SolarWinds Orion hack is VMware vSphere vulnerable
Most have heard about the breach at this point of the SolarWinds Orion product. This is an extremely concerning situation for those potentially using the Solarwinds Orion product in their environment. What is the Solarwinds Orion product? How is it used? Focusing on virtualization, what about your VMware vSphere environment? What precautions should you take to ensure you have your VMware vSphere environment is secure? Let’s take a look at SolarWinds Orion hack is VMware vSphere vulnerable to see what we know about the hack and specific to your vSphere virtualization environment, what steps might you take, especially if you have had the vulnerable version of SolarWinds Orion in your environment.
What is SolarWinds Orion?
First of all, what is SolarWinds Orion? The SolarWinds Orion solution is a single pane of glass platform that allows organizations to monitor their network, IT operations, and security from a single soluton. This includes providing the following:
- Centralized monitoring and management of the IT stack from applications to infrastructure
- Monitoring of all types of infrastructure including physical, virtualized, and cloud IT environments
- Ability to deploy on-premises or in the cloud
Specific to VMware vSphere environments, what does SolarWinds Orion provide?
- Comprehensive virtualization performance management
- Capacity planning tools
- VM sprawl management
- Manage across on-premises and cloud environments
- Visibility across the vSphere-backed application stack
What do we know about the Solarwinds Orion hack?
By way of a compromised build that was introduced by attackers using a supply chain compromise to serve backdoored updated versions of SolarWinds Orion.
- Compromised builds have access through the Orion software itself and not through some other remote access protocol like RDP or others.
- Attackers have been observed with the backdoor performing many different kinds of exploitation behaviors. This includes setting up federation trusts in Azure AD for malicious tokens with attacker certificates, adding x509 keys and password credentials to OAuth applications, and using memory-only droppers to deploy Cobalt Strike BEACON and other backdoors.
Organizations will need to find out if they have had a vulnerable version of 2019.4 HF 5 through 2020.2.1, released between March 2020 and June 2020 installed. If you had a vulnerable version, this becomes a discovery exercise of seeing if your environment was compromised.
What is extremely worrisome for everyone is what backdoors were planted by the attackers who had control of the vulnerable versions of SolarWinds. For those that had SolarWinds Orion Virtualization Manager monitoring their VMware vSphere environment, there certainly is at least some cause for concern. Let’s take a look at a few recommendations to help lock down your vSphere environment in case these have been compromised as a result of the Solarwinds Orion hack.
Attackers can move laterally across your network once they have access to your environment. They can use legitimate credentials that are compromised. This can be extremely difficult to have visibility to and determine. SAML and other tokens have also been noted as compromised with the Solarwinds Orion hack as well.
SolarWinds Orion hack is VMware vSphere vulnerable
What are a few things that you can do to ensure that your VMware ESXi hosts are protected if your organization has come into contact with the compromised version of SolarWinds Orion?
- Change ESXi root passwords
- Remove Active Directory Access from VMware vSphere
- Control who has access to your VMware vSphere management network
- Monitor logins and other activities in your VMware vSphere environment
1. Change ESXi root passwords
If you know you have had the compromised version of SolarWinds Orion in your environment, you want to make sure you start fresh with your ESXi credentials. Make sure you change all root passwords on ESXi hosts in your environment. This will help to close off access to compromised root credentials on your ESXi hosts.
2. Remove Active Directory Access from VMware vSphere
If an attacker is in your environment, it is highly likely they have access to Active Directory accounts that have been compromised. Many environments may have high-level vSphere accounts, even administrators that are Active Directory users. Removing these accounts from vSphere administrator permissions is a really good idea to prevent compromised AD credentials from also compromising your VMware vSphere environment.
3. Control access to your VMware vSphere Management network
Make sure you have management network access sealed off from the general-purpose LAN. This will restrict who has access from a network perspective to your VMware ESXi hosts. Having a flat Layer 2 network for literally everything, including sensitive servers, and your ESXi hosts is an extremely bad idea in many ways, and especially from a security perspective.
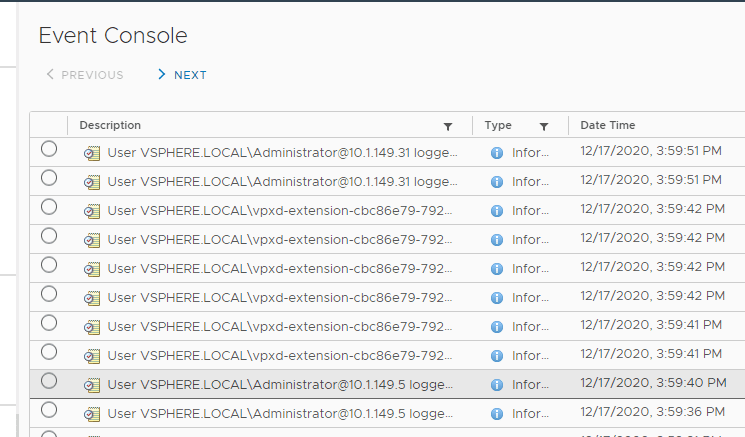
4. Monitor logins and other activities in your VMware vSphere environment
If you have had the compromised version of Solarwinds Orion in your environment, it is extremely important to monitor network login activity and ensure that you flag anything suspicious in the environment. Compromised credentials that are legitimate can be difficult to pinpoint. Pay close attention to your SIEM rules and those that have been released especially since the SolarWinds Orion hack to help pinpoint down on suspicious behavior.
If it isn’t enough that we are still dealing with the global pandemic, high profile cyberattacks are becoming the “new normal” of pandemic life and are becoming a pandemic in themselves. There is no question that businesses today have to be vigilant and not let their guard down when it comes to protecting business-critical assets such as their VMware vSphere environments.