Automate CurveBall Crypt32.dll Patching
With the recent developments with CurveBall Crypt32.dll, everyone is no doubt thinking about patching their Windows environments and doing this quickly. Even if you have WSUS in play, you may want to do something a little more proactive on your Windows Servers to make sure they have the patches installed for mitigating this vulnerability. I have covered in detail in a couple of other blog posts ways to automatically patch your Windows Servers using some automation tools.
Let’s take a look at these tools in the context of the CurveBall Crypt32.dll vulnerability patch and see how it can be used for making sure your systems are patched and no longer vulnerable to this bug which is fairly nasty.
Tools for Automating Windows Patching
There are a couple of tools that I really like to use when it comes to automated patching of Windows systems.
- Ansible
- PowerShell
I have listed Ansible here as number 1, however, either tool could be listed in my opinion for Windows patching. I really do like Ansible though for its abilities in this area. PowerShell is great as well and of course works very well for anything you need to do in Windows.
Why am I not listing WSUS Server here? Well, WSUS has its place. However, for proactive patching and “at the moment” patching of systems it is not the best in my opinion. Rather than pushing patches out to a Windows system, the Windows systems are basically targeting the WSUS server to pull updates from. So it is a bit more passive in terms of only relying on it for getting your systems patched.
However, it can be used in conjunction with the above tools as it can be the source of the updates that are pulled and the tools above are the engines driving the patch process. Hopefully this mindset makes sense to most.
Use Ansible for CurveBall Crypt32.dll Patching
Ansible provides an easy way to get your Windows Servers patched for the CurveBall Crypt32.dll vulnerability.
Using Ansible, you can create a simple .yaml file playbook that contains everything you need to patch your systems with the latest patches, including security and critical updates. Ansible uses the win_updates module to perform the updating.
You can use the simple .yaml code below for updating:
--- - name: Search, return, and log Windows Updates to c:ansible_wu.txt win_updates: state: searched log_path: c:ansible_wu.txt - name: install all critical and security updates win_updates: category_names: - CriticalUpdates - SecurityUpdates - UpdateRollups state: installed register: update_result - name: reboot host if required win_reboot: when: update_result.reboot_required
With Ansible you can create an inventory file that contains the list of all your Windows Servers you want to patch, install the patches, reboot the server, and listen for the server to come back online and finish out the process.
A few more examples of installing only Security updates or installing security updates for specific KB numbers (Below are the two KB numbers for Windows Server 2016 and Windows Server 2019.
- name: Search-only, return list of found updates (if any), log to C:ansible_wu.txt
win_updates:
category_names: SecurityUpdates
state: searched
log_path: C:ansible_wu.txt
- name: Install all security updates with automatic reboots
win_updates:
category_names:
- SecurityUpdates
reboot: yes
- name: Install only particular updates based on the KB numbers
win_updates:
category_name:
- SecurityUpdates
whitelist:
- KB4534273
- KB4534271
Take a closer look at the win_updates Ansible module here:
Use PowerShell for CurveBall Crypt32.dll Patching
With Powershell, there is a great module you can run that will allow automating the installation of CurveBall Crypt32.dll patching on your Windows machines.
To install the PSWindowsUpdate, use the following one-liner cmdlets in PowerShell on your Windows machines.
Get-PackageProvider -name nuget -force Install-Module PSWindowsUpdate -confirm:$false -force
To run the cmdlet to install updates, you can use the following cmdlet:
Get-WindowsUpdate -Install -acceptall -IgnoreReboot
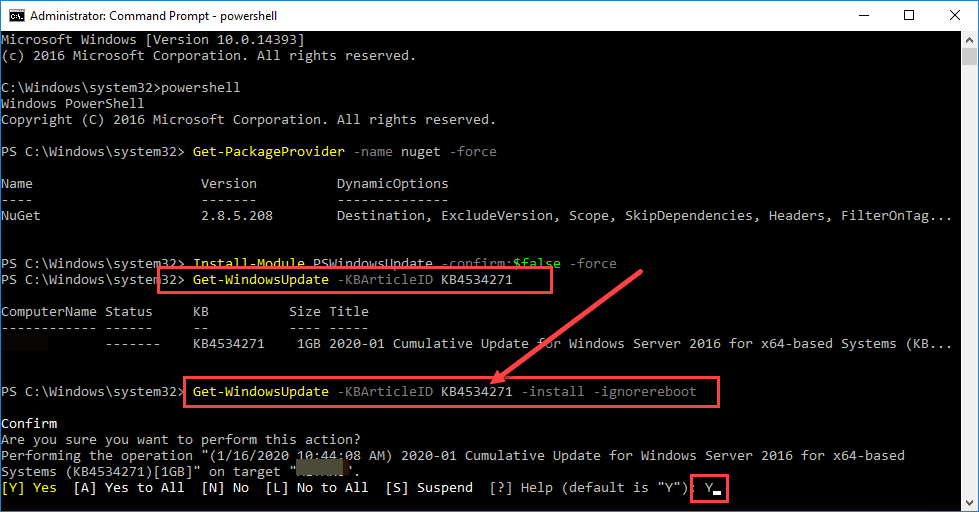
You can also install specific KB articles using the Get-WindowsUpdate cmdlet like so. Below is the KB article of the Windows Server 2016 security patch.
Get-WindowsUpdate -KBArticleID KB4534271
Below I am having to type “Y” to accept, however, you can use the -AcceptAll switch to automatically accept the patch.

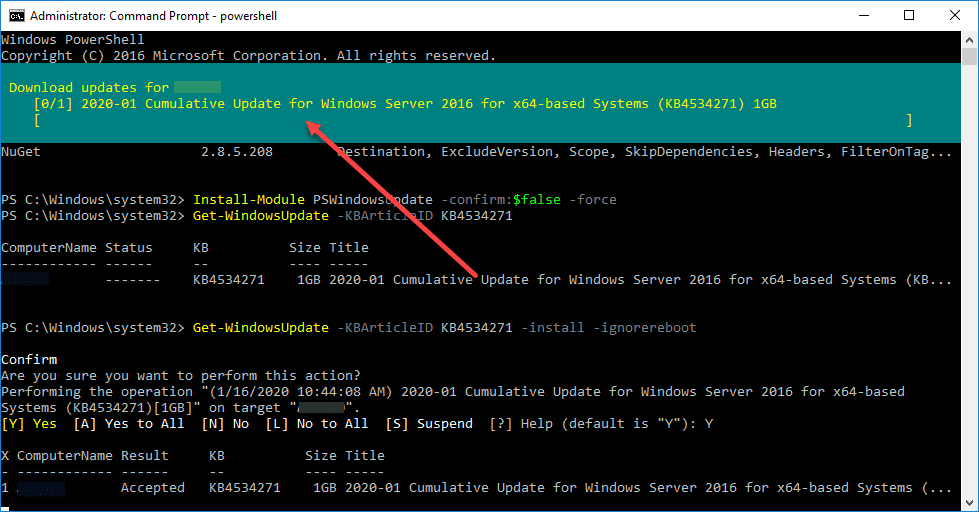
The PowerShell method could be used a number of different ways via PowerShell remoting, Ansible can be used here also, remote tools to remotely run PowerShell scripts, etc. It gives you a lot of options to remotely patch and automate CurveBall Crypt32.dll patching.
Wrapping Up
When it comes to major vulnerabilities that are discovered, patching is generally a necessary action for IT admins. Leveraging automation is your friend when you have many servers to patch and a short time to do it. Using Ansible and PowerShell are two really good ways to automate CurveBall Crypt32.dll patching that allows rolling the relevant patch out in a timely manner.









