Share SSL Certificates Between Multiple IIS Servers with Centralized Certificates
Managing certificates is probably one of the most cumbersome and administratively burdensome tasks that IT admins have to carry out on a day-to-day basis. This is especially true if you have multiple web servers that may be forward facing in a load balanced farm. There may be multiple servers that have multiple websites configured with different certificate configurations. Managing and scaling your SSL certificates across such an environment would be very labor intensive and tedious. Is there a way to centralize SSL cert management with Windows Server IIS? Yes. This is accomplished through the use of Centralized Certificate Store (CCS). Let’s take a look at how to share SSL Certificates between multiple IIS servers with Centralized Certificates.
What is Centralized Certificate Store CCS?
As the heading gives away, CCS stands for Centralized Certificate Store and has been around since Windows Server 2012 and higher. This may be a feature that you haven’t heard about or haven’t used in your environment. However, it is a great feature to manage SSL certificates, especially in environments where there are many sites and servers with multiple SSL certificates. In essence, instead of storing the SSL certificates locally on each server, the SSL certificates are stored in a central file share. How does Centralized Certificate Store (CCS) work?
Centralized Certificate Store CCS is a component of the Web Server Role in Windows Server 2012 and higher that allows you to have a shared configuration between Windows Server IIS Servers for SSL Certificates. Typically, most IT admins will make use of the certificates that are stored in the My Computer Personal store for certificates.
This has worked in the past and continues to work, even with modern versions of Windows Server. There isn’t an issue with utilizing this same approach. However, it does not scale very well. As mentioned, if you have a web farm with many servers perhaps using the same exact certificate, importing the same SSL cert and private key into each server can be tedious. A much better approach would be to centralize and share the SSL certificate that is used across the web farm members so the SSL cert lives in one location and the member servers of the web farm can all reach the same cert for encrypting the web traffic.
When the certificate comes up again for renewal, the same process has to be repeated across the board to import and install the new renewed certificate for the IIS website on each server. Centralized Certificate Store, again, helps to resolve this issue.
There are also some minor performance improvements for SSL communication when using CCS for serving out SSL certificates. When using CCS, there is only one binding and the certs are loaded on demand and cached for future use. In this way the memory consumption is reduced and there is a slight performance gain.
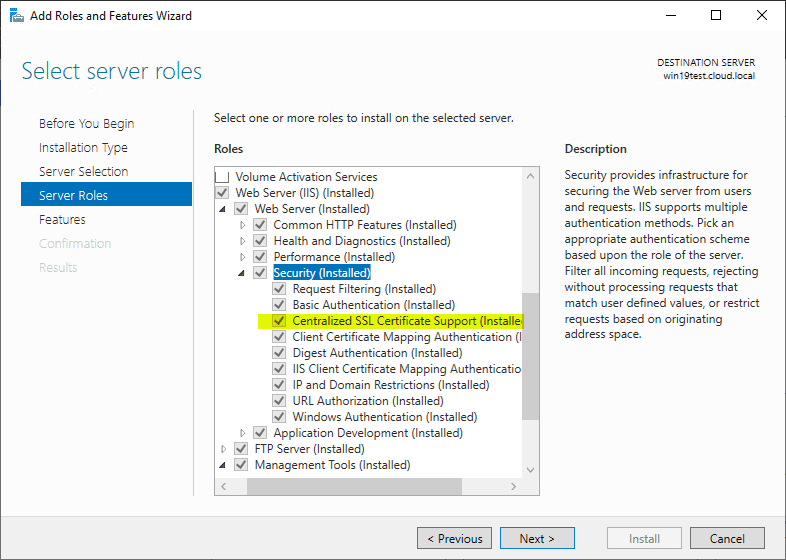
Installing Centralized Certificate Store (CCS)
Installing the Centralized Certificate Store Centralized SSL support for Windows Server IIS is easy. The Web Server subcomponent is found under the Web Server (IIS) > Web Server > Security section.
Other Requirements for Centralized Certificate Store (CCS)
What other requirements are needed for the CCS to work correctly? Aside from installing the sub component for IIS Web Server, you need to have:
- File share – You need to have a centralized share that will be accessible from each server that will be making use of the shared SSL certificate
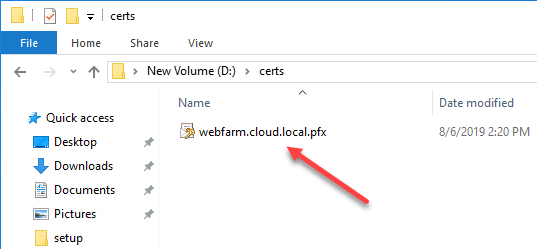
- Certificates – You need a certificate in the PFX format that contains both the public and private keys
- File naming formatted correctly – For IIS to find the exact file, a naming convention has to be used while storing certificates on the CCS file share. As per naming convention the name of the certificate should be: subject name of the cert. CCS will look for an SSL cert with this exact name when looking in the CCS share.
Share SSL Certificates Between Multiple IIS Servers with Centralized Certificates
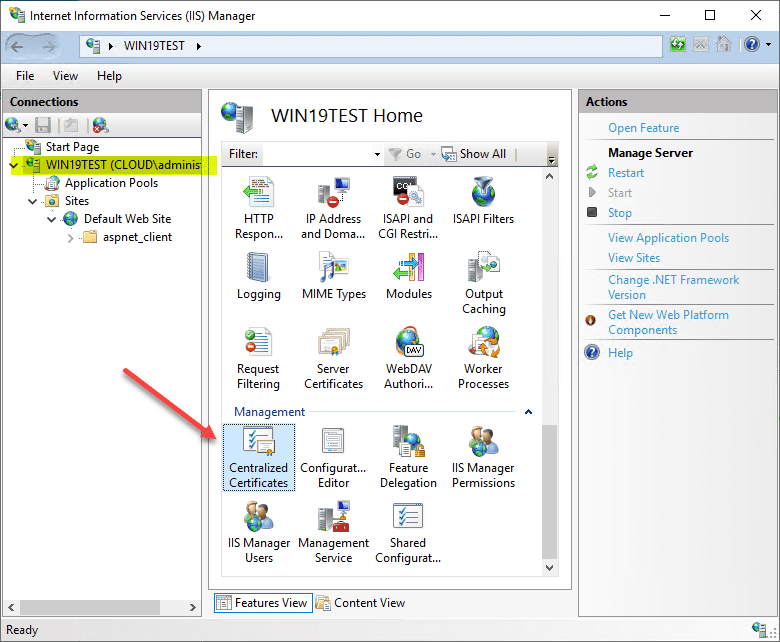
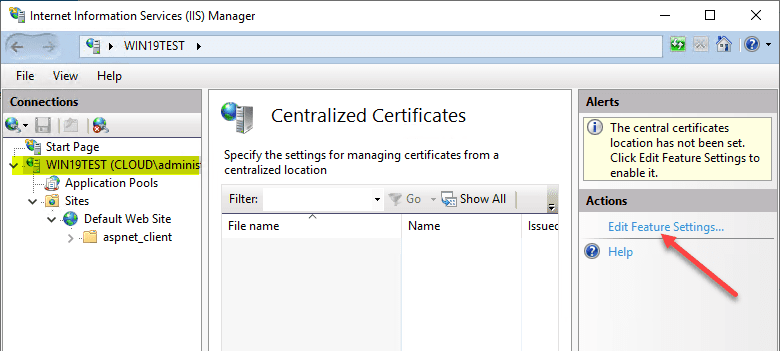
To start configuring the Centralized Certificates Store CCS for use with serving out SSL certs for your IIS websites, navigate to the IIS server name > Management > Centralized Certificates.
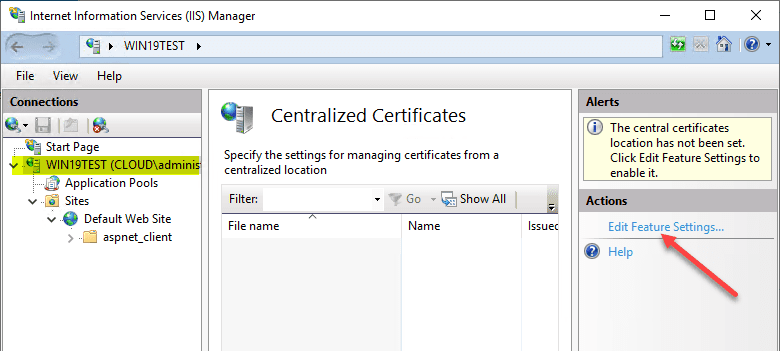
Click the Edit Feature Settings link to begin configuration.
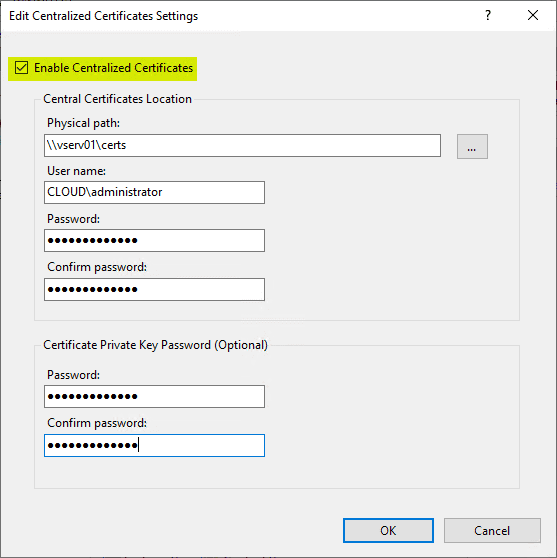
This launches the Edit Centralized Certificates configuration dialog box. Points of configuration to make note of:
- Enable Centralized Certificates (Enable the checkbox)
- Physical Path
- User name
- Password
- Certificate Private Key Password (Optional)
In the share, I have placed the PFX certificate for sharing between servers.
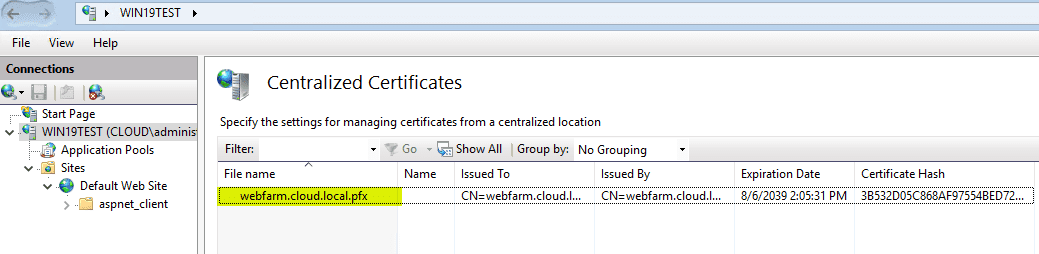
Automatically, the Centralized Certificates dashboard shows the certificate found in the share.
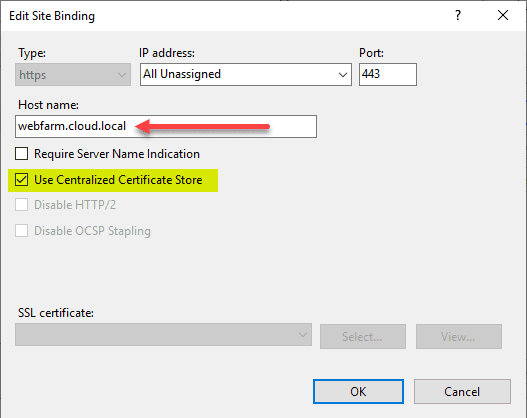
Configure IIS Website to Use Centralized Certificates
Now for using the certificate in the Centralized Certificate Store in the bindings of an IIS website. Populate the Host name and then place a check next to Use Centralized Certificate Store. You don’t have to use the Require Server Name Indication option, however, the two are compatible for use together.
Security Best Practices of Centralized Certificate Store
Don’t forget about security with CCS. As noted by the Microsoft blog post, the following are security best practices for CCS:
- Use least privilege practices for the account you configure IIS to use to access the share for CCS. Lock down your share and NTFS permissions as well as remove the account from Domain Users and set workstation logon restrictions (don’t forget to add the computer objects for the servers hosting the share!). Also restrict others from accessing the share since it will have full certificates stored there.
- At this time I am not aware of the ability to use Group Managed Service Accounts for this feature. I will update the blog if I find out that you can.
- Bitlocker protect the volume that hosts the share for the certs. We introduced the ability to Bitlocker protect Cluster Shared Volumes in Windows Server 2012. The volume hosting the share holding your SSL certs might be a good candidate perhaps? J
- Also note in the config dialog how the Private Key password is optional. This assumes that you did not use a password to protect the private key when you exported the certificate to place on the share. I can’t think of a reason as to why you would NOT want to use a private key password. So set a private key password and configure this option.
Wrapping Up
Share SSL Certificates Between Multiple IIS Servers with Centralized Certificates is a great way to lower the administrative burden of managing SSL certificates. Not only is the configuration of multiple servers much easier, there is also a slight performance advantage to CCS as well. The requirements are minimal and the binding for an IIS site is easy to activate for use with CCS.