Get notified of failed Windows login attempts
In tinkering a lot with security and other facets of security and notification lately with Windows workstations and servers, I am a big advocate of notications when it comes to security events that are worth notifying over. I had written a post earlier about getting notified when MAC address changes happen on your network to monitor when new machines are connected as well as when IPs change layer 2 addresses. When it comes to someone trying to brute force your passwords, you also need to know what is happening and from where those events are coming from. Let’s take a look at how to get notified of failed Windows login attempts.
Get notified of failed Windows login attempts
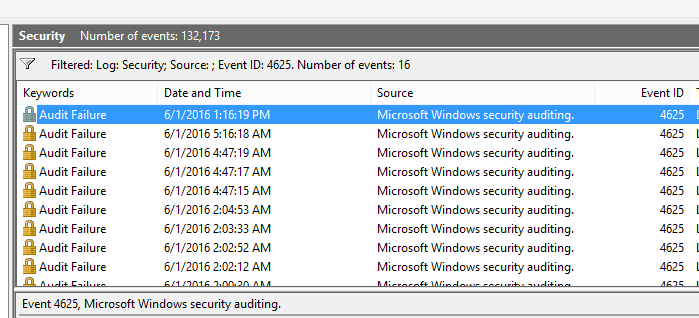
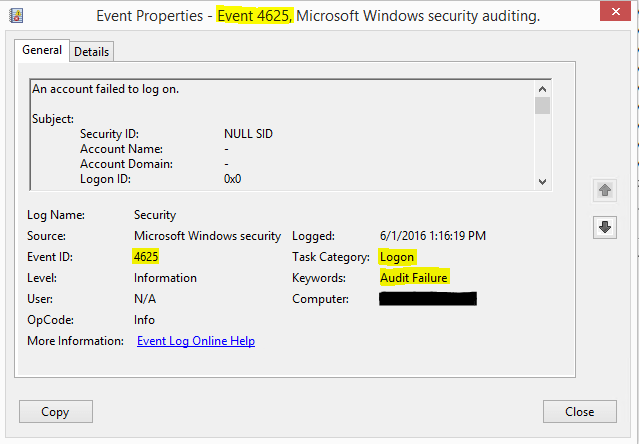
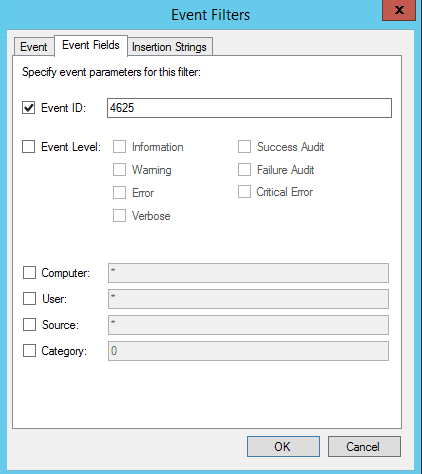
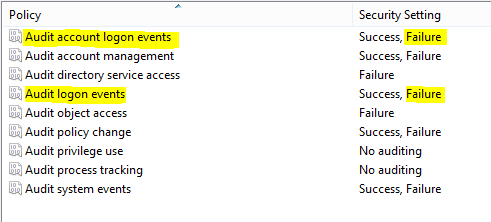
In newer Windows operating systems, Event ID 4625 is the key event to trap for in the Security log of a Windows machine. The key here is your audit policy settings to capture Event ID 4625. You need to audit at least for failure in Audit account logon events and Audit logon events.
Once you have Auditing enabled on your workstation/server, you can start capturing the events as you can see below in the filtered view of the Security log, filtering for Event ID 4625.
Now that we are gathering the events for the failed logins, we now have something we can work with to start notifying.
Notification Methods
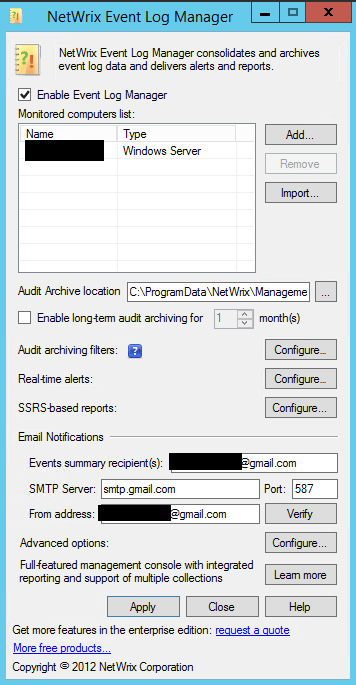
One of the easiest ways to get notified of failed login events is to use the Netwrix Event Log Manager which is a free tool from Netwrix. What I like is the SMTP configuration is easy to setup, even using the gmail SMTP server to a gmail address. The events are also highly configurable to the Event ID and even multiple event ids.
Let’s take a look at how to configure NetWrix Event Log Manager to capture Event ID 4625 and email a gmail address.
Below we have setup:
- SMTP Server: smtp(dot)gmail(dot)com
- Event summary recipient(s): specify your email address, gmail here in this example
- Port: For Gmail, we have to use port 587
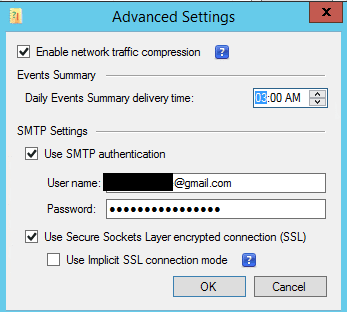
We need to click the Advanced Options and then Configure to check off the Use Secure Sockets Layer connection (SSL) – this is required for our connection to Gmail to work. I also suggest that you use the Verify button to see if you have any errors sending the test email before pulling your hair out trying to figure out why you aren’t getting alerts in testing.
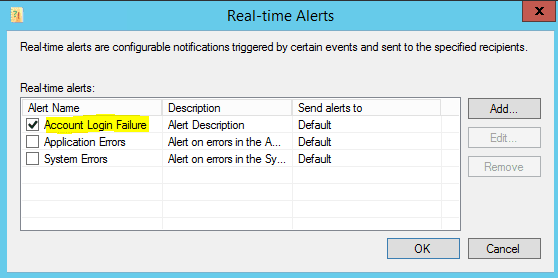
If we click the Real-time alerts Configure we will be able to setup the alerts we want to check for in real-time. Click Add.
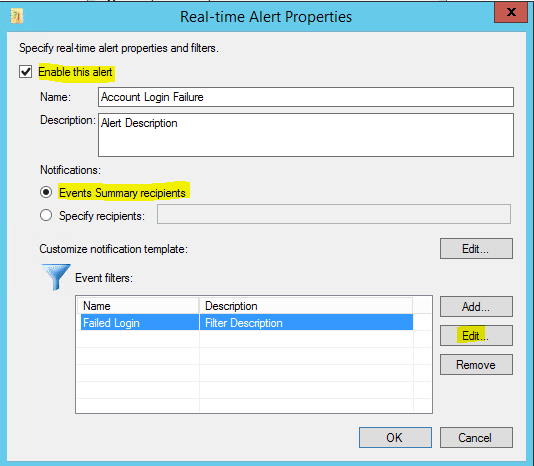
We want to Enable the alert and then Add a Customize notification template.
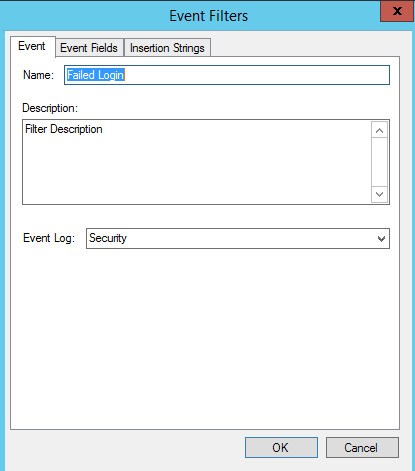
On the Event Filters we name the Alert.
Then in the Event Fields tab we can specify the Event ID we want to check for, in this case 4625.
Final Thoughts
Get notified of failed Windows login attempts is a really simple yet effective way to monitor if someone is trying to brute force a critical system such as a system out in the DMZ that may be exposed to the Internet. Checkout my post here about Securing RDP access to Home Lab as a typical example of securing a server that is forward facing.