Enable VMware Virtual Machine 802.1X Authentication
As I eluded to in a previous post about NIOC and consolidating my networking in the home lab using vSphere Distributed Switches and Network I/O Control, I had a few projects and testing in mind. One thing I wanted to do was move away from a physical workstation I was using for 802.1X testing. This is problematic from a remote testing standpoint as if something goes wrong with the 802.1X configuration or testing remotely, you will lose connection. Having a test workstation housed in a virtual machine was far more desirable from a lab and testing perspective. I wanted to share my findings in trying to enable VMware Virtual Machine 802.1X Authentication and how I was able to get this to work.
Using a Dedicated Portgroup for Virtual Machine
The first design thought I had in getting a VM up and running for testing 802.1X was to create a VSS portgroup using a specific physical network adapter from my host. My POC didn’t need any kind of fault tolerance since this is just for testing and labbing. Also, since I only have (2) free physical network cards after evacuating and consolidating onto a single VDS, I wanted to have as many possibilities and options so backing this portgroup with a single network adapter made sense. Also, I was ok with the fact that if I had an 802.1X policy that became effective on my switch port, I was OK if the switchport became locked down since it wasn’t backing a more critical port group
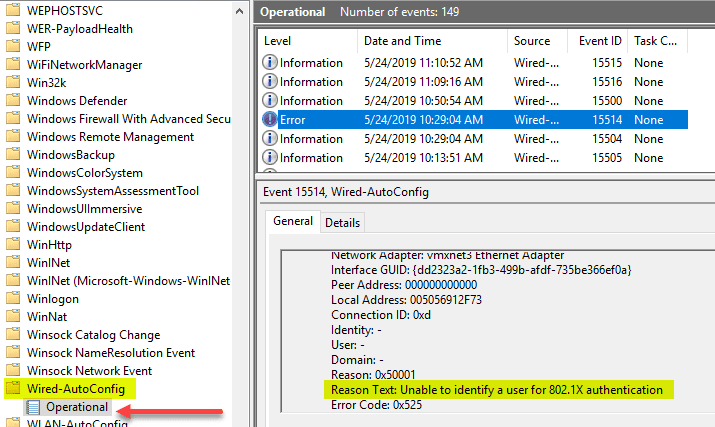
What I did was create a VSS portgroup tagged with one of the standard VLANs I had in my lab network backed by this single connection. This single connection was plumbed into my Extreme x440-G2 switch where I had the 802.1X policy configured. However, no matter what I tried, I was unable to get 802.1X policy to apply to the switch port. Below are a few of the errors I saw during the process. The first error was Unable to identify a user for 802.1X authentication.
Next, we have The network does not support authentication.
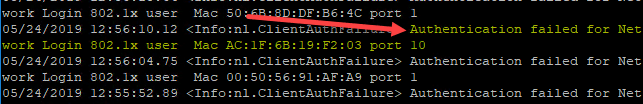
On my Extreme switch, in the logs, I saw the following: Authentication failed for Network Login 802.1x user with the MAC.
Also, as I detailed in this NPS troubleshooting post for Windows Server 2019, I looked in the NPS logs to see if authentication was passing through and was getting no activity.
I wasn’t able to grab a Wireshark trace of the traffic for this particular session but will do that soon and will most likely encapsulate the finds in another post. I was able to get this to work however. How?
VMware ESXi NIC PassThrough for 802.1X Authentication
After thinking a bit about this, the next move I wanted to try to eliminate the default VMware networking with a standard portgroup as the culprit was to remove the single physical adapter from the VSS portgroup and configure it as a PCI passthrough device. After configuring this, I would attach it to the VM as the network controller for the VM and use this for 802.1X testing to see what happens.
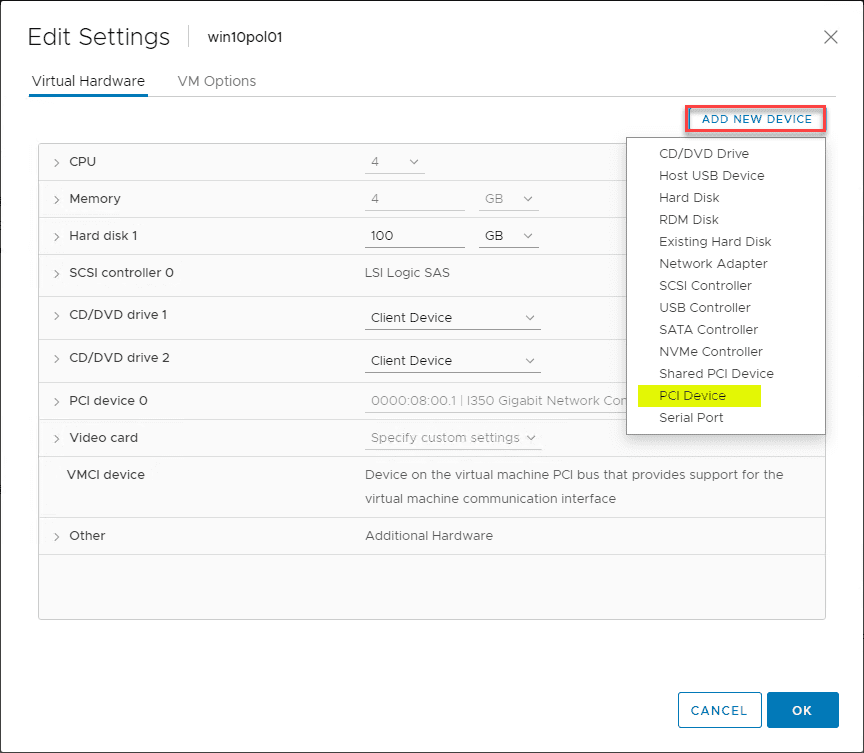
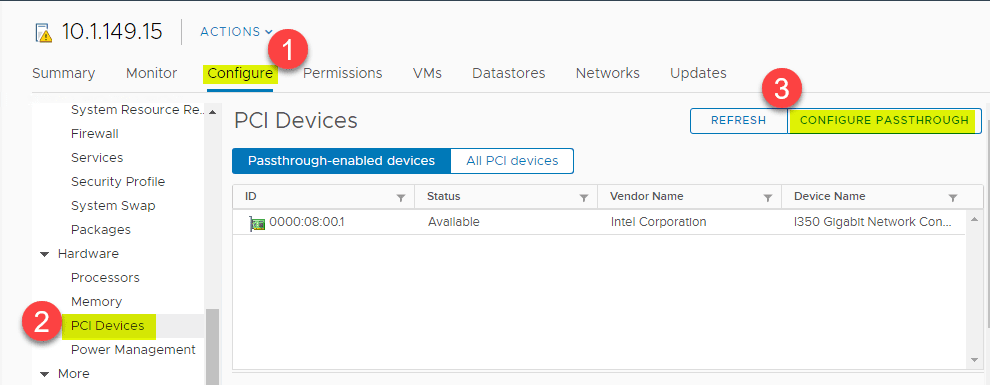
The steps to enable PCI PassThrough for a physical NIC adapter on the ESXi host is fairly straightforward. To do this, navigate to the ESXi host > Configure > Hardware > PCI Devices > Configure PassThrough.
Select the specific PCI device you want to passthrough to the virtual machine. In my case it is the Intel i350 Gigabit Network controller found on the host.
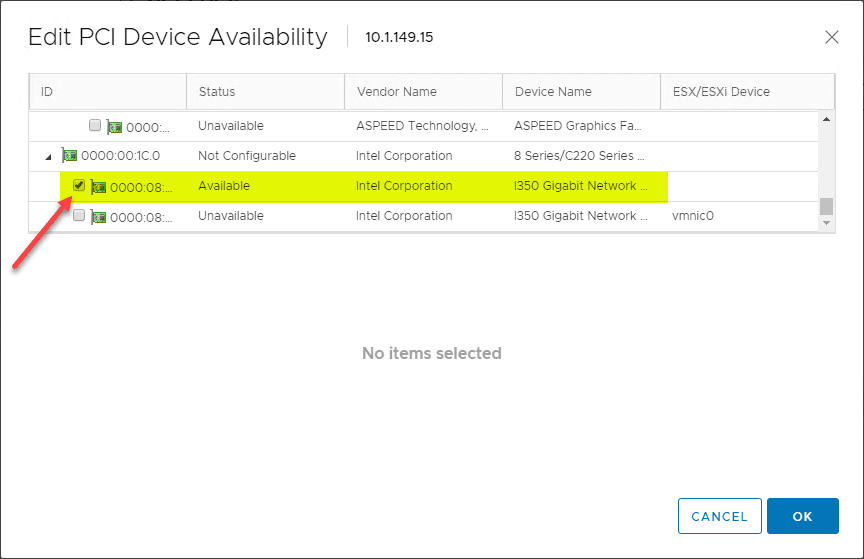
***NOTE*** It is important to know that you must reboot the ESXi host after enabled passthrough on a PCI device.
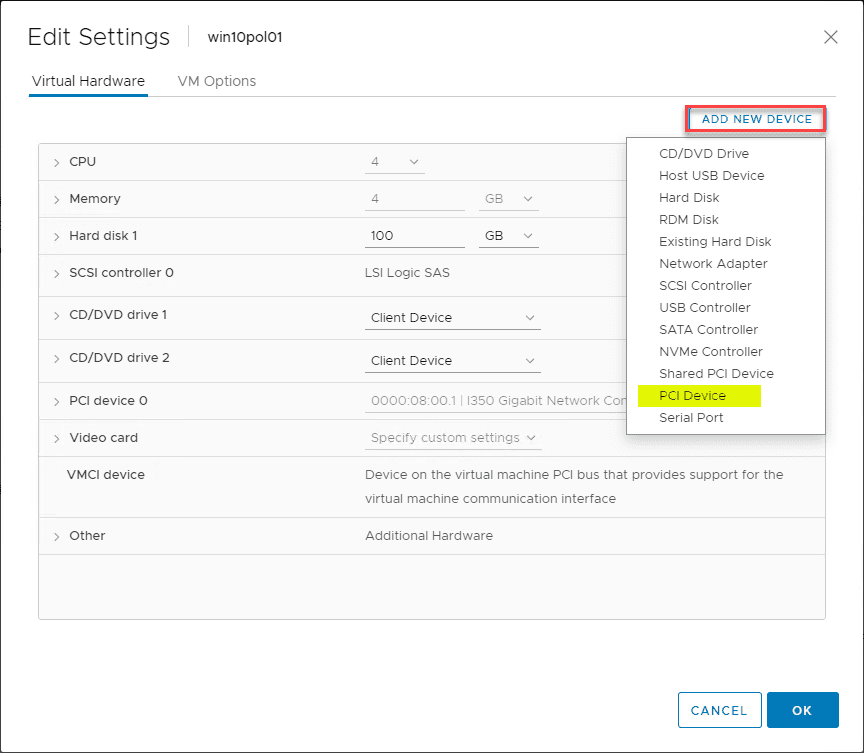
After I rebooted my host, I navigated to the properties of the virtual machine, clicked Add New Device > PCI Device and the Intel card was the only option available. I added it and applied the changes.
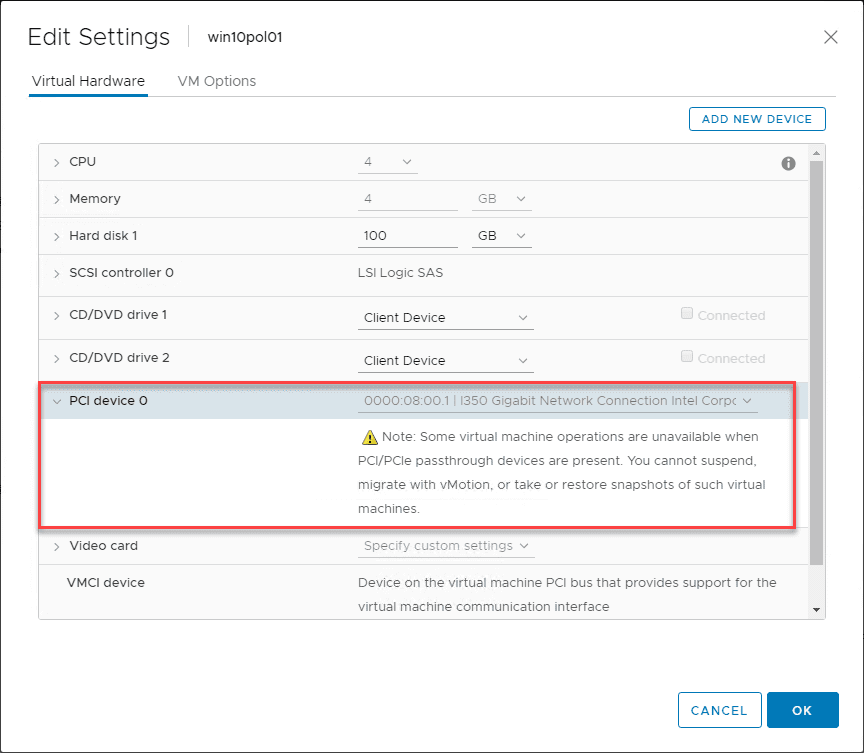
The card is successfully added. As noted here in the properties of the VMware virtual machine properties, you need to be aware of a few considerations when you PassThrough physical PCI devices. Some virtual machine operations are unavailable when PCI/PCIe passthrough devices are present. You cannot suspend, migrate with vMotion, create, or restore snapshots.
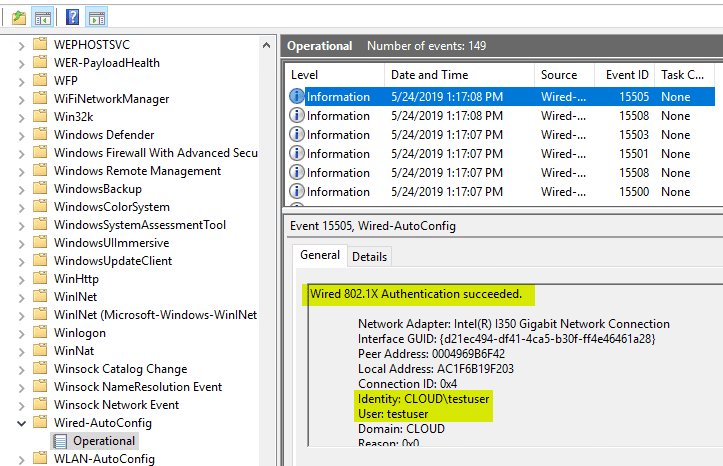
Now, when logging into the VMware virtual machine, 802.1X authentication works as expected. As you can see in the Wired-AutoConfig log, the identity and user are correctly pulled and authenticated via RADIUS.
Wrapping Up
For now, I am content with the PCI passthrough configuration of the host network adapter for my 802.1X labbing and POC on a VM. If you have another way you have been successful to Enable VMware Virtual Machine 802.1X Authentication, please let me know your solution. This post is simply my first stab at doing this with a VM for my particular use case, however, perhaps it is not the best way to accomplish this. The beauty of a home lab and labbing in general is learning by trial and error which I love to do. For me this was a success at least to see what worked and what did not work in initial testing. I will keep this post updated with any additional thoughts or findings, or possibly another blog post describing any major new developments.







You are Awesome