pfSense pfBlockerNG vs Pihole Pros and Cons
There is a wide range of excellent solutions for blocking ads, malware, tracking cookies, and other unwanted network traffic for home labs and home users. There are two open-source solutions available for download today, pfSense pfBlockerng and Pihole, that are each great solutions in their own right. However, each has pros and cons that may suit some better than others. This post will consider pfSense pfBlockerng vs Pihole and see which features and functionality. Before considering pfSense pfBlockerNG vs Pihole, what are they?
What is pfSense pfBlockerNG?
The first solution we are going to consider is pfSense pfBlockerng. What is pfSense pfblockerng? First of all, to avoid confusion, pfBlockerNG is not pfSense. The pfSense open-source firewall solution is a fully-featured firewall/router providing enterprise features. It allows businesses and home users to secure networks, create VPN tunnels, do advanced routing, remote access, DNS, DHCP, etc. many other core network services and features.
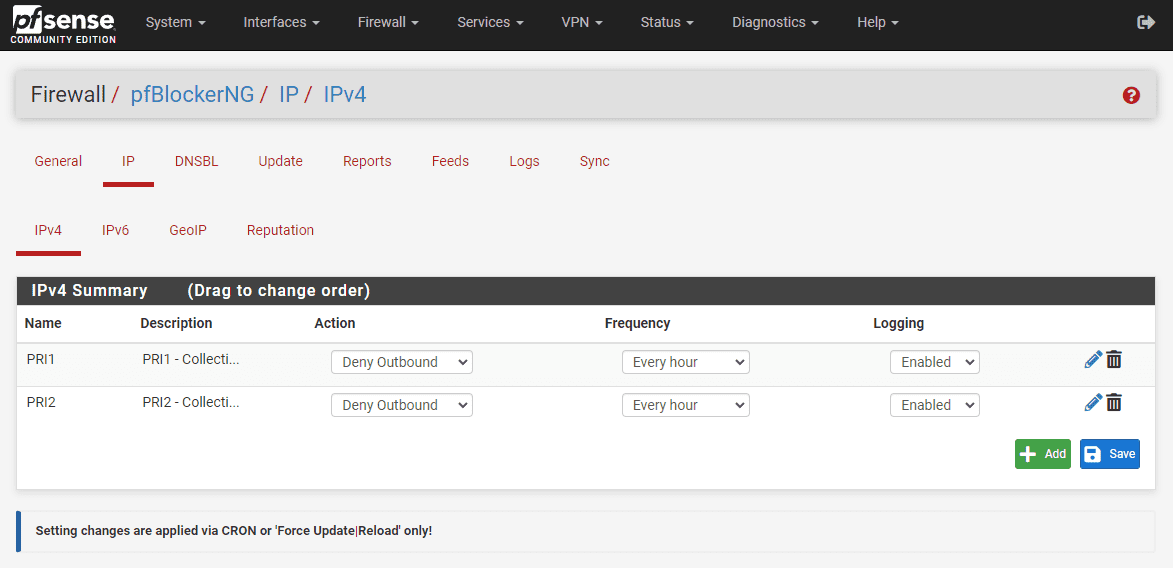
The pfBlockerng solution is an open-source software add-on package that can be downloaded and installed into pfSense. It provides many great features, including the following:
- Country_Block features
- IP_Blocklist features
- Dashboard widget
- XMLRPC Sync
- Dashboard widget with aliases applied and package hit
- Lists update frequency
- Options for choosing what to block and how to block
- Network lists may be used for custom rules.
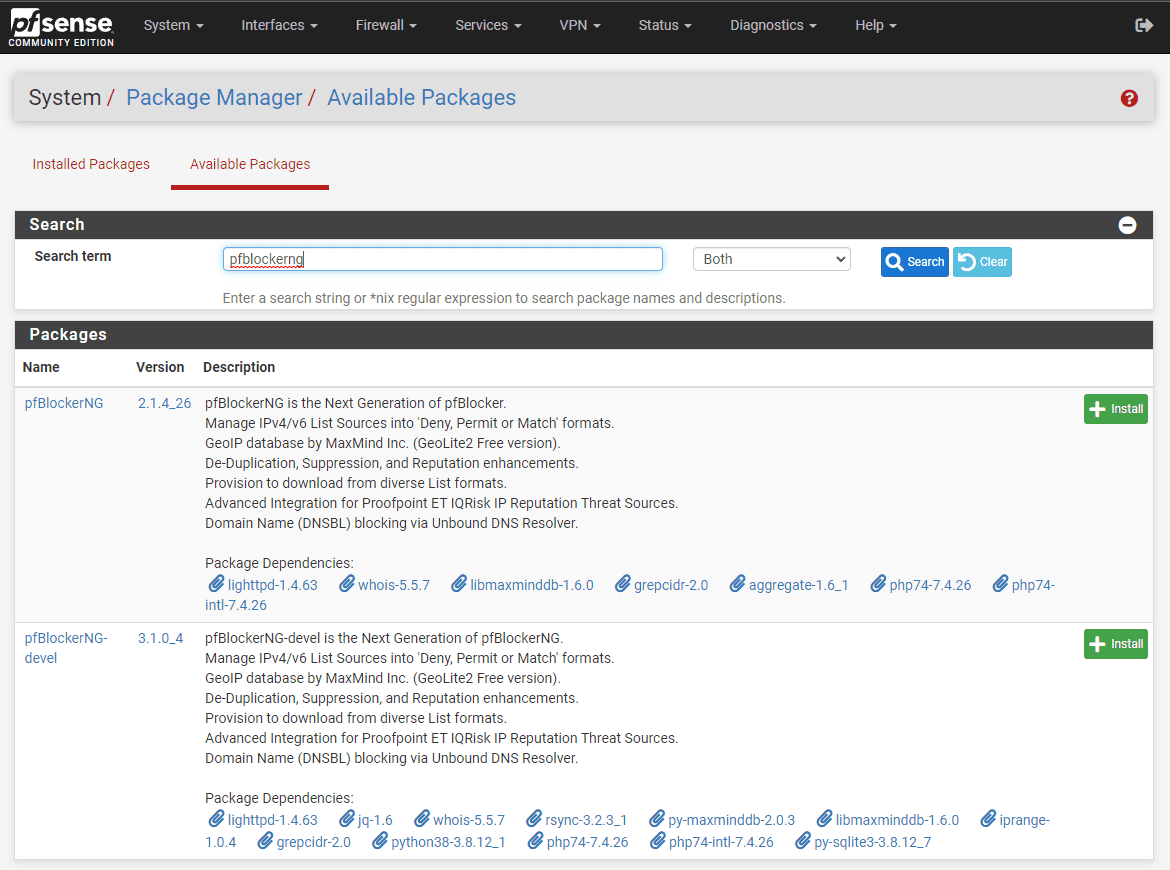
This extends pfSense’s normal L2/L3/L4 firewall capabilities to the DNS application layer, allowing pfSense to do DNSBL or Domain Name System Blackhole List. To view/install the pfBlockerNG package in pfSense, you navigate to System > Package Manager > Available Packages and search for “pfblockerng.”
As you will note, there will be two versions of the pfBlockerNG package returned, the pfBlockerNG package and the pfBlockerNG devel package. In most cases, the pfBlockerNG devel package is the package you want to install since it includes the latest and greatest features and functionality.
The pfSense pfBlockerNG package works by setting the pfSense interfaces you want to monitor with pfBlockerNG where the inbound configuration is the Internet connection. Like Pihole, pfBlockerNG can use lists that contain lists that can be used to block unwanted tracking, ads, malicious sites, etc.
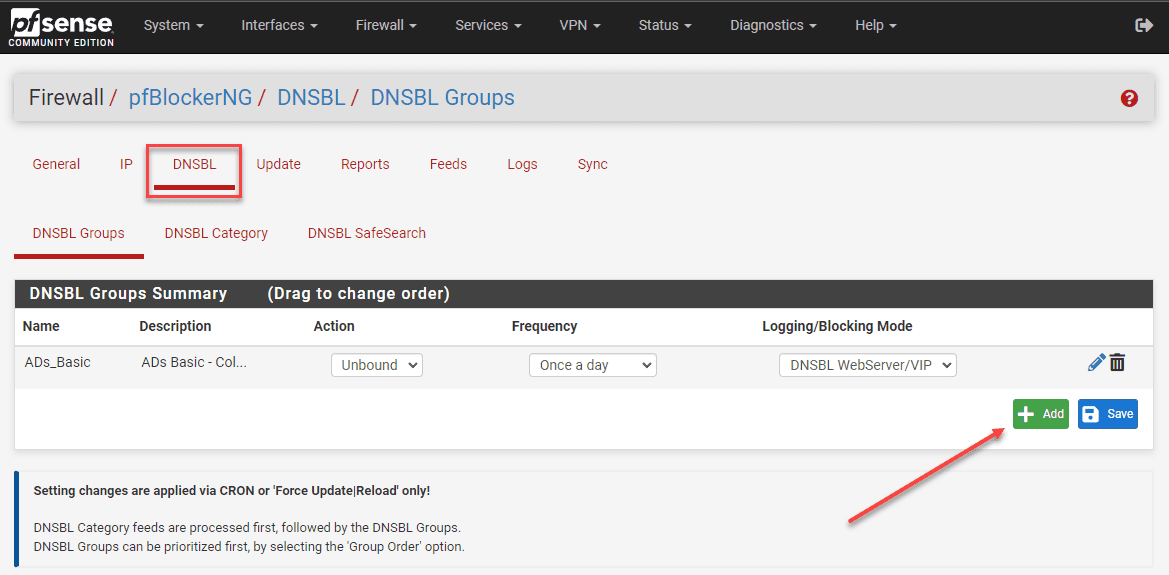
The feed system is the same or can be the same as the ones you use in Pi-hole. These are easily added in the pfBlockerNG > DNSBL > DNSBL Groups configuration.
Using pfBlockerNG, you can block DNS domains based on categories, a feature found in many modern firewalls. It allows the blocking of websites based on the categories they fall into.
One of the cool things that the pfBlockerNG package can do is block IPs and lists of IPs. As part of the solution, you can block lists of IP addresses and also block IPs based on the geolocation of the IP address.
You can check out the official documentation covering the pfBlockerNG module for pfSense here:
What is Pi-hole?
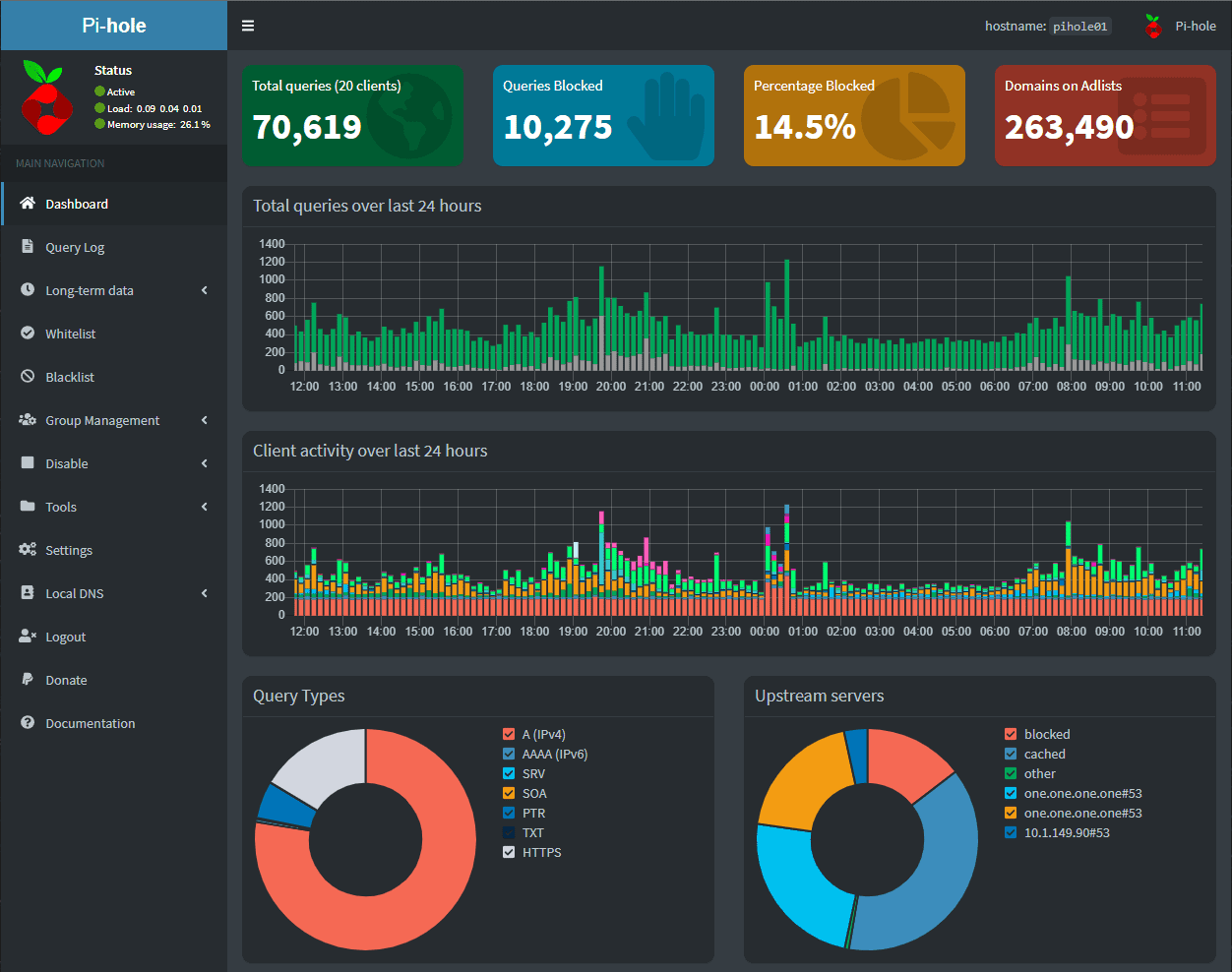
Pi-hole is a network-wide DNS ad-blocking solution that serves as an external DNS server. It means that Pi-hole essentially becomes the DNS server that you hand out to your network clients. Pi-hole then either allows or “sinkholes” DNS requests that match domain names included in disallowed lists.
It creates a “black hole” that denies clients’ DNS requests that request FQDNs associated with blocklists loaded into the Pi-hole server. Pi-hole does not do routing or other firewalling features. Instead, its “bread and butter” is DNS sinkholing which it does exceptionally well and is a very cool project that can run across multiple platforms, including Raspberry Pi devices. Hence, the name “Pi” hole. It does have a DHCP server built into the solution as well that can serve out IP address information for network clients.
Pi-hole has a really nice interface with great logging and reporting features that allow easily seeing the domains blocked and other information concerning clients creating the blocked traffic.
It also provides the following features:
- Allow lists and blocklists – you can point your Pi-hole to feed lists to blocklist or allowlist domains, as well as use regex statements to match various types of DNS queries
- Query log – With the query log, you can see all the domains queried by DNS resolution on your network, the originator of the query, and the requested DNS name
- Long-term statistics – DNS queries are stored in a built-in database that allows seeing trends over the course of time or other statistics that are helpful/useful
- Audit log – You can track the most queried domains and add these to block or allow lists
- Privacy mode – Pi-hole lets you choose the privacy level of how DNS queries should be anonymized
- API interface – Query the interface via API
- Conditional forwarding – With conditional forwarding, you can point Pi-hole to an upstream DNS server to resolve other internal hostnames, such as an Active Directory DNS server
Check out the official Pi-hole project website here:
Can you run both pfSense pfBlockerNG and Pihole together?
Yes, you can. There is nothing to prevent running pfSense as your main firewall/router and having Pi-hole serve as the DNS servers for clients who use the pfSense box as their gateway. The pfSense box would perform all other firewall/routing duties, while the Pi-hole would serve as a DNS server that performs DNS sinkholing.
This does introduce more complexity to the environment and can make troubleshooting when things don’t work or won’t connect more difficult. It means you may have two places to check each time to troubleshoot connectivity or false positive issues.
pfSense pfBlockerNG vs Pihole Pros and Cons of Each
I like pfSense pfBlockerNG and Pinhole to protect home and other networks from unwanted traffic, including malicious traffic, ads, tracking, etc. Both projects have tremendous value in your network to help protect your traffic. However, each has its strengths and weaknesses as a solution, and it comes down to what you prefer and what your individual needs and use cases include.
Let’s look at pfSense pfBlockerng vs Pihole pros and cons and list some things to consider:
pfSense pfBlockerNG
Pros:
- Free and open-source
- A powerful and robust solution including both DNS feeds and also can do IP blocking from lists and geolocation
- Integrates with your existing pfSense firewall appliance
- You don’t have to have a standalone box to run pfBlockerNG
- Integrates well with the pfSense interface and “feels” native to pfSense itself
- It allows taking advantage of the free block lists available on the Internet that can also be used with Pi-hole
- It can do IP blocking, enabling true L3 firewall features and functionality, which cannot be done with Pi-hole
- Can block categories of sites as opposed to simple blocklists, which is something that Pi-hole can’t do unless you have particular feed lists that only block a specific category
- pfSense, which pfBlockerNG runs on top of, has an HA configuration for high-availability
- pfSense has fully supported hardware devices from Netgate that can be purchased commercially
Cons:
- You may not currently run pfSense as your firewall, so you have to run pfSense to take advantage of pfBlockerNG
- It is a bit more complicated than Pi-hole, especially considering you have to standup pfSense to take advantage of it
- The interface for pfBlockerNG is not as intuitive as Pi-hole
- If you simply want to stand up an easy DNS solution in parallel with your firewall, this would be overkill, Pi-hole would be better
- You can’t run pfSense on an ARM device as you can Pi-hole
- Some do not like the reporting aspect of pfBlockerNG since it is part of the overall system logging and is more cumbersome to find entries when compared to Pi-hole
Pi-hole
Pros:
- Free and open-source
- Allows using DNS sinkholing, which is very effective to remove ads, malware, and other unwanted traffic as a network-wide solution
- Can run as a standalone box in parallel to your existing router/firewall
- Can run on a low-power Raspberry Pi or another ARM device
- Beautiful interface
- Very good reporting
- Interface is intuitive
- Very easy to setup
- It can do conditional forwarding to forward specific domain requests to another internal DNS server such as AD DNS.
Cons:
- You have to have a dedicated router/firewall in addition to the Pi-hole appliance
- It only does DNS sinkholing, DHCP, and a few other features
- Can’t block websites based on IP addresses
- Can’t easily block categories of websites as a built-in feature
- It requires changing your DNS configuration to the address of your Pi-hole
- Pi-hole does not have a native mechanism for high availability. There are scripts available such as GravitySync, but this is not a native solution and requires copying files back and forth
- There is no commercially available supported hardware that you can purchase with Pi-hole configured and running, as with Netgate’s pfSense appliance
pfSense pfBlockerNG vs Pihole FAQs
- What is pfSense? The pfSense open-source firewall solution provides a freely available firewall that is community supported and contains many enterprise features. There is also a commercially available version of pfSense called pfSense+ available from Netgate, making the physical hardware devices running pfSense.
- What is pfSense pfBlockerNG? The pfBlockerNG software package is an add-on module to pfSense. So you have to be running pfSense first, and then you can add the pfBlockerNG module to pfSense. The pfBlockerNG software package allows doing DNS sinkholing like Pi-hole.
- What is Pi-hole? Pi-hole gets its name from the ability to run the solution on Raspberry Pi devices. It performs DNS sinkholing and allows blocking URL requests based on URL feeds that provide the list of domains to block. It is a network-wide solution that works by pointing your client’s DNS settings to the address of the Pi-hole box.
- What is DNS sinkholing? DNS sinkholing intentionally fails requests that match the domain names in a list of blocked domains
- Is pfSense free? Yes, the Community Edition of pfSense is free. There is also a commercially available version called pfSense+ that runs on Netgate appliances, but can also run on commodity hardware. PfSense recently made a change in the licensing model so that pfSense+ is no longer free. See here: Addressing Changes to pfSense Plus Home+Lab (netgate.com).
- Is Pi-hole free? Yes, Pi-hole is a free solution available for download across a wide variety of operating systems and platforms.
- Which is better, pfSense pfBlockerNG or Pi-hole? Ultimately, the standard contractor’s answer of “it depends” applies here. What works in one environment may not work or make sense in another environment. For environments running a different firewall solution, changing out your entire firewall may not make sense to run the pfBlockerNG software package. Standing up a pfSense box outside of your main firewall just to run pfBlockerNG is probably overcomplicating matters and wouldn’t be feasible or recommended. However, if you are running pfSense already, adding pfBlockerNG makes perfect sense, and most likely, if you are running pfSense, you are already running pfBlockerNG. For environments not running pfSense as the firewall, Pi-hole might make a lot of sense to add this to the environment to perform DNS sinkholing duties for clients. You CAN also run pfSense and Pi-hole together to have a hybrid approach of the best of both potentially. However, keep in mind this is a more complex configuration and may make finding blocks and other troubleshooting more convoluted and difficult.
Final Notes and wrapping up
I have run both pfSense pfBlockerNG and Pi-hole in several environments, including the home lab environment. I like the features found in both solutions, and some things could be better about both. Hopefully, this pfSense pfBlockerng vs Pihole comparison of pros and cons will help any trying to decide which solution to use and the benefits and drawbacks for each. It is great to have choices. Both pfBlockerNG and Pi-hole are excellent and give us the options to block unwanted traffic across the network. Which one will you decide to use?









nicely done
Great article. Can pfBlockerNG run on OPNsense too alongside Zenarmor? Or is Zenarmor meant to be a replacement for pfBlockerNG, with it’s built-in URL filtering?
This helped me a lot since i’ve recently migrated to PfSense and my piHole hasn’t been blocking ads consistently. Thanks for all the info!
Slash,
Thank you for the comment! Great to hear and pfSense definitely works great with ad blocking. Very fully featured along with the other filtering it can do.
Brandon
“pfSense+ that only runs on Netgate appliances”
pfSense+ can and does run on non-Netgate devices. I’m currently running it on the following:
Intel(R) Core(TM) i5-3470 CPU @ 3.20GHz
4 CPUs : 1 package(s) x 4 core(s)
AES-NI CPU Crypto: Yes (active)
IPsec-MB Crypto: Yes (inactive)
QAT Crypto: No
Thank you for this article. My pi-hole hasn’t been blocking ads since the v6 upgrade. Was considering making a virtual pi-hole in my proxmox server but I run pfSense… I didn’t know about pfBlockerNG so I’ll give it a try!
Scott,
Thank you for the comment! Awesome. So glad this article was helpful to you. pfBlockerNG is a great module!
Brandon