Nmap Ping Sweep: Home Lab Network Ping Scan

Nmap is a super well-known command line tool that can do a lot of differen tthings. It can help you map out a network and discover what hosts are there. We will look at the Nmap Ping Sweep and see how we can use it as a network vulnerability ping scan for discovery and finding vulnerabilities.
What is Nmap and the Nmap Ping Sweep?
Nmap is a network scan tool that lets you see the hosts on your network and not just see them, but identify what they are. It is really good for cybersecurity, troubleshooting, and investigating networking issues. it stands for Network Mapper and this is exactly what it does. It can map out ports and applications that use those ports when it scans the network.
It scans using different techniques and discovery methods, but doesn’t just use the TCP scanning that many tools use. It can use SYN, UDP raw, ICMP, and other types of ping scans to discover hosts on the network.
You can easily install the tool across multiple operating systems. Below, I am installing it in Windows.
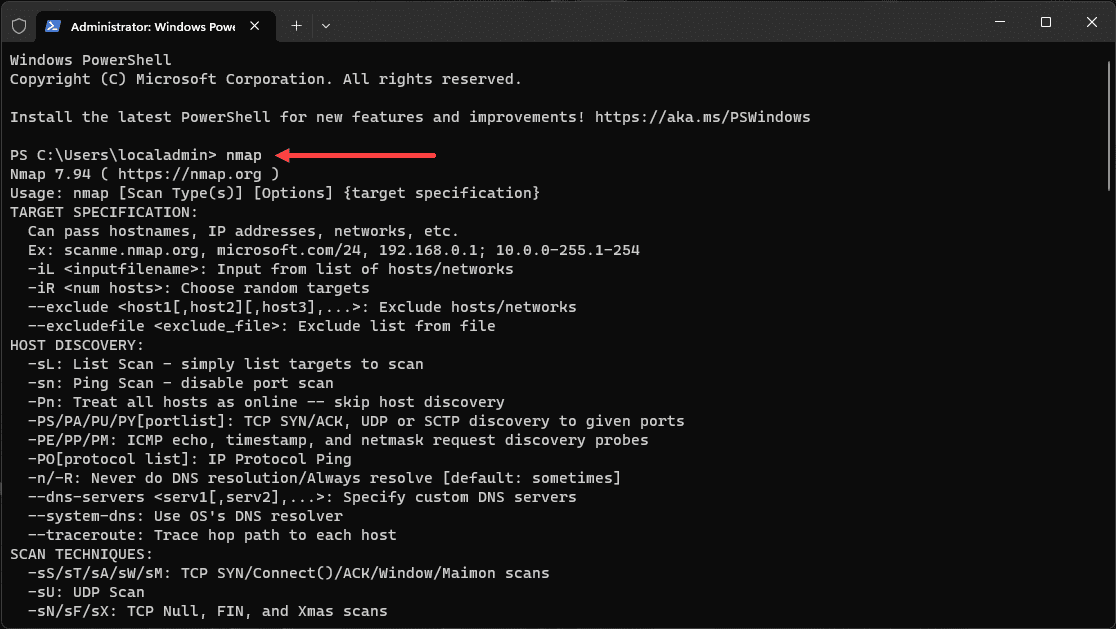
After installation, you can run the nmap command to see the available options.
Ping Sweep and Host Discovery
Ping sweep, an essential method of host discovery, primarily involves sending ICMP echo requests to IP addresses within a specified range. When these echo requests receive a reply, it signifies the presence of an active host in the network. However, you can also utilize ICMP timestamp requests, enhancing the depth of your network analysis.
Host discovery, coupled with a ping sweep, gives a comprehensive view of the active hosts in your network. Nmap sends these requests efficiently, even under strict firewalls, allowing you to manage your network better.
Nmap command examples
Navigating the Nmap command line requires a solid understanding of the potential commands and their impacts on the target network. Here, we’ll look at some examples of Nmap ping sweep commands, demonstrating the diversity and power of this tool.
Basic Ping Sweep:
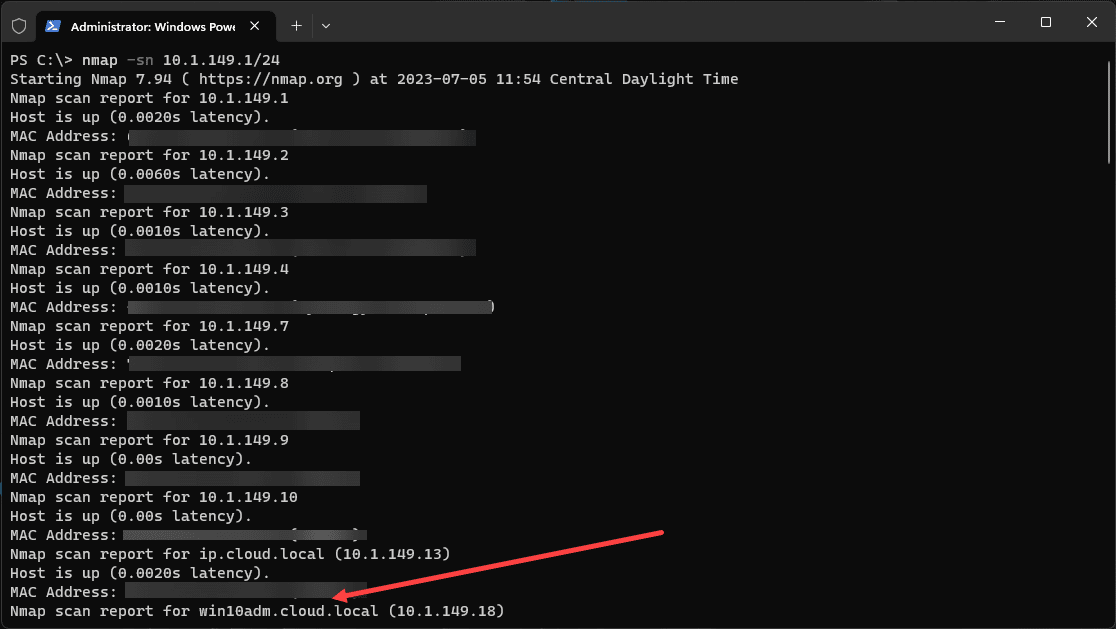
The simplest form of an Nmap ping sweep uses the following command: nmap -sn 192.168.1.1/24. This command will discover live hosts in the network range from 192.168.1.1 to 192.168.1.255.
Disabling DNS Resolution:
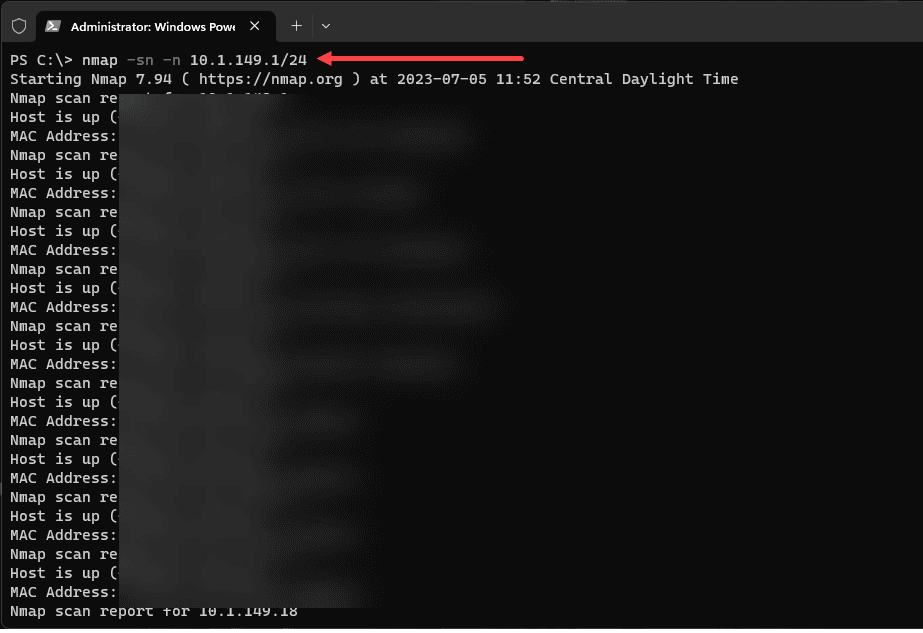
If you’d like to perform a ping sweep without DNS resolution to skip regular scan stages, use the -n flag. An example would be:
nmap -sn -n 192.168.1.1/24This command is beneficial when you want a faster scan by skipping the DNS resolution stage.
Ping Sweep with Port Scan:
You can combine a ping sweep with a simple port scan. Use the following command:
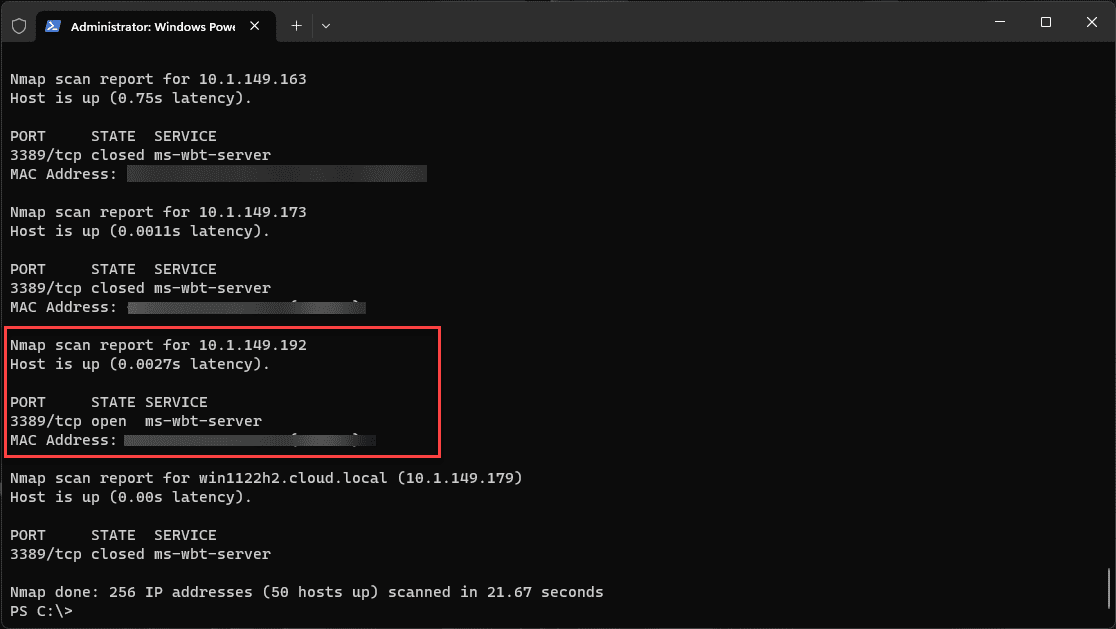
nmap -p 3389 192.168.1.1/24This command will perform a ping sweep and then scan for the availability of port 80 (typically used for HTTP traffic) on all live hosts.
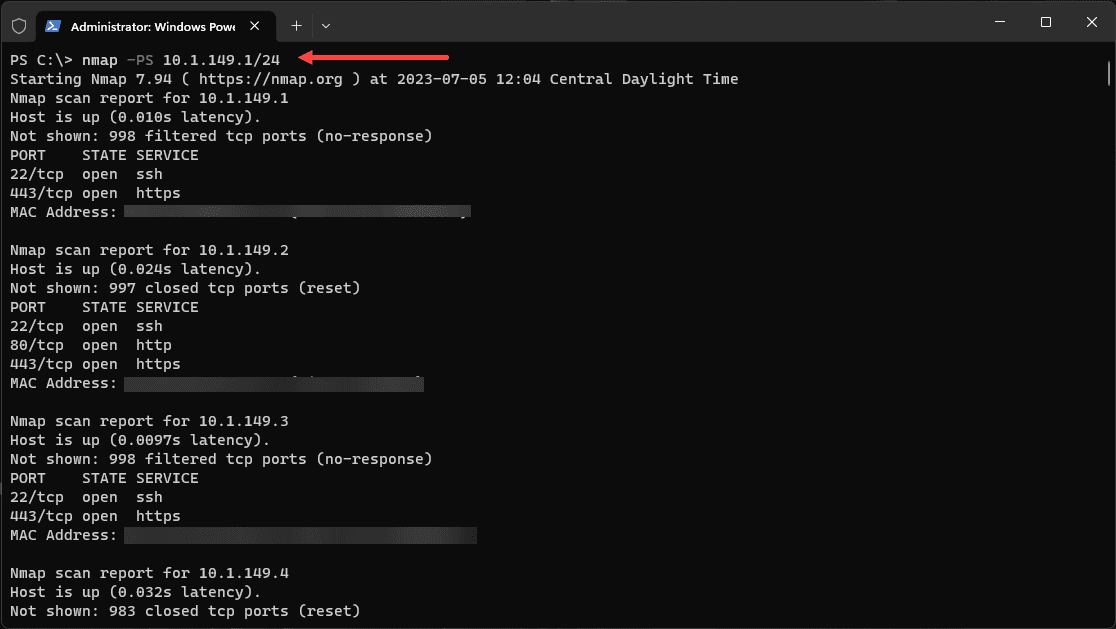
Using TCP SYN for Ping Sweep:
Strict firewalls may drop ICMP packets, thus limiting the effectiveness of the traditional ICMP-based ping sweep. However, Nmap allows for TCP SYN-based ping sweeps. The ICMP standards (RFC 792 and RFC 950) also specify icmp timestamp request, information request, and address mask request packets as codes 13, 15, and 17, respectively.
The following command performs a TCP SYN ping sweep:
nmap -PS 192.168.1.1/24 This command is handy when ICMP packets are filtered by the network’s firewall.
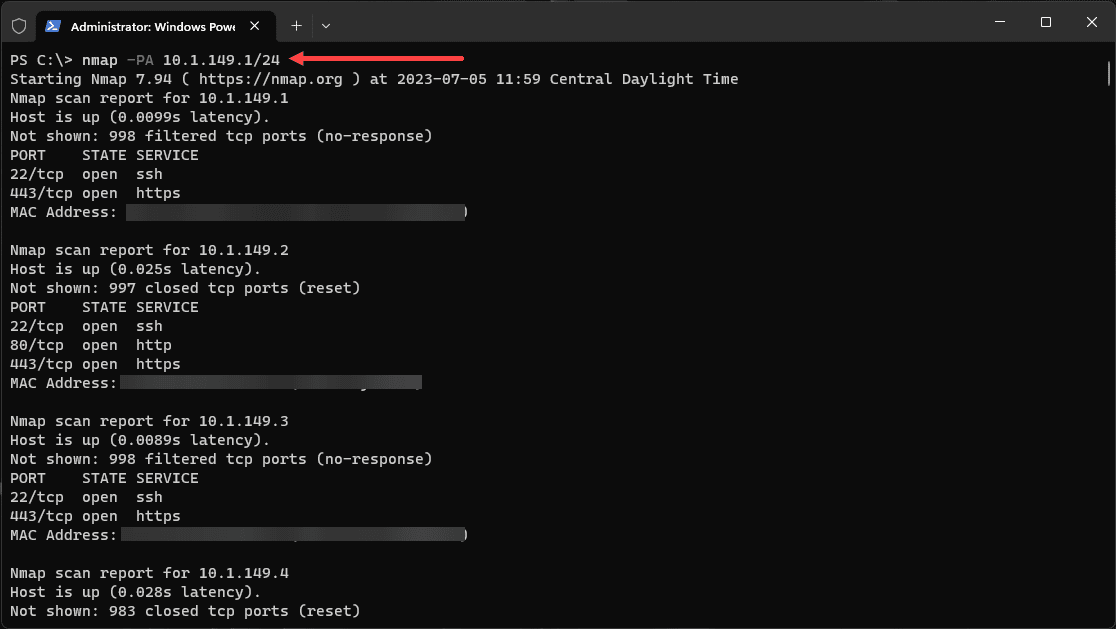
Using TCP ACK for Ping Sweep:
Similarly to the TCP SYN ping sweep, you can use TCP ACK packets for ping sweeps, especially when dealing with strict firewalls that block ICMP and SYN packets. The following command performs a TCP ACK ping sweep:
nmap -PA 192.168.1.1/24Ping Sweep using ICMP Timestamp Requests:
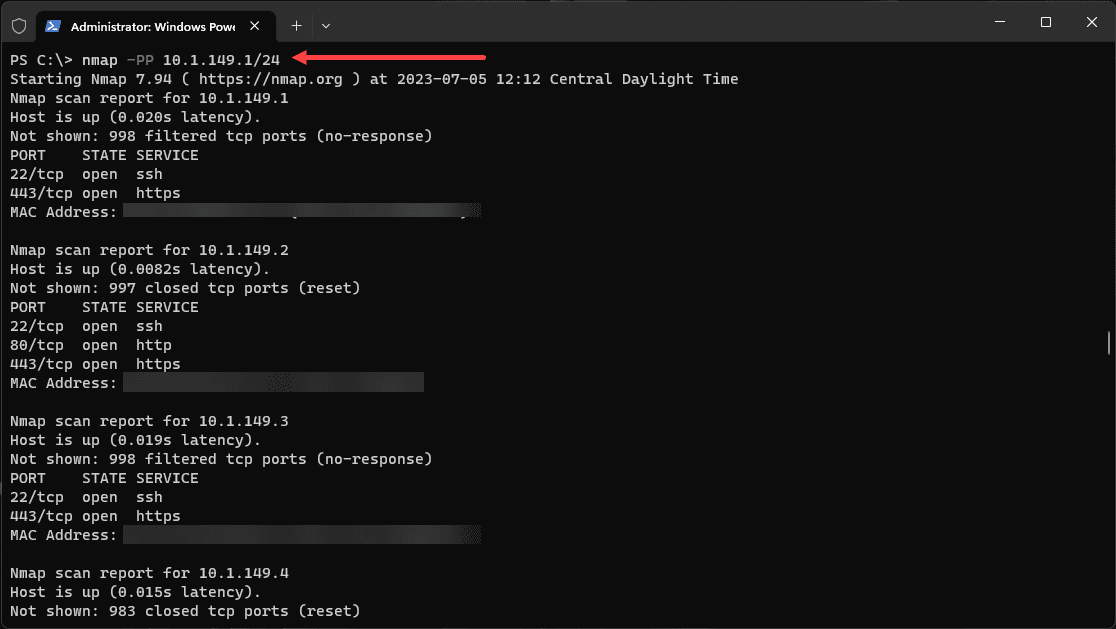
In addition to the typical ICMP echo request, you can use an ICMP timestamp request for ping sweeps. Use the following command:
nmap -PP 192.168.1.1/24This command adds another layer to the scanning process, especially when dealing with hosts that respond differently to various types of ICMP requests.
Remember, while these examples use a specific range of IP addresses, the same principles can be applied to larger IP ranges, entire networks, or even single IP addresses.
Wrapping up
If you are wanting to have a single network command line tool that can do just about anything you want it to do, nmap is like that swiss army knife solution that is all-in-one and can do what you need it to do. You can use it to map networks and also the main thing I really like to do with it I would say the majority of the time is discover what an unknown IP actually is. It can do this well with the operating system discovery.