Segment your VMware Network with pfSense
There are many firewall solutions out on the market that are great. I am a huge fan of many of the enterprise solutions out there that provide excellent features, powerful robust networking, advanced threat protection, and many others. However, there are also very interesting open-source and free solutions that are powerful in their own right. The pfSense open-source firewall is a really great firewall solution you see even in the enterprise data center because it is free, fully featured, and provides many features that businesses look for in the enterprise. I had a comment on a video I created not long ago about how to segment your VMware Network with pfSense and I thought it would be a great topic to cover at a high level with some details as well.
Why segment your network?
First of all, before you implement any technical solution in your environment, you first need to answer the important question of why. This is something I try to do with most solutions I recommend for businesses or clients I work with. If you can answer the “why” then it can be a worthwhile endeavor to realize the benefits of the technical solution. I am a geek and nerd at heart. While I like to implement technology, which is fun, I realize for most, there needs to be a business case and a reason for it. So, why segment your network?
This really is an age-old methodology to create more security and flexibility with your networking in the environment. Segmenting your network provides many benefits that help to minimize risks associated with having one large network. Time and again, we read of vulnerabilities that list the attack vector as including line-of-sight network connectivity to a specific port on the target server or workstation. If you can separate the ability for machines on one side from “seeing” the vulnerable ports on the other side, you have essentially greatly reduced the attack vector.
Notice I am not saying it is impossible now to be compromised, but rather, the threat is reduced. I have long heard and seen this in practice, security is like layers of an onion. You can’t depend on any single layer for total protection. Rather, combined, you want to make it as difficult and undesirable for an attacker to spend the time to compromise the environment.
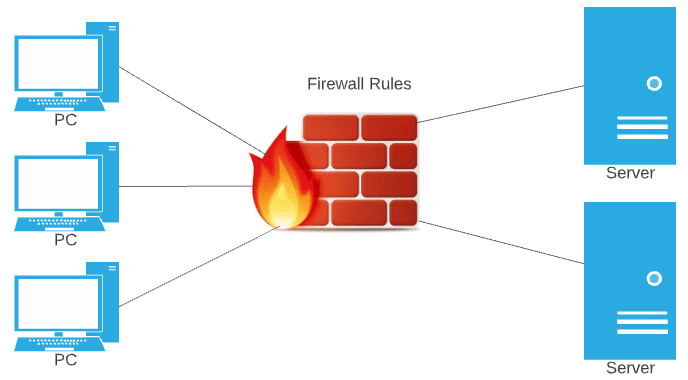
Segmenting your network allows carving up the network so you can place a “security device” or technology in between the segments so as to scrutinize the traffic sourced or destined between the various network segments.
For instance, it is very wise to NEVER have client workstations on the same segment as your servers. This is asking for a compromise. Workstations, even with endpoint protection are generally the most dangerous devices on the network since end-users are using them for email and general Internet browsing.
Instead, you want to have something like the following. Below, all traffic between PCs and Servers is scrutinized for various traffic types and network communication and clients and servers exist on different networks.
Segment your VMware Network with pfSense
While you can certainly segment your virtual network with a physical firewall device, in modern times, this does not scale well and is not very efficient. Instead, virtual firewall appliances can be used to provide traffic scrutinization between different network segments and can be used to route east/west and north/south traffic.
You can easily deploy pfSense inside your VMware vSphere environment and use it as a firewall between your various VMware virtual networks configured inside your vSphere environment. If you haven’t read my quick post on how to deploy pfSense in VMware vSphere, read my walkthrough post here:
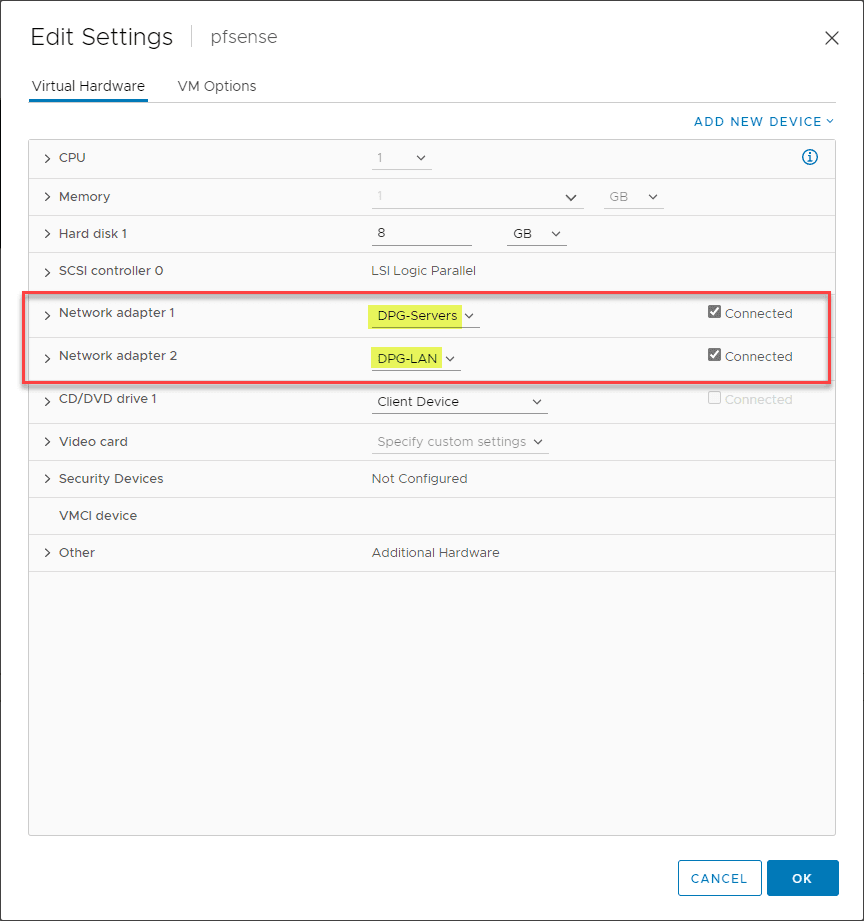
Now, let’s see how you can segment your VMware network with pfSense. I will show you a basic example of how this works. Below, you see the Virtual Hardware configuration of my pfSense VMware virtual machine configured in VMware vSphere. This is a simple example with two network adapters, one for the LAN segment, and one for the Servers segment.
To use pfSense as a firewall between the two segments, you would assign the pfSense VM address for each segment as the default gateway for the machines existing on each segment. In this way, the hosts have to route their traffic through pfSense and, by extension, will have traffic processed through the firewall rules assigned. In the network below:
- DPG-Servers is a vSphere Distributed Switch port group assigned VLAN 149
- DGP-LAN is a vSphere Distributed Switch port group assigned VLAN 10
- Each port group has its own address space contained within each VLAN
- To get to the other segment, each network segment is routing its traffic through the pfSense firewall
A conceptual overview of the networks looks like the following:
Creating pfSense allow and deny firewall rules to control traffic
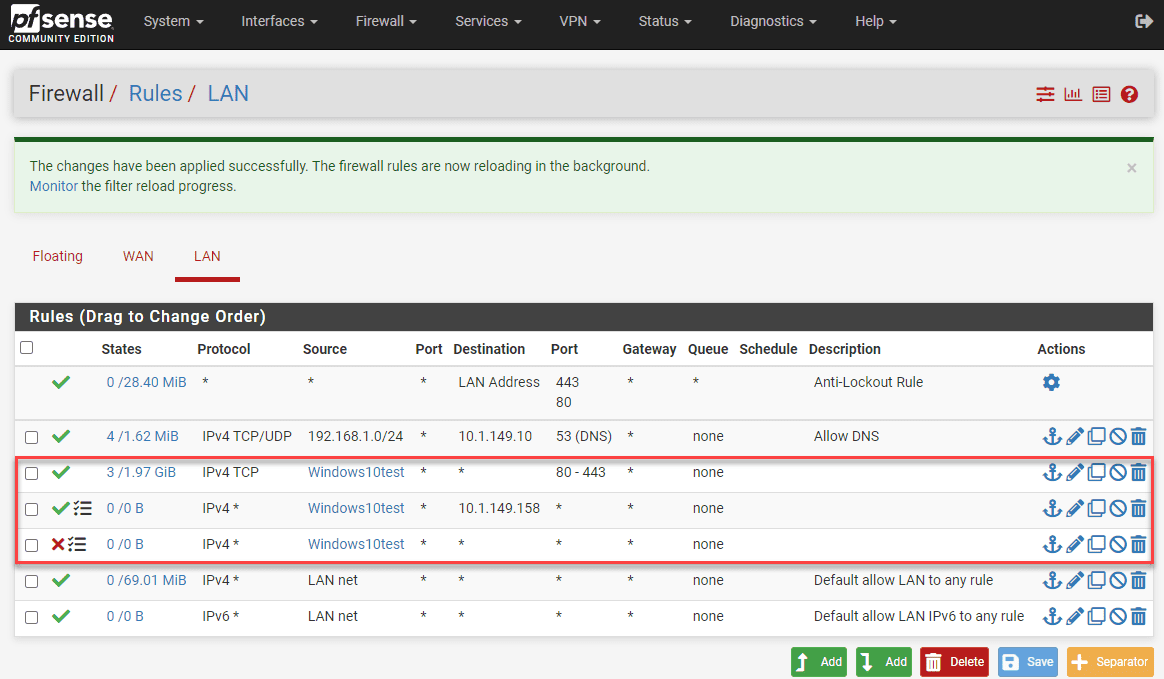
Now that we have pfSense sitting in between two VMware networks that we want to control traffic between, it is simply a matter of building out firewall rules. Below, I have setup a quick set of rules to demonstrate how this works.
Like many firewalls, pfSense processes the firewall rules from the top down. So if you have a blanket “deny all” type rule, you will want to place your specific traffic you want to “allow”, above the deny all rule. In this way, the specific traffic set to allow is processed, then any other traffic is denied based on the deny all rule.
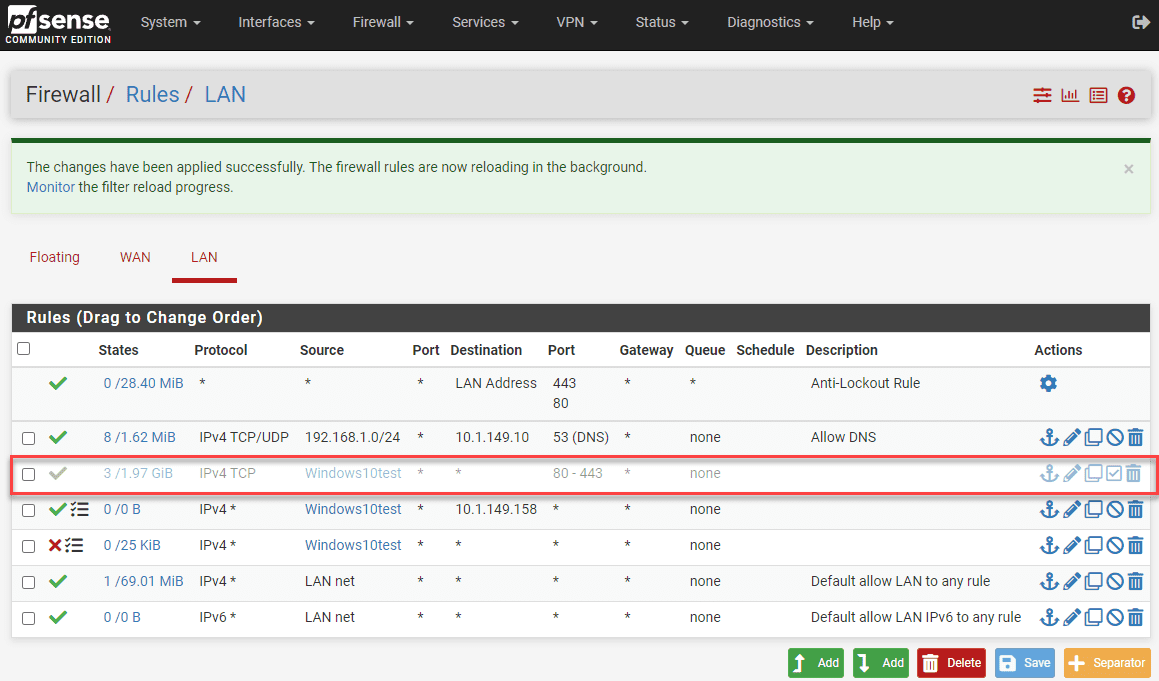
Following this principle, as you can see I have a client that I have an alias setup for in pfSense called Windows10test. In the top firewall rule outlined, note the following:
- TCP ports 80/443 are allowed
- All traffic between this client a Server at 10.1.149.158 is allowed
- All other traffic is denied from this host.
Testing pfSense firewall rules to segment a VMware network
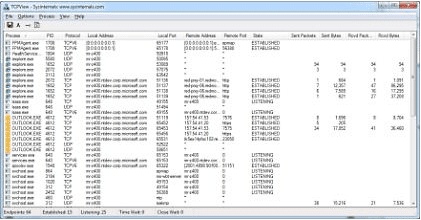
Note how we can test this with a simple ping test. In the screenshot below, I am pinging the “allowed” host from the Windows10test machine. The traffic is successful since it is allowed.
In the bottom ping test, the host being pinged from Windows10test does not match any rules above the “deny all” rule for this host, so it fails.
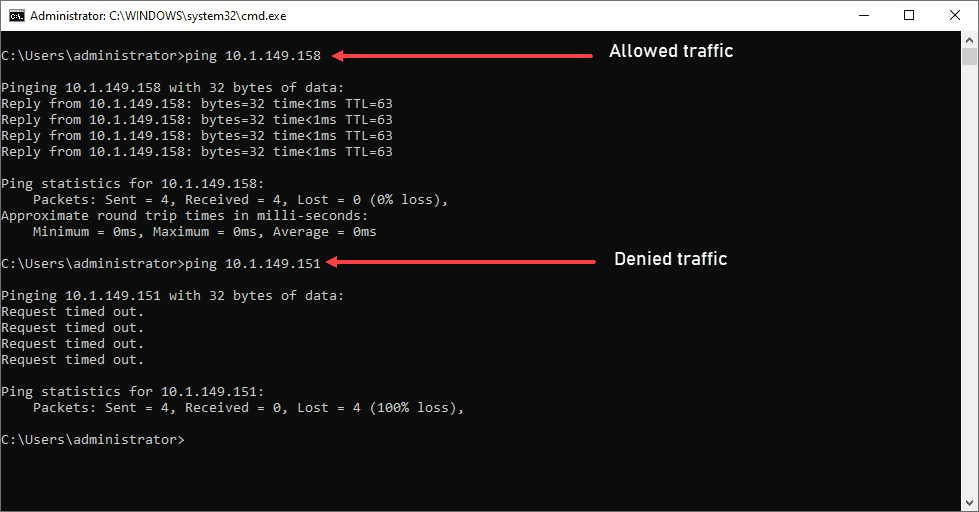
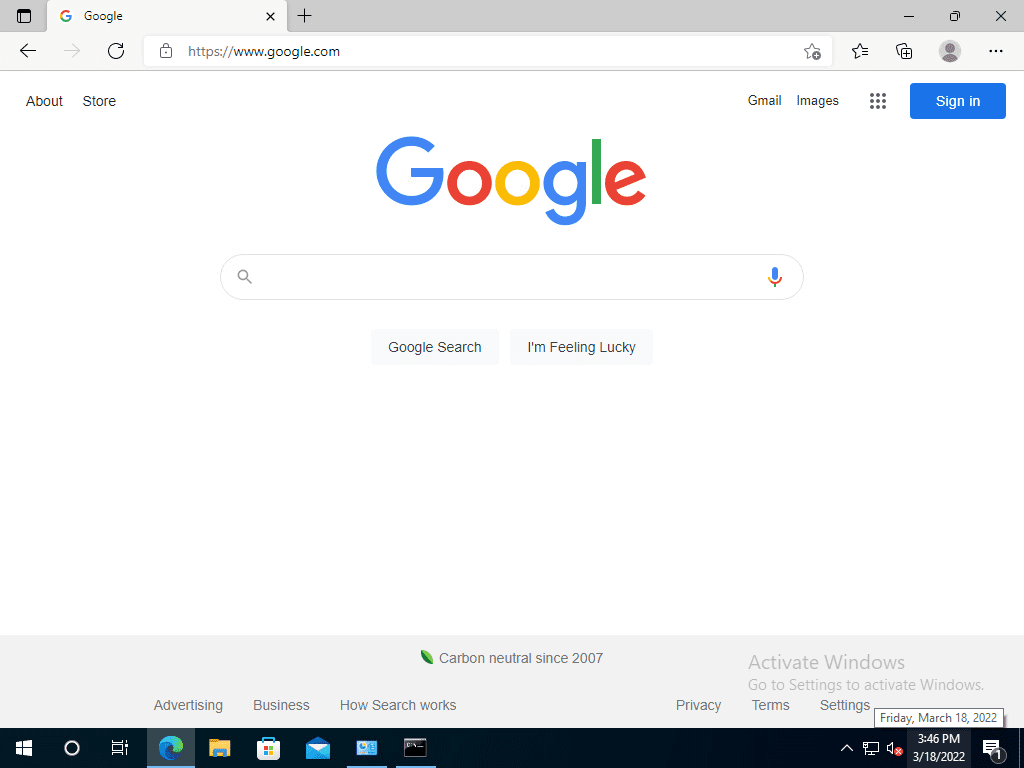
Aside from a ping test, what about web traffic? As you notice in the firewall rules I show above, we are allowing 80/443 for this host. As expected, if I test web connectivity from the Windows10test host, it works just fine.
Now, let’s disable the rule. As you can see below, I have disabled the pfSense firewall rule for this host allowing traffic destined to 80/443. You can tell by the faded-out appearance of the rule in pfSense.
After disabling the pfSense rule and refreshing the page, the page fails to load.
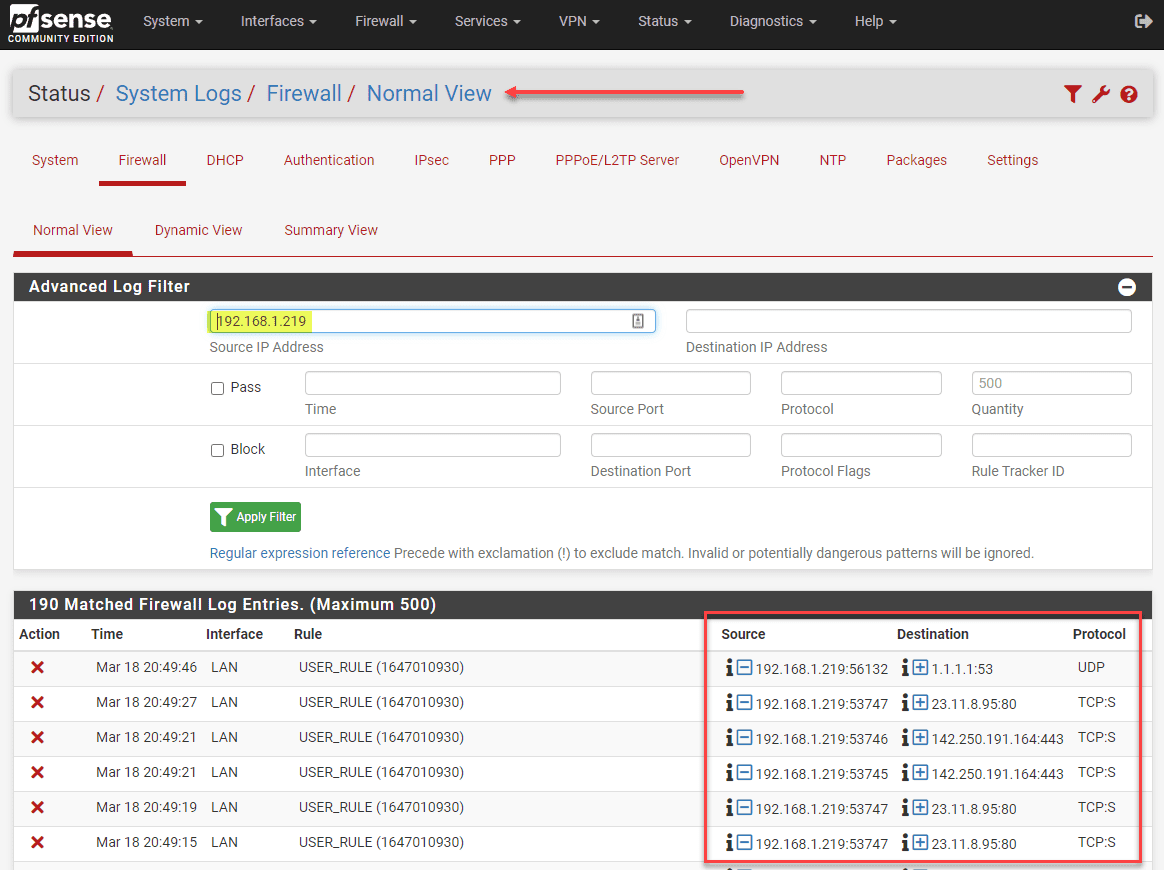
Viewing blogs in the firewall log
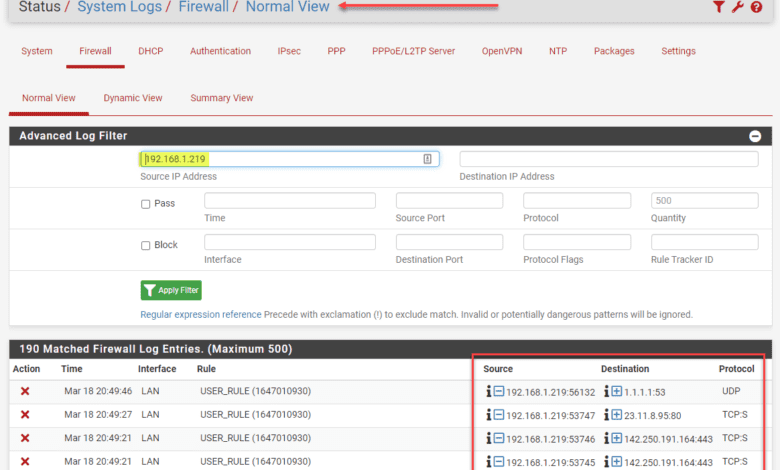
The pfSense platform provides decent logging of allow and block events. Navigate to System Logs > Firewall. Click the Advanced filter “funnel” on next to the “wrench.” It opens the Advanced Log Filter dialog box. Here you can use many filter types to narrow in on the traffic you want to see. Here, I am using the Source IP Address.
As you can see, the blocks appear for 80/443 as expected as well as queries for UDP DNS which I didn’t have allowed in the firewall rule list.
Segment your VMware Network with pfSense FAQs
- Why segment your network? Segmenting your network provides many benefits, including manageability and security. It allows placing a firewall in between for processing traffic types.
- Can you segment your VMware network with pfSense? Yes. As shown in the walkthrough above, you can place a pfSense virtual firewall in between two network segments, use it as the default gateway for those devices, and restrict or allow any type of traffic for all or specific hosts and combinations in between.
- Can you allow certain hosts and block others with pfSense? Yes, you can be very granular in the types of traffic allowed or denied.
- Is pfSense free? pfSense is a free open-source firewall that provides access to many enterprise features.
- Is pfSense a good firewall? It is a really good firewall, providing most of the functionality looked for in basic segmentation and traffic control.
Final Notes
The example above is very simple. It helps to demonstrate that you can easily segment your VMware network with pfSense and provide really good filtering and segmentation with traffic control for your network.







Hi, thanks for this. 3 questions:
1.Are the DPG-Servers & DPG-LAN Portgroups all on the same vSwitch?
2.When assigning interfaces in Pfsense did you put one of the DPG Portgroups on WAN and one on LAN? If so…
3.What if you have an actual WAN port group assigned too? Would one of the DPG Port groups be assigned to OPT1 interface rather than WAN?