DHCP Snooping configuration: Protect against Rogue DHCP Servers

DHCP snooping is a really good security feature on many switches that helps to make sure only trusted DHCP messages are allowed across your network. Let’s look at how it works and how you can configure it.
What is DHCP snooping?
The DHCP snoop mechanism, is a way that allows you to be able to monitor DHCP messages across the network and the environment in general. When one of your client devices makes a DHCP request to grab an IP address from a DHCP server, the reply for that request should be able to come from only an authorized source that you define. In most cases in a business environment, this is the corporate DHCP server, or home lab DHCP server if you are operating one in your environment.
Below is a trusted DHCP server that is allowed to hand out DHCP IP addresses.
How it works
When it is enabled, the network switch takes a look at DHCP traffic. It can identify and filter out malicious DHCP messages if these are seen from untrusted sources. This is configured by a DHCP snooping binding table. This table records a mapping of each connected device’s MAC address, IP address, lease time, and associated VLAN. This helps you to know that DHCP is being handled only by authorized DHCP servers.
Also, you can define a trusted port where an authorized DHCP message are allowed to come from. The other ports are viewed as untrusted. If DHCP offers are seen coming across untrusted ports, these can be blocked.
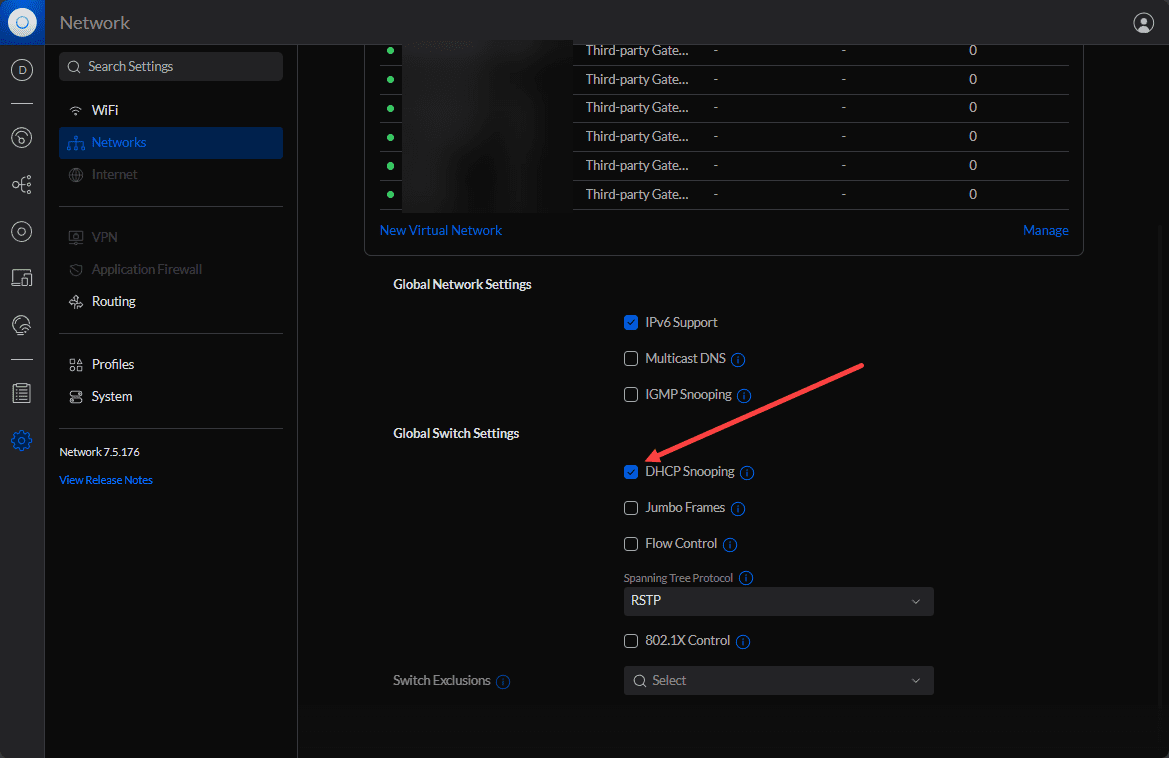
Below is a look at the Unifi Network application with DHCP snooping turned on globally for switches.
Terms to note
- Enabling DHCP Snooping: To activate DHCP snooping, most switches have a command similar to
ip dhcp snoopingcommand (familiar in Cisco IOS) - Trusted and Untrusted Ports: Trusted ports are marked for authorized DHCP servers, while other ports are marked as not trusted and are usually the ports marked towards end user devices.
- Snooping for VLANs: these can be setup for all vlans you are running on you can configure it for specific vlans in the network
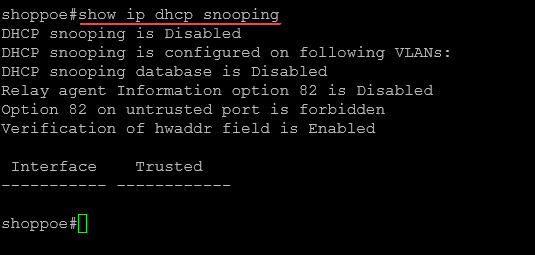
- DHCP Snooping Database: In the realm of Cisco devices, you can view the DHCP snooping DB using the command
show ip dhcp snooping. In there you can see the current DHCP snooping database, and details about leased IP addresses and their MAC addresses.
Below is a look at command:
show ip dhcp snoopingIn the switch below, the snooping configuration is disabled.
Configure DHCP snooping
Let’s look at a few steps to enable this feature in the realm of a Cisco switch which is a common piece of networking gear in the enterprise today.
Step 1: Connect to the switch
First, you need to remote into your switch. You can do this using a console cable, SSH, or Telnet (hopefully not), depending on your device configuration.
Step 2: Entering Global Configuration Mode
Once logged in, enter the global configuration mode by typing the command in the CLI:
configure terminalor
conf tStep 3: Enabling DHCP Snooping Globally
In the global configuration mode, enable DHCP snooping for the entire device by typing the command:
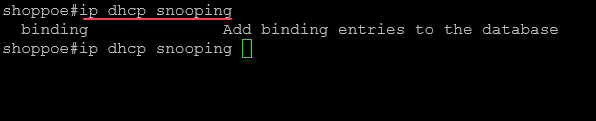
ip dhcp snoopingYou can also view the commands in the non-global configuration and global configuration modes.
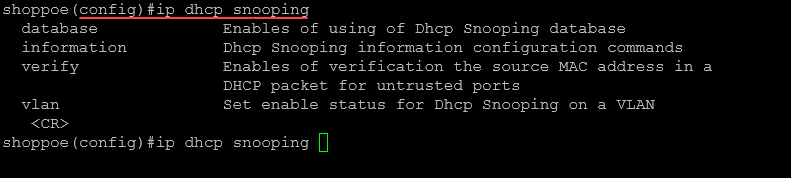
Below are the options you see with the ip dhcp snooping command outside of global configuration mode.
In global configuration mode, you will see the following:
Step 4: Enabling DHCP Snooping on VLANs
To enable DHCP snooping on specific VLANs, use the following command:
ip dhcp snooping vlan [VLAN_NUMBER]Replace [VLAN_NUMBER] with the actual VLAN number(s) you want to enable DHCP snooping on.
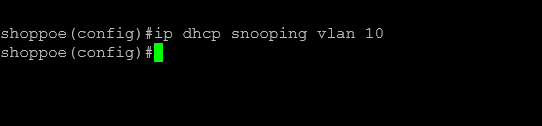
For example, for VLAN 10, you would type:
ip dhcp snooping vlan 10If you need to enable it on multiple VLANs, separate the VLAN numbers with a comma or specify a range.
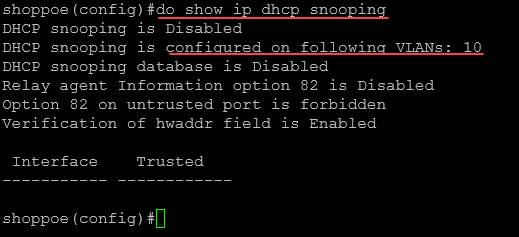
After enabling on vlan 10, you can run the following command to view the status of DHCP snooping on your switch if you are still in global configuration mode:
do show ip dhcp snoopingStep 5: Specifying Trusted Interfaces
By default, all interfaces on a Cisco device are untrusted for DHCP snooping. You need to specify which interfaces are trusted manually. A trusted interface is typically connected to a legitimate DHCP server or another trusted switch. To mark an interface as trusted, go to the interface configuration mode and type:
config t
interface [INTERFACE_TYPE/NUMBER]
ip dhcp snooping trustReplace [INTERFACE_TYPE/NUMBER] with your specific interface identifier, like GigabitEthernet0/1. Below, I am using a small business switch. The interface is gi1.
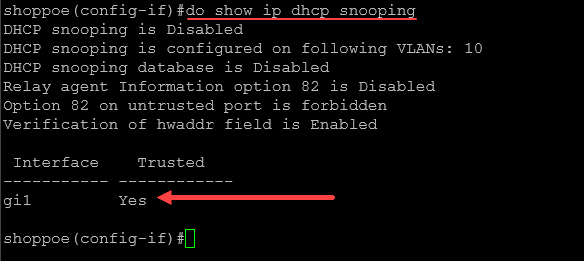
After we add the ip dhcp snooping trust for the interface, we can check the interface with the command:
show ip dhcp snooping
## in global config mode
do show ip dhcp snoopingStep 6: Optional Configurations
Rate Limiting DHCP Traffic: You can limit the number of DHCP packets on untrusted ports to prevent DHCP flooding attacks. Use the command:
ip dhcp snooping limit rate [PACKETS_PER_SECOND]Replace [PACKETS_PER_SECOND] with the desired rate limit.
Step 7: Saving the Configuration
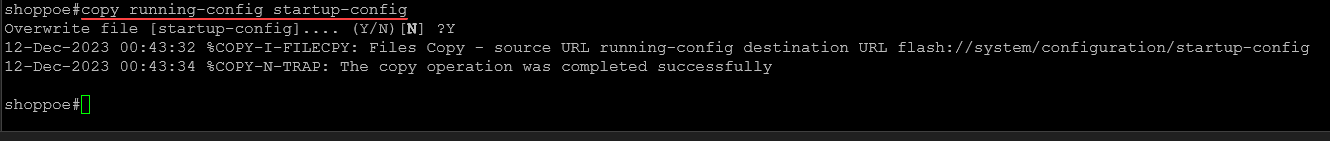
After configuring DHCP snooping, save your settings by exiting to the privileged EXEC mode and typing:
write memoryor
copy running-config startup-configReal-World Application
Note the following use cases that can help understand the benefits of DHCP snooping protection and how it can be used.
- Corporate Network: In a corporate setting, it is important to help protect the network from unauthorized DHCP servers
- University Campus Network: Educational institutions often have large and complex networks. Here, DHCP snooping can be used to segment different parts of the network, like administrative offices, classrooms, and student dorms. It helps to make sure the DHCP server comes from an authorized source provided by the educational institution IT department.
- Internet Service Providers (ISPs): ISPs use snooping to manage residential or business customers. It helps prevent malicious users from setting up unauthorized DHCP servers
- Data Centers: In data center environments, where hosting multiple clients on shared infrastructure, it can be used to prevent one client’s DHCP server from serving IP addresses to another client’s network. This isolation helps make sure security for each client hosted in the data center is protected
- Wi-Fi Networks in public: Protect against rogue DHCP servers into the network on public wi-fi. This is important as Wi-Fi networks are often attacked using these types of attacks
Rogue DHCP Servers
As we have mentioned, a rogue DHCP server can disrupt network operations by issuing incorrect IP addresses. These unauthorized servers are effectively blocked from impacting the network by turning on DHCP snooping. The DHCP snooping binding database verifies the authenticity of DHCP messages. Note the following advanced features:
Advanced Features
- IP Source Guard: IP Source Guard provides additional security by ensuring that IP traffic is received from the legitimate source.
- Dynamic ARP Inspection (DAI): DAI prevents malicious ARP spoofing attacks, further fortifying network security.
Wrapping up
DHCP snooping is a great feature to make sure you turn on in the network. It helps to make sure that only servers that are authorized to act as a DHCP server, can do that. If a rogue server is added to the network, either accidentally or intentionally, DHCP snooping will keep this from disrupting the network and make sure attackers can’t compromise the network using this type of attack.