Viewing and killing TCP IP connections Windows
Many time in troubleshooting or needing to view network traffic information or connection information, seeing your TCP/IP connections in Windows can provide valuable insight into problems or issues that may be going on in Windows with connectivity. Also, viewing connection information is a great way to narrow down on possible backdoor traffic to a workstation if malware is suspected. In this guide, we want to look at several tools and utilities to both view connection information as well as kill TCP connections in Windows that may be problematic or malicious.
Windows itself has many really nice tools built-in that will enable you to see TCP and UDP connections right out of the box via the commandline. Especially the later versions of Windows which include Powershell expand these capabilities as well.
Commandline Tools
Powershell
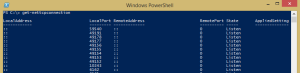
With powershell we have a whole new array of commandlets to peer inside of and control what is going on with Network connections in Windows. There are two commands in general among others that provide really powerful monitoring inside of Powershell and that is the get-nettcpconnection and get-udpendpoint. Take a look at the whole list of new powershell commands for monitoring and controlling TCP activity here: https://docs.microsoft.com
Get-NetTcpConnection – cmdlet gets current TCP connections. Use this cmdlet to view TCP connection properties such as local or remote IP address, local or remote port, and connection state.
Get-NetUDPEndpoint – gets current statistics for a UDP endpoint. The cmdlet returns UDP end point properties, such as local and remote UDP ports. If you do not specify any parameters, the cmdlet gets statistics for all UDP end points.
Netstat
Displays active TCP connections, ports on which the computer is listening, Ethernet statistics, the IP routing table, IPv4 statistics (for the IP, ICMP, TCP, and UDP protocols), and IPv6 statistics (for the IPv6, ICMPv6, TCP over IPv6, and UDP over IPv6 protocols). Used without parameters, netstat displays active TCP connections.
Below the command was issued netstat -ano
With the PID information you see above in the netstat output, you can use this number to correlate with PID information in Task Manager to identify the exact process and kill if need be.
wkillcx
Wkillcx is a small command-line utility to close any TCP connection under Windows XP/Vista/Seven as well as Windows Server 2003/2008. This is a great little commandline program that allows you to kill the remote IP:port connection information without knowing the PID. You simply issue the command, feed the appropriate connection information, it searches for that connection and kills it. Download wkillcx here: https://wkillcx.sourceforge.net/
syntax : wkillcx [dest_ip:dest_port] wkillcx 10.11.22.23:1234
GUI Tools
Along with the commandline tools included in Windows there are also a couple of really nice GUI tools that allow ones to see TCP activity as well as kill those TCP connections via killing the process that is spawning the TCP connections.
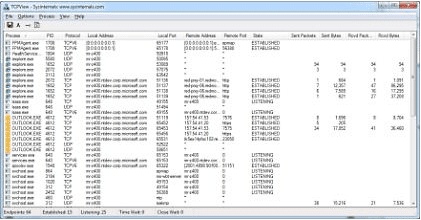
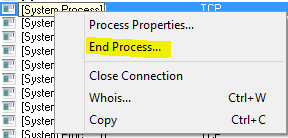
TCPView
TCPView is a Windows SysInternals Tool that is designed to basically show detailed listings of all TCP and UDP endpoints on your system, including the local and remote addresses and state of TCP connections. The download of the utility also includes a commandline version of the tool in tcpvcon. Download TCPView here: https://technet.microsoft.com/en-us/sysinternals/bb897437.aspx
Another really nice feature of TCPView is that you can right-click on any connection entry and then Kill the process that is using it:
Microsoft Message Analyzer 1.0
Microsoft Message Analyzer is a new tool for capturing, displaying, and analyzing protocol messaging traffic and other system messages. This is a relatively new tool that also can import data from the legacy Microsoft Network Protocol Analyzer 3.4.
This is a more full blown protocol analyzer, but can do many of the basic things we are referring too in the above guide. Download the Microsoft Message Analyzer here: https://docs.microsoft.com
Final Thoughts
Using the tools listed above, one can view network connection information via either the commandline or using GUI tools. This is extremely helpful when you are tracking down a rogue connection or a problematic process that has network hooks.


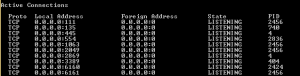






Microsoft Message Analyzer 1.0 is no longer available on MS’ website