IntSights Threat Command Tailored Threat Intelligence
Cyberattacks continue to riddle the news it seems on a daily/weekly basis. We constantly hear of the next major ransomware attack or major data leak event. According to an estimate from CybersecurityVentures, ransomware will attack a business in 2021 every 11 seconds. This is up from every 14 seconds in 2019. Businesses must leverage modern tools to combat the current threats and protect against those that are coming. If you add the current complexity brought about by the “work from home” shift since the beginning of 2020, organizations must extend their thinking beyond the corporate network and have a proactive security stance. Often, evidence of an attack may be brewing for days or weeks in the dark web before it comes to light as an actual attack. What if you had visibility into these threat indicators so you could start preparing? IntSights Threat Command tailored threat intelligence is a great solution that provides this proactive capability to your business.
IntSights Threat Command Tailored Threat Intelligence
In case you have not heard about Intsights before, it is an enterprise-grade external threat intelligence platform that provides external threat intelligence capabilities. it allows security teams to have an even playing field with the tools they need to defend against threats that are rapidly evolving.
IntSights was founded in 2015 by former members of an elite intelligence unit in the Israel Defense Forces. With this background, IntSight has deep “insights” into how attackers think, collaborate, and act. Using this deep understanding and knowledge of the dark web and how attackers operate, IntSights provides a solution that allows organizations to proactively protect themselves by determining the live threats happening across the web, dark web, and other sources.
In the modern, complicated world of sinister threats attacking business-critical data, the days of reactive, and “sit back and wait on an attack” are over. Businesses who do this will find their names in the headlines, in a way they do not want to be recognized (breaches, hacks, ransomware, etc).
IntSights is a proactive threat intelligence and orchestration platform that provides the proactive intelligence you need to defend your business against active threats.
How does IntSights work?
The product proactively scans and gathers intelligence that helps give legitimate businesses the upper hand. If businesses know the threats that may be directly brewing against their organization, it is much easier and more likely the threats can be neutralized effectively.
One of the core tenets of Intsights is it offers a solution that is as simple as it is robust in capabilities. Threat intelligence (TI) can be overwhelming, especially for organizations without a dedicated SecOps team. IntSights makes threat intelligence attainable to the masses. However, don’t let the simple-to-operate designation fool you. It is suited for small to large enterprise environments and brings the same value to businesses of all sizes. How does it do this?
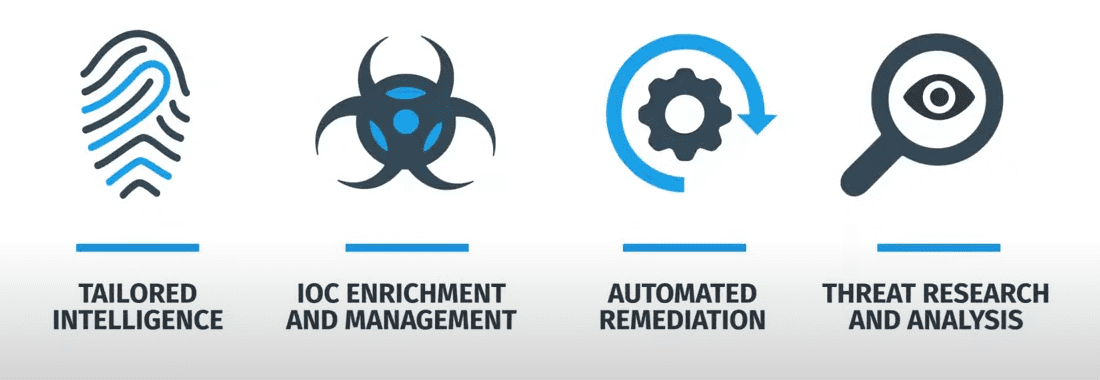
It combines four cybersecurity pillars:
- Tailored intelligence
- IOC enrichment and management
- Automated remediation
- Threat research and analysis
IntSights leverages groundbreaking data mining algorithms and unique cyber-reconnaissance capabilities to monitor hundreds of thousands of sources across the clear, deep, and dark webs, delivering tailored threat intelligence that is specific to your brand, assets, executives, and employees.
It includes monitoring of:
- External domains
- IP addresses
- Sensitive documents
- Brand names
- Mobile apps
- Social media pages
- Confidential projects
- more…
Intsights provides a collaborative solution for real-time threat harvesting that allows you to effectively triage and respond to the threats. Also, it aggregates external threat intelligence, internal device data, and generic and industry feeds to prioritize and enrich indicators of compromise (IOCs) with context and relevance and diagnose severity to your organization.
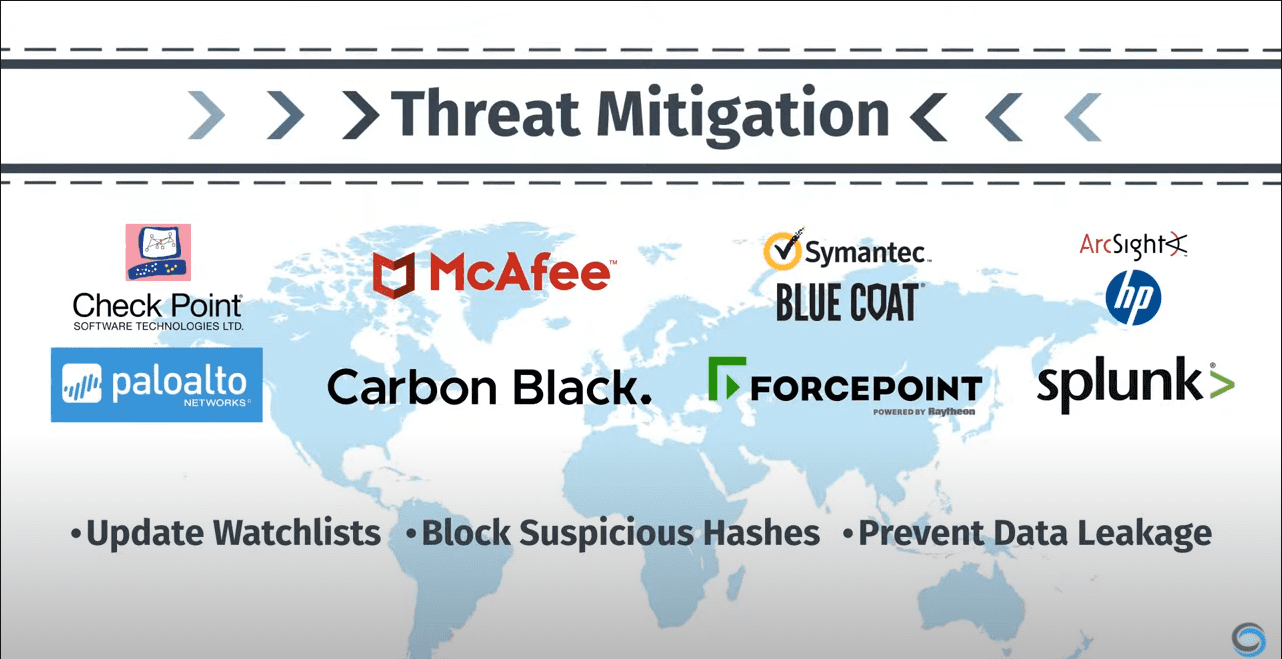
Only IntSights operationalizes intelligence and streamlines the threat mitigation process. It does this by identifying and automating the remediation of external threats. It uses orchestration and automation that ties in with your other security solutions, including connecting to:
- Leading firewalls
- endpoints
- web proxies
- SIEMs
- Automatically update watchlists
- Block suspicious hashes
- Prevent data leakeage using stolen credentials
It can also take down fake mobile applications, phishing sites, and malicious domains through integration with Google and partnerships with leading apps stores, social media platforms, and registrars.
IntSights Active Directory Integration
One of the robust solutions offered by IntSights is the IntSights Active Directory integration. Often attacks start with compromised credentials that can easily be bought and sold on the dark web. As a case in point, the major ransomware attack on Colonial Pipeline involved a set of VPN credentials that were part of a breached password list found on the dark web.
In addition to ransomware gangs and the ludicrous profits they make, a new lucrative market is opening on the dark web – Initial Access Brokers (IABs). IABs go out and harvest valuable credentials and simply sell these on the dark web, often to ransomware gangs looking to encrypt a business with ransomware.
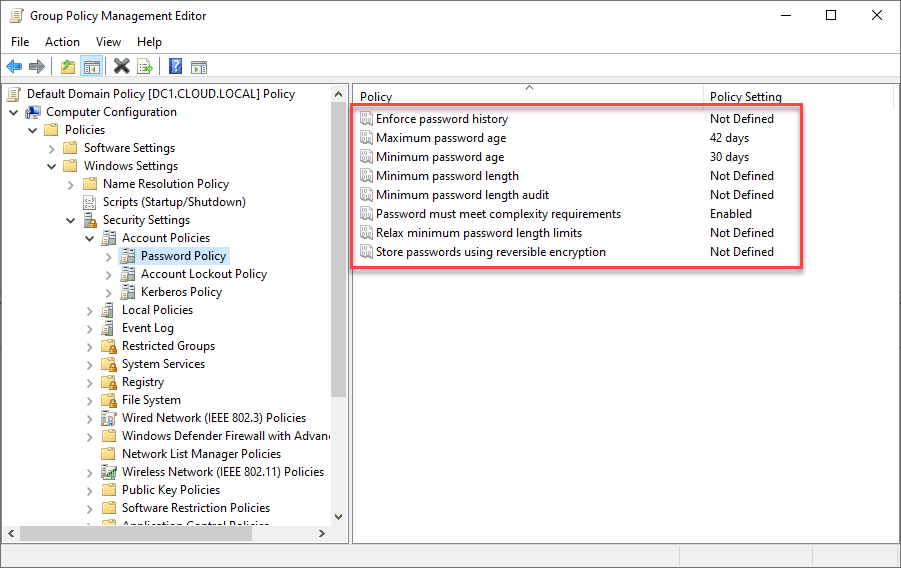
When you look at the traditional tools available in Active Directory, many things stand out:
- The traditional password policies are old and outdated
- They do not provide all the controls needed to protect against modern password threats
- It has no built-in breached password protection
This is where IntSights Active Directory Integration comes into play. IntSights Active Directory Integration is able to validate and lockdown compromised credentials automatically. As already detailed, IntSights is scanning the dark web for threat indicators. It can spot accounts from your organization being bought, sold, or leaked on the dark web and can instantly validate if credentials are active and require a response.
This helps to eliminate manual analysis which reduces the burden of manually checking compromised accounts against your active employee list. It then not only identifies these actively compromised credentials, it also allows building custom policies to instantly validate and trigger credentials reset notifications. This allows locking down compromised credentials without disrupting productivity.
Real world benefits
The IntSights solutions bring tremendous value to businesses. Not only are you getting tailored threat intelligence that is specific to your brand, external resources, employees, C-level, IP addresses, websites, etc. You are getting the automated response remediation that performs orchestration with your existing security solutions.
To me, that is the beauty of IntSights. It is not a rip and replace of your existing solutions with IntSights. IntSights is a solution that integrates with and turns your threat protection up 200% with the proactive intelligence provided.
IntSights Cybersecurity Products
- Threat Intelligence – https://intsights.com/products/threat-command –
- Threat Intelligence Platform (TIP) – https://intsights.com/products/threat-intelligence-platform
- Vulnerability Risk Analyzer – https://intsights.com/products/vulnerability-risk-analyzer
- Threat Third Party – https://intsights.com/products/threat-third-party
- Intsights Active Directory Integration – https://intsights.com/solutions/active-directory-integration
My Thoughts
While this is a compensated overview of the IntSights Threat Command tailored threat intelligence solution, as with any paid post, I reserve the right to my opinions. IntSights provides great value to customers to elevate your cybersecurity stance from a defensive /reactive posture to a defensive/offensive/proactive posture. In today’s threat-filled world, this is what is needed.
Aside from the product links above, be sure to check out the IntSights site here where you can request a demo: