Kube Bench – Secure your Kubernetes Cluster with CIS Benchmark

Let me introduce you to a tool that is hosted on github.com/aquasecurity/kube-bench, kube-bench is a powerful Go application designed to evaluate whether Kubernetes is deployed according to best practices.
Table of contents
- What is kube-bench?
- Why run kube-bench?
- Installation and Configuration of kube-bench
- Running kube-bench on Master and Worker Nodes
- Tuning Your Kubernetes Cluster Based on kube-bench Results
- The Role of kube-bench in Ensuring Kubernetes Cluster Security
- Utilizing kube-bench for Managed Kubernetes Services
- Understanding kube-bench Test Files and Config Files
- Wrapping up
What is kube-bench?
Kube-bench is an open-source tool developed by Aqua Security and hosted on github.com/aquasecurity/kube bench. The github.com aquasecurity kube bench project primarily benchmarks a Kubernetes cluster against the Center for Internet Security’s (CIS) Kubernetes Benchmark. This benchmark comprises a set of standards designed to ensure a secure configuration for Kubernetes deployments.
You can run a series of automated checks using the kube bench command against your Kubernetes cluster nodes, including both master node and worker node configuration, to identify potential security misconfigurations. Also, the kube-bench cfg command allows you to target specific CIS benchmark versions for your running Kubernetes version, helping ensure your cluster meets the most up-to-date security standards.
Organizations can gain valuable insights into their Kubernetes cluster security posture and make necessary adjustments to enhance their control plane and node security configurations.
Why run kube-bench?
For any organization that relies on Kubernetes clusters it analyzes your Kubernetes configuration against the CIS Kubernetes Benchmark. This tool helps check against security concerns that are important for every organization. B
You can pull up the CIS Benchmark standard here and look at the different items it checks:
Examples of just a few of the checks include:
1.2.10 Ensure that the admission control plugin EventRateLimit is set Not
1.2.11 Ensure that the admission control plugin AlwaysAdmit is not set
1.2.12 Ensure that the admission control plugin AlwaysPullImages is set
1.2.13 Ensure that the admission control plugin SecurityContextDeny is set if PodSecurityPolicy is not used
1.2.14 Ensure that the admission control plugin ServiceAccount is set
1.2.15 Ensure that the admission control plugin NamespaceLifecycle is set
1.2.16 Ensure that the admission control plugin PodSecurityPolicy is set
1.2.17 Ensure that the admission control plugin NodeRestriction is set
1.2.18 Ensure that the --insecure-bind-address argument is not set Installation and Configuration of kube-bench
Before you run kube-bench directly or inside a Kubernetes job, it must first be installed on your Kubernetes master node. The installation process includes downloading the release from the page on GitHub. After the kube bench binary has been manually downloaded, you can run kube bench directly on your master node.
By visiting the kube bench releases download page, you can download the appropriate version for your Kubernetes version running in your cluster. Ensure you select the corresponding CIS benchmark version to the Kubernetes version running in your cluster for accurate results.
Running kube-bench on Master and Worker Nodes
You can run kube-bench directly from the command line, but it’s often more convenient to run kube-bench as a Kubernetes job. Running kube-bench inside a Kubernetes job allows for a more flexible job run and implementation in the environment.
The process to install and run kube-bench is quite simple.
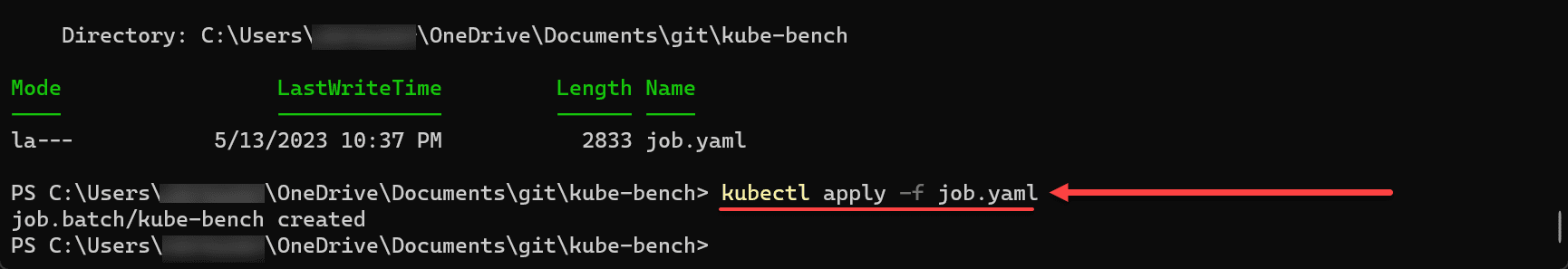
You download a job.yaml file and apply this to your Kubernetes cluster.
What does the job.yaml look like? You can download the sample job file here:
Running the job.yaml file
To run the job.yaml file, you simply use the command:
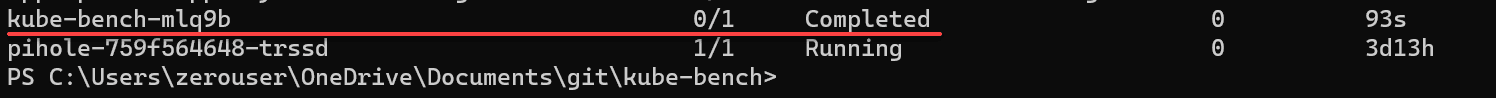
kubectl apply -f job.yamlThe job will spin up a new pod to fire off and run the security scan.
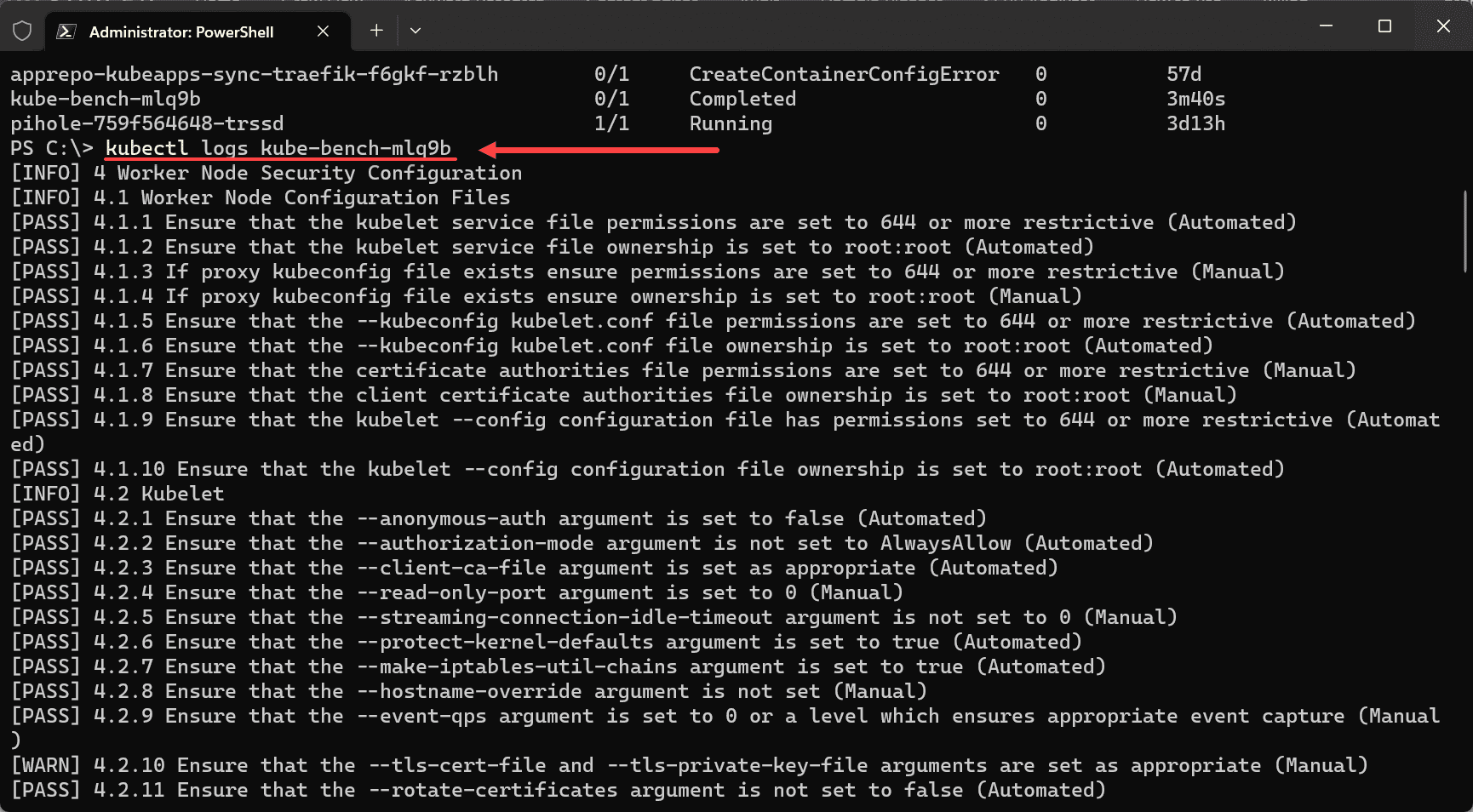
After the security scan runs, you will look at the logs for the pod, using general command kubectl logs <kube-bench pod name>
Tuning Your Kubernetes Cluster Based on kube-bench Results
The output from running kube-bench provides valuable insights into your master node security and worker node configurations. These results ensure your control plane node and other nodes meet the required security standards. For instance, it details the kubelet service file permissions and kubelet service file ownership – crucial aspects of node security configuration.
Additionally, kube-bench provides detailed information about the admission control plugins used in your cluster. These include AlwaysPullImages, NamespaceLifecycle, NodeRestriction, SecurityContextDeny, and ServiceAccount, all essential in enforcing specific behaviors in your cluster and maintaining security.
The Role of kube-bench in Ensuring Kubernetes Cluster Security
The kube-bench tool is not just about identifying potential issues; it’s also about helping you resolve them. The tool recommends hardening your Kubernetes cluster based on the corresponding CIS benchmark version. These recommendations include a variety of suggestions, from adjusting kubelet service file permissions to modifying the host’s PID namespace settings.
Utilizing kube-bench for Managed Kubernetes Services
Managed Kubernetes services, such as Amazon’s EKS cluster, Google’s GKE cluster, or other managed Kubernetes clusters, provide convenience and ease of use. However, security remains paramount. kube-bench can help assess and reinforce the security of these managed Kubernetes services.
To run kube-bench in an EKS cluster or a GKE cluster, you need to install kube-bench using the kubectl apply -f command. You can find the necessary YAML files on the kube-bench GitHub repository. After running the kubectl apply -f command, you can check the status of the kube-bench job using kubectl logs kube-bench.
Understanding kube-bench Test Files and Config Files
kube-bench relies heavily on test files and configuration files. The test files are located in the cfg directory and are formatted in YAML. These files contain the tests to be run by kube-bench, following the CIS Kubernetes benchmark.
In addition to the test files, kube-bench utilizes several configuration files. These include the master node security configuration, the kubelet service configuration, and others. It’s important to understand that these configuration files should be appropriately configured to ensure optimal results when running kube-bench.
Wrapping up
The kube-bench tool is a good tool for anyone managing Kubernetes clusters and who is focused on security to make sure things are deployed and secured according to best practices. Having a way to automate these types of security checks like kube-bench can do, greatly helps in large and even small environments to check Kubernetes clusters.
You can keep an eye on the kube-bench GitHub page for updates and new releases. Ensure your Kubernetes clusters are appropriately configured and stay ahead of potential security threats with kube-bench.