Suricata vs Snort: Which is the best IDS?
This post will look into a detailed comparison between Suricata vs Snort security solutions and look at their architectures, capabilities, community support, and technical nuances of network intrusion detection and threat detection.
Table of contents
- What is Snort?
- Performance
- Security
- Supported Platforms
- Effectiveness
- Community and Support: Snort vs Suricata
- Rule-Based vs Anomaly-Based Detection
- Anomaly-Based Detection: Snort vs. Suricata
- Installing Suricata in pfSense
- Installing Snort in pfSense
- Intrusion Detection and Prevention Systems
- Wrapping up
- Other posts you may like
What is Suricata?
Suricata is a solution developed by the Open Information Security Foundation that has a lot of great features. It is known for its multi-threaded architecture. This architecture has been something that it has had longer than Snort’s. With this, it can analyze network traffic and manage rule sets for detecting and mitigating potential threats.
The multi-threaded architecture makes sure efficient processing of network packets can happen in the system. It helps the system manage and analyze network traffic with good performance and it also provides strong defenses against malware with the rules that Suricata uses.
Learn more about Suricata here: Home – Suricata.
What is Snort?
Snort is a solution developed by Sourcefire (now a part of Cisco). It has been name that most know in network security for decades providing intrusion detection and prevention in different types of network environments.
It has a rule-based detection and supports many protocols that have enabled businesses to protect their networks against known threats effectively.
Previously Snort was a single-threaded architecture. However, as of Snort 3.0, they have introduced multi-threading architecture. This used to be a benefit of Suricata only, but now this brings Snort up to the performance levels of Suricata.
Snort rules have been widely adopted and are supported by an active community. However, high-throughput network scenarios have questioned the system’s age and performance.
Learn more about Snort here: Snort – Network Intrusion Detection & Prevention System.
Snort and Suricata as IDS and IPS solutions
Suricata vs Snort are both known for their comprehensive rule set and reliable performance in intrusion detection. It has been a staple in many organizations in existing security systems, helping to mitigate known threats.
Both Snort and Suricata bring unique capabilities to the table and the ability to manage high-throughput traffic with their multi-threaded architecture. Both have free and paid rulesets as well.
Performance
Performance with both are on par with one another. Both now offer multi-threading performance that leads to faster packet processing compared to single-threaded systems. In previous comparisons, with Suricata vs Snort, with Snort versions prior to 3.0, this was a win for the Suricata camp. However, no longer. Single-threaded apps can be limited in performance in high-throughput scenarios.
Both Snort and Suricata are reliable and effective in various environments due to their extensive rule set and protocol analysis capabilities.
Depending on your network traffic and security needs, either solution may perform well in your environment. Extensive testing is needed to understand how each will perform in each case.
Security
With their extensive rulesets for both platforms, Suricata and Snort, both are able to effectively identify and stop modern malware variants.
As mentioned earlier, they both have open source and community rulesets and also paid rulesets that are developed by internal teams. The open rule set of Suricata seems to have an advantage of having more rules available than Snort. However, Snort is widely known for its effectiveness in this area.
Supported Platforms
Suricata and Snort are widely supported, including various UNIX-based systems and Windows. However, due to its modern architecture, some users might find Suricata easier to deploy and manage across different platforms. However, in systems like pfSense, installing and using either is extremely easy as we will see below.
Effectiveness
Both are effective. Each solution features continuous updates to its rule set to address emerging threats. Their ability to integrate with other security tools and adapt to different network environments makes them powerful solutions for network security.
Community and Support: Snort vs Suricata
Snort and Suricata both have strong communities contributing to the rule sets, providing support, and sharing insights on optimizing the respective IDS/IPS for different network scenarios. Snort has a community that has been active for longer than Suricata. This leads to a vast community of snort rules that are available.
Suricata, is more of a newcomer between the two, but it has gained traction quickly with security professionals and organizations. Again, its multi-threaded architecture made it super appealing to most. The Suricata community, although it hasn’t been around as long, is active and contributes to the available rulesets.
Rule-Based vs Anomaly-Based Detection
Suricata and Snort both offer rule-based detection, which means they rely on predefined rule sets to identify and stop potential threats in network traffic. However, rule implementation can impact how efficient each is in terms of the IDS/IPS capabilities, especially considering the dynamic nature of cyber threats.
Surricata vs Snort: File extraction
Suricata can match on files from FTP, HTTP and SMTP streams and log these to disk for further review. Snort has the “file” preprocessor that is similar, but it is noted to be experimental and development of it has been stagnant for years. This has been noted as something you shouldn’t rely on for a production environment.
Anomaly-Based Detection: Snort vs. Suricata
Both can detect anomalies which means they can detect things that are out of the ordinary in the network environment which may indicate threats. Instead of relying on known signatures or patterns of malicious activity, it focuses on anomalies from norms or baselines.
Both Snort and Suricata incorporate anomaly-based detection, but their approach has distinct differences.
Snort’s Approach to Anomaly-Based Detection
Snort, being one of the earliest and most established intrusion detection systems, has evolved its anomaly-based detection capabilities over time. Note the following:
Baseline Establishment: Snort first establishes a “normal” network behavior baseline over a period. This involves analyzing network traffic, understanding standard protocols used, data transfer rates, connection frequencies, and other relevant metrics.
Threshold-based Alerts: Once the baseline is set, Snort uses threshold-based alerts. Certain activities exceeding or falling below these thresholds trigger an alert. For instance, if there’s a sudden spike in data transfer rates or an unusual number of connection requests, Snort would recognize this as an anomaly.
Protocol Analysis: Snort also employs protocol analysis for anomaly detection. By understanding how specific protocols typically operate, Snort can identify when these protocols behave unexpectedly, indicating potential malicious activity.
Suricata’s Approach to Anomaly-Based Detection
Suricata, the newer of the two has very effective anomaly-based detection as well:
Advanced Baseline Profiling: Suricata establishes a baseline of normal network behavior and continuously updates this profile. This dynamic profiling allows Suricata to adapt to changing network conditions and behaviors, making its anomaly detection more resilient to evolving threats.
Machine Learning Integration: Some implementations of Suricata have experimented with integrating machine learning models. These models can predict and identify anomalies more accurately by learning from vast network data over time.
File Extraction and Analysis: Suricata can extract and analyze files from network flows for anomalies. This feature is handy for detecting threats embedded in files or documents that might be transferred across a network.
Extensive Protocol Support: Suricata supports various protocols and can detect anomalies in various application layers. Its comprehensive protocol support means that it can identify unusual behaviors in more areas of network traffic than systems with limited protocol support
Installing Suricata in pfSense
Let’s look at installing the Suricata module in pfSense as an example of a network solution where you can implement it. It is as simple as navigating to the Package Manager > Available Packages and searching for “suricata. Click Install.
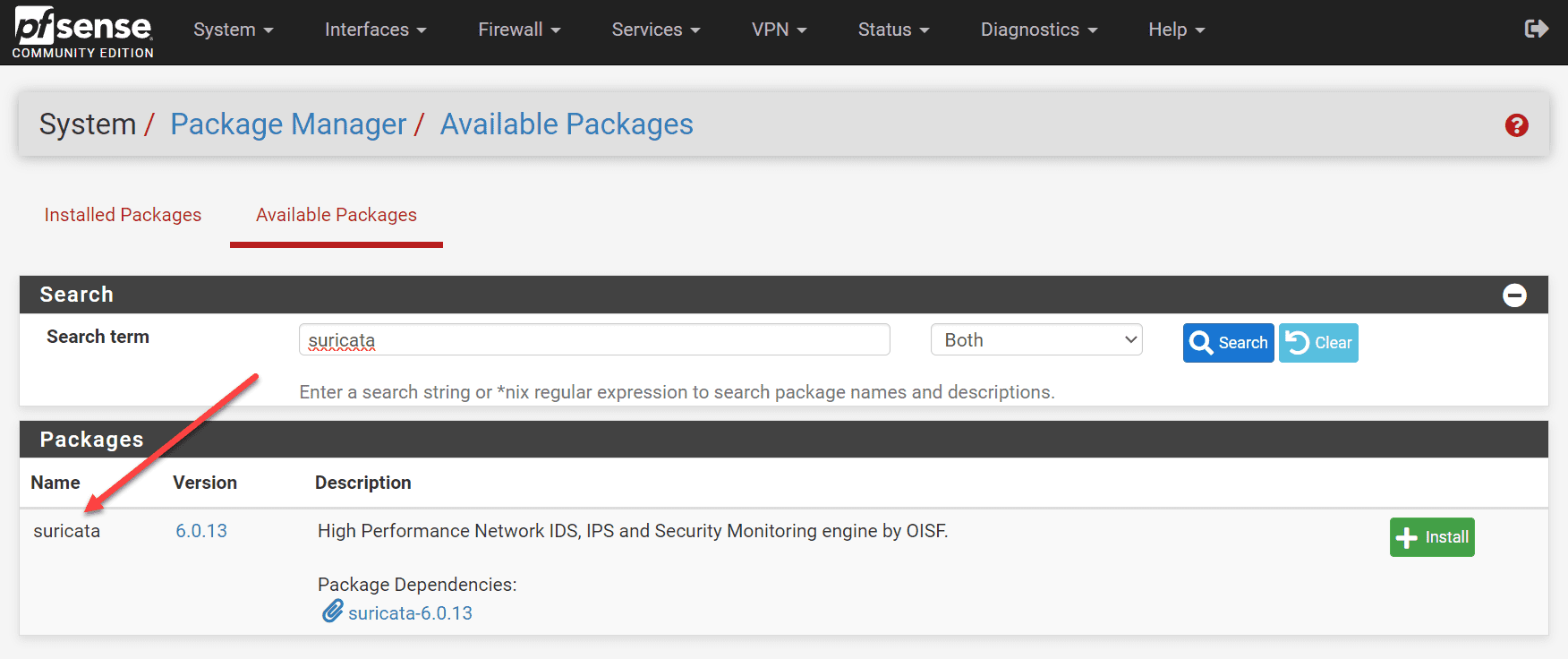
Confirm the installation.
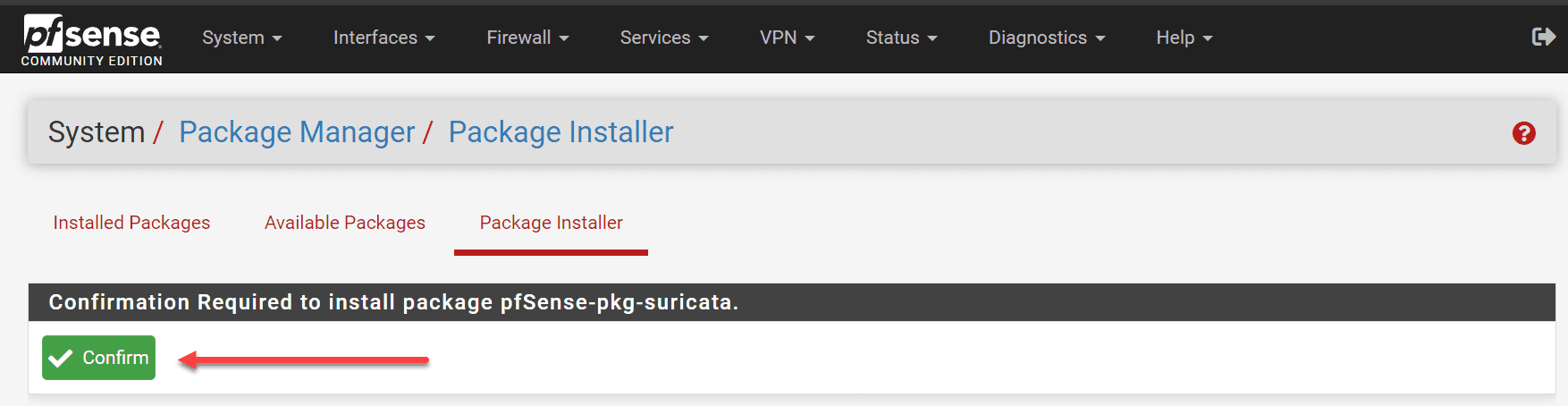
The installation of Suricata is successful.
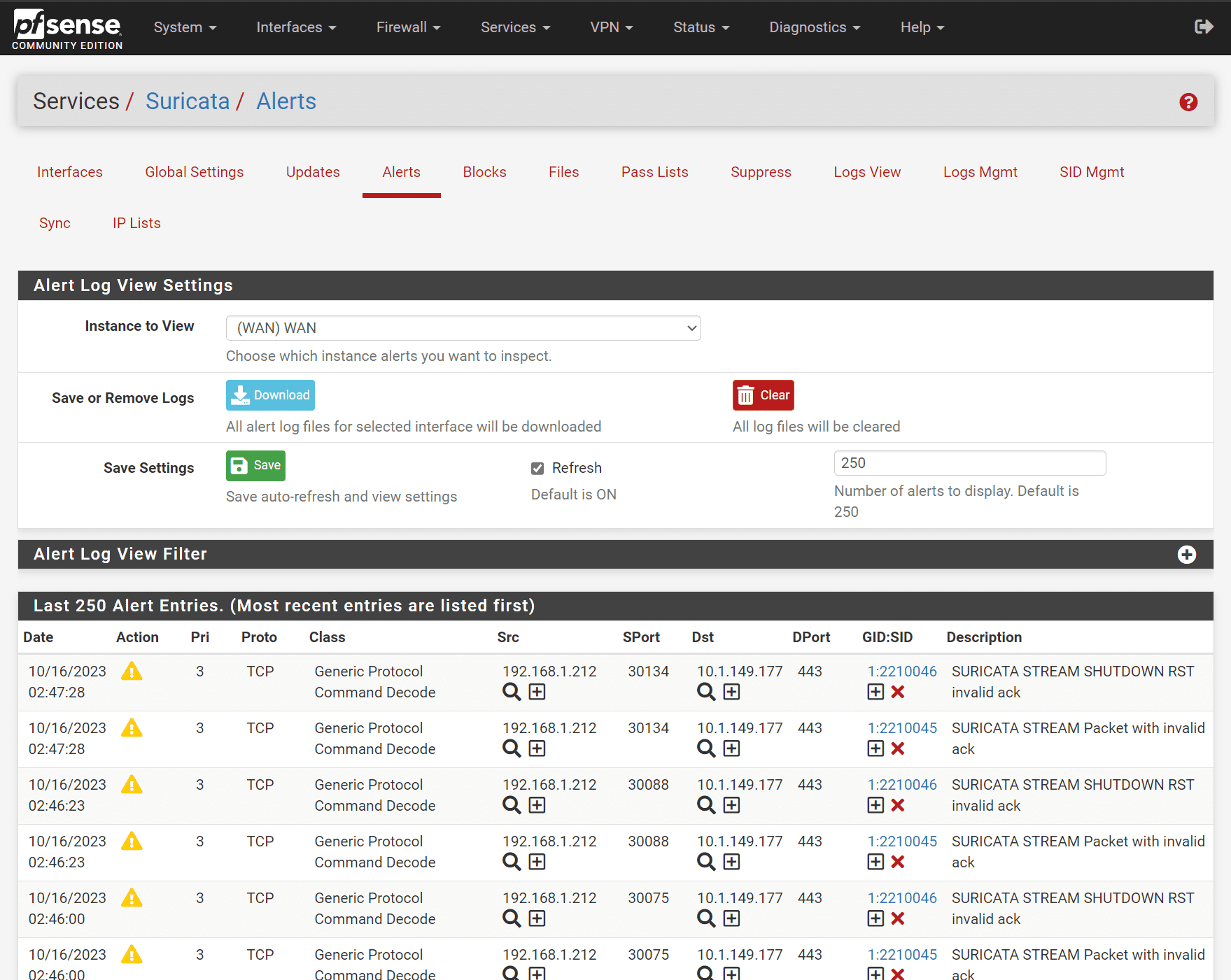
Looking at generated alerts in pfSense suricata. Below, you see alerts generated in the Suricata alerts tab in pfSense.
Installing Snort in pfSense
The process for installing Snort in pfSense is the same. Navigate to Package Manager > Available Packages and searching for “snort”. Click Install.
Confirm the installation.
The installation of Snort is successful.
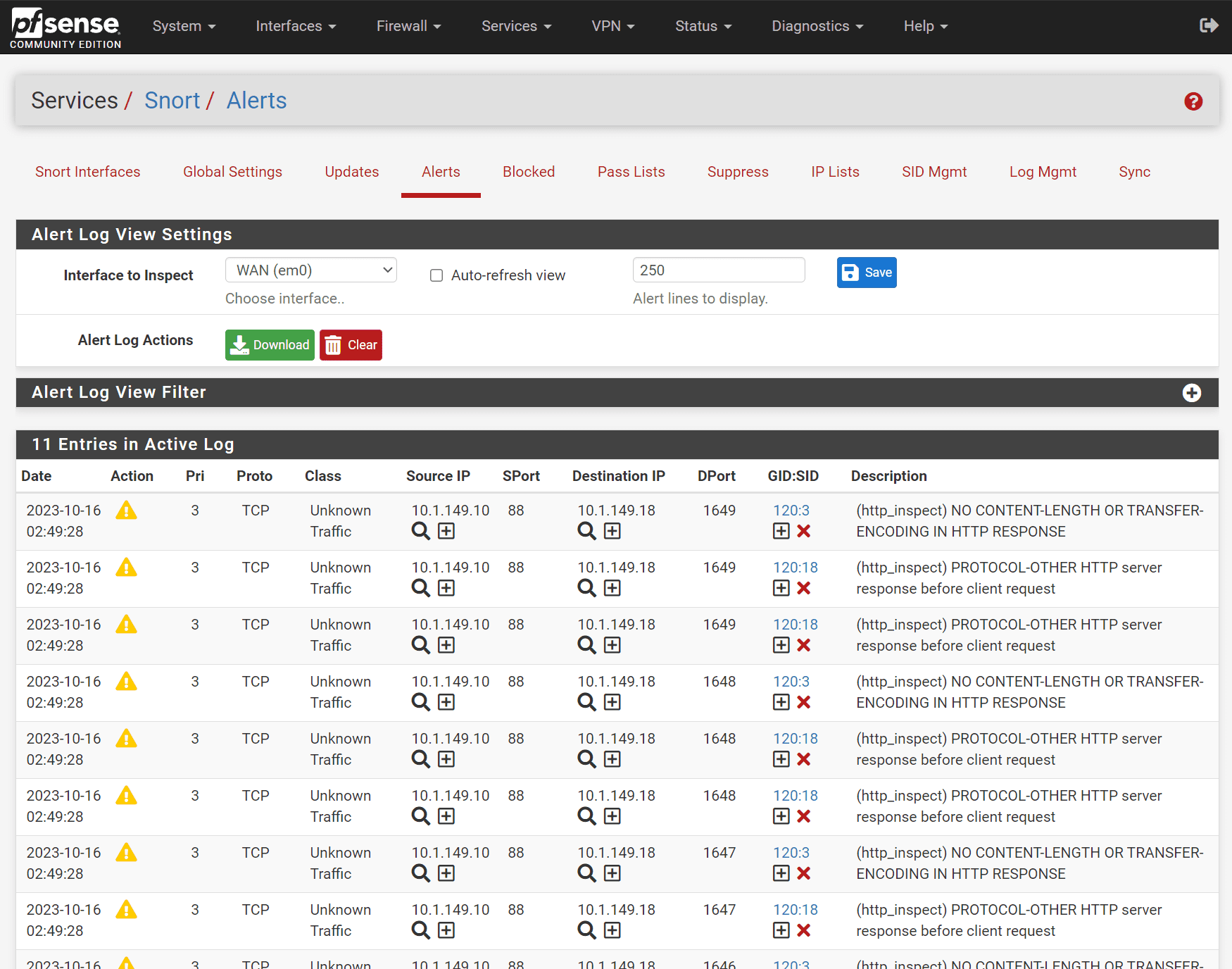
You can see the alerts generated in the Alerts tab for Snort in pfSense.
Intrusion Detection and Prevention Systems
You may have heard of Intrusion Detection Systems IDS and Intrusion Prevention Systems (IPS) when reading about firewall solutions or other security solutions.
Both are important in protecting systems against malicious traffic and threats. What are they exactly?
Intrusion Detection Systems
Intrusion Detection System, or IDS, monitors the environment for possible threats based on established rules and baselines. IDS focuses on recognizing and generating alerts for administrators about suspicious activities. IDS uses two main detection techniques, including signature-based detection and anomaly-based detection.
Signature-based IDS uses a specific rule set to scan network traffic, identifying known threats by matching data patterns or signatures.
Anomaly-based IDS, on the other hand, identifies potential threats by detecting unusual or unexpected patterns in network traffic, which could indicate malicious activity. Many of these leverage machine learning and other new technologies for behavior detection.
Intrusion Prevention Systems
Another system, Intrusion Prevention Systems (IPS) is used to not only in detecting threats but also taking actions against those threats. An IPS works to prevent threats from getting into the network in general.
This also protects the network from intrusion. It uses various detection and prevention techniques to analyze network traffic and enforce policies safeguarding the network’s security and integrity.
Wrapping up
Running intrusion detection systems and intrusion prevention systems IPS solutions are essential to protecting your network from known and unknown vulnerabilities and attacks. Suricata and Snort are two very good IDS IPS solutions well-known and respected in the community for their capabilities and features.
They are both found in solutions like pfSense that allow installing them easily as add-on modules. They have healthy community support, and you will find many great resources for each one around the net. The great thing about pfSense and other firewall solutions is that you can run both and test each one to see which delivers the best results in your environment.