Zerologon CVE-2020-1472 Vulnerability Automated Patching
Many security and IT teams are scrambling to get systems patched after the discovery of the “Zerologon”. It provides the holy grail of vulnerabilities to an attacker. An attacker can essentially become a Domain Admin with one click. And what is even scarier, the exploitability of this vulnerability is fairly simply. All that is required for the attacker is to have a connection to your domain controller. Let’s take a closer look at Zerologon CVE-2020-1472 automated patching and see more about the vulnerability as well as what can be done to patch it.
What is Zerologon CVE-2020-1472 vulnerability?
Security researcher Tom Tervoort discovered a severe vulnerability that has amounted to the highest on the scale (CVSS score: 10.0). What the vulnerability amounts to is an attacker can forge an authentication token for specific Netlogon functionality. He was able to call a function to set the computer password of the domain controller to a known value. After this, the attacker can use the new password to take over the domain controller and steal any credentials, including those of a domain admin.
The Zerologon vulnerability is due to a flaw in the cryptographic authentication scheme that is used by the Netlogon Remote Protocol which is used for important tasks such as updating computer passwords. This is evidently due to the incorrect use of an AES mode of operation that makes it possible to spoof the identity of any computer account and set an empty password for that account in the domain. With the flaw in place, attackers can essentially impersonate any computer, including a domain controller. This allows executing RPC calls on their behalf which leads to the very dangerous possibility mentioned above.
Microsoft patch for CVE-2020-1472
Microsoft has already released patches for the vulnerability that is described as a phased two-part follout. With the rollout, they are addressing how Netlogon handles the usesage of Netlogon secure channels in the first part.
With the second phase, Windows updates will become available in Q1 2021, customers will be notified via a revision to the security vulnerability.
You can find information on the patch as well as download links from Microsoft at the following URL:
Zerologon CVE-2020-1472 Vulnerability Automated Patching
Let’s now take a look at the Zerologon CVE-2020-1472 vulnerability automated patching. You can certainly use WSUS to approve and release the security update for the Zerologon CVE-2020-1472 vulnerability.
However, for automated patching and to ensure that domain controller receive the update, I like to use automated patching tools to ensure the machines receive the updates as soon as possible. There are two tools that I highly recommend for patching your domain controllers for this vulnerability:
- Ansible
- PowerShell
- PDQ Inventory and Deploy
Ansible
Many do not realize that Ansible is a very powerful platform for automating Windows environments and not just Linux. I have written about this subject numerous times on how to get up and running with Ansible and how to use it with Windows environments, even with Kerberos authentication. Check out my articles here on the subject:
- Ansible Manage Windows Servers Examples Guide
- Ansible Windows Join Domain and Rejoin Playbooks
- Manage and Configure Windows Servers with Ansible Tower
- Configure Ansible Windows Server Kerberos authentication in Ubuntu
- Basic Windows Server Automation with Ansible
For installing security updates and critical Windows Server updates, you can use a simple playbook on your domain controllers such as the following:
- name: Search-only, return list of found updates (if any), log to c:ansible_wu.txt win_updates: state: searched log_path: c:ansible_wu.txt - name: install all critical and security updates win_updates: category_names: - CriticalUpdates - SecurityUpdates - UpdateRollups state: installed register: update_result - name: reboot host if required win_reboot: when: update_result.reboot_required
PowerShell
PowerShell is also a great way to ensure Zerologon CVE-2020-1472 vulnerability automated patching. Using a special module in PowerShell called the PSWindowsUpdate module, Windows updates can be easily installed using PowerShell.
To get and install the PowerShell module, you can use the following:
Get-PackageProvider -name nuget -force Install-Module PSWindowsUpdate -confirm:$false -force
A simple one-liner to install Windows Updates using this PowerShell module looks something like this:
Get-WindowsUpdate -MicrosoftUpdate -install -IgnoreUserInput -acceptall -IgnoreReboot | Out-File -filepath 'c:windowsupdate.log' -append
You can either choose to suppress the update or have the script install the update and reboot your domain controller.
PDQ Inventory and Deploy
PDQ is a great tool that allows you to perform many labor intensive tasks in your Windows environment in a very easy and painless way. PDQ inventory allows building accurate inventory of your Windows nodes in your environment and allows you to have an accurate view of what software, including updates, are installed on all nodes in the environment.
With that information in hand, PDQ Deploy allows using your inventory that was aggregated in PDQ Inventory and using this to install software, including Windows updates.
PDQ automatically produces and pulls down the Monthly rollups from Microsoft. You can readily use these packages that are produced to update machines in your environment.
Check out my post here on how to use PDQ Deploy to install Windows updates in your environment:
You can also use a combination of PowerShell and PDQ Deploy to deploy updates as well. Using the PSWindowsUpdate module, you can use PDQ Deploy to run a PowerShell script against all domain controllers in your environment for easy patching.
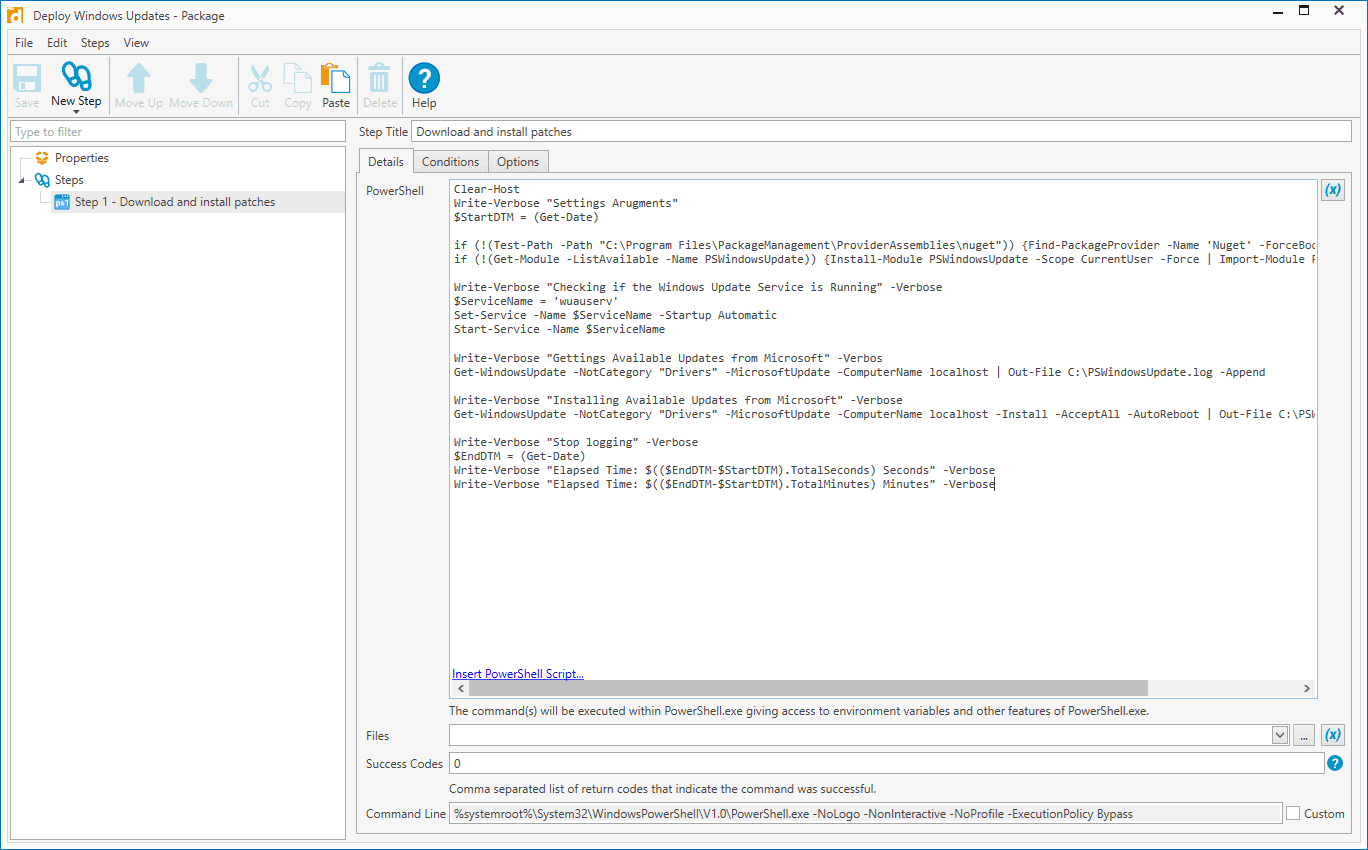
Below is a great script that I had seen from @xenappblog Trond Haavarstein.
Clear-Host
Write-Verbose "Settings Arugments"
$StartDTM = (Get-Date)
if (!(Test-Path -Path "C:Program FilesPackageManagementProviderAssembliesnuget")) {Find-PackageProvider -Name 'Nuget' -ForceBootstrap -IncludeDependencies}
if (!(Get-Module -ListAvailable -Name PSWindowsUpdate)) {Install-Module PSWindowsUpdate -Scope CurrentUser -Force | Import-Module PSWindowsUpdate}
Write-Verbose "Checking if the Windows Update Service is Running" -Verbose
$ServiceName = 'wuauserv'
Set-Service -Name $ServiceName -Startup Automatic
Start-Service -Name $ServiceName
Write-Verbose "Gettings Available Updates from Microsoft" -Verbos
Get-WindowsUpdate -NotCategory "Drivers" -MicrosoftUpdate -ComputerName localhost | Out-File C:PSWindowsUpdate.log -Append
Write-Verbose "Installing Available Updates from Microsoft" -Verbose
Get-WindowsUpdate -NotCategory "Drivers" -MicrosoftUpdate -ComputerName localhost -Install -AcceptAll -AutoReboot | Out-File C:PSWindowsUpdate.log -Append
Write-Verbose "Stop logging" -Verbose
$EndDTM = (Get-Date)
Write-Verbose "Elapsed Time: $(($EndDTM-$StartDTM).TotalSeconds) Seconds" -Verbose
Write-Verbose "Elapsed Time: $(($EndDTM-$StartDTM).TotalMinutes) Minutes" -Verbose
Wrapping Up
There are some really great options for Zerologon CVE-2020-1472 vulnerability automated patching. You can easily use Ansible, PowerShell, or PDQ Deploy for patching your systems and make the process to get this very important security update pushed out across your systems.
These types of tools help to make the most of your time and efforts and helps to streamline the process of very critical but mundane tasks of installing updates.