Running your home lab is a tremendously good resource for learning. It allows you to get your hands on many different technologies and experiment with these in a way that would not be possible otherwise. However, Most who spin up a home lab will focus on the functionality aspect of the lab or the performance aspect and not home lab security. Security is usually an afterthought since most consider their home labs to be a playgrond of sorts.
But the threats facing home environments today are evolving, and traditional perimeter thinking doesn’t cut it anymore. Let’s look at five overlooked threats that could be compromising your home lab security right now and what you should do to fix them.
1. Exposed services due to misconfigured reverse proxies or firewall rules
If you expose any type of service or service port to the Internet, you better be thinking about security of your solution. If you have monitored a typical residential Internet connection, if you expose just a simple web server, it only takes minutes before it starts getting hit with all types of scans and compromise attempts. RDP servers are even worse, along with other dangerous ports to expose like SQL servers, etc.
Some may intentionally expose services to the outside, but others may just be learning how to use a reverse proxy and not really realize that the services they have spun up with a reverse proxy are actually exposed to the outside, either due to their proxy config or a misconfigured firewall rule.
Why this is dangerous in 2025:
Threat actors use tools like IP scanners that can scan IP ranges for known reverse proxy signatures and test these for subdomains. There may be public DNS records and misconfigured firewall rules that allow scanners in.
How to fix it:
- Scope Internet access down: My cardinal rule of exposing services is don’t do it unless you have to. If you have to expose a service to the outside world, do it in a way that it is scoped down to a specific IP address, or IP range, DNS name, etc. Use a VPN instead or a modern solution like Twingate, which I highly recommend.
- Use Access Control: Tools like Cloudflare Access, Authelia, or SSO with OAuth2 Proxy are critical for securing public-facing services.
- Default Deny: Set your reverse proxy to deny all and only allow explicitly defined hosts.
- Subdomain hygiene: Regularly do an audit of your DNS records, proxies, and access logs. Remove subdomains that you aren’t using for a specific DNS zone.
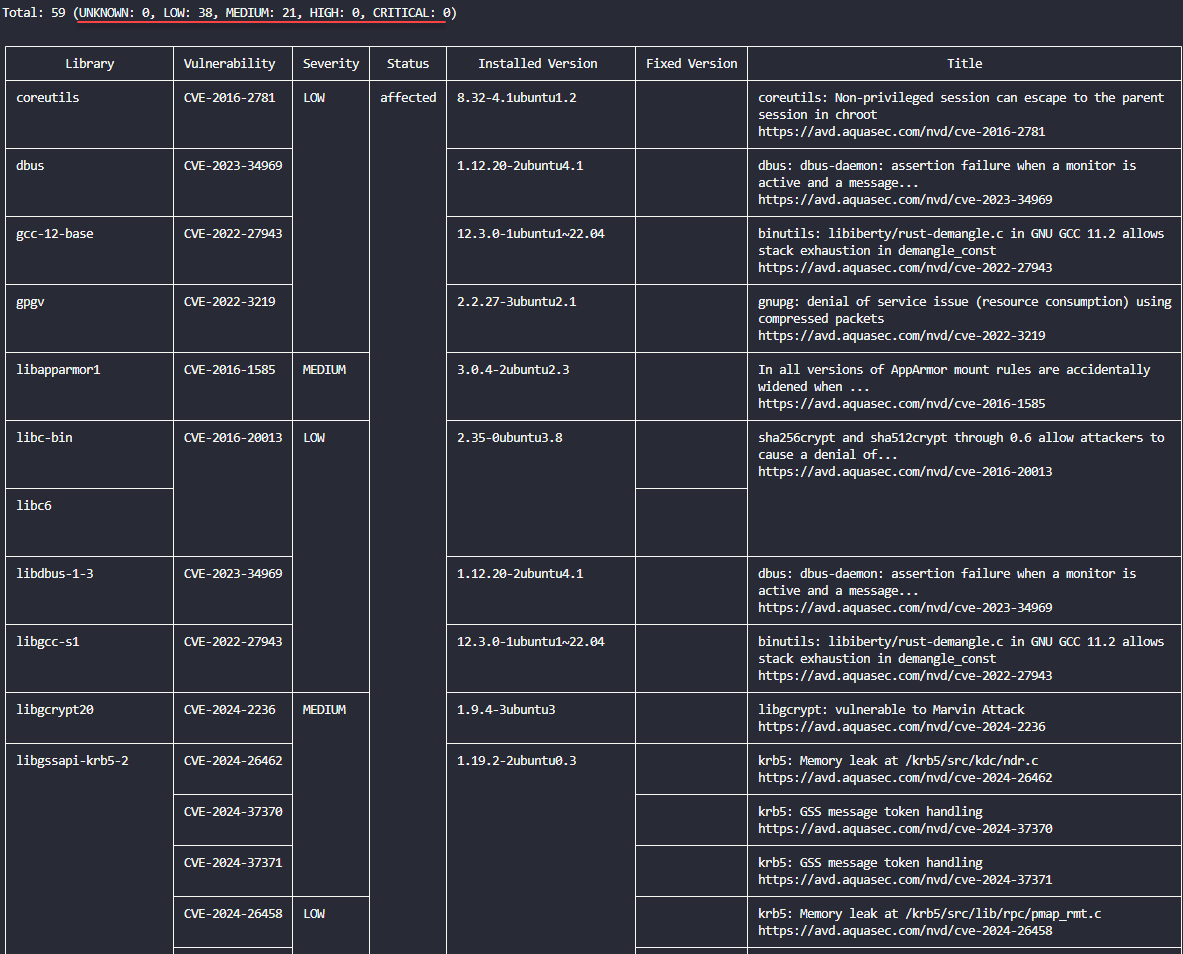
2. Unmonitored containers and images
Docker containers and containerized environments are awesome. However, due to their small size and ephemeral nature, they can tend to be neglected or forgotten about altogether. This includes the containers themselves and container images.
Why it’s dangerous:
Tracking your container images and vulnerabilities found in those images is extremely important. Just like a virtual machine running a full-blown operating system that needs patching, container images also need to be repulled, patched, etc.
Real-world scenario:
In a recent Shodan scan, hundreds of self-hosted admin tools running in Docker were discovered using images over 2 years old—many of which had known CVEs. Also, it may not be the base image that has or develops vulnerabilities but the libraries inside the container images.
How to fix it:
- Use image scanning tools like Trivy, Grype, or Docker Scout to scan your Docker images for vulnerabilities. These are also great tools to incorporate as part of the CI CD pipelines
- Automate updates to Docker with Watchtower or Shepherd – These allow you to keep your container images updated with the latest, both in standalone Docker hosts or Docke rSwarm clusters
- Use GitOps workflows in Portainer or Flux CD to track and validate image versions before deployment.
3. Excessive privileges
Privileges in a home lab can get to be all over the place. Typically we may just assign ourselves administrator access for everything as this is just the easy way to do it. However, this can be a dangerous thing to do.
Why it’s dangerous:
Leaving administrator access that was granted in your lab 2 years ago can easily be something that is just left that way, or totally forgotten altogether. Weak passwords may also be used on these admin accounts for convenience or to easily remember while labbing. This can open gaping holes in your security for your lab environment, especially when this gets accidentally combined with forgotten or misconfigured exposure to the outside Internet.
Why it matters in 2025:
Excessive privileges found on user accounts are one of the main ways that attackers can breach environments. Also, it’s easier than ever to spin up VMs and containers that copy credentials or bake in admin access or SSH keys.
How to fix it:
- Rotate SSH keys quarterly, and store them in a secure vault like Hashicorp Vault, etc
- Audit
~/.ssh/authorized_keysand/etc/sudoersregularly across all hosts. - Limit container capabilities using
--cap-dropand--read-onlywhere possible. - Use RBAC in Portainer, Kubernetes, and GitLab to reduce privileges and exposure from certain accounts.
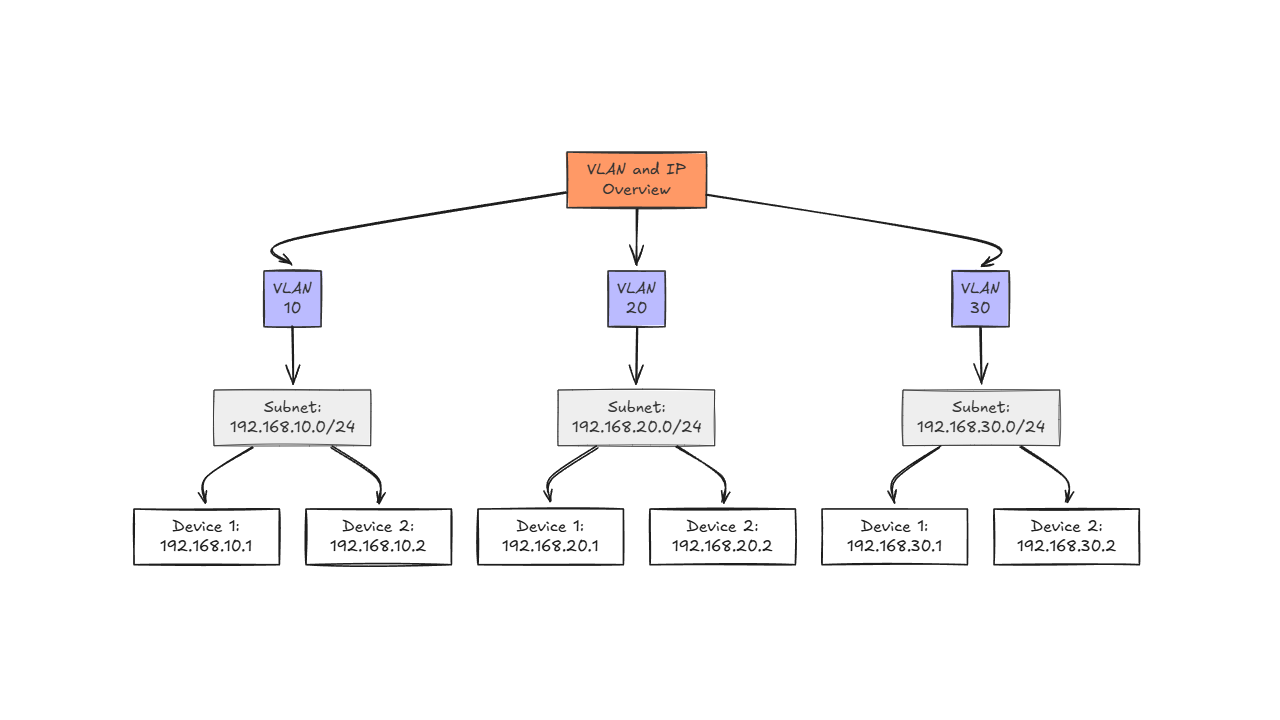
4. Lack of internal network segmentation
This is a huge one. Segmenting your network should be a “step 1” type configuration when you are setting up and configuring a home lab environment. You need to separate your resources based on their role and risk profile. Always put things like IoT and wireless devices on their own layer 2 VLANs and network address spaces.
Why it’s dangerous:
A lot of home labs run flat networks (192.168.1.x or 10.0.0.x) where every device can talk to everything. That includes your smart thermostat, your VM running Kali Linux, and your NAS full of backups. This setup is a dangerous configuration that can lead to easy lateral movement from an attacker
Why this matters in 2025:
Even with clusters of Raspberry Pis, many virtual hosts running on mini PCs, many home labbers are not segmenting traffic between their various networks. This includes traffic that is management, data, and public-facing services. If one device is compromised in a flat network, everything else is at risk.
How to fix it:
- Create VLANs: Separate IoT, lab, and admin traffic using VLANs on your Unifi, pfSense, or OPNsense firewall.
- Use firewall rules: Always block unnecessary inter-VLAN traffic unless absolutely needed for services. Even then scope this down to where only those needed services can communicate between specific hosts that need them.
- Isolate management interfaces: iDRAC and IPMI interfaces, management IPs, and ESXi hosts should live on their own network, not on the same network as your smart thermostat.
5. Browser extensions and SaaS apps
I’m not sure about you, but I am reading more and more about compromised browser plugins and other ways that attackers are stealing data through browsers. This is a huge risk as many are inclined to use their admin workstation for general Internet browsing at the same time as managing their home labs. Using the same browser to do general Internet browsing is a dangerous practice.
Why it’s dangerous:
You use your main browser to check logs in Portainer, access Grafana dashboards, and SSH into servers via browser extensions. But you’re also using that same browser to check Gmail and install extensions that might be harvesting data. Also, sensitive cookies and tokens get stored often long term in browser sessions. These can even bypass 2FA that you have configured.
Why this is important in 2025:
If you happen to install a malicious browser extension, these are now sophisticated enough to scrape data from local web apps and forward cookies, tokens, and even screenshots of your data.
How to fix it:
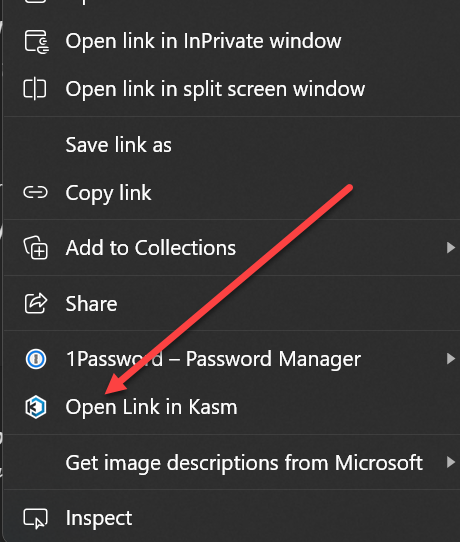
- Use separate browser profiles for personal use and home lab access.
- I personally use Kasm as a secure browser environment for accessing external resources or even internal resources
- Block outbound access to known SaaS exfil domains using pfBlockerNG, Pi-Hole or AdGuard Home.
- Consider tools Wazuh to watch for suspicious outbound traffic from your network.
Bonus: Use tools like Netdata and Syslog Aggregation
One of the reasons that persistent threats go unnoticed in home lab environments is that home labbers don’t often monitor their networks or devices.
Netdata is one of my favorite tools for easy real-time monitoring for the home lab, especially for containers and Kubernetes. It has cloud and even a local dashboard for monitored nodes, and you don’t have to manage the infrastructure for your monitoring since it is SaaS. They also have a home lab license that is super reasonable.
It can monitor and alert on:
- Unauthorized login attempts
- High network utilization
- Unexpected container or VM restarts
Also, you can configure syslog aggregation using Graylog or Loki/Grafana to have log data to reference when needed and to perform security audits.
Wrapping up
One of the biggest myths in 2025 is that a home lab isn’t worth targeting. However, now, with scanning bots leveraging AI to detect vulnerable environments, your lab is absolutely a target, especially if it’s online 24/7/365. You don’t necessarily need enterprise security solutions that are pay for products, but you do need an intentional game plan fro home lab security. This includes good security hygiene, network segmentation along with good firewall rules, limiting exposing services to the outside, and many other good practices.
Start with:
- A routine patch cycle
- Proper isolation
- Logging and alerts
- Access reviews of users and SSH key rotation
- Endpoint and container hygiene
My motto is to treat your home lab like a mini datacenter that contains your personal data and admin information. You are solely responsible for protecting yourself. Do yourself a favor and add 10 minutes a day to perform some type of security audit in your home lab and document this. You would be surprised in a week’s time how many security holes you will plug with this approach.
Google is updating how articles are shown. Don’t miss our leading home lab and tech content, written by humans, by setting Virtualization Howto as a preferred source.