Openscap: Open Source Vulnerability and Compliance Scanner

Open-source security tools are not only cost-effective, they are also very powerful. OpenSCAP is a robust line of defense in achieving and maintaining system security compliance. It delivers many features, including for the community and enterprise businesses.
Table of contents
- What is OpenSCAP?
- Diving Deeper into the SCAP Security Guide
- Customizing OpenSCAP with Your Own Content Files
- OpenSCAP Compliance with the Australian Cyber Security Centre
- The Process of an OpenSCAP Audit Scan
- Interpreting OpenSCAP Outputs
- OpenSCAP and Health Insurance Portability Accountability Act Compliance
- Installing the OpenSCAP Scanner
- Mastering OpenSCAP Scanner Commands
- Wrapping up
What is OpenSCAP?
OpenSCAP, is short for or an abbreviation for Open Security Content Automation Protocol. It in short is a standardized set of open-source software tools that provides you with automated vulnerability management. OpenSCAP also helps to automate the process of maintaining system security.
OpenSCAP suite includes libraries that provide an array of SCAP functionalities, a scanner that runs on various operating systems, and a multi-purpose tool designed for manual XCCDF (Extensible Configuration Checklist Description Format) and OVAL (Open Vulnerability and Assessment Language) management.
SCAP security guide
A defining feature of OpenSCAP is its SCAP Security Guide, a repository of SCAP content files and security policies for different operating systems. These policies define security checklists and create standard system security profiles that assist in maintaining an optimal security posture.
OpenSCAP is a powerful solution, compatible with multiple operating systems like Red Hat Enterprise Linux, SUSE Linux Enterprise Server, and others. It can be customized to fetch remote resources or utilize default content file templates to assess system security. The scan results, represented as XML SCAP SSG content, can then be interpreted and acted upon to ensure the robustness of system security.
By enabling a repeatable and open standard for managing security, OpenSCAP serves as a crucial tool in the ever-evolving field of cybersecurity, catering to a wide range of community and enterprise businesses.
Understanding OpenSCAP and the Security Content Automation Protocol
OpenSCAP is a sophisticated suite of software utilities that leverages the Security Content Automation Protocol (SCAP). It operates on the principle of automating technical control compliance and vulnerability management. This functionality serves a variety of general-purpose operating systems including, but not limited to, Red Hat Enterprise Linux, SUSE Linux Enterprise Server, and others.
Diving Deeper into the SCAP Security Guide
A central component of OpenSCAP is the SCAP Security Guide. This repository is a collection of SCAP content files, including the SCAP Security Guide package, providing detailed security policies for multiple systems. Each guide in the SCAP Security Guide package defines security checklists and standard system security profiles for specific operating systems.
Compatibility with Red Hat Enterprise Linux
Red Hat Enterprise Linux and OpenSCAP are definitely compatible. With the SCAP Security Guide extensively compatible with Red Hat Enterprise Linux, users can fetch remote resources or use the default content file templates.
The SCAP Security Guide package ensures seamless integration with Red Hat Enterprise Linux 8 and other RPM-based operating systems, bolstering system security. However, I would imagine the compatibility with Red Hat Linux may be waning as of late.
Integration with SUSE Linux Enterprise Server
The SCAP Security Guide offers extensive support for SUSE Linux Enterprise Server. As a testament to OpenSCAP’s versatility, it provides detailed SCAP file options, enabling SUSE Linux Enterprise Server to maintain high system security. Moreover, the SUSE Security Team often utilizes the SCAP Security Guide package to promote optimal security practices.
Customizing OpenSCAP with Your Own Content Files
The OpenSCAP suite allows for the creation of its own custom content files. Users can tweak the XML SCAP SSG content found in usr share XML SCAP to meet specific security requirements. This feature makes OpenSCAP a versatile tool for maintaining system security in both traditional and Salt client systems.
OpenSCAP Compliance with the Australian Cyber Security Centre
Reputable institutions like the Australian Cyber Security Centre have recognized OpenSCAP’s flexibility and robustness. The center’s endorsement provides assurance that OpenSCAP can be utilized to enforce a comprehensive system security profile for various general-purpose operating systems.
The Process of an OpenSCAP Audit Scan
OpenSCAP allows users to perform audit scans using the OpenSCAP scanner. These scans can fetch and evaluate remote resources against the SCAP Security Guide, generating XML SCAP SSG content. The output can then be used to reinforce system security and protection profile adherence.
Interpreting OpenSCAP Outputs
OpenSCAP’s output includes the SCAP content file and remediation Bash scripts. Users can identify and rectify security flaws using these Bash shell scripts. The scans produce detailed reports, giving users a complete picture of their system security standing.
OpenSCAP and Health Insurance Portability Accountability Act Compliance
OpenSCAP facilitates compliance with standards such as the Health Insurance Portability and Accountability Act. Businesses operating in sensitive sectors can ensure system security and maintain regulatory compliance by leveraging the SCAP Security Guide packages.
Installing the OpenSCAP Scanner
Installing the OpenSCAP scanner is straightforward and varies slightly depending on the operating system. Below, we explore the steps for Red Hat Enterprise Linux, SUSE Linux Enterprise Server, and a general guide for DEB and RPM-based operating systems.
Red Hat Enterprise Linux
On a Red Hat Enterprise Linux system, you can install the OpenSCAP scanner by using the yum package manager. You also need to install the SCAP Security Guide which provides the security policies for the scan:
sudo yum install openscap-scanner scap-security-guideSUSE Linux Enterprise Server
To install the OpenSCAP scanner on SUSE Linux Enterprise Server, you will use the zypper package manager:
sudo zypper install openscap-utils suse-openscap-contentThis command installs the scanner and the SCAP content files for SUSE Linux Enterprise.
DEB and RPM-Based Operating Systems
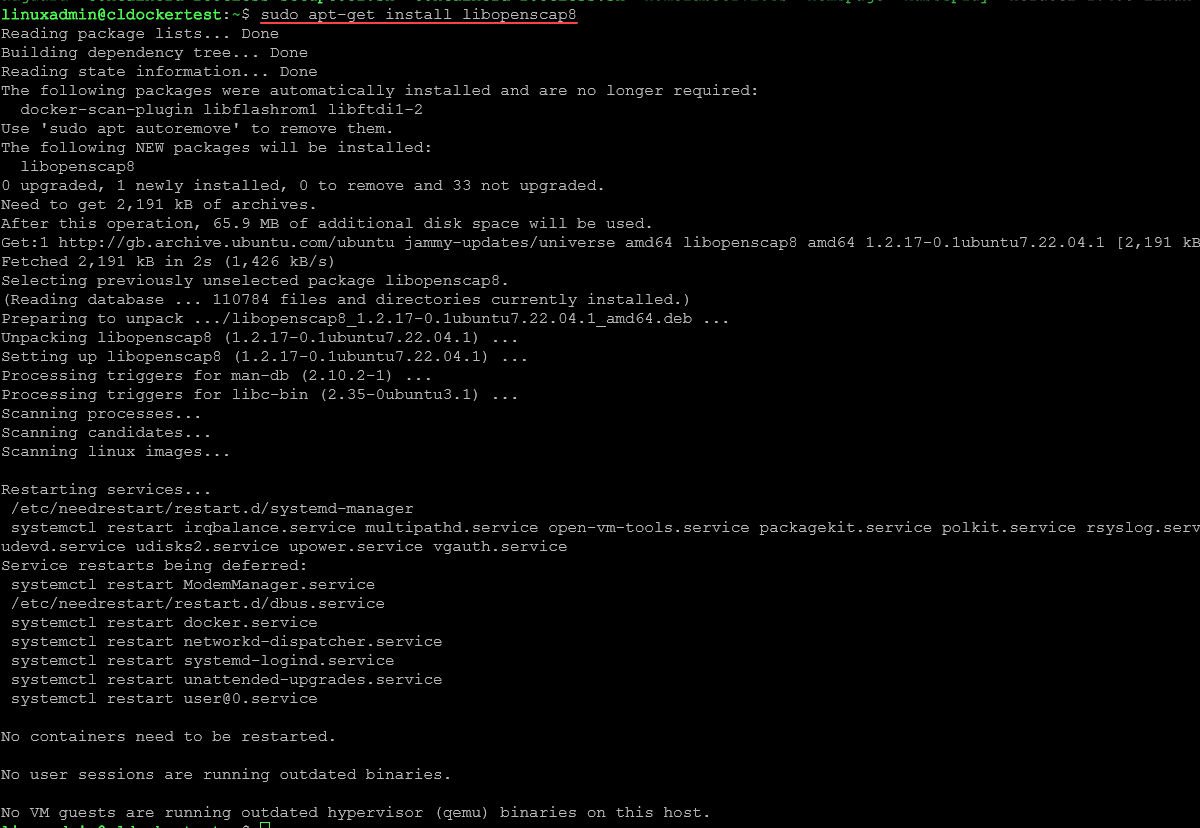
For other operating systems that support either DEB or RPM packages, you can use the appropriate package manager (apt for DEB systems like Ubuntu, and yum or dnf for RPM systems like Fedora). Here is the command for Ubuntu:
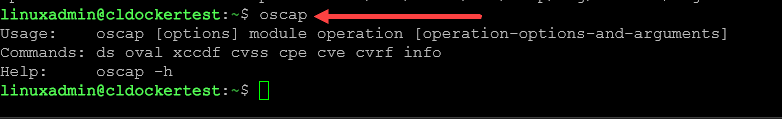
sudo apt-get install libopenscap8You can verify that OSCAP is installed by typing oscap.
For Fedora, you can use:
sudo dnf install openscap-scanner scap-security-guideAfter successful installation, the OpenSCAP scanner can be utilized to evaluate system security using various commands as outlined in the previous section. Ensuring proper installation is the first step in the journey to maintaining system security and protection profile adherence with the help of OpenSCAP.
Mastering OpenSCAP Scanner Commands
One of the distinguishing features of OpenSCAP is its ability to allow users to interact with the suite through a variety of commands. Understanding these commands enables better utilization of the tool, contributing to the overall system security.
Basic Scan with oscap
To initiate a basic evaluation of your system, you’ll use the oscap command, followed by the source data stream imported, the profile, and the path to the source data stream.
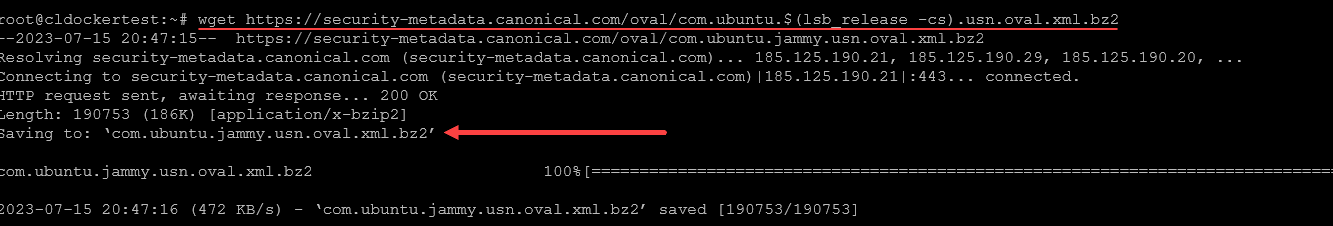
For Ubuntu 22.04, you can use the following XML system command to pull the file for your Ubuntu release:
wget https://security-metadata.canonical.com/oval/com.ubuntu.$(lsb_release -cs).usn.oval.xml.bz2Next, we unzip the resource file:
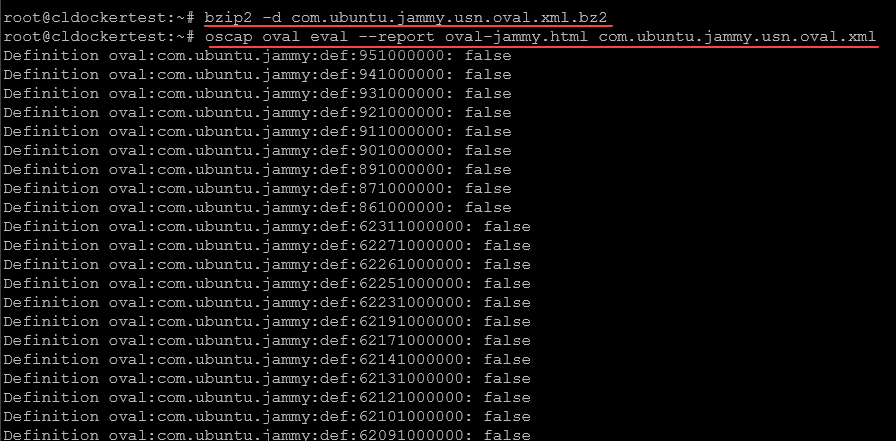
bzip2 -d com.ubuntu.jammy.usn.oval.xml.bz2Next, we run the scan and create the HTML output file for the scan results:
oscap oval eval --report oval-jammy.html com.ubuntu.jammy.usn.oval.xmlAnother example of generating a report for a Redhat system:
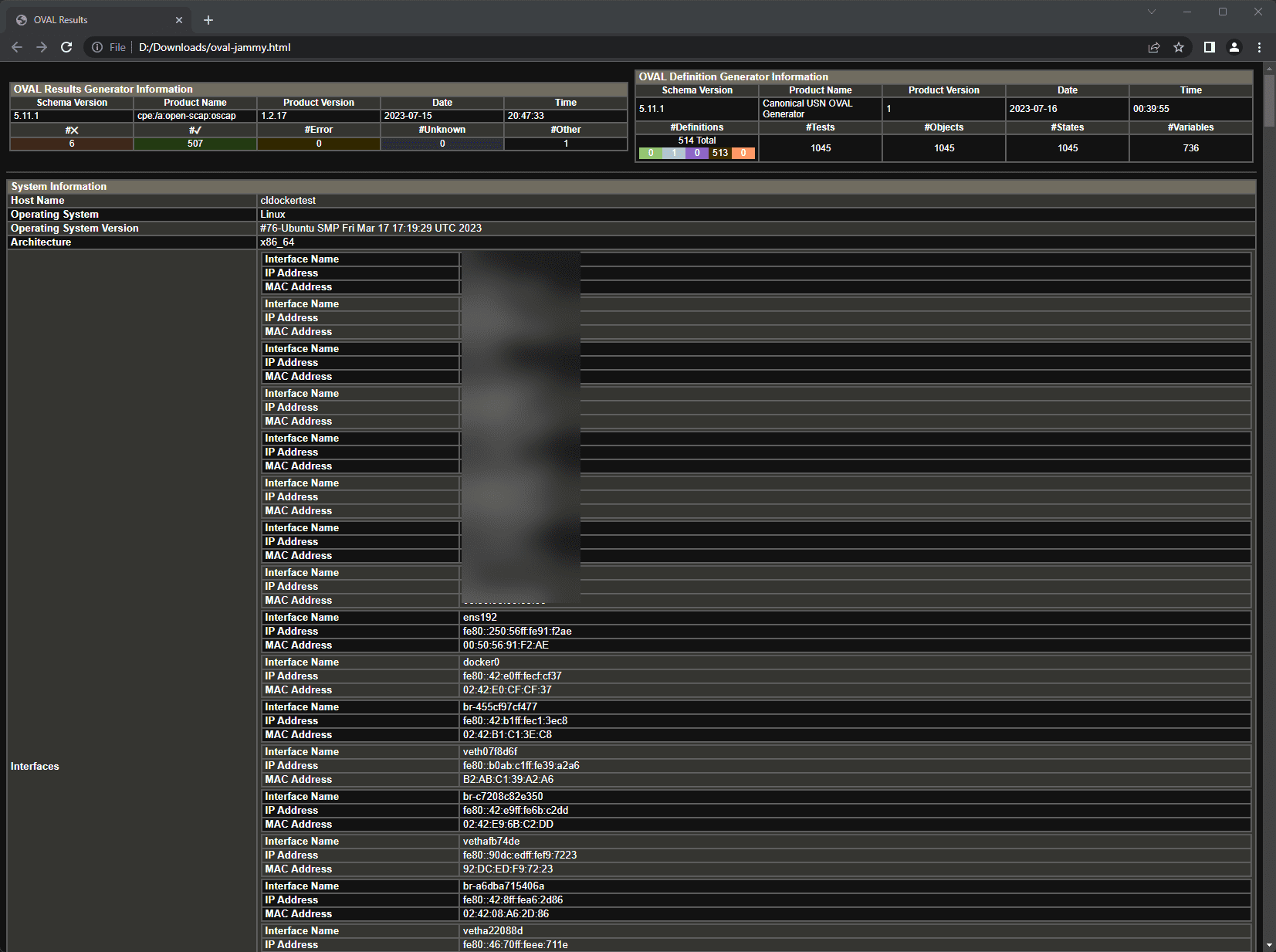
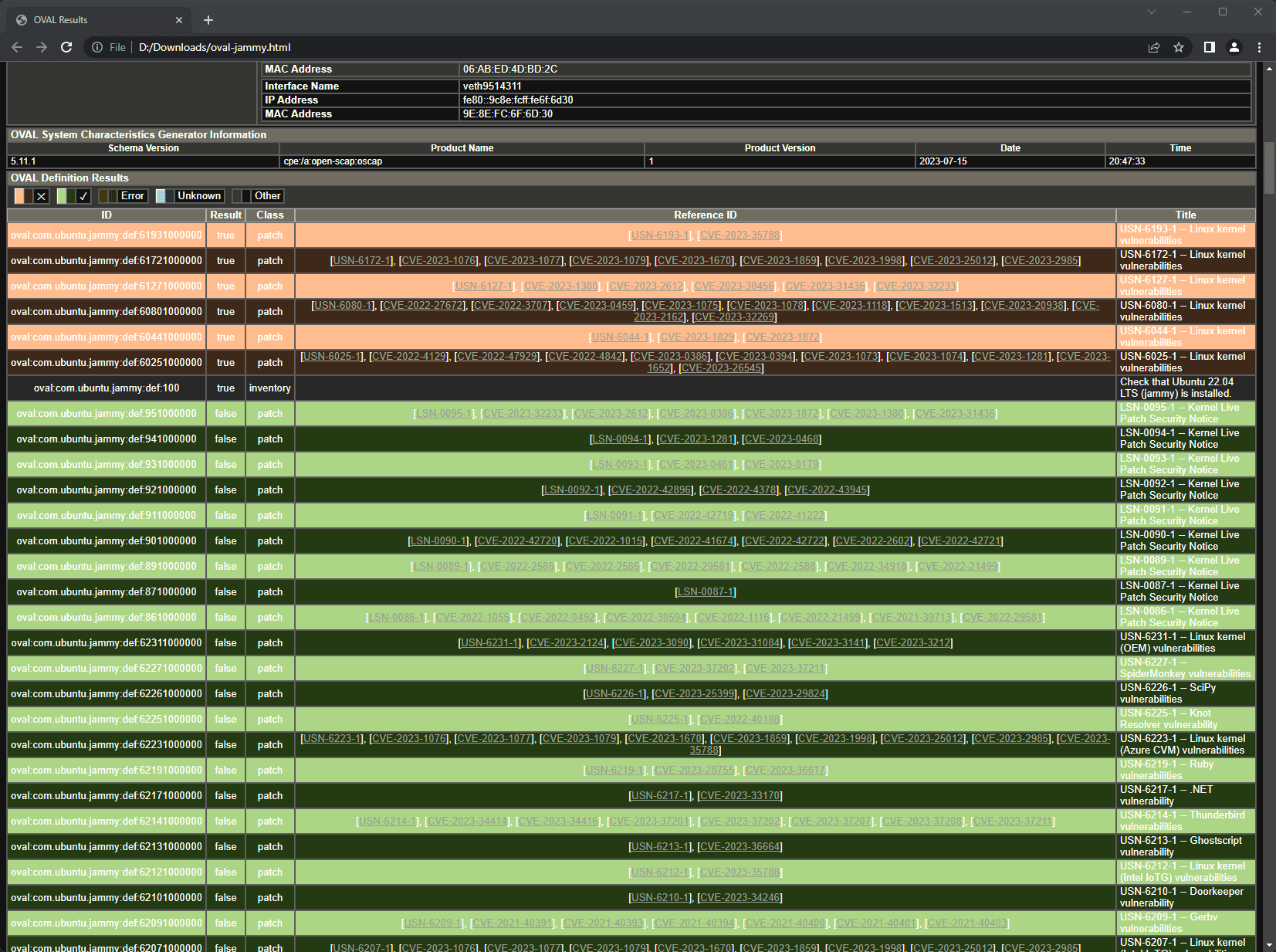
oscap xccdf eval --profile xccdf_org.ssgproject.content_profile_standard --report report.html /usr/share/xml/scap/ssg/content/ssg-rhel7-ds.xmlThis command generates a user-friendly, easy-to-read HTML page system security report detailing your system’s security. Below, I have downloaded the resulting HTML file and viewing it in a browser. It will give you detailed system information about the target of the scan.
Also, you will see discovered vulnerabilities on the system.
Customizing Scans
OpenSCAP allows you to customize your scans by defining test rules in your own content files. This feature gives users greater flexibility when securing their systems:
oscap xccdf eval --profile my_profile --cpe my_cpe_dictionary.xml --check-engine-results my_test_result.xml my_custom_content_file.xmlThis command launches an evaluation with your customized test rules, offering a more tailored approach to system security.
By learning and applying these commands, users can use the OpenSCAP scanner more effectively to enhance their cybersecurity measures, performing audit scans and improving their system security.
Wrapping up
OpenSCAP is a really good tool for organizations serious about cybersecurity. It has constant innovations and updates that line up with NIST’s SCAP release cycle, and it makes sure that organizations stay one step ahead in the changing and worsening cybersecurity threats. It is an effective way to have vulnerability management.