12 Ways to Protect your Organization from Ransomware
It sends a chill up the spine of any CIO, IT admin, or SecOps professional – ransomware. Ransomware is growing in terms of how often it is used to attack an organization, the sophistication, and the tactics used by modern ransomware to persuade businesses to pay ransoms. Ransomware is a sinister threat to business-critical data today and must be treated as a serious threat by organizations worldwide. This post will consider 12 ways to protect your organization from ransomware. Consider this a list of the best security layers you can put into practice to protect your organization not only from a ransomware attack initially, but to minimize the damage an attack can cause.
12 Ways to Protect your Organization from Ransomware
The following 12 ways to protect your organization from ransomware is a list of the recommended security layers needed to successfully and effectively defend against the arguably most dangerous threat to your data today.
- Backup your data
- Perform regular patching for security vulnerabilities
- Use multi-factor authentication
- Do not expose RDP to the Internet
- Adopt least privilege access methodologies
- Use email SPAM and phishing protection
- Implement micro-segmentation
- Use next-generation web filtering
- Perform cybersecurity awareness training
- Use endpoint protection
- Use application whitelisting
- Implement strong password policies and breached password protection
1. Backup your data
Ransomware is extremely effective at locking up your data so there is no way to recover without paying the ransom unless you have a backup. Some have had limited success with searching for decryptor tools and other utilities to try and break the encryption used by the ransomware to recover the data. However, when the minutes and even seconds count towards your RTO to get your data back, you can’t depend on that. In addition, most ransomware variants do not have an easily found decryptor utility to decrypt your data, if one even exists.
Backing up your data correctly and in a way that provides the most protection should be in line with the 3-2-1 backup rule. With the 3-2-1 backup rule, you should have (3) copies of your data, stored on (2) different kinds of media, with at least (1) copy stored offsite. By storing backups in this way, you provide diversity to backup data, where it is stored, and what types of locations it is stored, and you have one that is located away from your production data center.
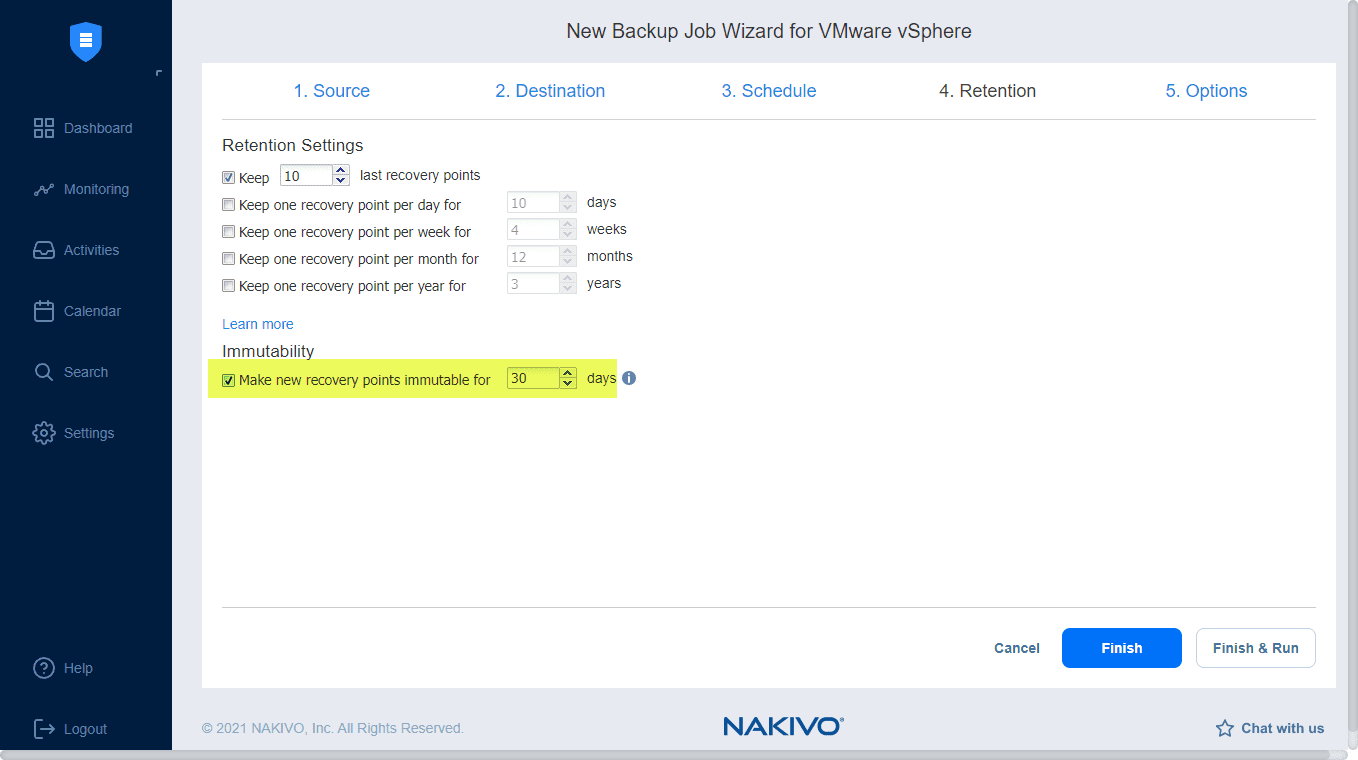
With new backup technologies, including immutable backups, organizations can set an immutability flag that makes backup data persistent without the possibility of it being deleted by a threat actor or ransomware. Using a capable data protection platform that provides capabilities that bolster the 3-2-1 backup rule is essential.
2. Perform regular patching for security vulnerabilities
Attackers often target known vulnerabilities to launch a ransomware attack. Most often, it is usually not zero-day vulnerabilities that cause the greatest risk, it is known vulnerabilities that have been patched. Organizations without a routine patch schedule are prime targets for attackers since they may have systems that are running old, unpatched code with a nasty vulnerability.
Performing regular patching of business-critical systems helps to ensure these are protected from known vulnerabilities that are often used to launch a ransomware attack.
3. Use multi-factor authentication
Attackers often target environments by compromising passwords or finding weak, re-used, or previously breached passwords in the environment. Multi-factor authentication adds additional “factors” to the authentication process. It exponentially improves account security.
Even if an attacker knows the correct password for the account, all of the factors are still not possessed by the attacker. The most common form of multi-factor authentication is two-factor authentication. With 2FA, a one-time password is generally sent to a mobile device, or the user makes use of an authenticator app that generates the one-time passwords for the second factor of authentication. Again, this greatly improves the security of the environment and helps to protect against ransomware attacks.
4. Do not expose RDP to the Internet
Many businesses have suffered ransomware attacks as a result of exposed RDP servers. Remote Desktop Protocol is recklessly implemented incorrectly in most organizations. Many businesses simply stick an RDP server out on the Internet to easily allow remote access for remote workers. However, this is asking for trouble. Monitoring RDP connection attempts on a server on the Internet will generally find that within minutes, an RDP server is barraged with invalid login attempts due to password spraying, dictionary-based attacks, or another password attack.
End-users are notoriously lax in choosing secure passwords. Weak passwords and an exposed RDP server are a recipe for ransomware disasters waiting to happen. After an attacker finds an account that works, they then will attempt to find another vulnerability to escalate privileges or attempt to harvest credentials from the memory of an RDP server.

If attackers are able to find the credentials for an administrator account, it is game over for your data. RDP servers were never meant to be openly exposed to the Internet. Per Microsoft’s best practice design, RDP should be behind a Remote Desktop Gateway server that tunnels RDP traffic over HTTPS connections.
5. Adopt least privilege access methodologies
A common problem in many environments is overprovisioned permissions. Giving more permissions than needed is the easy way out as it guarantees users will be able to access what they need. However, it does not take security into consideration. By overprovisioning permissions, if the user account is compromised, attackers will have access to even more resources than if the account was provisioned according to least privilege access. What is this?
Least privilege access is granting only the exact permissions a user needs and no more. It ensures the user access is scoped appropriately and is not overprovisioned. If a user account is compromised that is scoped according to least privilege access, the damage path is reduced and makes it more difficult for an attacker to move about in the environment.
6. Use email SPAM and phishing protection
Email is a favorite attack vector for ransomware by way of phishing attacks. Attackers masquerade malicious emails as legitimate email communications, even from reputable businesses or online companies. Modern phishing attacks are often very difficult to recognize.
Phishing attacks may have malicious attachments or coax users to click malicious web links to download and execute malicious code on their workstations. An employee who installs the malicious program allows the ransomware to begin its encryption process and spread across the environment.
Using effective SPAM and phishing protection on email services helps to reduce the number of malicious emails that make it through. However, keep in mind that no SPAM or phishing service is 100% effective. Other security protections must be in place.
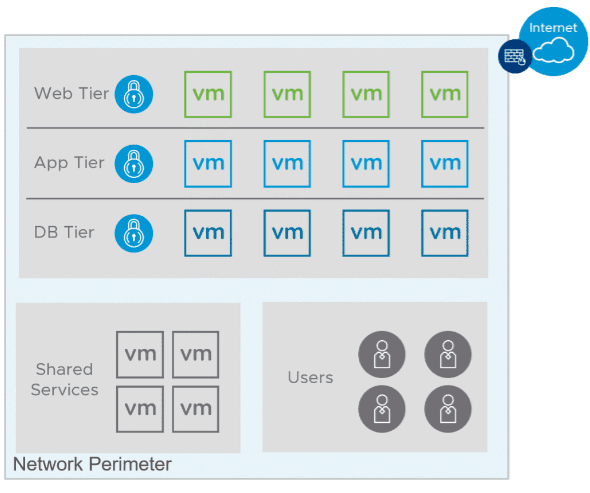
7. Implement micro-segmentation
Large, flat layer 2 networks are often found in SMB environments or enterprise environments without thought given to security. A large single layer 2 local area network is easy for an attacker to maneuver in if they have infiltrated the perimeter and start moving laterally. On the other hand, networks that implement micro-segmentation helps to minimize the ease with which attackers or ransomware can spread through the environment.
Micro-segmentation provides the same functionality as having many tiny firewalls on each device on the network. Traffic is usually scrutinized based on “zero-trust” network design. All traffic is scrutinized, even if it is within the LAN. Again, this type of design helps to bolster security defenses against ransomware.
8. Use next-generation web filtering
Ransomware can attack environments using drive-by attacks on malicious sites or by using malicious ads running on a legitimate site. Organizations must heavily scrutinize web traffic and use effective web filtering to help scrutinize web traffic that could be malicious.
This needs to include SSL traffic. Modern security appliances and firewalls generally have the ability to inspect HTTPS traffic to help ensure there is no blind spot with SSL-encrypted web traffic.
9. Perform cybersecurity awareness training
One of the best tactics to defend against ransomware is to educate end-users on what to look for to recognize something malicious, including a risky website, a phishing email, or a malicious program that masquerades as something legitimate.
Requiring end-users to go through cybersecurity awareness training is a great way to bolster the security of your environment. It has often been said the weakest link of any cybersecurity defense is users. By educating your employees, end-users are able to filter malicious risks before these need to be taken care of with technology defenses.
10. Use endpoint protection
It has been said that antivirus is dead and no longer effective against ransomware. While traditional antivirus programs are certainly no longer effective against modern threats, next-generation endpoint protection uses artificial intelligence (AI) and machine learning (ML) to help recognize malicious threats. While endpoint protection should not be your only means of protection against ransomware, it is still a valuable component of overall cybersecurity defenses.
11. Use application whitelisting
Application whitelisting is a type of security mechanism that prevents the execution of any program, script, or another executable that isn’t explicitly allowed. In other words, you define the exact programs you want to be able to execute. Executing any other code will be blocked. The thought here is the ransomware executable will not be included in the allowed list of applications and will be blocked.
Application whitelisting is very effective. However, it does require quite a bit of time in implementation and tweaking to ensure legitimate business-critical apps are not blocked.
12. Implement strong password policies and breached password protection
Tying into using multi-factor authentication, bolstering the overall security of passwords used in the environment is essential. Use strong password policies to prevent the use of weak passwords, reused passwords, incremental passwords, and also use breached password protection.
Strong password policies and breached password protection require a third-party solution as Active Directory Domain services (ADDS) is limited in its password policy capabilities and has no native breached password protection.
Protect your organization from ransomware with NAKIVO
As detailed in our first point, backing up your data is absolutely critical to surviving a ransomware attack and regaining access to your data. Aligning your backup strategy with the 3-2-1 backup rule largely depends on the capabilities of your data protection solution. NAKIVO Backup & Replication is a modern backup solution that provides the features organizations need to protect their data from ransomware. Also, read my recent post here specifically on using NAKIVO to recover from ransomware: How to Recover from a Ransomware Attack with NAKIVO
NAKIVO helps to protect against ransomware by providing the following:
- Automatic, versioned backups
- Backups of Microsoft 365 cloud SaaS environments (Exchange Online, OneDrive for Business, and SharePoint Online)
- Ability to replicate data
- Hardened virtual appliance
- Ability to create backup copies to store data offsite
- Immutable backups – Prevents ransomware from intentionally deleting backup files
- Two-factor authentication – NAKIVO enables IT admins to setup two-factor authentication to gain access to the NAKIVO interface
NAKIVO Immutability provides protection to your backups from deletion, ransomware, or another threat that attempts to delete data.
Wrapping Up
Protecting your organization’s data from ransomware is an absolute priority in today’s business-critical environment. Ransomware is a threat to any business using digital data and can affect any business. Ransomware protection today is a multi-layered approach that consists of many defensive and offensive mechanisms. Businesses must protect their data with backups.
NAKIVO Backup & Replication is a modern backup solutions that provides the tools needed to backup and protect data from ransomware. The latest NAKIVO Backup & Replication v10.5 adds new security capabilities, including a hardened NAKIVO virtual appliance with additional security benefits.
Download and learn more about NAKIVO Backup & Replication here:
Read my previous NAKIVO posts here:
- NAKIVO Backup and Replication v10.5 Beta Released New Features
- NAKIVO Backup and Replication v10.4 GA Released for Download