Easy vCenter Server two-factor authentication without ADFS
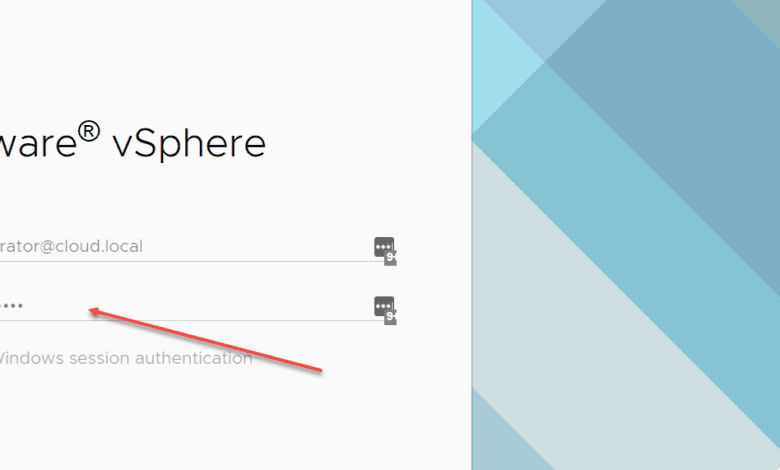
One of the new features added in vSphere 7 is the new identity federation component that allows organizations to point vCenter Server to an external identity source for the authentication workflow. This adds new possibilities for multi-factor authentication. However, currently, only Active Directory Federation Services (ADFS) is supported by the new identity sources component. What if your organization is not using ADFS? If you aren’t, standing up ADFS for multi-factor authentication in vCenter Server is overkill. Let’s see how you can implement easy vCenter Server two-factor authentication without ADFS.
Why not stand up ADFS for 2FA in vCenter Server?
If you don’t have the need for ADFS federation functionality for other services in the environment, it is a lot of complexity to stand this up simply for 2FA on your vCenter Server. If you do have ADFS, then it makes a lot more sense to simply create a new group application in ADFS for vCenter and proceed using ADFS.
Another consideration for ADFS with vCenter is you need to be running vCenter 7.0 or higher. For many environments, they may still be on VCSA 6.5 or 6.7. This leaves out those environments for integrating with ADFS to gain the MFA benefits.
So, if either you don’t have ADFS or you are not running vCenter Server 7.0 or higher, there is a much easier way to stand up two-factor authentication with vCenter Server. As a note, the method shown below works equally well on a VCSA 7 appliance and is the appliance shown in the configuration.
Easy vCenter Server two-factor authentication without ADFS
To do this, we will use a simple protected application using Duo Security. You can sign up for a free Duo account and create a protected application to protect your vCenter Server. The steps to implement two-factor for your vCenter Server include the following:
- Create a new Duo protected application
- Deploy the Duo Proxy appliance
- Configure Duo Proxy with application information
- Point vCenter Server LDAP connection to the Duo proxy
- Test the vSphere Client login to ensure two-factor prompts
Prerequisites
- You need a Duo account
- The user that will log into vCenter needs to be enrolled in Duo
1. Create a new Duo protected application
After logging into your Duo account, navigate to your Applications and Protect an Application button.
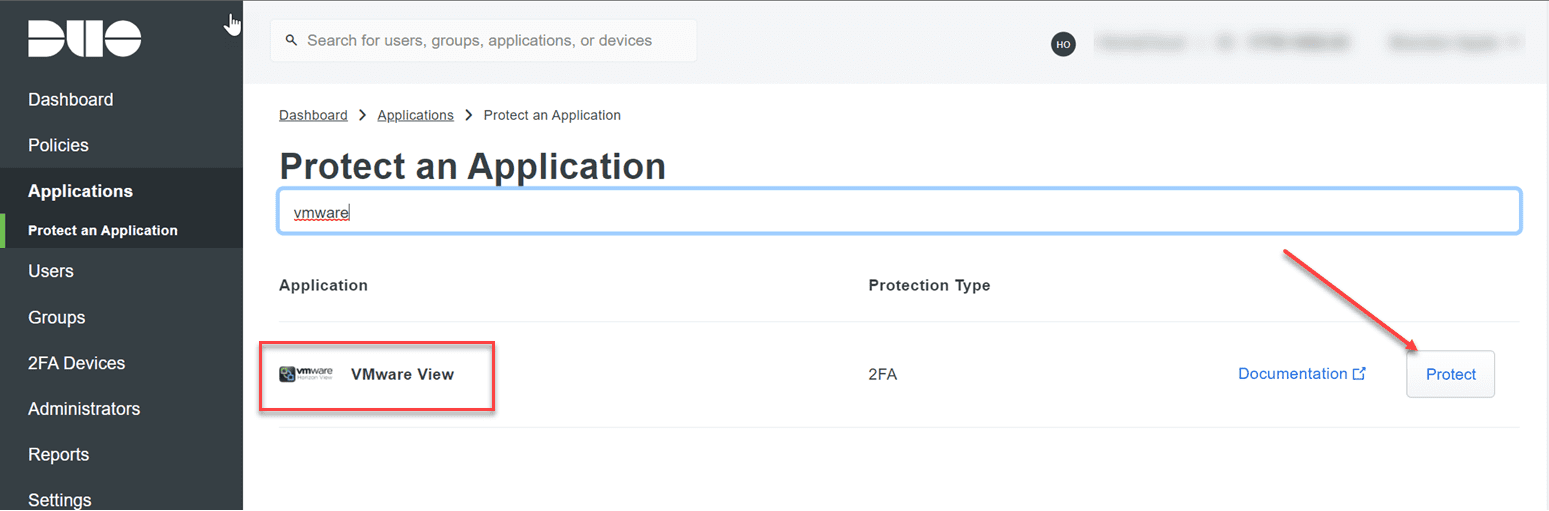
Search for VMware View. Since there isn’t an application in the catalog for vCenter Server, the VMware View app works just fine. There is nothing really specific to VMware Horizon with this particular Duo app. We simply need an application that sends LDAP credentials to the Duo cloud and verifies access by sending the two-factor authentication prompt. Click Protect to begin creating the new protected application.
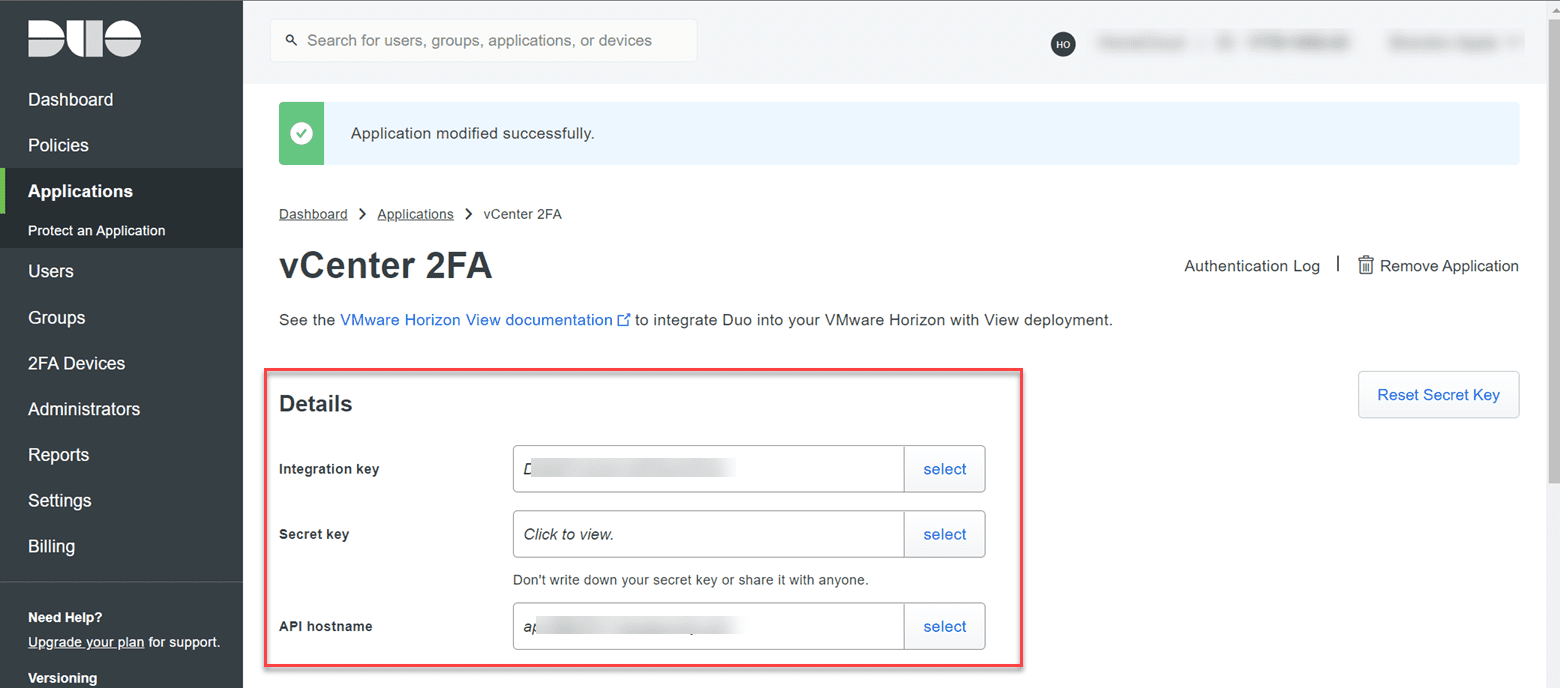
Rename the application to an intuitive name for protecting your vCenter Server appliance. Also, collect the information contained in the boxes below for:
- Integration key
- Secret key
- API hostname
These will be used when configuring the Duo proxy configuration.
Now, we are done for now on the Duo side.
2. Deploy the Duo Proxy appliance
The next step in the process to implement the 2FA prompt for vCenter is deploy the Duo authentication proxy. The authentication proxy is best installed in a very small-footprint Linux VM. It is a simple install and requires minimal resources on the box. ***Note*** it can also be installed on Windows, but this is overkill on resources, etc.
You can find the latest installer here:
3. Configure Duo Proxy with application information
The Duo Proxy operation is simple. It has a config file that points to your various protected applications. It does this by referencing the integration key, secret key, and API hostname. The configuration file is located at:
- /opt/duoauthproxy/conf
Below is a sample configuration that configures the ad_client (your domain controller) and the ldap_server_auto config which uses the ad_client and points the configuration to the relevant protected application in the Duo cloud for your account.
After modifying your Duo Proxy configuration file, be sure to restart your Duo Proxy service with this command:
/opt/duoauthproxy/bin/authproxyctl restartSample Duo Proxy configuration file for vCenter two-factor
; Complete documentation about the Duo Auth Proxy can be found here:
; https://duo.com/docs/authproxy_reference
; MAIN: Include this section to specify global configuration options.
; Reference: https://duo.com/docs/authproxy_reference#main-section
;[main]
; CLIENTS: Include one or more of the following configuration sections.
; To configure more than one client configuration of the same type, append a
; number to the section name (e.g. [ad_client2])
[ad_client]
host=DC1.cloud.local
service_account_username=vc_adlist
service_account_password=P@$$w0rd1
search_dn=DC=cloud,DC=local
port=389
; SERVERS: Include one or more of the following configuration sections.
; To configure more than one server configuration of the same type, append a
; number to the section name (e.g. radius_server_auto1, radius_server_auto2)
[ldap_server_auto]
client=ad_client
ikey=<your integration key value>
skey=<your secret key value>
api_host=<your api hostname>
port=389
exempt_ou_1=CN=vc_adlist,OU=ServiceAccounts,DC=cloud,DC=local
exempt_primary_bind=false
failmode=secure
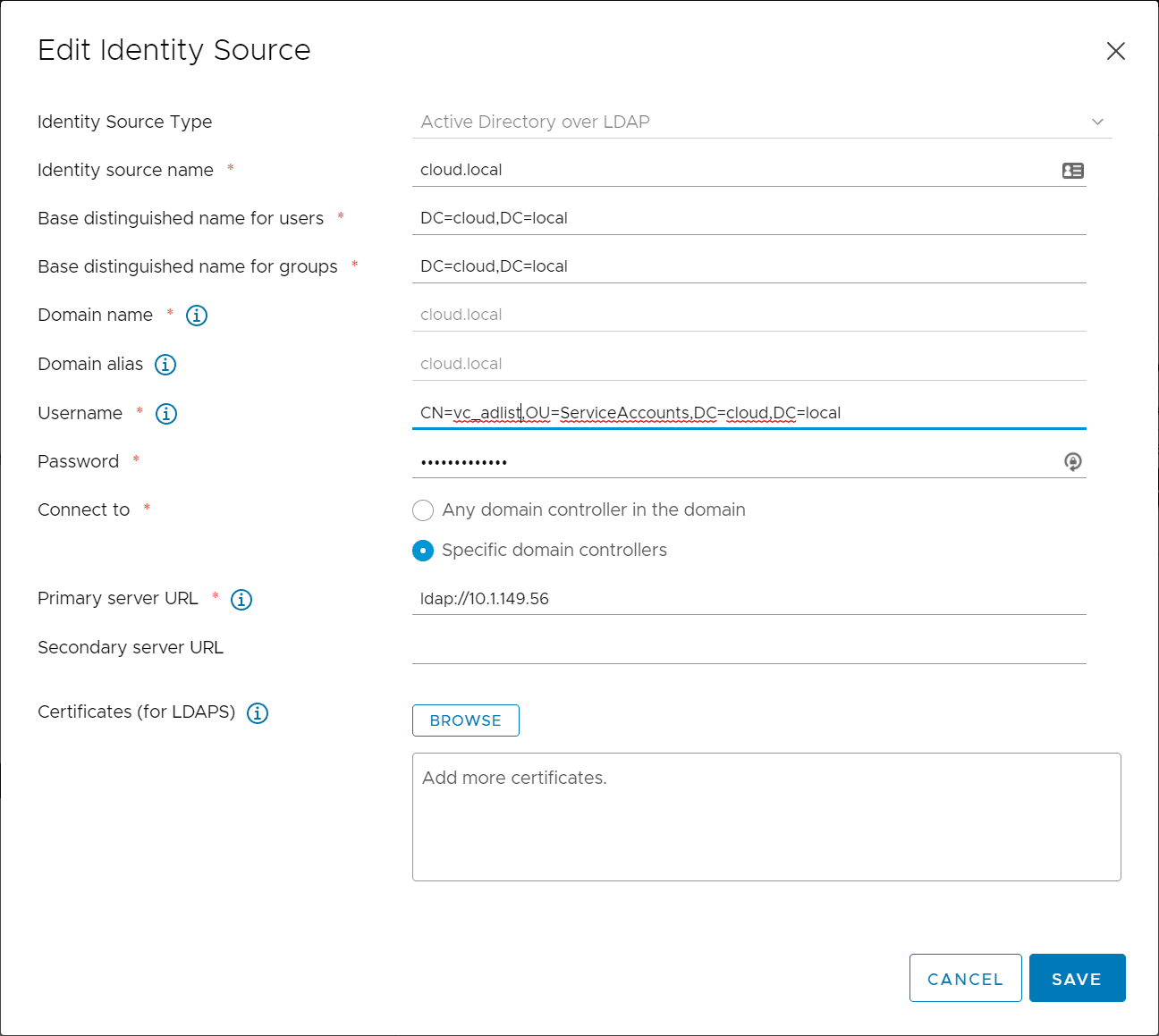
4. Point vCenter Server LDAP connection to the Duo proxy
Now that we have the Duo configuration in place, we just need to point vCenter Server to the Duo Proxy for the LDAP connection. Note the DN format for the service account you need to list out the directory and this should be the user that matches in your Duo proxy configuration. Note, the IP address listed for the Primary Server URL is not a domain controller, but rather the IP address of the Duo proxy appliance.
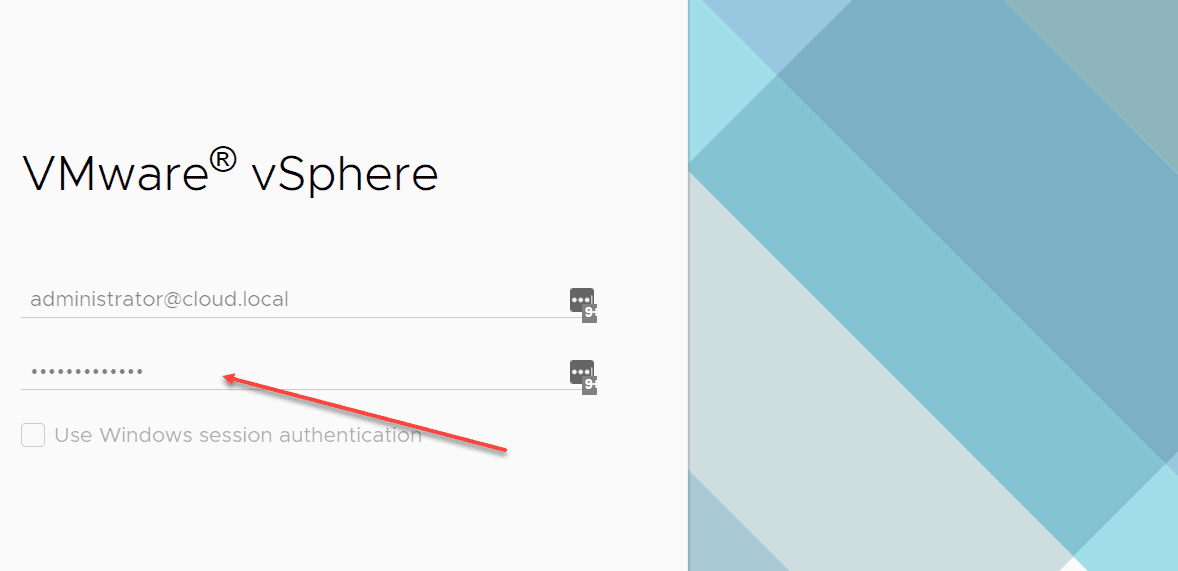
5. Test the vSphere Client login to ensure two-factor prompts
All that is left to do is test the vSphere Client log in to ensure you get the prompt in your Duo application. Log in as a domain user and you should get the Duo prompt for your configured user.
Troubleshooting your vCenter Server Two-Factor Authentication with Duo
If you get an error logging in after configuring your Duo proxy, make sure to check the Duo Proxy authentication log found here:
/opt/duoauthproxy/log/authproxy.log
Make sure your user names setup in Duo match the users that are matched from the proxy up to the Duo cloud. Duo allows you to add aliases so you can easily match the usernames if these are missing in how they are formed and transmitted up to Duo from the auth proxy.
Video showing vCenter Server two-factor configuration
Check out my video showing the process detailed in this post:
Wrapping Up
It is great to see that VMware is serious about adding new and improved two-factor and identity source configurations in vCenter Server. The new vCenter Server 7 and higher appliances provide the ability to integrate with ADFS. While this is a good start, it can be complicated and many additional requirements and infrastructure just to get a 2FA prompt for a vCenter Server login. Hopefully, this easy vCenter Server two-factor authentication without ADFS configuration walkthrough will help any who want to implement two-factor authentication on their vCenter Servers easily and bolster their security posture as a result.










Hello,
Thank you for this article. Any chance you would be willing to update it for LDAPS?
It’s not required to set as applocation vmware view. The more generic “ldap proxy”app should work. I would also describe the required setup to sync users from ad to duo and add the missing “cloud” part from duo proxy conf. Imho your documentation is not complete.