-
home lab
15 Weekend-Ready Ansible Playbooks for Your Home Lab
I’ve spent countless weekends automating every corner of my home lab, and nothing feels better than kicking back on Monday morning knowing that routine tasks and projects in the home lab ran themselves over the…
Read More » -

-

-
-

Latest articles
-
Networking
Home Lab Create a DMZ VLAN
A really cool fun project I have been wanting to take on at home for a while now is to…
-
Networking

Dell NSeries Switch Basic configuration cheat sheet
In working recently with a few Dell NSeries switches on the bench and in production, I have created a simple…
-
Security
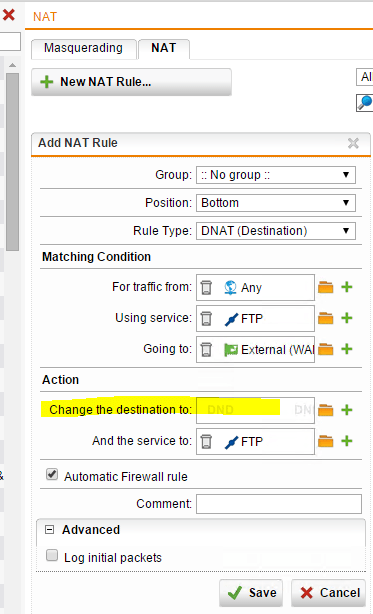
Configure Sophos UTM to work with Filezilla FTP Server
If you are running Sophos UTM at home and would like to use FileZilla FTP server, there are a few…
-
ActiveDirectory
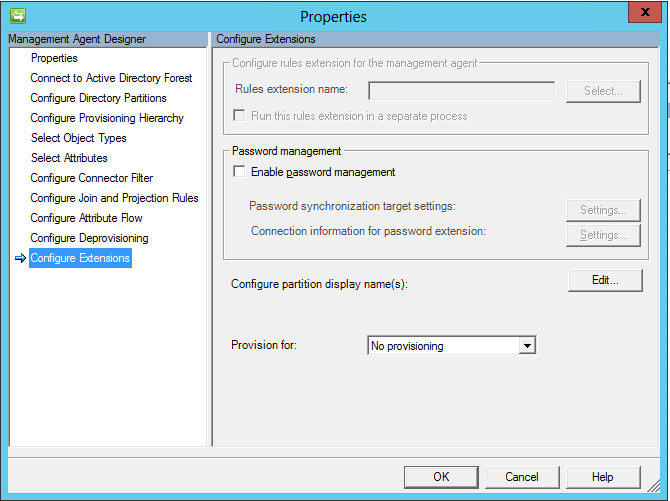
How to Sync Passwords between Child and Parent Domain with FIM 2010 R2
For those of you in a multi domain environment due to the structure of your company or from migrations from…
-
Networking
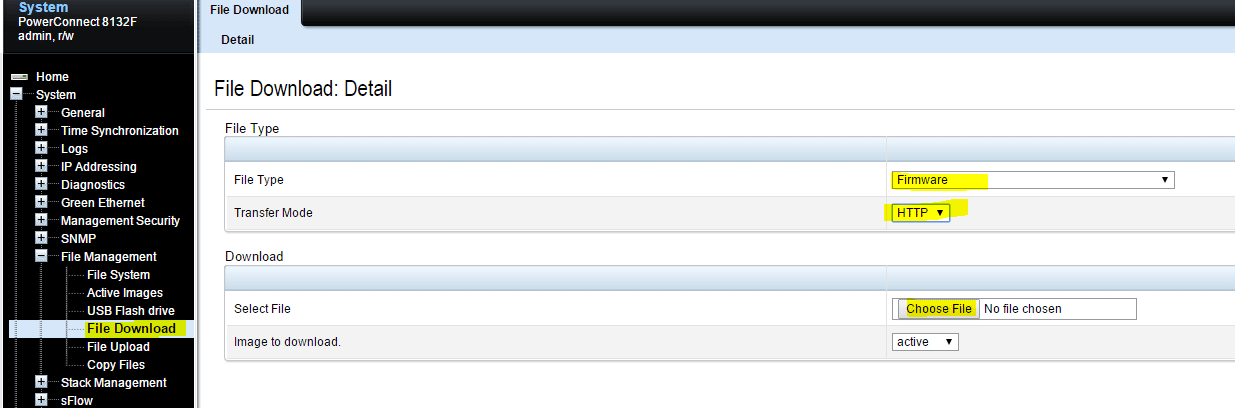
Basic Dell Powerconnect Nseries iSCSI switch configuration
Recently, I got my hands on a couple of Dell PowerConnect 8132f switches for a client to configure for iSCSI traffic…
-
Networking
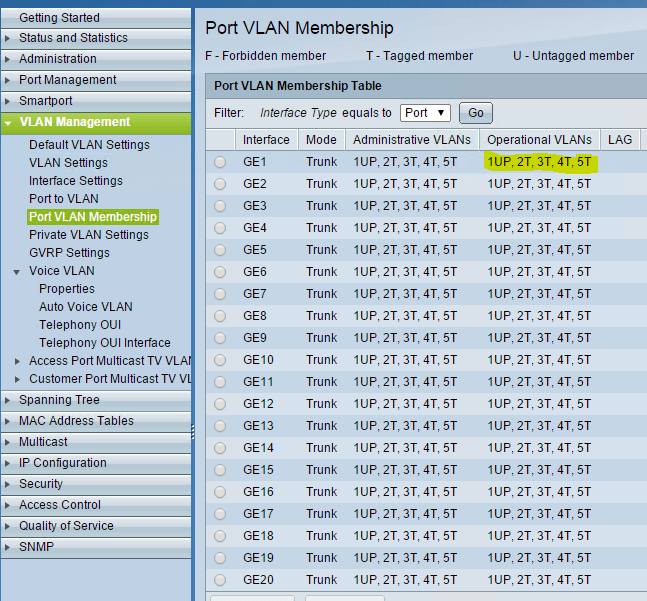
Setting up VLANs Cisco SG300-20 Switch
The Cisco SG300-20 Switch is a great home lab switch that features most of the capabilities that ones see and…
-
Hyper-V
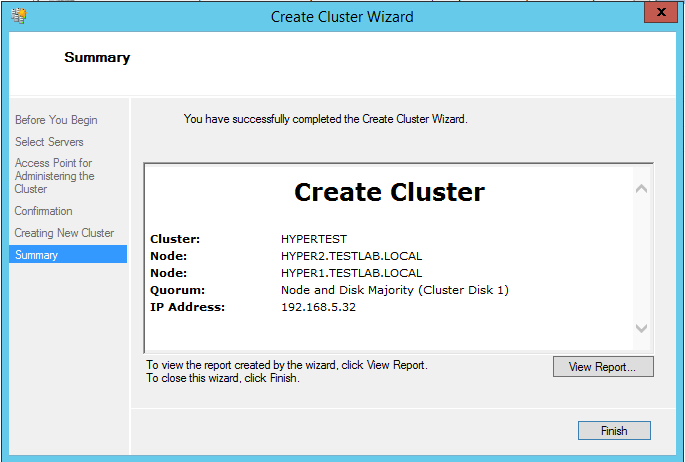
Setup a Hyper-V Cluster Lab in VMware Workstation
Setting up a Hyper-V cluster lab in VMware Workstation is not too difficult and can easily be accomplished in a…
-
vSphere 6
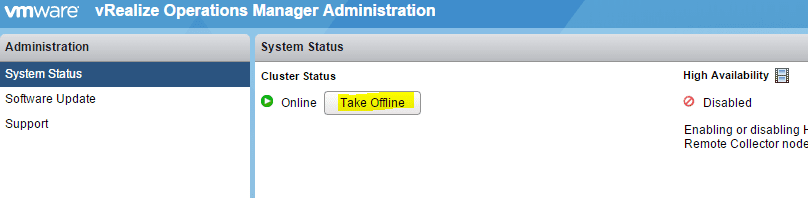
Change vRealize Operations Manager 6.01 appliance IP Address
Recently in upgrading a production vSphere 5.5 environment to 6.0, I have been working through the individual infrastructure pieces left…
-
vSphere 6
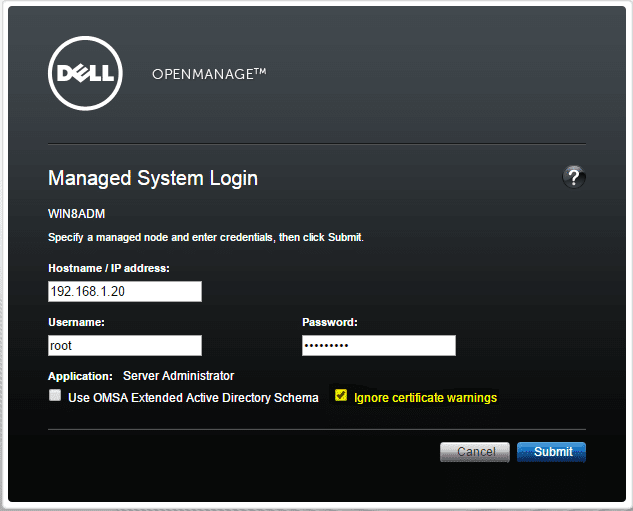
Install Dell OMSA 8.1 in ESXi 6.0 and add to OME
Recently, after upgrading a Dell Cluster to vSphere 6.0, one of the tasks that I wanted to accomplish was to…