-
home lab

5 Proxmox Projects to Level Up Your Home Lab This Weekend
I am a huge advocate of project-based learning and I think a little extra time on the weekend if you have a few minutes or a couple of hours in the home lab can pay…
Read More » -

-

-

-
Latest articles
-
Storage
StarWind VSAN for vSphere Virtual Appliances
You may have been considering VMware vSAN for your ROBO or Edge environment, however, your budget constraints simply do not…
-
vRealize Suite
Upgrade to VMware vRealize Operations Manager vROPs 8.0
One of the tasks I have been wanting to get done in the home lab as a test bed for…
-
Windows 10
Windows 10 1909 Download Released New Features
Well, apparently the wait is over for Windows 10 version 1909 aka 19H2 as it appears it has been released…
-
Windows Server 2019
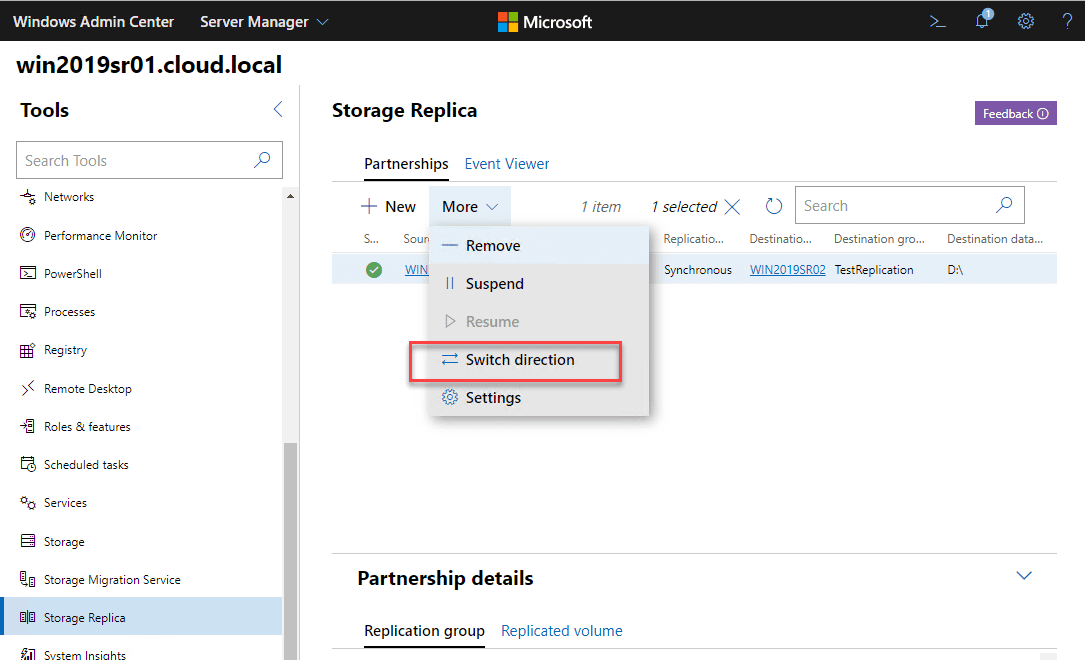
Windows Server 2019 Storage Replica Failover Process
In the previous post, we took a look at Storage Replica in Windows Server 2019 Features and Configuration. The new…
-
Windows Server 2019
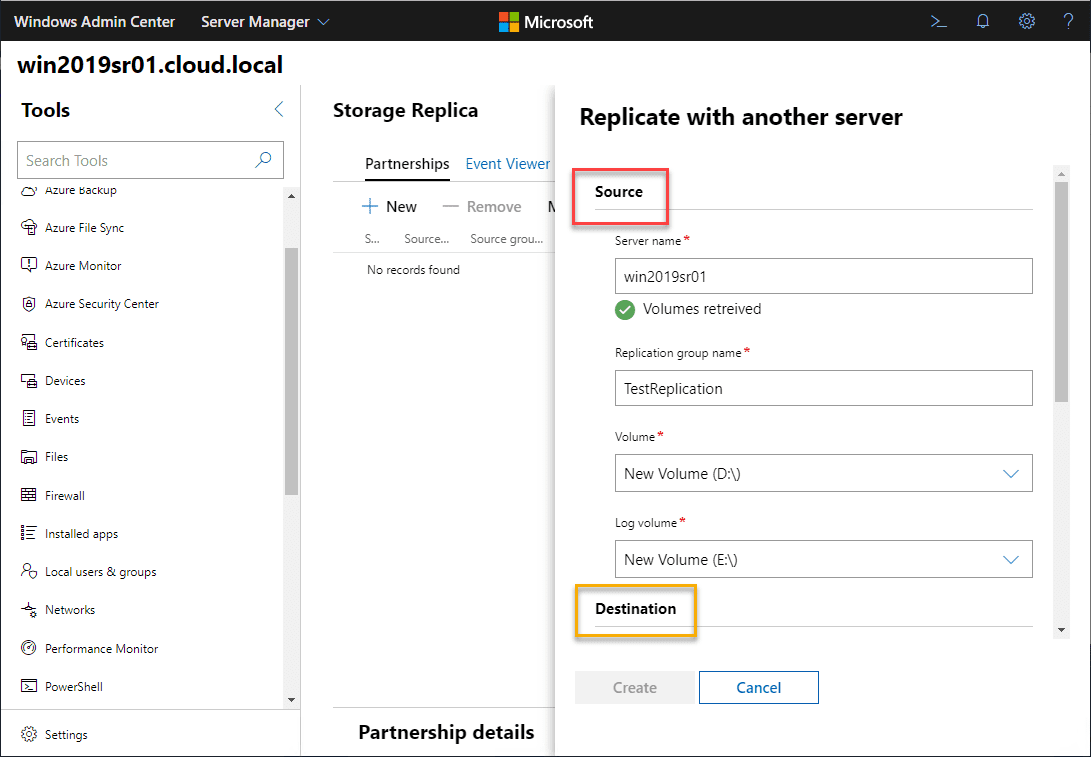
Storage Replica in Windows Server 2019 Features and Configuration
A capability that has been around for quite some time with Storage Area Network (SAN) devices is the ability to…
-
Backup Software

Best Practices for Protecting Your Data Center from Disaster
Your datacenter feels almost like a living, breathing thing with all the various systems and complexities involved in make your…
-
NSX-T
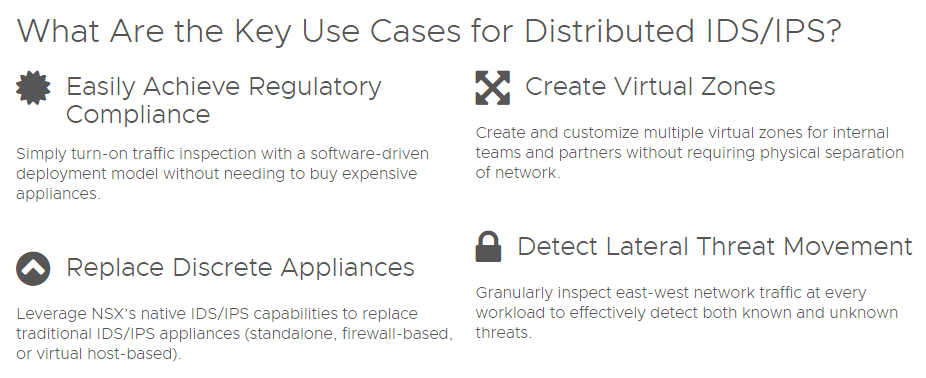
VMware NSX Distributed IDS/IPS Announced Features
VMware is continuing to strengthen their security position, tools, and solutions for offering top notch security to the enterprise. If…
-
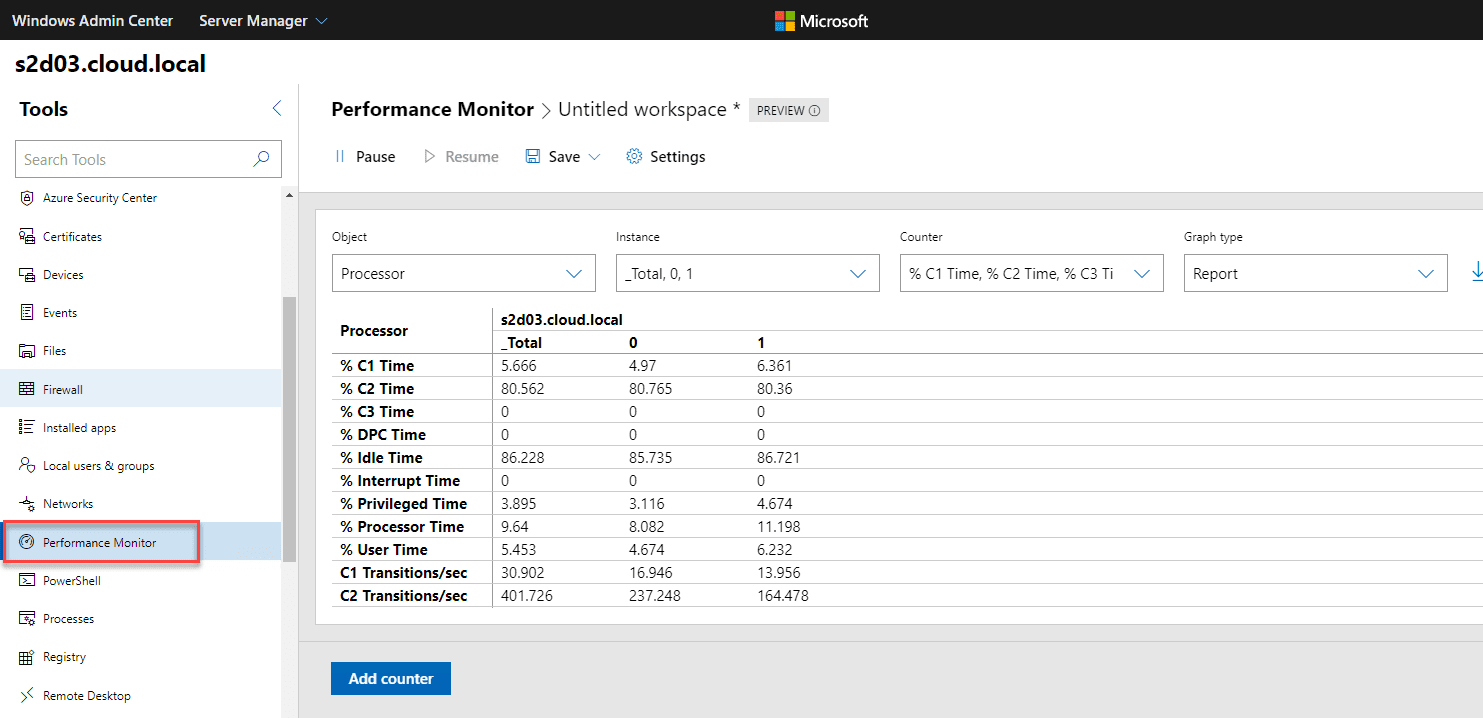
Windows Admin Center
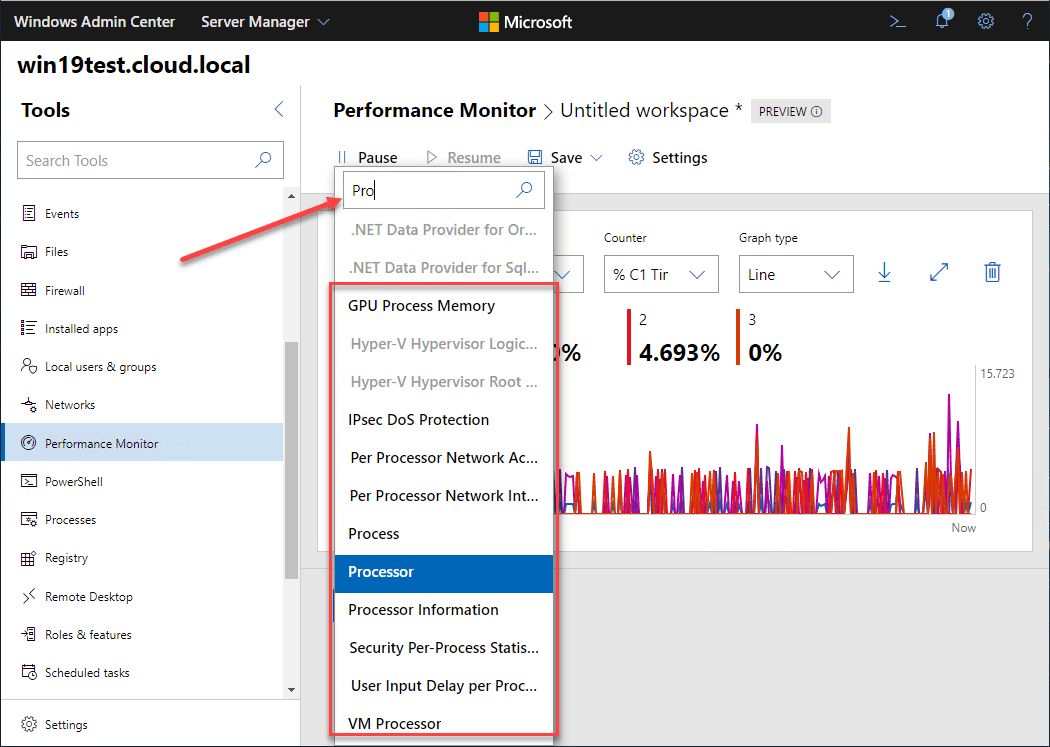
New Performance Monitor released in Windows Admin Center
It is the tool that we have all either loved/hated for years working with Microsoft Windows Server systems. It has…
-
Windows Admin Center
Windows Admin Center 1910 GA Download with New Features
Windows Admin Center is the de facto standard now for managing Windows Servers, HCI, Hyper-V, and bridging your on-premises environment…
-
vSphere 6.7
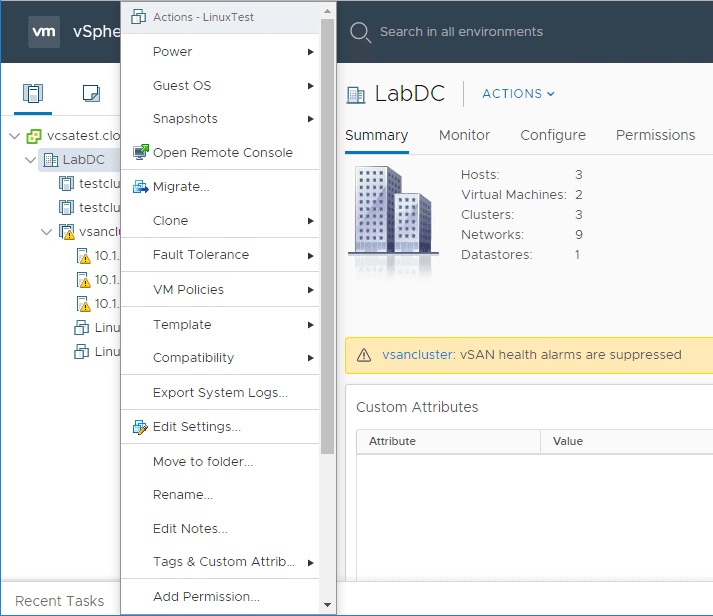
vSphere Client 6.7 Download and Features
One of the great features of the new vSphere versions since vSphere 6.5 is the vSphere Client. It has been…



