Hypervisor Security Best Practices
When it comes to today’s modern infrastructures, most if not all are running some type of hypervisor powered virtual environment in some part of their organization. Virtualization has opened many possibilities for new features and capabilities when it comes to mobility, scalability, and high-availability of workloads. With the nature of virtual environments, the hypervisor host(s) is responsible for running a number of business-critical workloads instead of just one. Since a number of business-critical workloads can be ran on top of a single hypervisor, it is extremely important to ensure that your hypervisor is secured. The consequences of a hypervisor breach can yield many if not all of your resources compromised. In this post, we will take a look at hypervisor security best practices to see what measures need to be taken to ensure your virtual environments are secure.
New Hypervisor Security Threats
We live in a time where security is growing ever more important. Never before have there been so many security threats to your data. With last year’s major debacle with Spectre and Meltdown, organizations and hypervisor vendors are still figuring out new and better ways to mitigate the issue with current processor technology that is found in servers powering most of the virtual environments still in production.
Hypervisor hosts present the perfect environment for this kind of exploitation since they host many business-critical workloads and perhaps from a number of different tenants. Aside from this, there is no shortage of concerns for a virtualization administrator when it comes to security.
Hypervisor Security Best Practices
The following list of hypervisor security best practices is in no way an all-inclusive list, however, they are some of the more important things that you can do at the time of this writing. Let’s take a look at the following hypervisor security best practices:
- Mitigate Spectre and Meltdown
- Patch Hypervisor hosts regularly
- Limit access to hypervisor host management
- Audit access to hypervisor hosts
- Limit network access to hypervisor host management
- Use Virtual Machine Encryption
- Use UEFI secure boot
- Use Virtualization-based security
Let’s take these one by one and describe their importance.
1. Mitigate Spectre and Meltdown
In the beginning of 2018, the IT world was shocked to learn that an alarming vulnerability was found in Intel processors along with a smaller set of vulnerabilities found with AMD processors. These “affectionately” became known as the Spectre and Meltdown vulnerabilities.
This introduced some pretty scary scenarios where attackers could potentially get access to the speculative execution contained in today’s processors and read the data that is contained therein. Things always get more interesting in virtualization environments.
Most hardware vendors have introduced BIOS hardware-level mitigation to help plug the vulnerability associated with the Spectre/Meltdown flaws. Also, hypervisor vendors like VMware and Microsoft have released patches that mitigate these flaws at the hypervisor level. Be sure you are running the mitigate patches and workarounds recommended at the hardware, hypervisor, and operating system level.
Take a look at our posts here on this topic:
- New Intel Vulnerability Foreshadow L1 Terminal Fault VMware Affected
- VMware patches new Intel speculative execution microarchitectural data sampling MDS vulnerability
- 5 Ways to Improve Virtualization Security
- VMware Performance Impact of Meltdown and Spectre Patches
- Roll Back VMware Meltdown and Spectre Microcode Patch
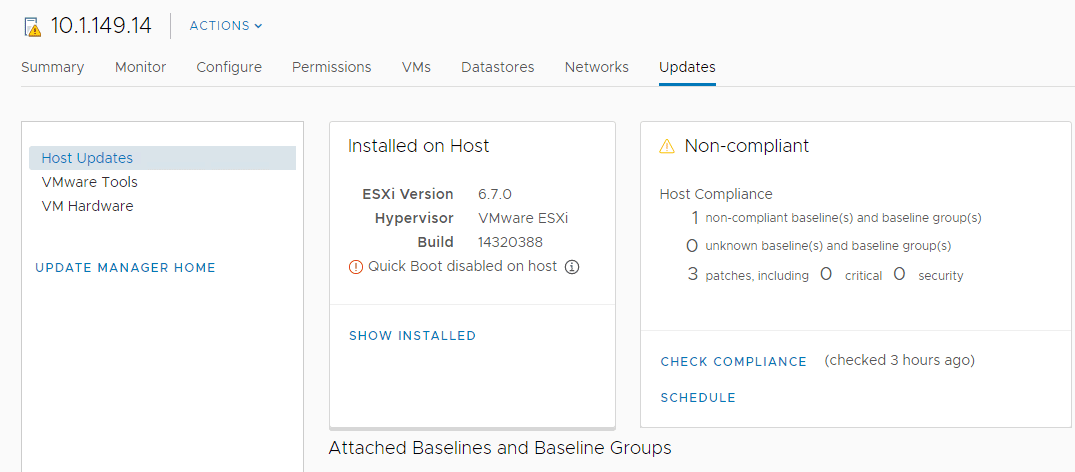
2. Patch Hypervisor Hosts Regularly
This goes without saying, in addition to the emergency type patches as needed by Spectre and Meltdown, you want to always make sure you are keeping your hypervsior hosts at the current patch level.
Regular hypervisor host patching includes the latest security patches that have been released for the newest vulnerabilities. Often when an environment is hacked, it is related to a known vulnerability that has not been patched or mitigated.
Check out the following posts on patching:
- Automated Patching of Microsoft Wormable RDP Vulnerabilities
- Windows Server 2019 Unattended Install Windows Updates
- Upgrade to VMware vSphere ESXi 6.7 Update 2 with Command Line
3. Limit Access to Hypervisor Host Management
A good way to help limit any chance of security compromise to your hypervisor host is to limit hypervisor host management. This means that only those who have a need to manage the hypervior host have credentials to do so. This goes back to the age-old security principle of role-based access and users only having the access they absolutely need.
Having a large number of IT staff that didn’t need access to manage a hypervisor host would be a bad idea from a security standpoint.
Limit Network Access:
- Five Ways to Improve Network Security
- Scan PCI-DSS Network Security Compliance with VMware vRealize Network Insight 4.0
4. Audit Access to Hypervisor Hosts
Auditing access to hypervisor hosts is generally required from a compliance standpoint. This ensures you know who did what, and when they did it. Virtual environments are critical infrastructure and represent a “holy grail” prize for an attacker if they can get management-level access to the hypervisor.
Make sure you are logging access to the hypervisor hosts. Additionally integrating logins with Active Directory or LDAP system allows centralizing your user accounts and allowing the use of specific user accounts for management. This helps give accountability. Generic accounts can make it difficult to investigate potential security breaches or access/actions.
5. Limit Network Access to Hypervisor Host Management
In addition to limiting who has access to manage a hypervisor host, you also want to limit the ways the hypervisor host can be accessed from a network perspective.
Having a dedicated management network that is not accessible from other generalized networks is certainly a security best practice. The harder you make access, the less desirable it is as an easy target.
Having a secure jump box that is used for management helps to limit other pivot points for managing a hypervisor host. Micro-segmenting your network to prevent unauthorized users from accessing network resources goes a long way in helping to prevent security breaches.
- Physical Device Microsegmentation with Extreme Networks Policy
- Monitor Network Traffic with Port Mirror and TAP Port with Palo Alto
- Configure VMware Distributed Switch Private VLANs
6. Use Virtual Machine Encryption
Your data is the most valuable asset that you possess as a business. No one wants to have data stolen or breached. Encrypting your business-critical VMs is a great way to help prevent your data from falling into the wrong hands.
An unscrupulous administrator could copy entire VM disks to removable media and take those offsite to a different environment and have unlimited access to the data they contain.
With virtual machine encryption, this helps to ensure the VM disks are totally unreadable outside of the sanctioned environment they are running in.
Virtualization encryption:
- Configure VMware vSphere Encryption Key Management Server Cluster
- Hytrust VMware Virtual Machine Encryption
- VMware Virtual Machine Encryption Key Management
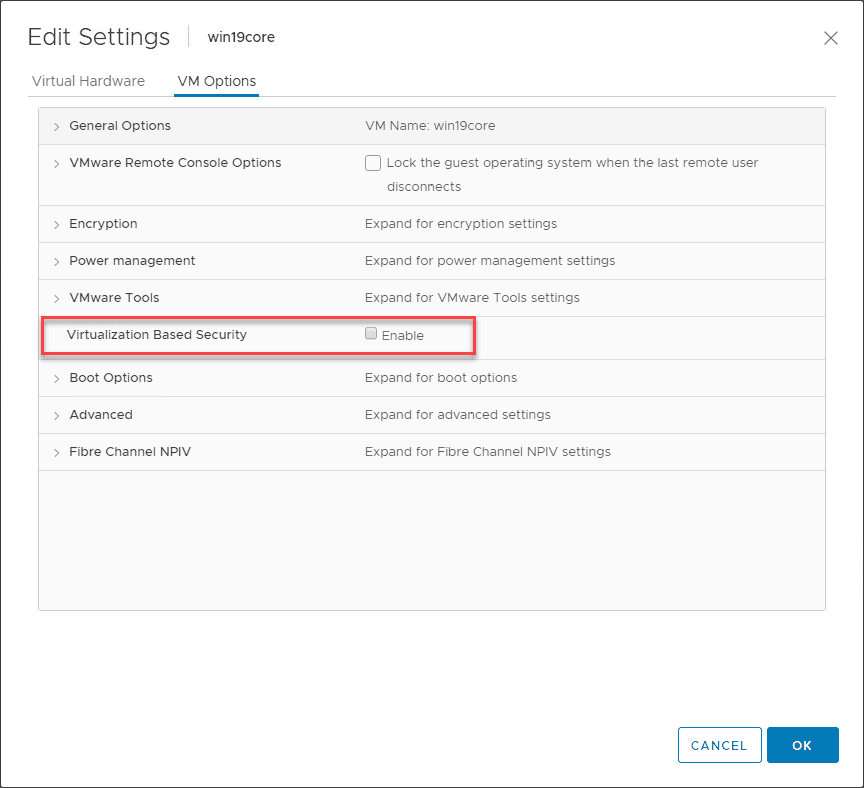
7. Use Virtualization-Based Security
Virtualization-based security helps to protect the most sensitive parts of in-memory data contained in the Windows operating system and helps to ensure that data is in a protected space that cannot be accessed by malware or other code looking to steal password secrets and other sensitive data.
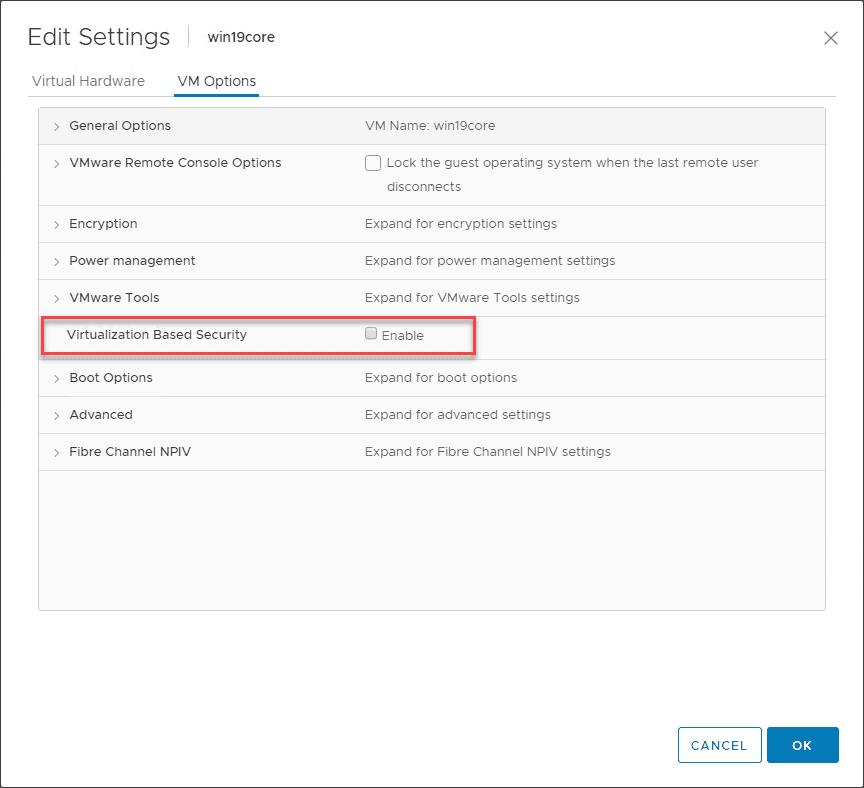
Virtualization-based security or VBS helps to protect these areas of memory by itself using the Hyper-V hypervisor to protect these sensitive areas of memory from even the operating system itself.
Working with Virtualization-based security:
Wrapping Up
There are many hypervisor security best practices to follow. The above-mentioned list is a great place to get started with securing your virtualized environments. Security continues to evolve. However, generally speaking, it most often comes down to the basics of minimizing the attack surface, patching, and monitoring/auditing/securing that makes a huge difference in shoring up security.














