AMD Secure Encrypted Virtualization-Encrypted State (SEV-ES) in VMware vSphere 7.0 U1
Most of us remember how January 2018 began. Must like how the first of this year began with unexpected events, 2018 saw the Spectre and Meltdown vulnerability come to light with Intel CPUs majorly affected by the design flaw that literally affected every Intel CPU on the market. AMD, while vulnerable to a small portion of the vulnerability, was largely unaffected by the scariest of the vulnerabilities due to the way their chips were designed. AMD has certainly been making waves in the enterprise market for some time now with the introduction of the AMD EPYC processors. Security is a major reason that many are looking at AMD in the datacenter. With the new AMD EPYC Rome series, AMD has strongly positioned themselves in this space. Performance aside, security is still a major benefit of AMD processors.
Hot off the press in conjunction with VMworld, AMD in conjunction with VMware vSphere 7.0 U1 have enabled a new feature called Secure Encrypted Virtualization-Encrypted State (SEV-ES). In this post we will take a look at AMD Secure Encrypted Virtualization-Encrypted State (SEV-ES) in vSphere 7.0 U1 and see what this brings to the table.
What is AMD Secure Encrypted Virtualization-Encrypted State (SEV-ES)?
AMD’s SEV technology is developed more specifically to support encrypted virtual machines. This allows the hypervisor to mark sensitive page tables in the nested page table and automatically encrypt them for the VM by the hardware. Specific cryptographic keys are generated for each guest and only accessible by the hardware. Even the hypervisor can’t read into the secure memory.
Every VM is assigned a different key and is cryptographically isolated from all other VMs on the system. If an attacker tries to scrape memory or perform a “cold boot” attack, all they get is garbage data.
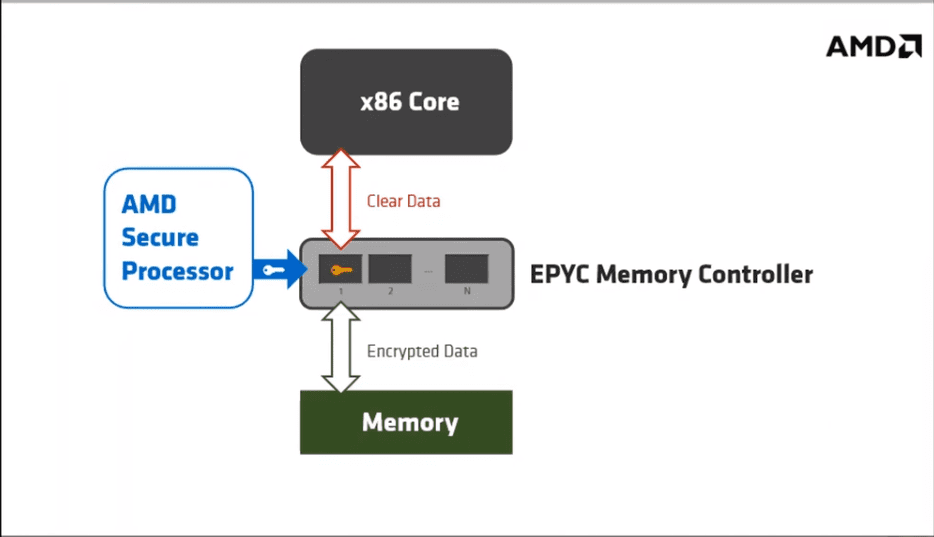
As you can see via the high-level architecture overview, SEV is made possible by two different components:
- EPYC Memory Controller – Integrated encryption engine with 128-bit key slots. Any memory that is written with the associated key is encrypted as it goes to memory and decrypted as it comes back
- AMD Secure Processor – Secure root of trust, that comes up first, key generation, and installs key into the memory controller. The x86 cores do not have the ability to read this key
The EPYC Memory Controller generates the cryptogrphic
SEV-ES extends this functionality to also encrypt the CPU registers. With both, the enablement happens at the hypervisor or at the VM level. So, VMware does all the heavy lifting for the customer for adding this additional security layer.
VMware hypervisor enables this cryptographic isolation. Even the hypervisor can’t read the memory or registers. This provides extra layer of security on top of what VMware has already done. There is no refactoring required at the application level, so this feature is much easier for organizations to implement.
Statements from both AMD and VMware are as follows:
Dan McNamara, senior vice president and general manager, Server Business Unit, AMD:
“As the modern data center continues to evolve into a virtualized, hybrid cloud environment, AMD and VMware are working together to make sure customers have access to systems that provide high levels of performance on virtualization workloads, while enabling advanced security features that are simple to implement for better protection of data. A virtualized data center with AMD EPYC processors and VMware enables customers to modernize the data center and have access to high-performance and leading-edge security features, across a wide variety of OEM platforms.”
Krish Prasad, Senior Vice President and General Manager, Cloud Platform Business Unit, VMware
“In a virtualized environment, it is critical to have protection of data not only from other virtual machines, but the hypervisor itself. This is why we chose to make vSphere 7 the first hypervisor to provide full SEV-ES support from AMD EPYC processors. This additional layer of security and data encryption is truly impactful for our customers as they can now encrypt data throughout their environment. But more importantly, customers don’t have to make changes to their applications to take full advantage of SEV-ES, making security implementation simple. AMD has made security an easy choice for our customers with these features and we’re excited to provide the security of AMD EPYC to them.”
AMD EPYC Powerful Choice for vSAN ReadyNodes
With both the performance of the AMD EPYC processor as well as the increasingly valuable security features as demonstrated by SEV-ES, AMD makes a great choice for powering your vSAN ReadyNodes.
AMD EPYC-based vSAN ReadyNodes are already available from OEM providers such as:
- Dell EMC VxRail E Series hyperconverged systems
- Dell EMC vSAN Ready Nodes
- HPE ProLiant DL325 and DL385 Gen10 and Gen10 Plus servers
- Lenovo Data Center Group – ThinkSystem
- Supermicro vSAN ReadyNode
Wrapping Up
I really like the AMD EPYC offerings when you consider the price point, performance, and especially the high level of security that is offered by the platform. Additionally, when you think about the density of the AMD EPYC processors, customers can now potentially go with single socket configurations in a vSAN ReadyNode and save licensing costs for vSAN.
Especially now with the AMD Secure Encrypted Virtualization-Encrypted State (SEV-ES) in VMware vSphere 7.0 U1, security is still a major reason that many may choose the AMD EPYC offering over Intel at this point. It will be interesting to see how the market responds and if AMD will continue to see the increased growth in the datacenter space.
For a good high-level discussion on AMD and VMware and their partnership, check out the following VMworld session:
- AMD and VMware: Partnering to bring leadership solutions to customers [HCI3198S]