Monitor for ZeroLogon Vulnerability Events in Active Directory
Late in the Summer, Microsoft released patches for one of the most critical vulnerabilities that we have seen in quite some time. Using this vulnerability, an attacker could completely “own” your network and do anything they want to do. The other worrisome part of the attack is that it isn’t that difficult for exploitation and only requires a compromised machine that is sitting on the internal network with access to a domain controller. This vulnerability has become known as the ZeroLogon vulnerability due to the way the attacker can exploit it. In the first phase, Microsoft expects everyone to apply the patch to the domain controllers. Then what? You need to be looking for client connections making insecure netlogon connections to Active Directory. I want to show you a free little tool that will allow you to monitor for ZeroLogon events in your Active Directory environment.
ZeroLogon Vulnerability Patch and Next Steps
As mentioned, Microsoft has released a patch for the ZeroLogon vulnerability that needs to be applied to your domain controllers. If you haven’t done this already, do this ASAP!
Download the patch here:
Microsoft is dealing with the ZeroLogon vulnerability in two phases. The initial phase is patching the Active Directory servers for the vulnerability in the NetLogon process. There is an additional phase that will begin on February 9, 2021. This is known as the enforcement phase. Let’s detail these a bit further.
Microsoft has detailed a plan of action as an overview to the entire process as the following:
- Update your Active Directory domain controllers with the patch that has been released as of August 11, 2020
- Find any and all devices that are making vulnerable connections by monitoring the event logs
- Address the non-compliant devices making the vulnerable calls to AD
- Enable the enforcement mode on your domain controllers to deny access to any vulnerable devices. This will be done on February 9, 2021. The following registry key will be changed to a “1”.
ComputerHKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesNetlogonParametersFullSecureChannelProtection
If you noticed, I have the point 2 in bold. This is the point that we want to take a look at for monitoring purposes. If you are like me, you most likely do not want to reactively go through the event logs on your domain controller looking for non-compliant device connections by way of an EventID.
With this being said, if you don’t have a SIEM in place or another log-forwarding device that you are already using to collect event logs and notify on these, there is another little tool that can do the trick.
Monitor for ZeroLogon vulnerability events in Active Directory
There is a little tool that you can download for free from NetWrix called the Netwrix Event Log Manager. With this tool, you can setup a monitor that will query event logs for particular hosts and set these up to email you if the event IDs are seen in the logs.
In this way, you can have relatively real-time alerting setup if any of the vulnerable Netlogon EventIDs are seen on your domain controllers. Let’s step through how to setup the utility.
You can download the utility here:
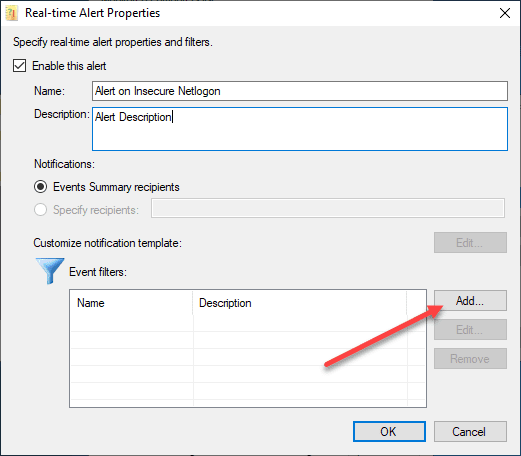
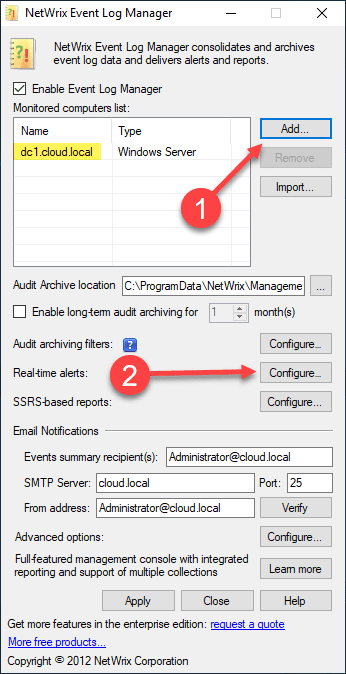
After installing the utility, which is just a “next, next, finish” process, you will see a simple GUI to configure. Basically you will add the machines (domain controllers) you want to monitor, as well as add the EventID filters you want to alert on. After you add your DC name, 2) click the Configure button to add the real-time alerts to Monitor for ZeroLogon vulnerability events in Active Directory.
Here I only have one DC in the lab environment, but you would add all the DCs in the environment that will be used for authentication.
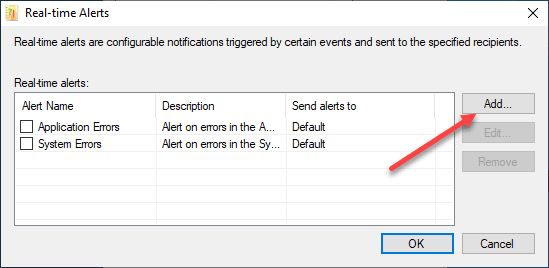
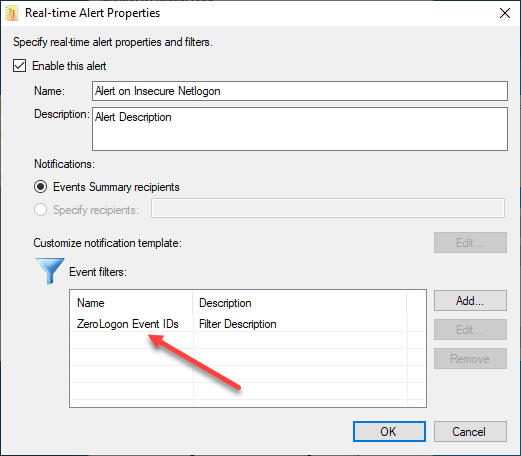
Click on the Add button in the Real-time Alerts dialog box.
On the Real-time Alert Properties, click the Add button under the Event filters to add the EventIDs you want to alert on.
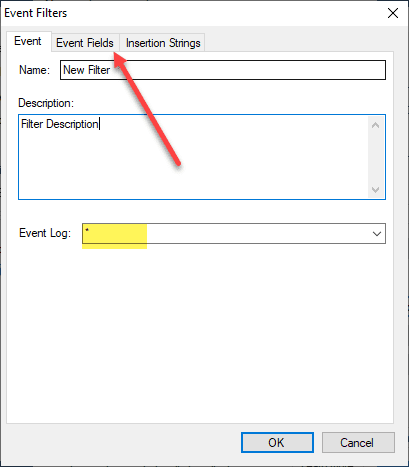
Here you can scope it down to the Event Log that you want to monitor. I am simply leaving at “*” for all of them. According to the Microsoft documentation, the ZeroLogon eventIDs for insecure connections should be displayed in the System log.
Which EventIDs do you add?
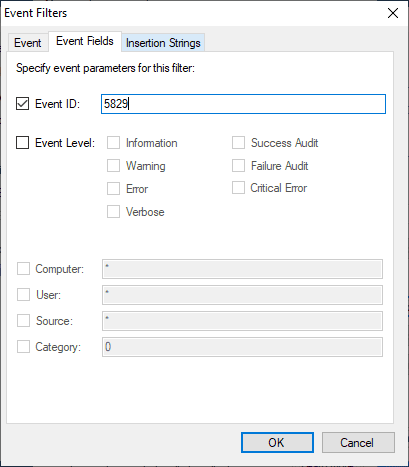
- Event ID 5829 – non-compliant devices (insecure Netlogon sessions)
- Event IDs 5827 and 5828 – Microsoft alludes to these Event IDs with supported devices that for some reason are connecting insecurely (check patching, etc).
Below, I am adding the 5829.
After clicking OK to add the EventID, it should display in the Event filters.
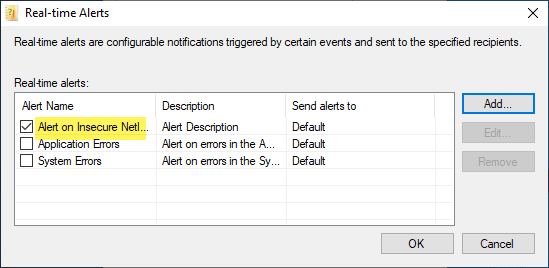
After clicking OK here, you will see your Real-time Alerts displayed with the new alert you just added with a check, showing it is enabled.
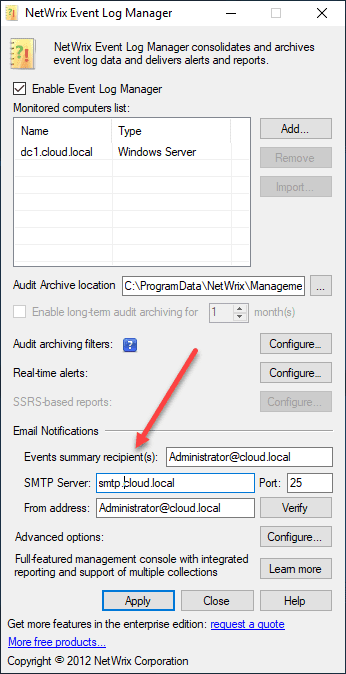
Now, just make sure your SMTP properties are configured as you want them with the correct SMTP server and email address configured for both the from and the Events summary recipients configured.
When the EventIDs are seen, you will get an email.
Wrapping Up
With the NetWrix Event Log Manager installed and configured, you can monitor for ZeroLogon events in your Active Directory environment and make sure you get real-time notifications of EventIDs that correspond to the ones noted by Microsoft after patching your servers for the ZeroLogon vulnerability.
Between now and February 9, 2021, you want to be monitoring your Active Directory domain controllers to see if you have any devices hitting the DCs insecurely as these will need to be remediated before the enforcement phase. Microsoft has also introduced a new Group Policy that will allow those devices to continue connecting insecurely as well. Stay tuned for more as we draw closer to this.
Netwrix also has a full-blown solution called Netwrix Auditor that provides powerful solution to network monitoring and Event logs across your environment.