Automate Letsencrypt Certificate Renewal with PowerShell
SSL certificates, especially in the home lab, can be difficult to manage and maintain if you have even a handful of VMs to eliminate certificate errors. Letsencrypt has been arguably the best development in the SSL space. It allows having valid SSL certificates on your servers, for free, for 3 months at a time. While this is a great way to secure your environment, the three-month limitation can become a bit difficult to manage with multiple servers. This means you will be renewing your SSL certificates on servers you are often maintaining. However, I want to introduce you to a couple of PowerShell tools that can help eliminate this task’s headache with Letsencrypt and allow you to have fully automated Letsencrypt certificates in your environment without the manual management generally required. Let’s look at how to automate Letsencrypt certificate renewal with PowerShell.
What is Letsencrypt?
Let’s take a quick overview of Letsencrypt. You can read more about Letsencrypt here. However, it is a free automated and open certificate authority that allows organizations to have free, trusted certificates. This is with the end-goal of having a more secure and private Web.
Letsencrypt is the “real deal” when it comes to a trusted CA. In fact, on Thursday, September 3rd, 2020, Letsencrypt issued six new certificates: one root, four intermediates, and one cross-sign certificate. They have been recognized y a wide variety of operating systems and browsers, making them a viable solution for securing web traffic for many different use cases.
The advantage of the Letsencrypt project is that no longer are SSL certificates cost-prohibitive. Anyone can have a trusted SSL certificate for free. The great thing about Letsencrypt as well is that it allows those of us with home lab environments to have real trusted certificates in the lab environment to avoid SSL errors. However, keep in mind, these are not just for home lab users. Organizations can also take advantage of Letsencrypt in various ways, especially in dev/test/staging environments.
Automate Letsencrypt Certificate Renewal with PowerShell
We all love the automation capabilities that we can achieve using PowerShell. The process to manage and automate Letsencrypt certificate renewal with PowerShell allows using the short-lived SSL certs that are provided by Letsencrypt and taking the management burden off of administrators doing this manually.
There are two modules that you need to know about when working to automate Letsencrypt certificate renewals with PowerShell:
- Posh-ACME – Posh-Acme provides the ability to obtain your Letsencrypt certificates
- Posh-ACME.Deploy – Posh-ACME.Deploy is the PowerShell module that you use to actually deploy your certificates to your websites such as those that are hosted in IIS.
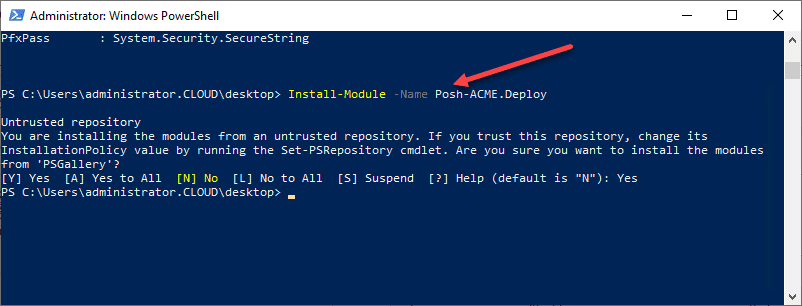
Installing Posh-ACME and Posh-ACME.Deploy
Both Posh-ACME and Posh.ACME.Deploy are available as PowerShell modules from the PowerShell Gallery making them both extremely easy to deploy.
Automated DNS management using Cloudflare API token
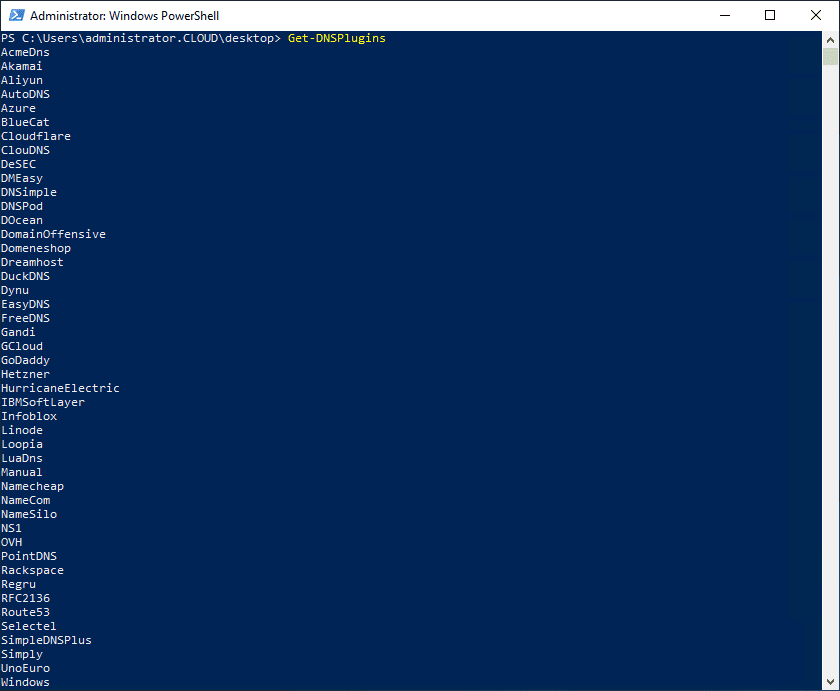
One of the great things about the Posh-ACME module is it has many different DNS modules to interact with various DNS providers. As you can see below, once you install Posh-ACME, you can run the command:
Get-DNSPlugins
This will list all the DNS providers the plugin can interoperate with. Most of the big ones are available.
I use Cloudflare for personal DNS and other things. Using Posh-ACME, you can easily manage your Cloudflare DNS to verify your domain for issuing your Letsencrypt certificates.
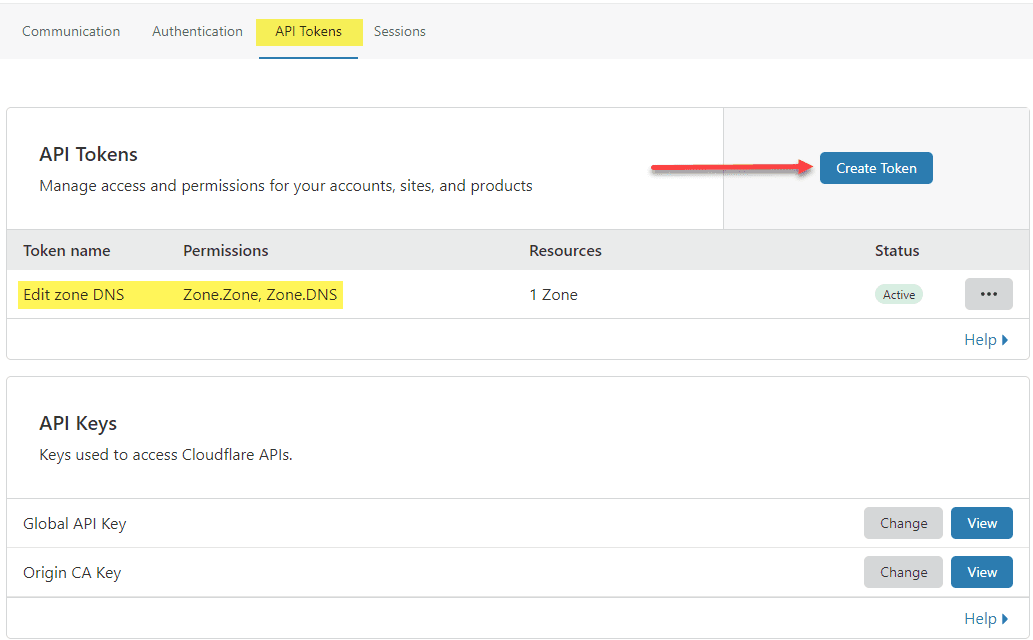
Part of the process that is involved with Letsencrypt is verifying your domain ownership. This is accomplished by creating a TXT record in your DNS zone to validate ownership of your domain for which you want to issue certificates. Cloudflare has a newer method introduced called API tokens as opposed to the legacy API keys. With the new API token method, you can configure granular permissions for accessing your DNS zones and even filter the IP addresses from which the API calls are coming from. This provides a much more secure way to manage your DNS zones programmatically.
Once you have your API Token, you can then create a PowerShell script, leveraging Posh-ACME to create certificates for your domain host:
$Domain = "host.mydomain.com" $Email = "[email protected]" $pArgs = @{ CFToken = $token } $pArgs = @{ CFTokenInsecure = 'mycloudflaretoken' } (Optional) Only specify the ReadAll token if you generated one $pArgs.CFTokenReadAllInsecure = 'mycloudflaretoken' New-PAAccount -AcceptTOS -Contact $Email New-PAOrder $Domain New-PACertificate host.mydomain.com -DnsPlugin Cloudflare -PluginArgs $pArgs
Posh-ACME Letsencrypt Certificate Renewals
To renew a certificate, it is even easier. As shown by the Posh-ACME documentation:
Set-PAOrder mydomain.com
if ($cert = Submit-Renewal) {
# do stuff with $cert to deploy it
}
For a job that is renewing multiple certificates, it might look more like this.
Submit-Renewal -AllOrders | ForEach-Object {
$cert = $_
if ($cert.MainDomain -eq 'mydomain.com') {
# deploy for mydomain.com
} elseif ($cert.MainDomain -eq 'mydomain2.com') {
# deploy for mydomain2.com
} else {
# deploy for everything else
}
}
Now, you may wonder where the Posh-ACME.Deploy module comes in. After you have obtained your certificate or renewed your certificate with the Posh-ACME module, you can use the Posh-ACME.Deploy module to actually apply the certificate to your websites:
Set-PAOrder mydomain.com Get-PACertificate | Set-IISCertificate -SiteName 'Default Web Site' -Verbose
Your Posh-ACME renewal script might look something like this.
Set-PAOrder mydomain.com
if ($cert = Submit-Renewal) {
$cert | Set-IISCertificate -SiteName 'Default Web Site' -RemoveOldCert
}
Using both of the commands, you can then effectively automate both the renewal process with Posh-ACME and the applying of the certificates to your websites with the Posh-ACME.Deploy module using a simple script. No longer will you have to set a reminder to renew your SSL certificates issued by Letsencrypt as your automated PowerShell script can do this for you.