Bootstrap Windows Server Configuration with Ansible Playbooks
In our previous Ansible post covering basic Windows Server automation with Ansible, we looked at how to get an ansible server up and running as well as how to get the Ansible server connected to a Windows Server that we want to automate using WinRM. We saw how to test the WinRM connection to the Windows Server and run a few basic “raw” commands as well. However, in this post let’s take this a few steps further with seeing how we can bootstrap Windows Server configuration with Ansible playbooks. This will include seeing how we can structure our Ansible working directory as well as creating a playbook that includes the commands we want to run on a fresh Windows Server installation to run some normal basic setup on our server.
Setting Up Ansible Directory Structure
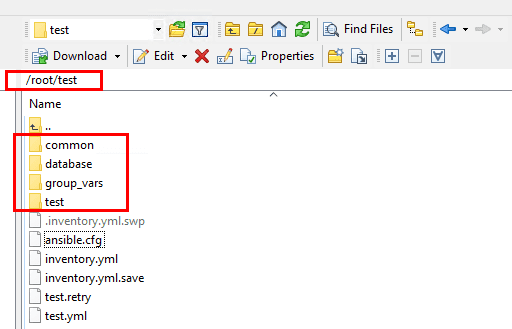
One of the first quick things to cover is setting up our Ansible directory structure. On my server in the root directory, I setup a test folder to represent my working directory that I will be setting up files, folders and such to interact with Ansible.
Below is a high level view of the working directory that I have setup for working with Ansible bootstrapping a Windows server. The folders you see below including common, database, and test are server roles. Each role can/should have its own playbook, so you would have different configuration for each server role.
Also below, you will see the ansible.cfg file. In this file we can do little things that are useful such as hardcoding the location of our inventory file. The inventory file is what tells Ansible which group or role that a particular host resides in. This way, we don’t have to specify the inventory file each time we run the Ansible executable.

In the group_vars folder, the test.yml file contains the following information for WinRM connectivity:
ansible_user: ansible ansible_password: ansible ansible_port: 5985 ansible_connection: winrm ansible_winrm_transport: basic ansible_winrm_cert_validation: ignore
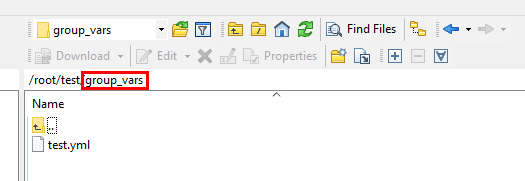
Below we see the test role folder that contains the tasks and templates folders. Templates contains templates such as the .j2 formatted template file for use with setting up a new IIS site.
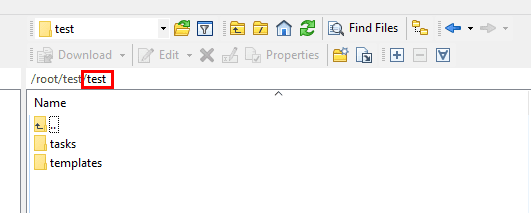
Under the tasks folder, we have the main.yml file where we can place our windows modules and command snippets.
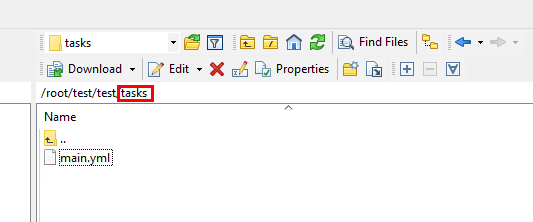
In the parent .yml file that exists outside of our directories for the server roles, we can call the server roles specific playbooks for our inventory. Below, the hosts are the section of the inventory file that we want to run. The roles are the role playbooks that we want to run against those hosts in the inventory file that we have defined.
---
- hosts: test
roles:
- test
- common
Bootstrap Windows Server Configuration with Ansible Playbooks
There are many really nice basic Ansible code snippets that shortcut many of the basic Windows setup steps that most of us go through to stand up a fresh Windows server. There are many setup steps that most can think of including, running Windows updates, setting up local user accounts, DNS values, domain joins, etc. Let’s take a look at a few of these snippets that can be used for really quick provisioning of a Windows server with a hands off, automated approach.
Most of the Ansible Windows modules start with the win_ prefix to the module for the specific functionality. A full listing of the Windows modules available is found here:
Configuring DNS server values for a Windows server
- win_dns_client: adapter_names: '*' ipv4_addresses: - 8.8.8.8 - 8.8.4.4
Windows Domain join
- hosts: winclient
gather_facts: no
tasks:
- win_domain_membership:
dns_domain_name: ansible.vagrant
hostname: mydomainclient
domain_admin_user: [email protected]
domain_admin_password: password123!
domain_ou_path: "OU=Windows,OU=Servers,DC=ansible,DC=vagrant"
state: domain
register: domain_state
- win_reboot:
when: domain_state.reboot_required
Install IIS Server and Set the Default template
win_feature: name: Web-Server state: present - name: Deploy default iisstart.htm file template: src: iisstart.j2 dest: c:inetpubwwwrootiisstart.htm
Create a Custom Directory Structure
- name: Create directory structure win_file: path: C:windowstools state: directory
Create a local user account:
name: create local user
win_user:
name: '{{item.name}}'
password: '{{item.password}}'
groups: LocalGroup
update_password: no
password_never_expired: yes
As you can see this is only scratching the surface but allows performing very mundane labor intensive tasks very quickly and efficiently.
Takeaways
The process to Bootstrap Windows Server Configuration with Ansible Playbooks is easily accomplished by just a few steps. Laying out the directory structure so that you can organize server roles and tasks makes keeping things straight much easier. The prebuilt windows modules for Ansible make things extremely easy so you don’t have to reinvent the wheel for Windows Server configuration. More Ansible goodness to come. Stay tuned.