-
ActiveDirectory
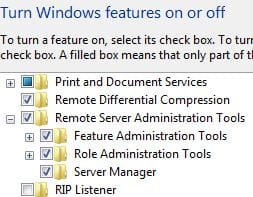
How to Install Remote Server Administration Tools Windows 7
If you are a system administrator who administers a Microsoft Active Directory environment, the Remote Server Administration Tools or RSAT is a must have to be able to quickly and easily manage your environment from a workstation. It is cumbersome…
-
Troubleshooting
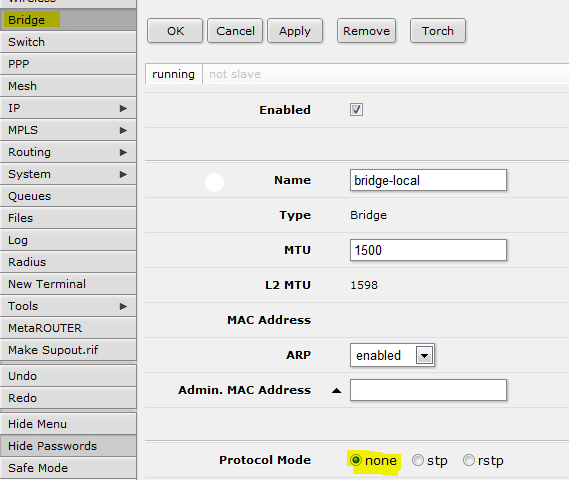
How to fix Mikrotik Router freezing edge switch
For those of you who work in the enterprise environment and are using Mikrotik Routerboard products, you may have run into a case of where plugging in the Routerboard AP freezes your edge switch (lights go solid, all network traffic…
-
Windows
Windows Server 2012 Release Candidate Datacenter Available for Download
On the heels of the latest news and download for the Windows 8 Release Preview ISO, Microsoft has released the next version of their server operating system now officially dubbed Windows Server 2012. Microsoft is touting this server OS to…
-
Computers
Looking for a great LED HD Monitor – LG Flatron E2411PU
If you are looking for a really great LED full HD monitor, then the LG Flatron E2411 is a great choice! The other day, we picked up a couple of these monitors from Newegg, and have been very impressed with…
-
Wallpaper
Free High Resolution Desktop Wallpaper for Download
If you are like me, you are always looking for great wallpaper content for your desktop. It makes our day to be able to have nice looking wallpaper as the backdrop for the work environment. It is difficult to find…
-
Exchange
Resolving Exchange 2010 Queue 4.2.0 ambiguous address error
If you have run into the message in the Exchange 2010 queue about delivery delayed or “will retry” messages with error message 4.2.0 and an ambiguous address message, we can actually pinpoint this problem to an Active Directory attributed called…
-
Mobile
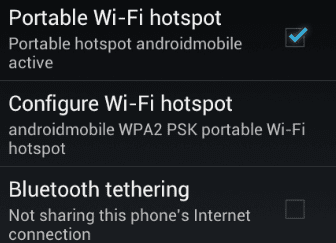
How to setup a mobile hotspot with Android and CM9
We have all been there, stuck in a location where there is no WIFI service and we desperately need to connect our laptop, tablet, or other mobile device to the Internet. Well, using one of the latest CM9 nightlies on…
-
Networking
How to setup Mikrotik 751 Router for home or office
Mikrotik makes great quality products that can do just about anything you would like them to do. The RB751 routerboard can be bought for cheap on the net and we can assure you that this little router can do WAY more…
-
Windows
How to correct reverse DNS issues
Most of the time people think of DNS as being the service that helps us to resolve a name to an IP address and that is certainly true, as without this service, the Internet as we know it could not…
-
Windows
How to use Windows Server Backup to backup files
Backing up files using the builtin backup utility in Windows Server 2008 R2 is really a piece of cake. We will take you through the steps in the WBADMIN.MSC interface as to how you would go about backing up file(s)…