How should you secure your home wireless network for teleworking

Even though companies are starting to tighten down on who can work remotely and where hybrid work happens, it is still being leveraged like never before. Workers are at least working remotely part of the time, which means that sensitive information and data are subject to the security of the network the workers connect to. It often means the security of their home wireless network. Let’s consider how should you secure your home wireless network for teleworking and understand the security precautions that need to be taken.
Table of contents
- Part 1: Home Internet Connection, Gadgets, and Dividing Areas
- Part 2: The Power of a Strong Password and Security Measures
- Part 3: Making Your Network Stronger with Secret Internet Paths (VPNs)
- Part 4: Advanced Security Measures: MAC Address Filtering
- Part 5: Keep devices updated
- Part 6: Guest networks and two-factor authentication
- Part 7: Regular Monitoring
- Home Network Security Overview
- Keep security in mind
Part 1: Home Internet Connection, Gadgets, and Dividing Areas
Your home Internet connection is like the main road for your work-from-home setup. It lets many things like computers,mobile devices, smart gadgets, and Internet-connected things talk to the web. Knowing the parts of your network and what’s hooked to it is the first step to ensuring it’s safe.
Wi-Fi routers and Internet connectivity
Wi-Fi routers, usually given by the company that brings the Internet to your house, are like the door between your home Internet and the big Internet out there. They send information from the web to the right gadgets in your house and the other way around. This big job makes them a key spot for bad people to try to break in. So, knowing how they work and how to secure them is really important.
Get familiar with the security settings offered by your device, including the wireless encryption capabilities, additional security features like multi-factor authentication, and other types of filtering.
VLANs and segmentation
Use VLANs to segment your network. Don’t have IoT and general home devices on the same network or wireless network as your remote teleworking network. VLANs logically separate network traffic using network encapsulation so that traffic on one VLAN cannot be accessed from traffic on another VLAN.
Part 2: The Power of a Strong Password and Security Measures
Password security is fundamental to home Wi-Fi network protection. Hackers can guess or crack passwords with relative ease, leaving your network vulnerable to unauthorized access and cyber-attacks. Strong passwords and comprehensive network security measures can help shield your network from such threats.
The Importance of a Solid Wi-Fi Password
A Wi-Fi password that’s hard to crack should combine a mix of uppercase and lowercase letters, numbers, and special characters (symbols). This mix makes it difficult for anyone trying to guess or break it.
Change the defaults
Commodity routers, switches, access points, and other gear often have well-known and documented default passwords out of the box. ALWAYs change these default passwords on your home wireless gear and networks. Leaving these known defaults is extremely dangerous and will most definitely lead to compromise.
Part 3: Making Your Network Stronger with Secret Internet Paths (VPNs)
Virtual Private Networks, or VPNs, are like a special secret road on the Internet that makes everything more secure, and they’re really handy when you’re not in the office.
How VPNs Help When You’re Working Away from the Office
VPNs take all the information going between your computer or gadget and the VPN spot and mix it up so it can’t be read. If a person with bad intentions grabs your information, they’ll find it’s all jumbled up. Using a VPN when you’re working somewhere other than the office makes sure that important work stuff is sent safely, even over your home Wi-Fi.
Part 4: Advanced Security Measures: MAC Address Filtering
Devices that connect to computer networks have a unique identifier known as a MAC address. The MAC address is a layer 2 address that you can use to filter connectivity and secure connectivity to your SSID at home. You can specify which MAC addresses are allowed to connect. Keep in mind that MAC addresses can be spoofed as well so this shouldn’t be relied upon as a sole means of security, but rather as one of the layers of security on your network.
Minimizing the Attack Surface with MAC Address Filtering
By enabling MAC address filtering, you’re effectively restricting network access to a set list of devices. This strategy helps reduce the attack surface.
Part 5: Keep devices updated
Regular updates are one of the best things you can do for security, even at home. Wi-Fi router and other network devices need to be updated like other devices. This includes firmware, etc. These updates will often patch identified security vulnerabilities. So, these are very important.
Part 6: Guest networks and two-factor authentication
Guest networks and two-factor authentication (2FA) are two other ways you can improve your home wireless network’s security. These measures further prevent malicious intent, secure your connection, and protect sensitive data.
A guest network is a separate network on your Wi-Fi router that connects visitors in your to access the Internet without them being connected to the main wireless network where your devices are connected. This segregation protects your main network and its connected devices from potential threats that guests’ devices may pose.
Enforcing Two-Factor Authentication
One of the best ways that you can secure any type of password is using 2FA. Many Wi-Fi vendors allow you to enable 2FA for the management interface and some even allow 2FA access when accessing the wireless network. This may delve more into enterprise feature sets available in more high-end devices, but it drastically increases the security of your password authentication across the board.
Part 7: Regular Monitoring
Regular monitoring and auditing of your home network can help you identify any anomalies or potential threats, such as unfamiliar devices connected to your network or unusual network activity.
Recognizing and Addressing Network Anomalies
You can quickly notice and address any irregularities by staying aware of all the devices connected to your home Wi-Fi network and the data traffic they generate. Immediate action can range from disconnecting unfamiliar devices to modifying network security settings or even alerting your ISP or a cybersecurity professional if necessary.
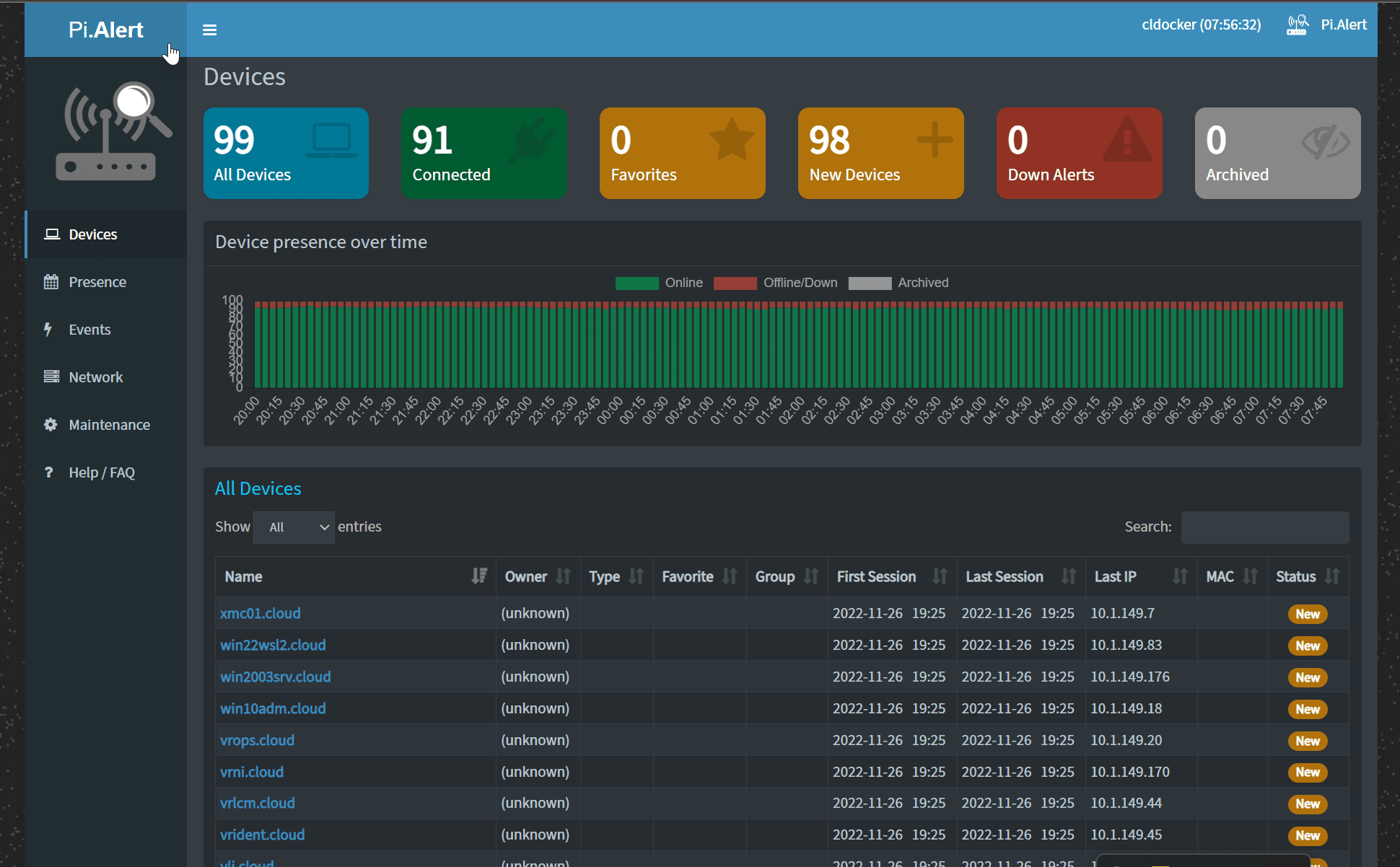
Using a solution like Pi-Alert helps to monitor what is happening on your network. It will send you a message when new devices come online or devices change.
Home Network Security Overview
Keep security in mind
Securing your home wireless network is extremely important as remote work continues to blur the line between professional and personal life. Protecting your home network is not merely about safeguarding your sensitive data but also about contributing to your organization’s overall cybersecurity stance and protecting against escalating cyber threats.
When thinking about How should you secure your home wireless network for teleworking, Implementing the discussed security measures — from setting strong passwords, using a VPN, enabling MAC address filtering, keeping devices and networks up-to-date, setting up guest networks, and enforcing two-factor authentication — is critical in securing your home for remote work. Aligning with best practices helps ensure a secure connection, allowing you to focus on productivity without worrying about cybersecurity risks.