VMware NSX Palo Alto Integration
Today’s network environments are more complex than ever before. The move to the public cloud and extending resources from on-premises to the cloud is not showing any sign of slowing down anytime soon. Business are continuing to leverage technologies in the cloud and applications often depend on resources both in the cloud and some that are still housed on-premises.
This has led to a network layout where east/west traffic has grown larger than ever before. Especially with software-defined networking at play, traffic simply operates like it is adjacent nodes. When it comes to security this creates difficulties having the visibility and control necessary to maintain a secure environment. Palo Alto is a firewall that I use and provides technologies that can help augment and bolster your network security, even in vSphere environments running NSX. Let’s take a look at VMware NSX Palo Alto integration and see how Palo can increase visibility and control in your environment.
Networks and security threats have evolved
It has been noted that some 80% of network traffic today is east/west traffic. This is eye-opening as it helps to underscore the importance of securing this traffic. In traditional environments, east/west traffic has been “trusted” since it is inside the network perimeter. However, this is no longer a wise network security stance.
Attackers often infiltrate networks and then look to move laterally within an environment, performing reconaissance, and information gathering. Many high-level breaches often occur this way. Attackers are able to infiltrate the perimeter and then are able to move around freely in a lateral fashion.
At that point they are able to often compromise other internal systems, loading malware, exfiltrating data, and other malicious activities. So, the perimeter mentality of where traffic is unsafe or safe is no longer relevant in today’s environments.
As mentioned earlier, the perimeter is often blurred or even non-existent with cloud and other connections that are made between environments. This requires that organizations take on a “zero-trust” methodology to network security. This means even between hosts on the same network, there is no “assumed” trust between nodes, unless explicitly defined.
Additionally, organizations are facing challenges with having multiple security tools that all have visibility over different areas of the network or different contexts. It becomes very difficult to correlate security alerts between products and dashboards effectively.
VMware NSX Palo Alto Integration
Let’s narrow in on how to further secure VMware vSphere environments with Palo Alto. What tooling does Palo Alto bring to the table to help bolster the security of your environment. As many may already know, Palo Alto offers both a hardware firewall appliance as well as VM series appliances that have the same features as the hardware counterparts. The VM series firewalls are a great way to augment and bolster network security in environments that are heavily virtualized where it is not possible to have a hardware appliance sitting between your VMs.
Advanced protection against threats
What are some of the advantages of the Palo Alto security solution over a strictly NSX implementation? Palo provides really great protection against what they describe as “application shift” as well as “delayed threats”.
NSX has application capabilities, but it only identifies the application initially and places the flow into fastpath. This works on the assumption that the application is not malicious and will not change the flow in the future. This ties into the delayed threats discussion.
Attackers who write malware are very smart in knowing that if the code and network flow comes across as malware initially, they are much less likely to get this into your environment.
Your network security solution needs to follow that flow through the entire lifecycle of the flow, not just the initial identification of the network flow as either malicious or harmless.
No longer are traditional firewall rules effective against next-generation threats in your data center. Traditional firewall rules include the old fashioned Src IP, Dst IP, and port. However, there is no context with this type of network security.
User and workload context with Palo Alto
With next generation firewalling you can combine user contexts and workload context and create realtime policies that reflect active users and real workloads in your datacenter. This allows actually building policies that are relevant and correlated to users and workloads.
Within the next-generation firewalls Palo helps to protect against data exfiltration and advanced malware threats.
Automation
Palo Alto VM firewalls can take advantage of very common and powerful automation tools in use today such as Ansible, Terraform, and vRealize Automation to deploy and configure the firewalls as well as interact with the Palo Alto management tool called Panorama.
Palo Alto VMware NSX Security components
What are the components of the Palo Alto security solution?
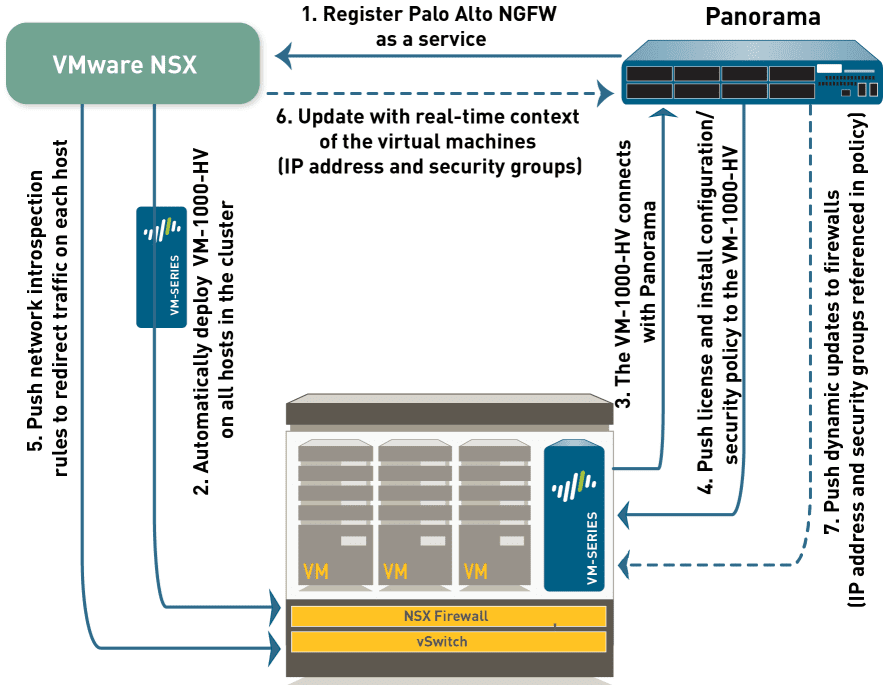
- Panorama – This is the centralized management tool for the Palo Alto environment. It provides management of all firewalls in the environment and can also act as the centralized log repository as well. It can be used to automate VM-series deployments in vSphere and NSX with device groups and templates. It also provides centralized policy configuration and implementation. It is also a very modular platform that provides the ability to have plugins from third-party solutions outside of Panorama and integrations with vSphere and NSX.
- Plugin architecture – Specifically related to VMware, there are two Palo Alto plugins available that integrate with your VMware environment. The first is the vCenter Plugin that allows Palo to query the inventory database and extract information about the workloads themselves. This includes hostname, portgroup, inventory tags, and also see “Notes”. This can be used to populate a dynamic address group. The NSX plugin allows Panorama to interact with the NSX Manager. With NSX Manager, Panorama can access the various attributes from NSX. This includes logical switches, security tags, port groups, ip sets, etc.
- Dynamic Address Groups – Container that holds the information that is extracted from either vCenter or NSX Manager. This allows for automatic network security based on workloads that are provisioned. Once dynamic address groups are populated, then these can be matched to firewall policies.

VM series firewalls work like the hardware firewalls. These provide not only the tradition layer 2 and 3 capabilities, it also provides layer 7 application firewalling. These also support dynamic routing protocols on the firewalls as well such as BGP.
- Zero-touch provisioning capabilities – This is made possible by the capabilities found in Panorama
- Improved network visibility – NSX has layer 7 capabilities. VM series app-id DB has over 2300 applications and constantly watches the flows to protect against app shift and delayed threats
- Advanced threat protection – Palo’s threat protection feed has been around for years. Customers share the same feed so when a threat is detected, all customers get the benefits of the threat intelligence
- Automated response – Detection and response are two different concepts. Today’s attacks are highly automated so the detection and response must be automated as well.
Wrapping Up
VMware NSX Palo Alto Integration provides some really great advantages of bolting on the security capabilities of the Palo security solution on top of the NSX platform.
While NSX-T is rapidly improving, there are definitely advantages to the Palo firewall capabilities when compared to what is found in NSX currently. In using Palo firewalls over the years, they provide really great protection, especially with the app-id protection and threat feeds. Having this on top of NSX makes for a formidable defense against current attacks.
Learn more about the Palo Alto VM series firewalls here.








