10 Best Docker Containers for Security in 2024

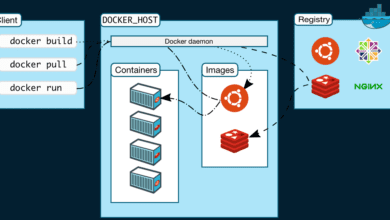
Many are embracing running containers as opposed to running a virtual machines instance for workloads. There are so many great Docker containers users can look at for many different use cases and applications. However, there are also excellent container security tool images and solutions we can use for Docker security and securing Docker container image configurations, and giving visibility to vulnerabilities in the context of containerization. They can also help sure of code quality for development (eliminate code smells – yes this is a real term) and help minimize the risk of bad code. This blog post dives into 10 of the best containers and container images to enhance your container security posture in 2024 as well as example Docker run and Docker compose code on your server platform.
Table of contents
1. SonarQube
SonarQube is a containerized security tool that definitely makes the list of best Docker Containers for security in 2024 with a free community edition that provides a first line of defense for your resources and service configurations. It gives you static code analysis, and helps to identify vulnerabilities, bugs, and code issues early in the development lifecycle for organizations. SonarQube can be integrated into your CI/CD pipeline and enables resolving issues with code and security before they reach production. All of these things help reduce the attack surface of your apps.
Learn more about Sonarqube and its integration here: https://www.sonarsource.com/.
Features:
- Supports 25+ programming languages
- Detects vulnerabilities, code issues, and potential bugs
- Offers various metrics for developers and their code quality and security
- Integrates with popular CI/CD tools
Docker Compose snippet:
version: '3'
services:
sonarqube:
image: sonarqube:latest
ports:
- "9000:9000" # SonarQube web interface
volumes:
- sonarqube_data:/var/sonarqube/data # Persistent storage for SonarQube data
volumes:
sonarqube_data: {}2. Sysdig Secure
Sysdig Secure is a solution running in Docker that provides container runtime security. It can also monitor and do things like forensics. It can do this for containers and also for Kubernetes and microservices. It has visibility into your container infrastructure and then it helps to detect and protect against security threats in real time. It is also worth mentioning, that this is a paid solution. Sysdig also produces Falco, which we will also cover below.
Learn more about Sysdig here: Sysdig | Security for Containers, Kubernetes, and Cloud.
Features:
- Runtime security with threat detection and prevention
- Container monitoring for performance and resource optimization
- Forensic analysis for incident investigation
- Support for Kubernetes and other container orchestration platforms
3. Falco
Falco is a lightweight runtime security tool that continuously monitors system calls within containers. It can detect activity that is out of the ordinary (malware and other anomalous communication) as well as potential security threats. This can help identity attacks and even prevent attacks before they occur.
Learn more about Falco here: Falco.
Features:
- It is lightweight and efficient which minimizes any performance impact
- Monitors syscall activity for suspicious behavior
- It provides a flexible rules engine for custom threat detection
- It integrates with security information and event management (SIEM) tools
Docker run snippet including the daemon socket:
docker run --rm -i -t \
--privileged \
-v /var/run/docker.sock:/host/var/run/docker.sock \
-v /dev:/host/dev \
-v /proc:/host/proc:ro \
-v /boot:/host/boot:ro \
-v /lib/modules:/host/lib/modules:ro \
-v /usr:/host/usr:ro \
-v /etc:/host/etc:ro \
falcosecurity/falco:latest4. Hadolint
Hadolint is a Dockerfile linter which has many benefits in practice. It is a hardening layer that helps enforce best practices and identify errors in your Dockerfiles and other ways. By making sure your Dockerfiles are secure and efficient, Hadolint helps you build secure container images for your container registries (self-hosted or Docker Hub) from the ground up, which also helps with compliance and security policies.
Learn more about Hadolint and download here: GitHub – hadolint/hadolint: Dockerfile linter, validate inline bash, written in Haskell.
Features:
- Lints Dockerfiles for security vulnerabilities and best practices processes
- Identifies potential issues like unused stages, inefficient base images, and hardcoded secrets code content before these are hosted on your servers
- Offers suggestions for improvement and changes
- Integrates with CI/CD pipelines for automated checks and results as part of your pipeline
Hadolint can be integrated as a pre-build step in your CI/CD pipeline. Also, you can point Hadolint using a Docker container to your Dockerfile like the following:
docker run --rm -i hadolint/hadolint < Dockerfile
# OR
docker run --rm -i ghcr.io/hadolint/hadolint < Dockerfile5. Trivy
Trivy is a simple and comprehensive vulnerability scanner specifically designed for containers. It integrates seamlessly into your CI/CD pipeline, scanning container images in your registry for protection against known vulnerabilities in packages, operating systems, and libraries inspection. This can help you find these before an attacker in your implementation (host machine or cloud).
Features:
- Scans container images for vulnerabilities
- Supports various image formats (Docker, OCI)
- Integrates with popular CI/CD tools
- Offers SBOM (Software Bill of Materials) generation for transparency
Docker Compose snippet:
version: '3'
services:
trivy-scanner:
image: aquasec/trivy:0.49.1
command: ["trivy", "image", "<your-image-name>"] # Replace with the image you want to scanOr you can use Docker run:
docker run -v /var/run/docker.sock:/var/run/docker.sock -v $HOME/Library/Caches:/root/.cache/ aquasec/trivy:0.49.1 image python:3.4-alpine
6. Snyk CLI
Snyk CLI is a containerized tool that extends Snyk’s vulnerability scanning capabilities beyond container images. It allows you to scan your entire codebase for integrity, dependencies, and container images for vulnerabilities. It helps with an overall view of your application security posture architecture and its effectiveness from a security perspective.
Features:
- Scans codebases for vulnerabilities in various programming languages
- Analyzes dependencies for known security risks
- Scans container images for vulnerabilities
- Integrates with CI/CD pipelines for automated security checks
Docker Compose snippet:
version: '3'
services:
snyk-scanner:
image: snyk/cli:latest
command: ["snyk", "test", "--file", "path/to/your/codebase"] # Replace with your codebase path
7. Grype
Grype is an open-source vulnerability scanner specifically designed for container images. It focuses on analyzing the Bill of Materials (BOM) of container images, identifying vulnerabilities within the listed packages and dependencies.
Features:
- Analyzes container image BOM for vulnerabilities
- Supports various image formats (Docker, OCI)
- Integrates with CI/CD pipelines
- Offers SBOM generation for improved transparency
Docker run snippet:
version: '3'
services:
grype-scanner:
image: anchore/grype:latest
command: ["grype", "<your-image-name>"] # Replace with the image you want to scan
8. Syft
Syft is another open-source tool that focuses on software dependencies. It analyzes the dependencies used in your project, identifying potential vulnerabilities across various package formats. Syft helps you understand the overall security posture of your application’s dependencies.
Docker Compose snippet:
version: '3'
services:
syft-scanner:
image: anchore/syft:latest
command: ["syft", "bill-of-materials", "<your-application-directory>"] # Replace with your application directory
9. Gitleaks
Gitleaks is a security scanner that allows you to scan your Git repositories for leaks of information. It scans your code repository and files for leaks like access keys, passwords, and other secrets. If you can find things like this early, it can definitely help to prevent unauthorized access and security breaches.
Features:
- Scans Git repositories for leaks of sensitive information
- Supports various types of secrets (e.g., API keys, passwords, tokens)
- Offers custom rule creation for specific needs
- Integrates with CI/CD pipelines for automated checks
Docker run snippet commands:#
Docker (DockerHub)
docker pull zricethezav/gitleaks:latest
docker run -v ${path_to_host_folder_to_scan}:/path zricethezav/gitleaks:latest [COMMAND] --source="/path" [OPTIONS]
# Docker (ghcr.io)
docker pull ghcr.io/gitleaks/gitleaks:latest
docker run -v ${path_to_host_folder_to_scan}:/path ghcr.io/gitleaks/gitleaks:latest [COMMAND] --source="/path" [OPTIONS]10. Docker Bench
Docker Bench is a script that checks your Docker host and container configurations against the CIS Docker Benchmark. It identifies potential security misconfigurations and helps with the process to harden your container environment and hosts deployment.
Features:
- Checks Docker daemon configuration, host settings, container images, and build practices
- Identifies security misconfigurations based on CIS Docker Benchmark
- Offers remediation guidance for identified issues
- Open-source and actively maintained
Docker Bench doesn’t require dedicated docker images running in containers. You can run it directly on your host system to scan your Docker configuration.
Here are the general steps for using Docker Bench (refer to official documentation for detailed instructions):
- Download the Docker Bench script.
- Run the script with appropriate flags (e.g., docker-bench security).
- Review the output and address any security warnings.
Wrapping up the best Docker containers for security in 2024
Running Docker containers provides a world of possibility, including great features and technology capabilities. However, as we have covered in this best Docker containers for security in 2024 guide, there are many great security solutions we can deploy for deep container visibility, Docker image security, help with compliance policies, and deploying Docker containers with quality code releases.
Many solutions can scan images, check for container vulnerabilities, and security best practices, and help protect running containers. Keep in mind this isn’t a replacement for other security best practices like isolation, auditing, proper authentication and authorization, and the principle of least privilege to help prevent privilege escalation, encryption, logging, patching, access control, and securing networks, When it comes to ensuring the effectiveness of these security measures in Docker containers, it is crucial to choose the right containers that prioritize security and offer robust features. sandboxing, using a firewall, and other intrusion detection solutions. It is simply another layer of security that helps anyone with the need of securing their container infrastructure deployments.