Easy Windows Server Just In Time Administration JIT
One of the core pillars of good security with Windows Server is role-based access and least privilege access to resources in your environment. One of the newer buzzwords with security related to your Windows Server environment is called Just in Time administration (JIT). If you have ever taken a look at how to set this up in a native, purely Windows Server way, it is very complicated. It requires setting up a bastion forest simply as a resource forest for the JIT administration requirements. This is no insignificant task. Is there an easy Just in Time administration for Windows Server JIT, including 2016 and 2019? Let me introduce you to a product that can greatly ease the pain and burden of keeping privileged access under control in your environment. It is Securden’s Privileged Access Manager. Let’s take a look at how Just in time administration can easily be achieved using the Securden solution.
What is Securden Privileged Account Manager (PAM)?
When managing and administering privileged access in your environment, it is difficult to keep up with who has access to which resources and what level of access they have.
Also, there are many important aspects of granting privileges in your environment such as keeping an audit trail, having approval chains, as well as apply Just in Time administration to permissions granted so these are revoked in an automated way.
Securden Privileged Account Manager helps to solve all of these challenges. It provides the following features for your environment:
- Account discovery – Discover all types of accounts including Windows, Linux, and Mac systems, devices, databases, and applications
- Ability to securely share admin accounts – You would never give a regular user the password to an admin account. However, Securden provides a way to share accounts without disclosing the password and audits the access and actions taken by individuals using shared accounts
- Protect SSH keys – Store SSH keys securely, track who are using them and create an audit trail
- Windows Account Management – You have the ability to manage Windows domain, service, and local accounts. Also, manage the dependencies of the accounts
- Manage application passwords – Also, manage application passwords to help eliminate hard-coded passwords or those that are historically embedded in config files, scripts, and other code
- Automatically randomize passwords – With PAM you have the ability to automatically randomize passwords of administrative, service, and application accounts periodically
- Secure Remote Access – Provide a way for users to have secure remote access without copying, pasting, or even knowing the account they are connecting as
- Grant access to third-parties – As an extension of the remote access capabilities, you can easily grant access to a third-party without them knowing the account they are given access to
- Session recording – Do you need the ability to record the actions of a user with who a connection has been shared? Securden allows you to do this easily and record the activities of users who have been shared access to a resource
- Integrate wth your Active Directory infrastructure – You can connect Securden with your Active Directory infrastructure for user authentication, onboarding/offboarding
- Approval workflows – Securden allows you to easily setup approval workflows for users requesting access to resources
- Full audit and compliance reporting – Track all privileged access in your environment. This includes monitoring and reporting on privileged access activity
Easy Windows Server Just In Time Administration
As mentioned above, setting up privileged access management in Windows Server using native Microsoft technologies is very in-depth and challenging to configure correctly with many moving parts.
In my testing of Securden, setting up privileged access management to various resources that are given through an RDP connection was simple, easy, and the auditing capabilities were powerful. Let’s see how this works.
Installation and Requirements
I am not detailing here how to install Securden, however, it is basically a “next, next, finish” process on a Windows Server in your environment. I have it setup on a Windows Server 2019 VM in the lab.
The following are the requirements for an on-premises installation:
- Windows Server 2019
- 8 GB RAM and 50 GB hard disk space
- SQL Server 2017 (PostgreSQL is bundled with installation, however for larger deployment, it is recommended to use SQL Server)
- Web-interface supports Chrome, Firefox, Edge, Safari, IE 10 and above
Configuring Accounts
The first task you need to complete is onboarding “accounts” into Securden. Accounts with Securden includes endpoints, servers, and privileged accounts and their dependencies.
You can choose to automatically discover, manually add, or import from a file.
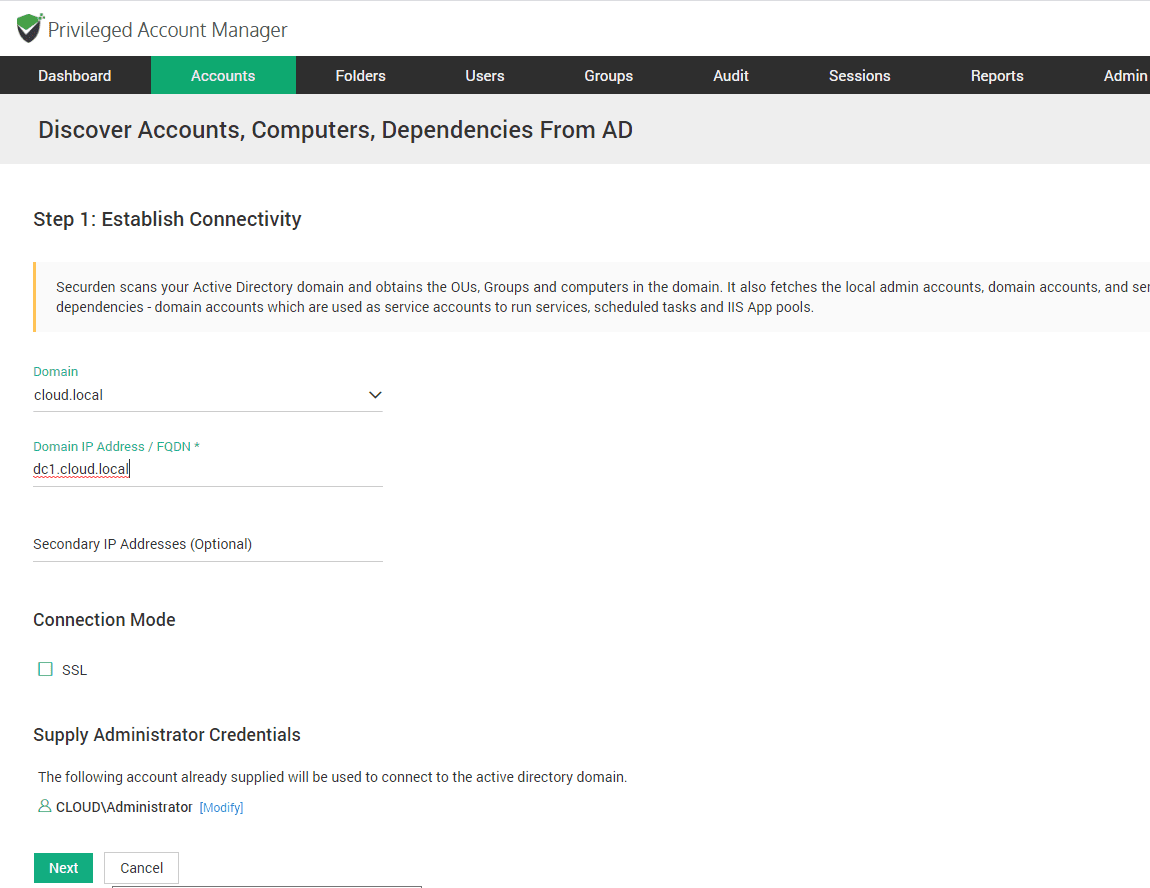
Here I am using the Active Directory import method which is the discover accounts option. You simply fill in your AD details on step 1.
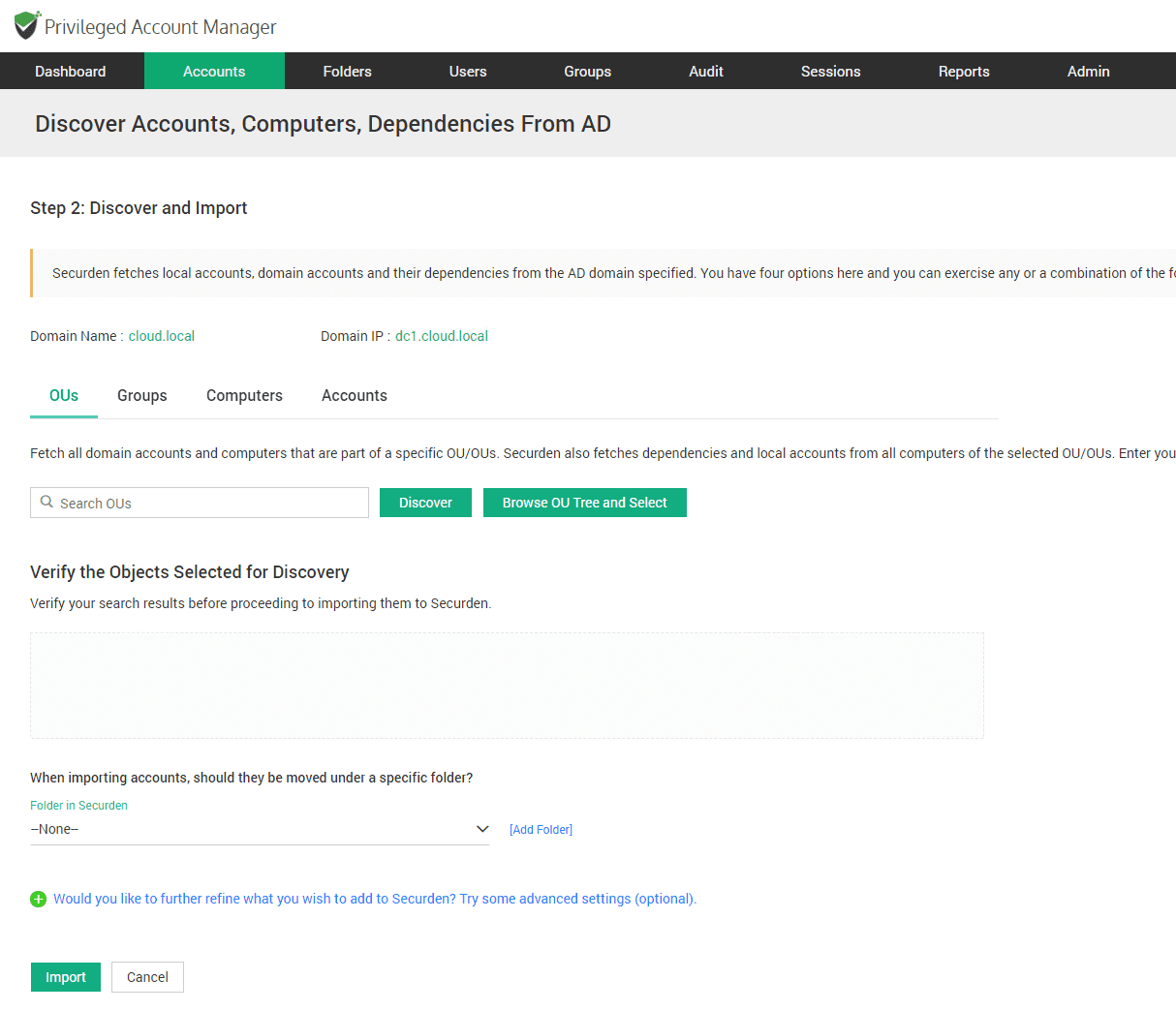
Next, you can define the scope of the discovery to a specific OU, or even specific account.
Configuring Privileged Access Management for Windows Server
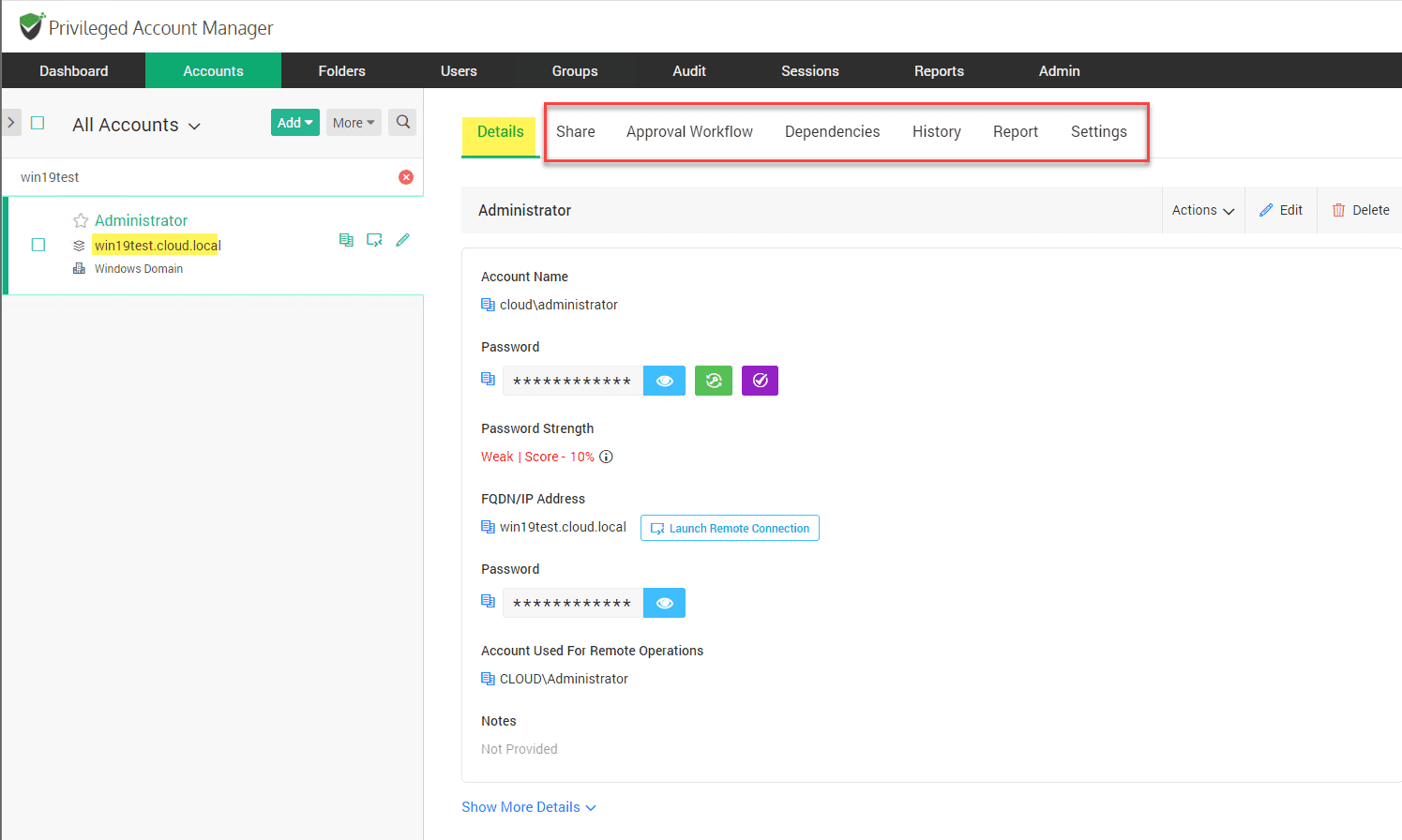
After you have discovered your accounts you will see a similar dashboard to the following. You will see the resource. Here I have a Windows Server 2019 test server. Note the options:
- Share
- Approval Workflow
- Dependencies
- History
- Report
- Settings
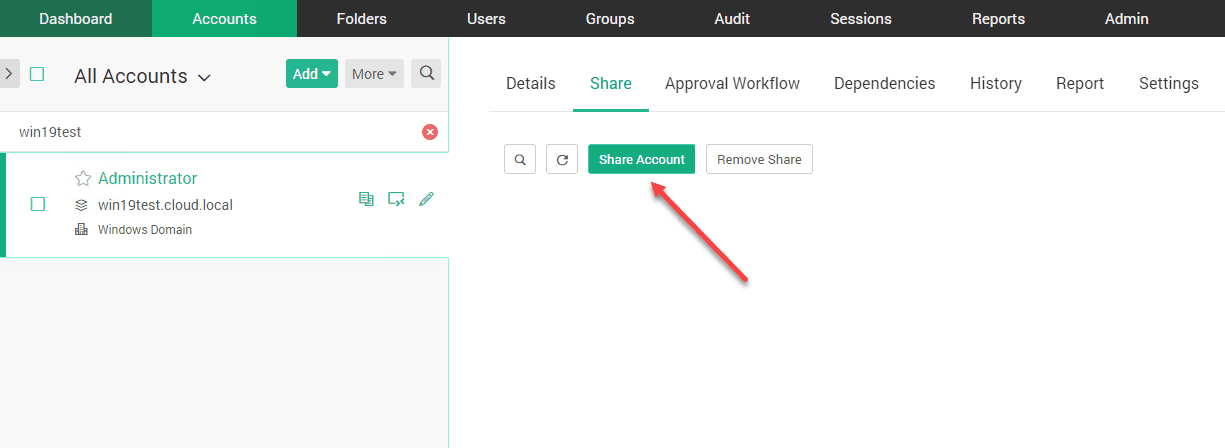
To grant Just In Time JIT administration access to a particular resource, you use the Share option. With Securden, you basically are granting a share of the user account that has permissions to the resource.
Click the Share Account button.
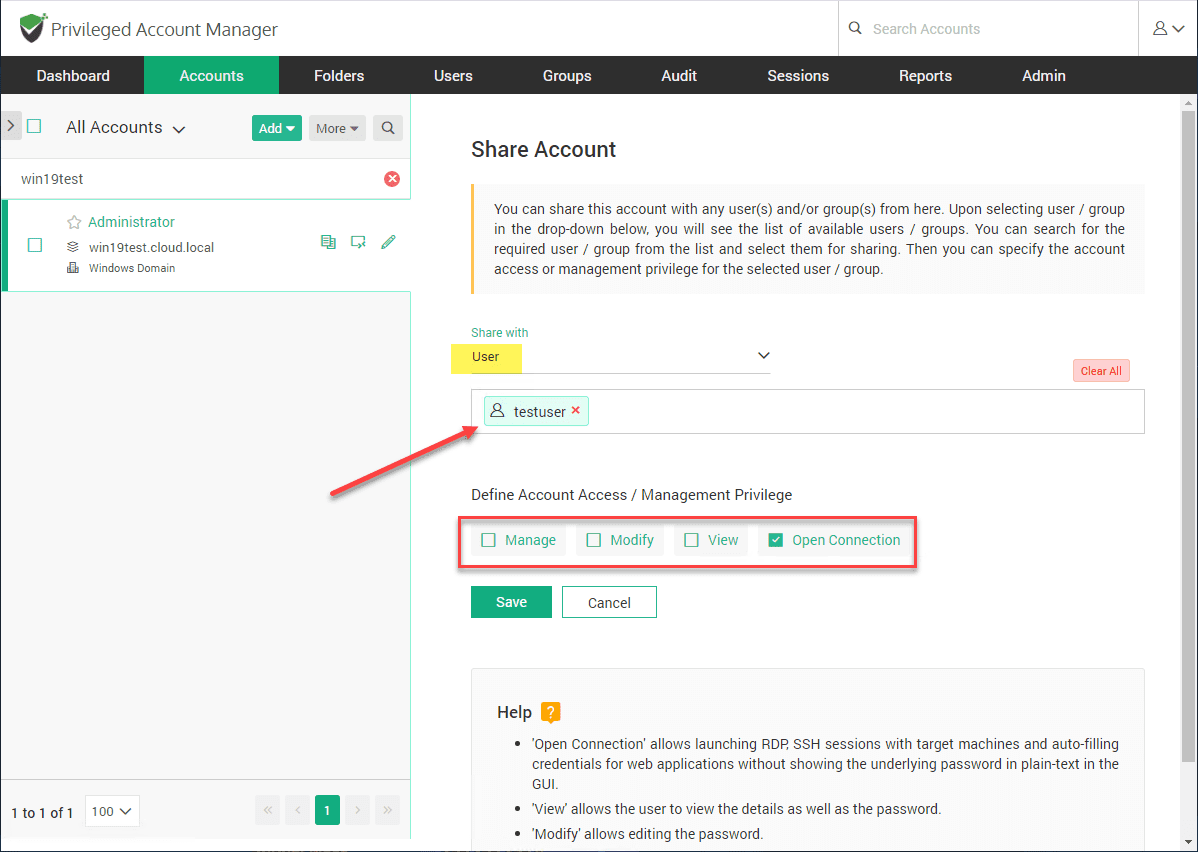
Select the user you want to share the account with. Also here, you set the account access and management privilege. This defines what access the user has to the account information. Do you want them to be able to view the password? Even modify account details? Or, do you simply want them to be able to open a connection as that user.
For most underprivileged users, you will most likely want to simply allow opening the connection. That is what I have defined here. This means they can’t see the password or other details.
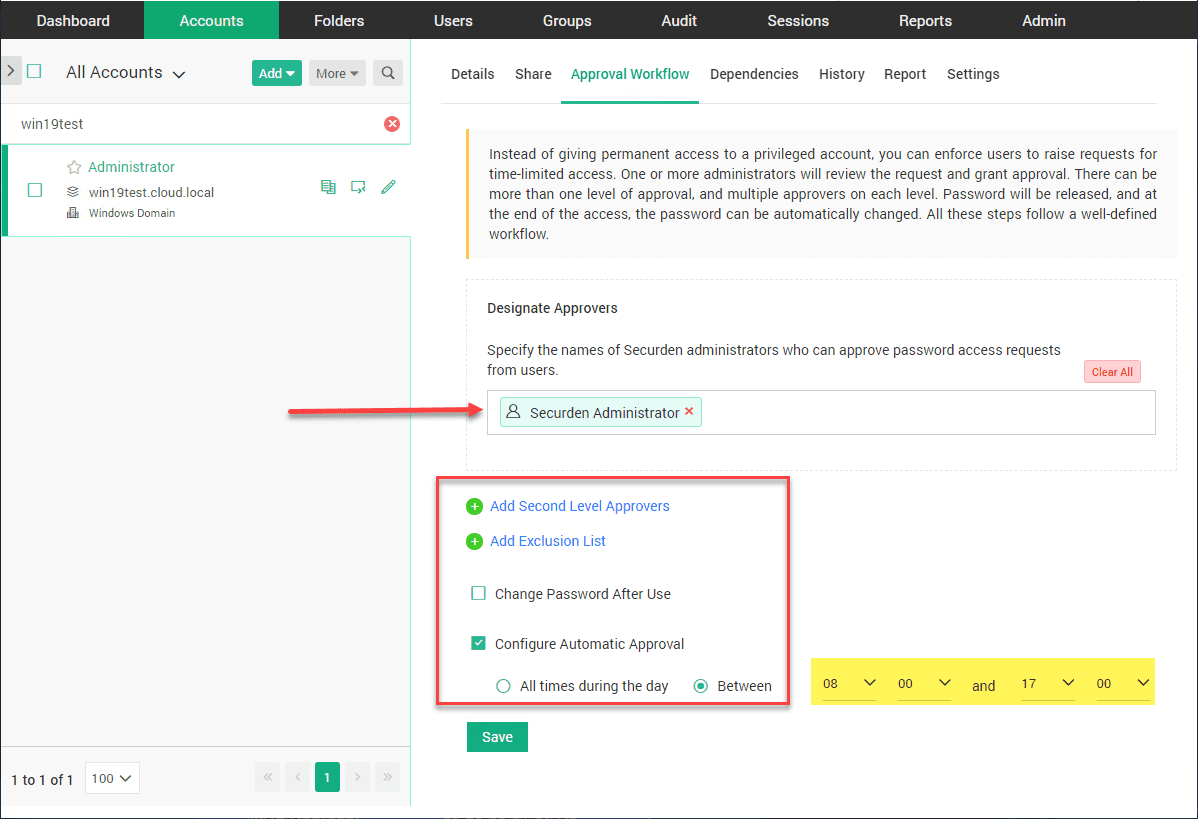
Another powerful feature is the Approval Workflow. This allows you the ability to setup approvals for granting access. You can setup a single level of approvals or even second level approvals.
Also, it is interesting as well you can setup Automatic approvals. This allows the approval to be automatic during specific time periods. If for instance you want it to automatically be approved from 8-5, you can set that up.
Testing Just In Time Management
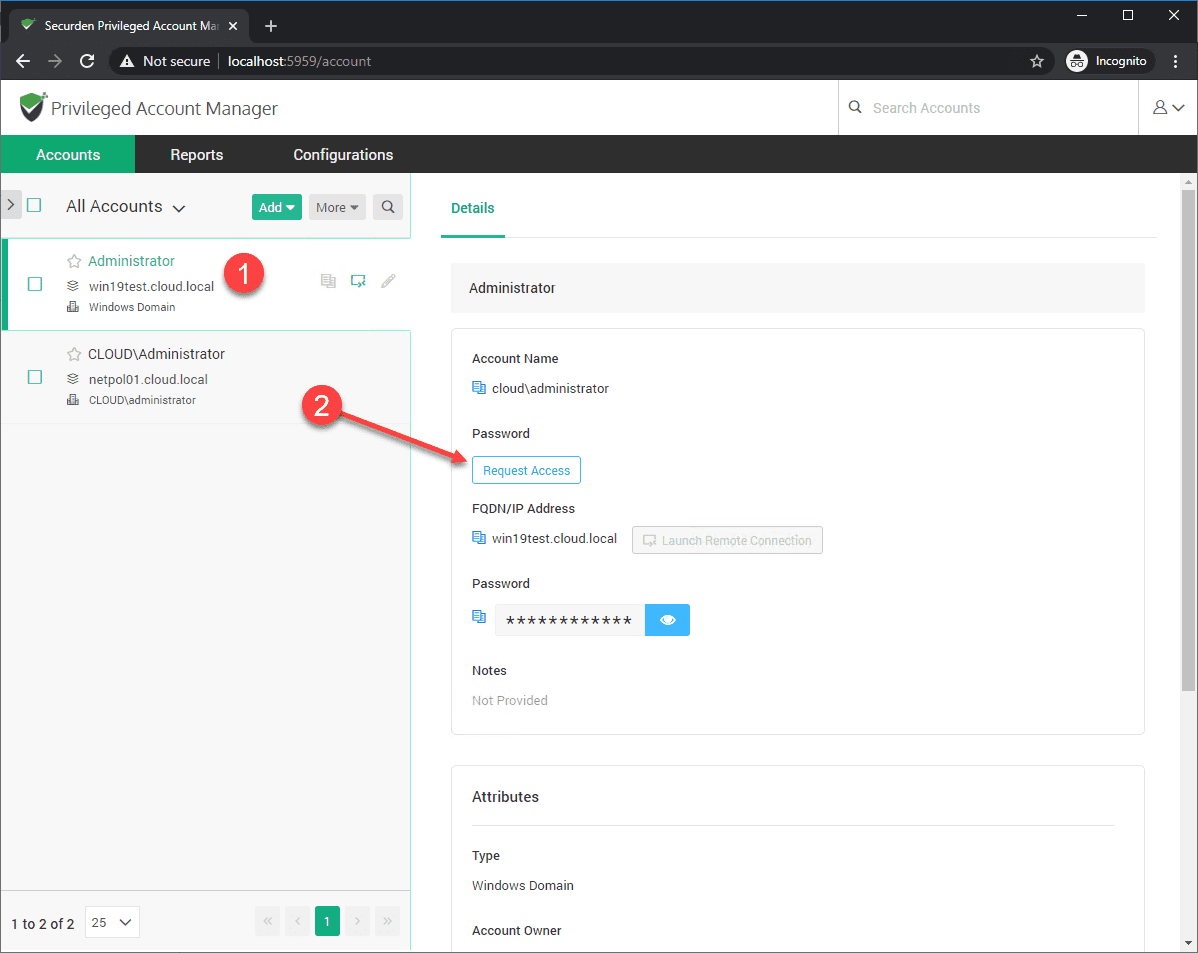
Now, let’s login as an underprivileged user that we have shared account access with called testuser.
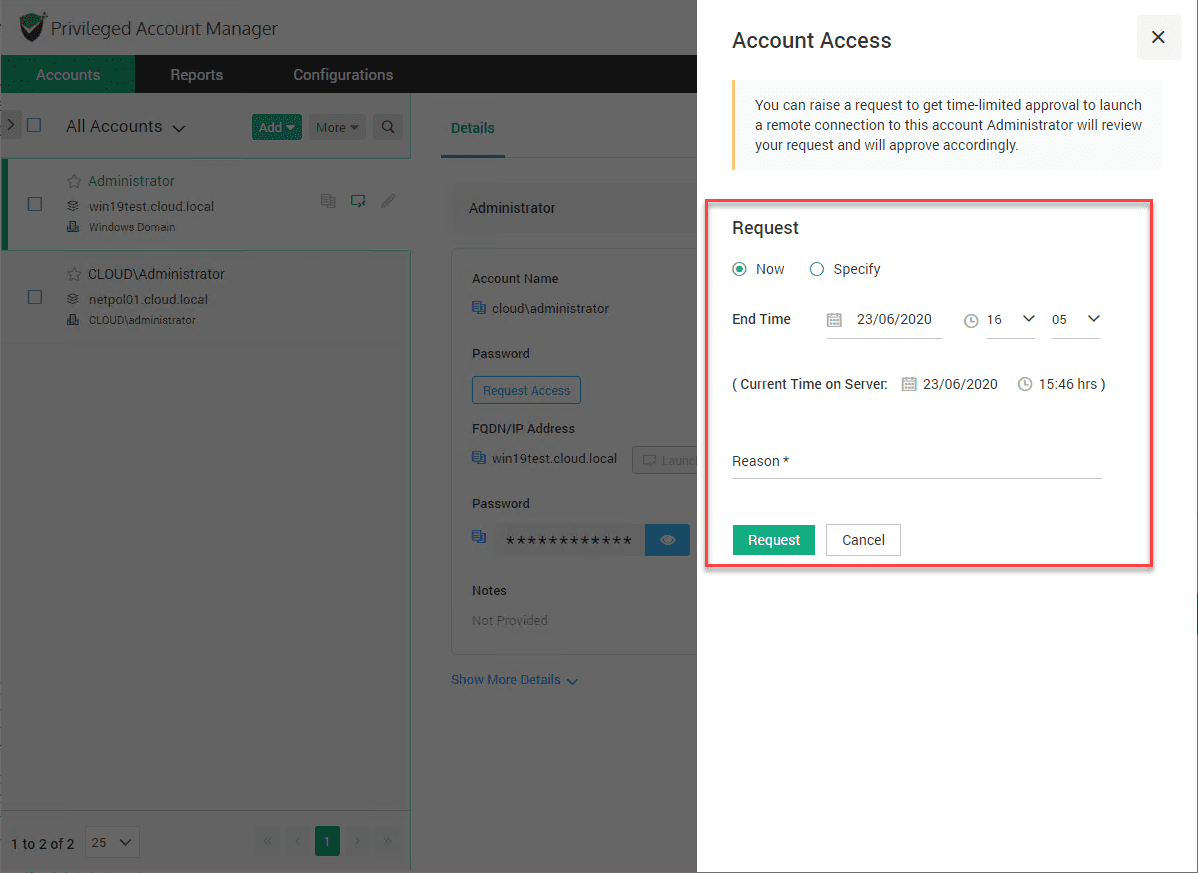
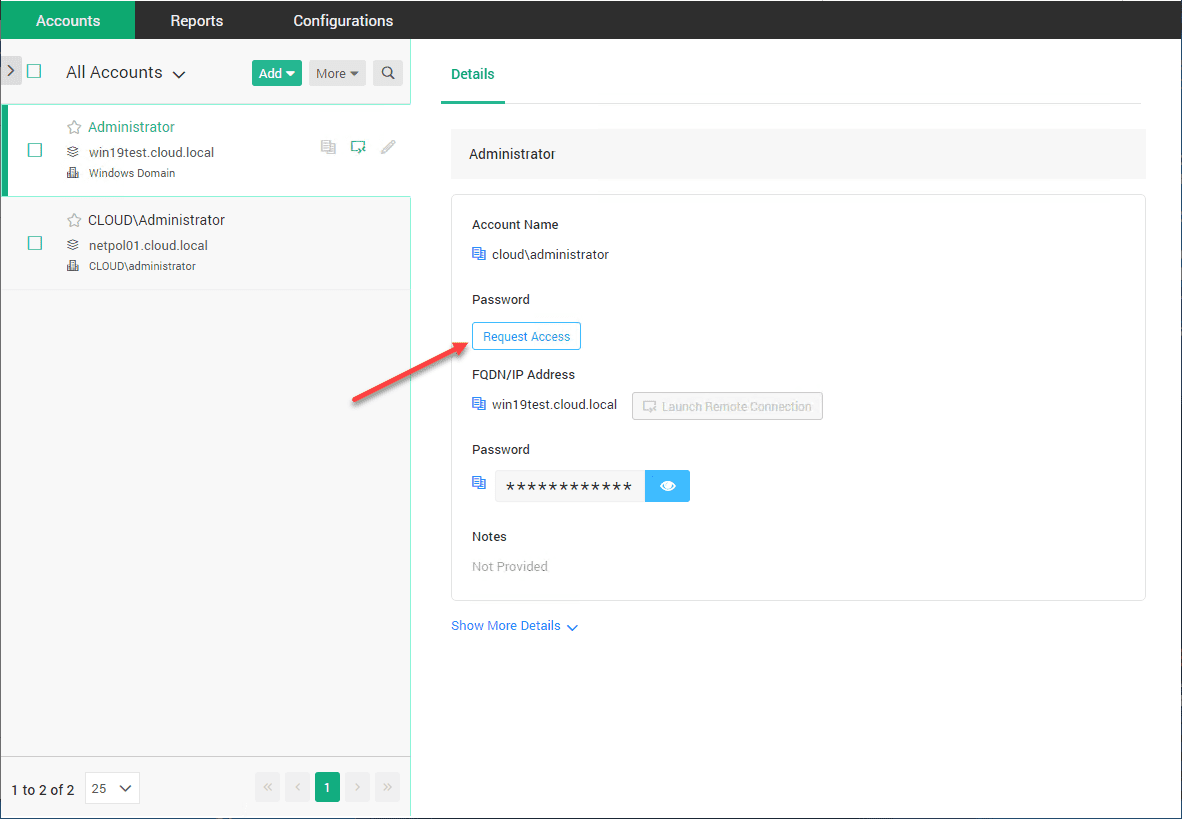
Note, testuser only sees resources they have been shared. One of the servers is the Windows Server 2019 server. The user then clicks Request Access.
This starts the process of requesting Just In Time access.
Next, they have to fill in the start time and end time for the access request. They also have the “reason” field to fill in. They click Request.
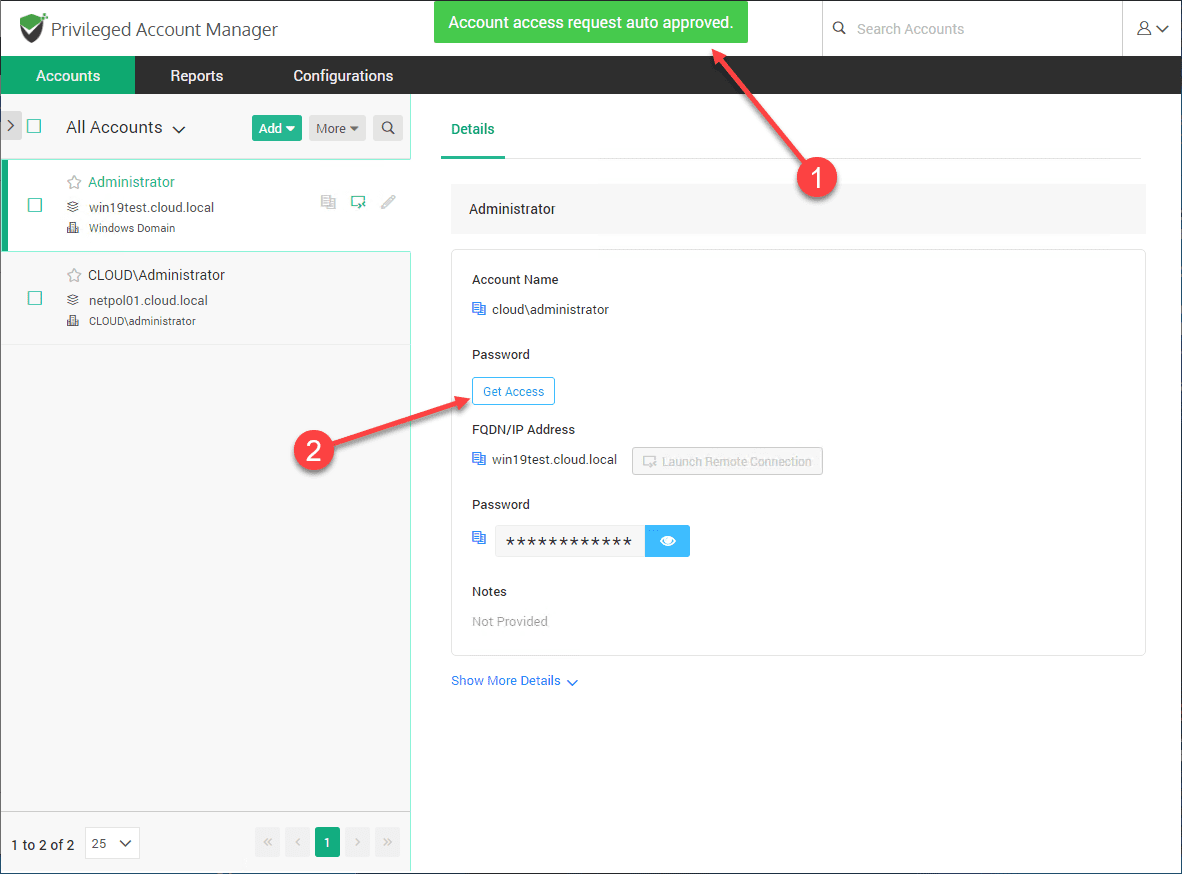
The next Request Access that is requested starts the approval process.
Note the automatic approval kicks in as it is during the time period specified. They click Get Access.
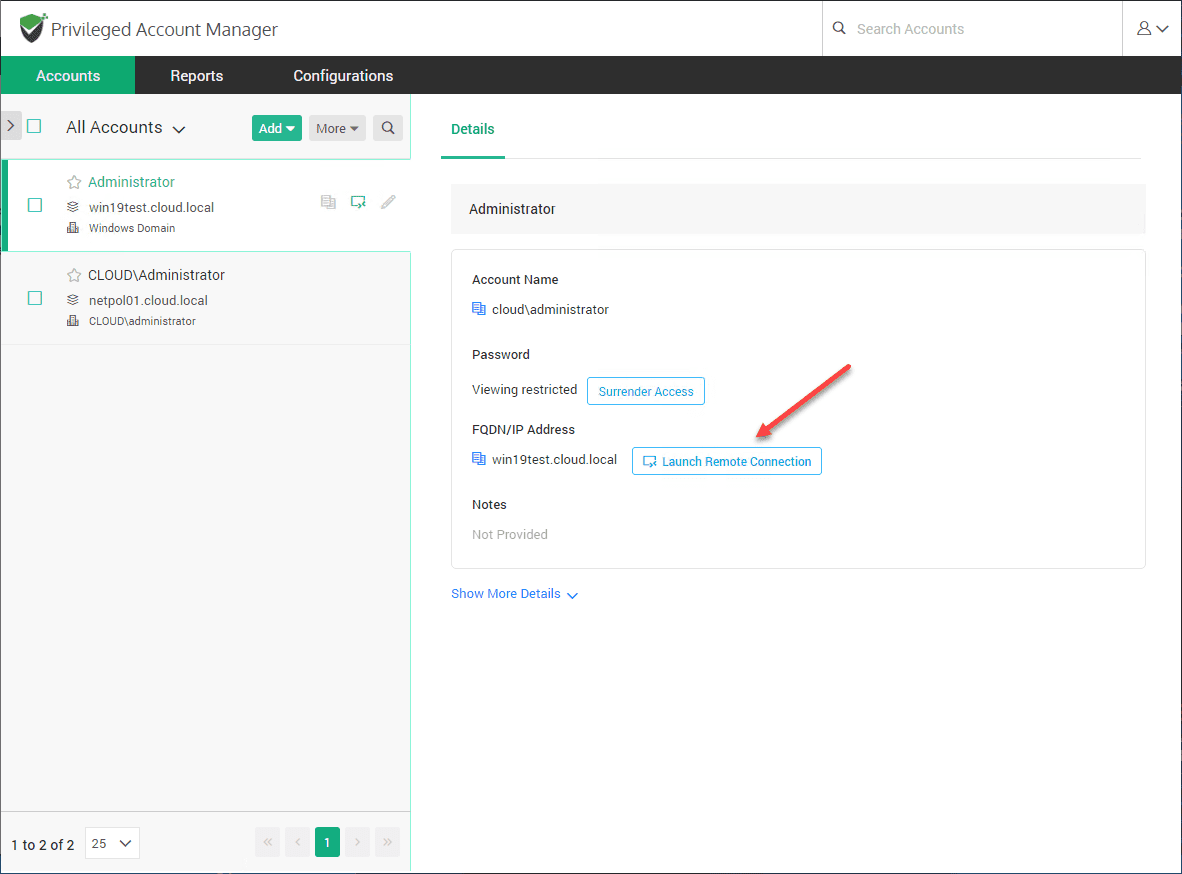
Now, they have access to Launch Remote Connection. Note they cannot see the password as View restricted displays for that field.
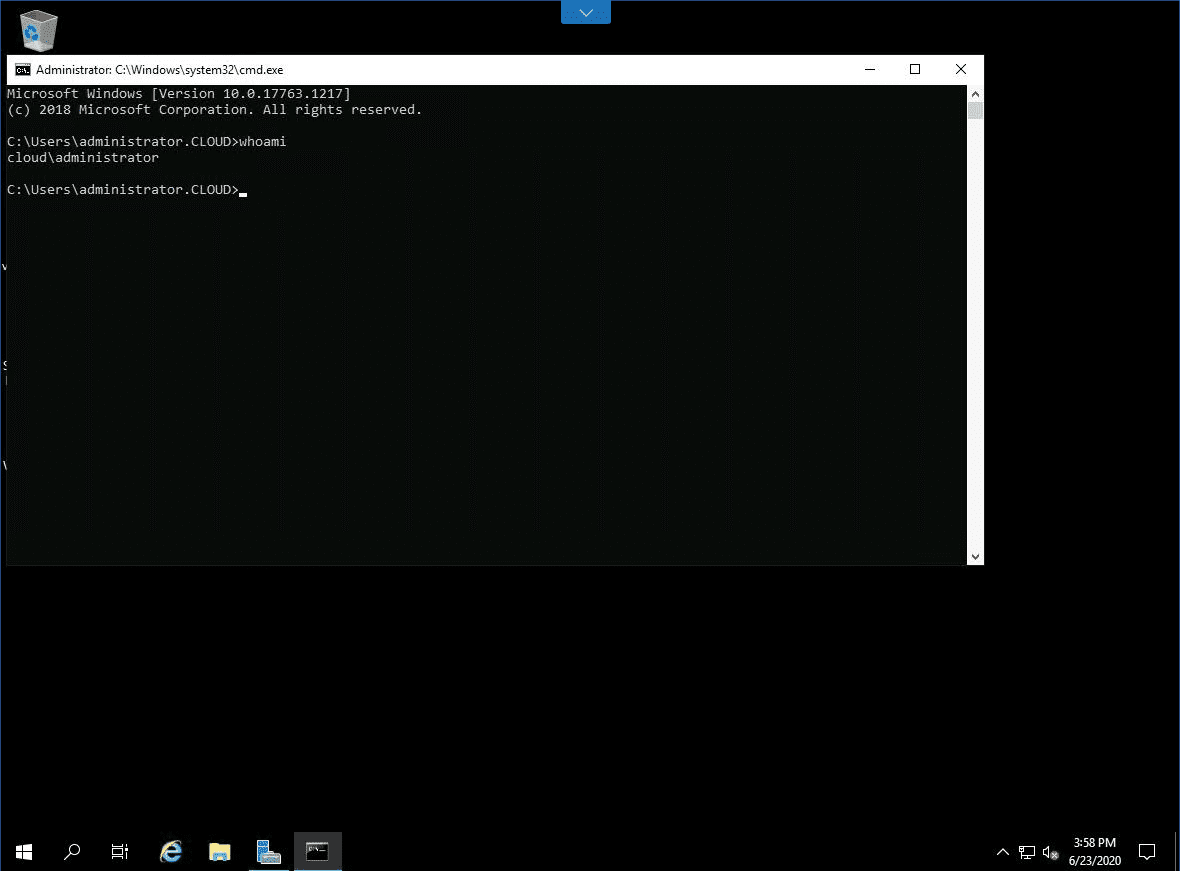
Let’s verify the user context they have with the connection. They are logged in as the domain administrator. Cool stuff! Even though the user has no knowledge of the account password, they are able to launch a connection as a privileged user.
As you can tell, the possibilities with this are endless. It allows effectively securing your environment with Just In Time administration across the board so that access to business-critical systems are secured in a way that locks down privileged access.
Wrapping Up
If you are looking for Windows Server 2016 or 2019 Just in Time JIT administration, Securden is by far one of the easiest solutions you will find to setup and hit the ground running with privileged access management in your environment.
Configuring native Windows Server JIT is not for the faint of heart and the solution is very challenging to configure correctly. In just a few minutes with the Securden PAM product, you can easily control privileged access in your environment.
Check out a fully featured trial version of Securden Privileged Access Management here.