Secure SSH with Public Key Authentication and Two Factor with Duo
If you want the ultimate in security for your SSH enabled Linux box that is sitting in the DMZ or in a 1-to-1 NAT scenario, you can basically have 3 factor authentication setup for your SSH enabled server by using public key authentication with a passcode, then using that in combination with two factor authentication. In my opinion the best two factor authentication service/app out there is Duo. With Duo you have the ability to send push notifications for two factor authentication to your mobile device and with the simple click of the green check box that pops up, you are logged in – simple as that. So by using what we stated above, the following has to be known or in possession of for access:
- The private key of the public/private keypair
- The passcode the private key is secured with
- The device that is paired using the Duo authentication service
First off, let’s go about seeing how we can setup public key authentication with our linux box. The test box I used was an Ubuntu 14.04 LTS server.
Public Key Authentication
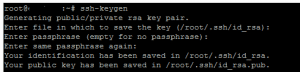
There are a lot of ways to go about getting the key pair generated, but the method that I prefer to use is to let the server generate the keypair, rename the public key file, move the private key from the server, and then use puttygen to convert the private key to a format that putty understands. In order to setup public key authentication on our server, we first run the following command to generate our key pair:
ssh-keygen ssh-keygen -b 16384 (maximum)
In the above command we can specify the key size with the “-b” switch, with 16384 being the maximum configurable size. The default size that gets created if the size is not specified is 2048. The key pair value/name is created in:
.ssh/id_rsa
Once the keys are created in the directory above, copy the private key to your client and delete the private key from the server (the file without the .pub extension). We only want the public key to exist on the server side and not both. Rename the .pub file to authorized_keys with no extension.
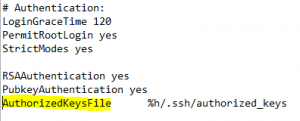
Alter your sshd_config file, found in /etc/ssh/ to use the authorized_keys file. The line is in the config already but simply needs to be uncommented:
At this point, we can restart ssh:
sudo service ssh restart
Using Puttygen we can now convert the openssl private key into a putty friendly format to use when authenticating.
- Load the private key that we copied from the server
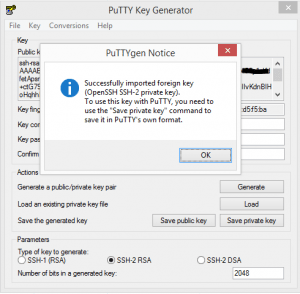
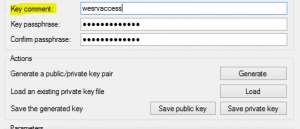
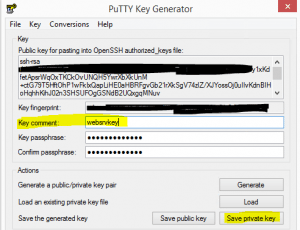
- Below we are changing the comment on the “key comment” as this is what is displayed when connecting to the server. Make the description meaningful.
- After you have altered the comment, choose to Save private key which saves the format into the .ppk file format that putty understands to use when creating a connection profile.
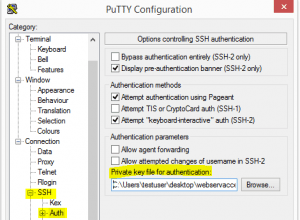
- Now point you putty profile to use the .ppk file you created
Duo Authentication
With the public key authentication key pair setup now completed, we move on to the Duo implementation. I am not going to reinvent the wheel here as Duo has excellent documentation on how to get this setup. Check out the detailed how to article on how to implement this.
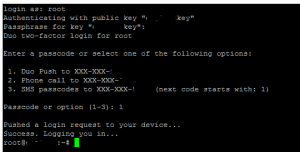
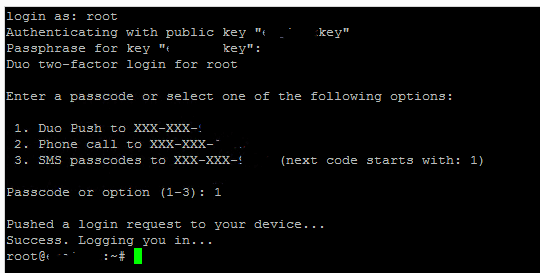
After you have everything setup, public key authentication, duo two factor push authentication, your login will look similar to the following and happen in this order:
- You are prompted for key password
- You will then be asked how you want to receive the Duo authenication
I am not sure about you all, but I feel much better knowing that to login, I have to be in possession of the private key, know the password to the key, AND have the push device in my possession to access the incoming Duo request —–AWESOME!