use of TPM attestation for the most secure workloads
Shielded VMs branch office support
- Hyper-V hosts can be configured with both a primary and fallback HGS – Useful if there is a local HGS for dialy use and a remote HGS if the local HGS is down/unavailable. Enables the deployment of GHS in a shielded VM
- For completely offline applications, you can now authorize hosts to cache VM keys and start up VMs even if the host guardian service cannot be reached. Cache is bound to the last successful security/health attestation event, so a change in the host’s configuration that affects its security posture invalidates the cache.
Shielded VMs Improved Troubleshooting
- Enhanced VMConnect now permitted with fully shielded VMs assists with troubleshooting NIC misconfigurations, etc. Can be disabled within the shielded VM.
- PowerShell Direct also permitted to shielded VMs – Combine with JEA to let the host admin fix only specific problems on the VM without giving them full admin privileges. Can also be disabled within the shielded VM
- Make sure code executes with integrity. User identities cannog be compromised spoofed or stolen. Attacker with casual physical access cannot modify data or code. Malicious code cannot persist. Violations of promises are observable. All apps and system components have only the privileges they need.
- Make Windows tamper evident – System Guard Runtime monitor spots tampering events. Platform tamper detection for Windows. High integrity sensor reportwss evidence of tampering. Designed for remote assesment of device health. Platform approach to benefit a varitey of 3rd parties and scenarios.
Takeaways
There are a wide variety of Windows Server 2019 New Security Features that are set to help organizations take their security posture to the next level. Especially in the realm of virtualization, Windows Server 2019 helps organizations guard the fabric and underlying components and privileges that are often subject to compromise by attackers. With new enhancements to Shielded VMs, and the host attestation service with new branch office and troubleshooting features, businesses can better implement this technology to protect their business-critical data. The new System Guard Runtime Monitor that looks to be making it into Windows Server 2019 is a great new service that basically watches everything else security related and makes sure there are no anomalies.