Critical Veeam Backup & Replication Vulnerability Found Patch Now
It is never a good thing when you have a critical vulnerability on your hands and one that allows an attacker to compromise your environment, uploading malicious code. However, over the weekend, Veeam disclosed two very serious vulnerabilities that affect their flagship solutions, including Veeam Backup & Replication and Veeam Agent. Let’s take a closer look at Critical Veeam Backup & Replication vulnerability found, what is affected, workarounds, and patch downloads. This will be a high priority to get updated in your environment as soon as possible.
Critical Veeam Backup & Replication vulnerability in 9.5, 10, and 11
There are two CVEs that affect Veeam Backup & Replication and account for two of the three critical Veeam Backup & Replication CVEs, and the most serious of the products affected. The Critical Veeam Backup & Replication vulnerability notes include:
- CVE-2022-26500, CVE–2022-26501 – These two CVEs relate to Veeam Backup & Replication allow executing malicious code remotely without authentication. This may lead to gaining control over the target system. This carries a CVSS rating of 9.8 and is classified as Critical.
- Cause? – The vulnerability is caused by the Veeam Distribution Service, running on TCP 9380 by default, allows unauthenticated users to access internal Veeam API functions. An attacker may send input to the Veeam API which may allow uploading and executing malicious code
Veeam has published patches for Veeam 11a and 10a. These are noted by the following versions:
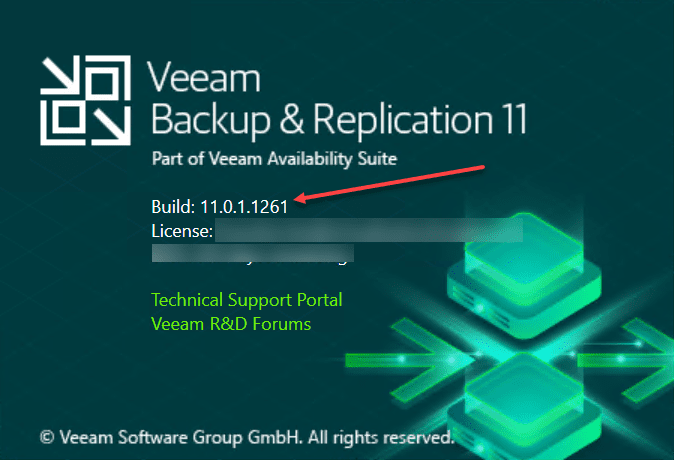
- Veeam Backup & Replication 11a – Build 11.0.1.1261 P20220302
- Veeam Backup & Replication 10a – Build 10.0.1.4854 P20220304
Below is an unpatched Veeam Backup & Replication 11 server running the 11.0.1.1261 release without the P20220302 patch and is subject to the new Critical Veeam Backup & Replication vulnerability.
Veeam has published a few notes about the patches for Veeam Backup & Replication, including the following:
- You need to install the patch on the VBR server. Any managed servers running Veeam components will automatically be updated after installing the patch
- If you are planning on deploying Veeam Backup & Replication 11 or 10, make sure you are using the ISO images that contain the fixes. These include ISO images dated 20220302 or later.
- Unfortunately, it does not appear there will be a patch for Veeam Backup & Replication 9.5. Veeam simply notes these will need to be upgraded to a supported version.
The Critical Veeam Backup & Replication vulnerability was disclosed privately by Positive Technologies.
Workaround
If you are feeling the pressure to get the fixed versions in place and may not have a maintenance window for a few days/weeks, there is a documented workaround. Veeam says that stopping and disabling the Veeam Distribution Service, a service on the VBR server and any servers earmarked as distribution servers in Protection Groups.
Fixed versions download:
Unfortunately, the Critical Veeam Backup & Replication vulnerability was not the only vulnerability disclosed. There is another high-priority vulnerability affecting the Veeam Agent.
Veeam Agent Vulnerability – CVE-2022-26503
The next CVE-2022-26503 relates to the Veeam Agent. What is affected by the Veeam Agent vulnerability? The vulnerability is found in Veeam Agent for Microsoft Windows and allows local privilege escalation. An attacker who successfully exploits this vulnerability could run arbitrary code with LOCAL SYSTEM privileges.
- The CVSS score is rated 7.8 which is a High on the vulnerability scale.
What is the cause of the vulnerability with Veeam Agent?
- The Veeam Agent for Microsoft Windows uses Microsoft .NET data serialization mechanisms. A local user may send malicious code to the network port opened by Veeam Agent for Windows Service, TCP 9395 by default, which will not be deserialized properly and allow malicious compromise of the system.
The fixed versions are as follows:
- Veeam Agent 5, build 5.0.3.4708
- Veeam Agent 4, build 4.0.2.2208
Take note of the following guidance from Veeam on remediating your Veeam Agents:
- If you are running the standalone version of Veeam Agent for Microsoft Windows (not managed by Veeam Backup & Replication) the patched release will need to be manually installed on each Veeam Agent machine.
- If your Veeam Agents are managed by Veeam Backup & Replication, you can upgrade your Veeam Agents from the Veeam Backup & Replication Console after installing the cumulative Veeam Backup & Replication patches. Ideally, install the remediated version of VBR that fixes the new critical vulnerabilities and then upgrade your Veeam Agents from there. You can also upgrade the Agents automatically if the “auto-update backup agent” setting is enabled.
- If you are running a Veeam Agent version prior to v4 or v5, you need to upgrade to a supported version to fix the vulnerability.
The vulnerability was also disclosed by Positive Technologies.
Workaround
Unfortunately, there is no workaround for the Veeam Agent vulnerability as there is with the Veeam Backup & Replication critical vulnerability. Customers will need to prioritize getting the Veeam Agent upgraded on all affected Veeam Agent clients to remediate the vulnerability.
Fixed version download
Final Notes
Organizations recently dealt with another critical vulnerability, the Apache Log4j library vulnerability, leaving many businesses scrambling to patch vulnerable systems. The critical Veeam Backup & Replication vulnerability undoubtedly needs to be addressed as soon as possible along with the high-priority Veeam Agent vulnerability. Veeam is arguably the most common backup vendor you see in the enterprise data center. So, this will be a high priority for most organizations this coming week.