Palo Alto PA 440 New Firewall Review
For the past few years now, I have been running the Palo Alto Networks PA 220 in the home lab environment. I have the lab bundle subscription with the PA 220. However, I have seen the PA 220 will no longer be available for purchase in 2023, with the replacement model being the Palo Alto 400 series firewalls, including the PA 440 security appliance. Let’s look at the new PAN PA 440 security appliance and see the appliance’s new features and capabilities for home lab enthusiasts and others looking to upgrade firewalls located in distributed enterprise branch offices.
PAN-OS on the PA 400 series
The Palo Alto PAN-OS operating system is a world-class network operating system that can classify traffic, applications, threats, and content contained in the traffic. It can also match the traffic with the user, regardless of the user’s location or the type of device they are using to connect.
PAN-OS embeds machine learning into the mix, allowing the Palo Alto Networks PA series firewalls to provide inline signatureless attack prevention and using behavioral analysis to help classify intent.
Palo Alto Networks PA 440
Look at the new Palo Alto Networks PA 400 series firewall, particularly the PA 440 security appliance, and see the units’ hardware specifications, architecture, and performance and key security features.
Overview of features of Palo Alto Networks PA 440 security
The PAN PA 440 firewall is what Palo Alto Networks defines as a next-generation firewall. The 400-series firewalls include the PA-410, PA-415, PA-440, PA-445, PA-450, and PA-460. It brings in machine learning-based NGFW capabilities for distributed enterprise branch offices, retail locations, and midsize businesses and allows these to have enterprise data center features with the standard Palo Alto features and capabilities.

Palo Alto PA 440 features
What are some of the features of the unit? Take note of the following, which describes a few of the features and capabilities of the PA 400 series firewalls:
It embeds machine learning capabilities to provide inline signatureless attack prevention to ward off file-based attacks. It can identify and immediately stop threats, including phishing attacks
It uses cloud-based ML to push zero-day signatures and instructions back to the NGFW and helps block never before seen phishing attempts
Use Behavioral analysis that helps to detect IoT devices and make policy recommendations as part of natively integrated service features on the NGFW
Categorizes applications traversing the network, irrespective of ports, protocols, or other evasive techniques. With the App-IDs, the PA 440 identifies threats based on the app signatures, not just threats at the network layer
You can use app identification to identify payload data within the application. This helps to block malicious files and exfiltration attempts
Create standard and customized application usage reports to help you understand how traffic and user activity enables visibility
You can easily migrate legacy Layer 4 rule sets to App ID-based rules with the policy optimizer.
Enables visibility, reporting, usage reports, security policies, and forensics, not just logs of IP addresses with rich visibility of threats, and other types of traffic
Reduced incident response times
Allows enabling multi-factor authentication
ML-powered NGFW capabilities for improved security posture
Define Dynamic user groups
Applies consistent policies irrespective of locations (home, office, travel), etc
Prevents corporate credentials from leaking and preventing stolen credentials
Provide dynamic security actions based on user behavior analysis
Suspicious or malicious users and enforces security policies to protect your environment
Enables SD-WAN functionality
Threat prevention
Decrypt TLS traffic
Advanced URL Filtering
Advanced Threat Prevention
SaaS security appliance
IoT security policies
Data loss prevention and enables control of your data
Encrypted traffic scanning
Web threat protection
Prevents malicious activity concealed in other types of traffic
It protects your Software-as-a-Service environment
Cloud-delivered enterprise DLP and cloud-based ML processes
Prevent advanced threats and Prevent unknown threats when scanning traffic
PA 440 Network layer features
What are the network layer features of the PA 440 security appliance? Note the following:
L2, L3, tap, virtual wire
OSPFV2/V3 with graceful restart, BGP with graceful restart, RIP, static IP routing, policy-based forwarding, point-to-point protocol over Ethernet (PPPoE)
Multicast: PIM-SM, PIM-SSM,IGMP v1, v2, and v3
Path quality measurement
Inital path selection
Dynamic path change
App-ID, User-ID, Content-ID, WildFire, and SSL Decryption SLAAC
Enterprise Branch Offices
The PA 440 security appliance and the other 400 series appliances are great options for Enterprise branch offices. The 400 series is a great size for the enterprise branch providing great features and capabilities for branch office locations.
Distributed enterprise branch offices are now more widespread and disaggregated. These require more security features and capabilities than ever before, requiring modern advanced security appliance features.
Centralized Management and Visibility
The Palo Alto 400 series firewalls provide centralized management and visibility. You can obtain deep visibility using the Application Command Center (ACC). In the ACC, you can see what comprises network traffic, insights, traffic analytics, and data patterns.
Palo Alto also offers Panorama as part of the management solution with templates and device groups with exceptional end-user experience that allow admins to mitigate risks.
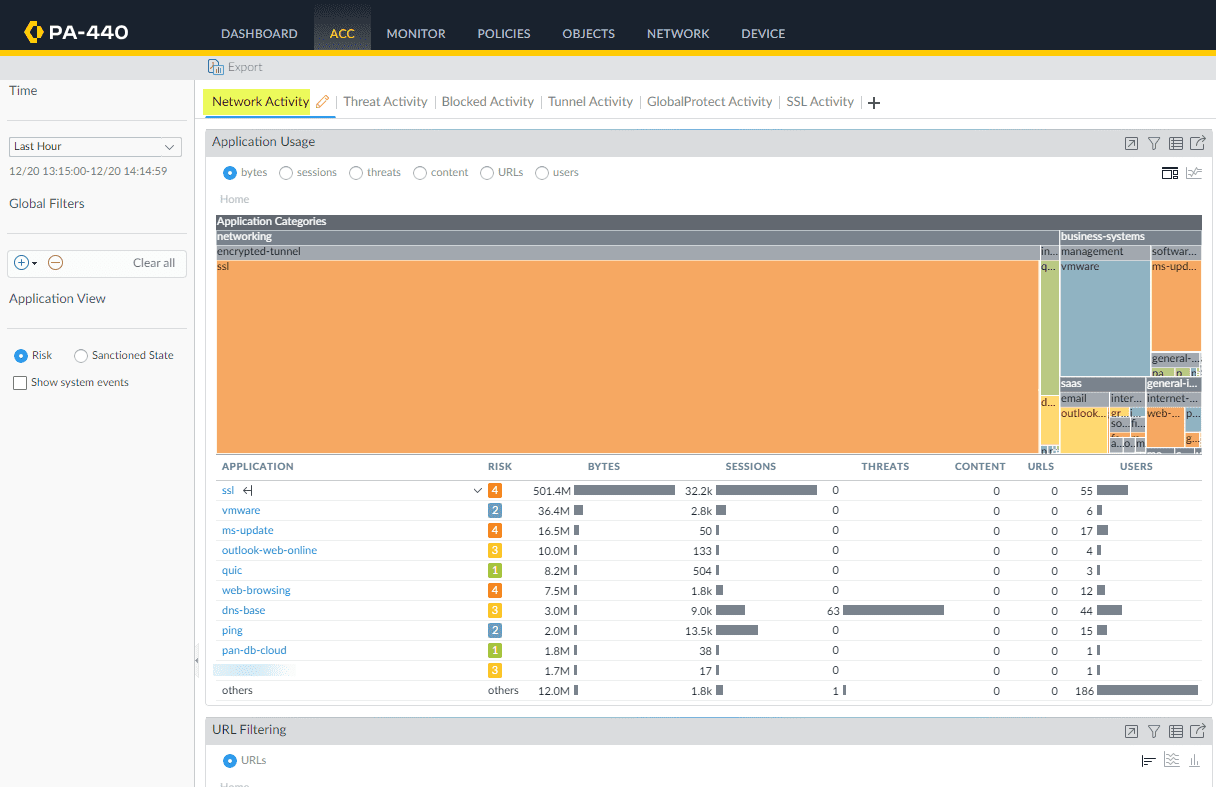
Palo Alto Networks PA 400 series hardware architecture
Take note of the following PA 400 series hardware architecture. As you can see below, the PAN PA 440 and other 400 series firewalls use a dedicated management plane with dedicated CPU and data plane processing, including security, signature, and network processing.
Dedicating resources to management and the data plane prevents a situation where the CPU is taxed such that management of the device is impaired.
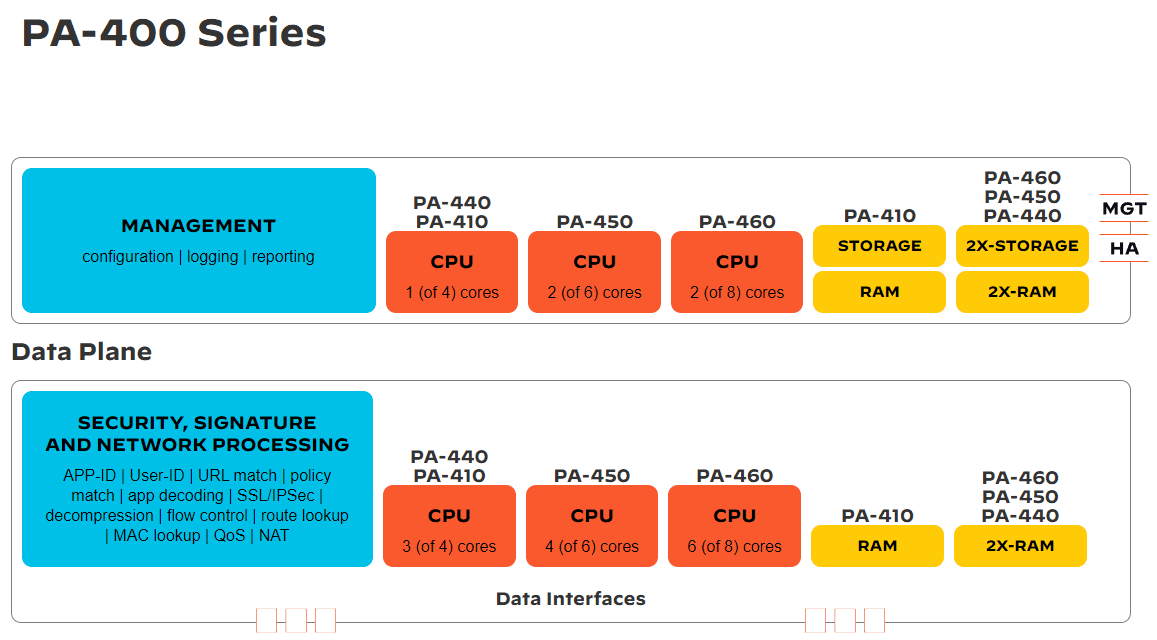
PAN PA 440 throughput and performance
Note the following performance metrics for each of the PA 400 series models to note.
| PA-410 | PA-415 | PA-440 | PA-445 | PA-450 | PA-460 | |
| Firewall throughput (HTTP/appmix) | 1.6/1.2 Gbps | 1.6/1.2 Gbps | 2.9/2.2 Gbps | 2.9/2.2 Gbps | 3.6/3.0 Gbps | 5.1/4.4 Gbps |
| Threat Prevention throughput (HTTP/appmix) | 0.6/0.685 Gbps | 0.6/0.685 Gbps | 0.9/1.0 Gbps | 0.9/1.0 Gbps | 1.4/1.6 Gbps | 2.1/2.4 Gbps |
| IPsec VPN throughput | 0.93 Gbps | 0.93 Gbps | 1.7 Gbps | 1.7 Gbps | 2.2 Gbps | 3.0 Gbps |
| Max sessions | 64,000 | 64,000 | 200,000 | 200,000 | 300,000 | 400,000 |
| New sessions per second | 12,000 | 12,000 | 37,000 | 37,000 | 51,000 | 73,000 |
| Virtual systems (base/max) | 1,1 | 1,1 | 1,2 | 1,2 | 1,5 | 1,7 |
Palo Alto Lab Bundle Subscription
There is a great resource for those looking to get Palo Alto Networks in the home lab environment. They generally are pretty expensive to purchase at MSRP prices. However, in my honest opinion, they are some of the best firewalls you can get in terms of security.
There is an option I want to make sure ones know about, and that is the Palo Alto lab bundle. The lab units are new devices set aside for lab use and aren’t sold for production use in production data center environments. They are a great fit for a home lab. The lab bundles are generally half or more of the MSRP price for the same firewall.
You can purchase the PA 440 security appliance for around $750 instead of $1500. So, be sure to look for the lab bundle for the unit and the subscription when looking for these for home lab use.
Wrapping Up
The Palo Alto Network PA 440 is a great firewall for many different uses and provides great features and capabilities for securing networks at the edge, SMB environments, and even the home lab.






Great review of the Palo Alto firewalls. I’d love to see more content on home use setup and labs. While there are a few videos that cover factory reset to finished home configuration, the videos don’t cover vary many ISP connection types (L3 sub-interface w/PPPoE for example). Also, I haven’t found any videos that cover building a CA to support the HTTPS proxy capability (which would be very helpful).
Robert,
Definitely. I will look at creating some more Palo content, especially around home lab configs and such.
Brandon