Microsoft 365 security and backup with Hornetsecurity
To the topic of Microsoft 365 security, many businesses are leveraging the cloud’s power for the modern hybrid workforce. One of the most popular offerings for a cloud SaaS solution is Microsoft 365. Microsoft 365 provides the productivity, communication, collaboration, and other tools remote teams need to communicate and collaborate efficiently.
However, as businesses are moving large quantities of business-critical services and data to the cloud, they must remain vigilant about their organization’s security and data protection needs. 365 Total Protection from Hornetsecurity is a solution that helps businesses achieve their security and data protection goals. Let’s see how.
What is Microsoft 365?
First, what is Microsoft 365? The Microsoft 365 solution includes many popular solutions used by organizations today, including Microsoft Teams and the traditional Office 365 apps that businesses have been using for decades. It enables these through a cloud Software-as-a-Service delivery model.
Microsoft 365 also includes other great services, such as Defender for Office 365, SharePoint Online, Microsoft Defender, Exchange Online, OneDrive for Business, and other core productivity and collaboration services.
It is a Software-as-a-Service (SaaS) offering that allows organizations to pay for the services monthly per user.
Microsoft 365 security and data loss prevention
Attackers realize that organizations are moving more of their infrastructure to cloud-native and Software-as-a-Service (SaaS) environments. More commonly, attackers are looking to compromise SaaS and public cloud environments. Organizations must account for this with their data protection, loss prevention, and threat protection policies.
The right tooling for investigation and response and automated investigation and response is critical to advanced threat protection with Microsoft 365 and has a multitude of capabilities to protect the organization from data dangers like data leaks, phishing attacks, ransomware, data loss, and others.
While Microsoft offers many built-in tools as part of Microsoft 365, such as the compliance center, Microsoft Defender, and security teams watching the overall Microsoft 365 security environment, organizations still need to take a proactive approach to their organization’s security and data protection.
Microsoft Office 365 provides different challenges for businesses to protect their data. One is the lack of centralized tooling. While many robust tools are part of Microsoft 365, administrators must access these in different dashboards and links, making it difficult to have one cohesive solution for managing and securing the environment.
What is 365 Total Protection from Hornetsecurity?
The 365 Total Protection solution from Hornetsecurity is an advanced security and data protection solution housed in the cloud that protects your organization from malicious emails, SPAM, ransomware, and other types of threats.
It contains many features, including disclaimers, email archiving, eDiscovery, forensic analyses, ATP sandboxing, real-time threat reporting, and malware alerting.
In addition to the security features and capabilities of the product, it also provides data backup for your Microsoft 365 environment. While there are retention periods for Microsoft 365 emails as part of Exchange Online, this built-in feature is not a true backup mechanism where you can protect your data outside of the production system and from threats like cloud-based ransomware.
Let’s consider several of the features of the 365 Total Protection solution and see how these can be used to protect your Microsoft 365/Office 365 environment.
Outlook add-in
The 365 Total Protection solution also provides an Outlook add-in that allows users to quickly classify information and manage allow and deny lists right from within their Outlook client instead of the dashboard.
Overview dashboard
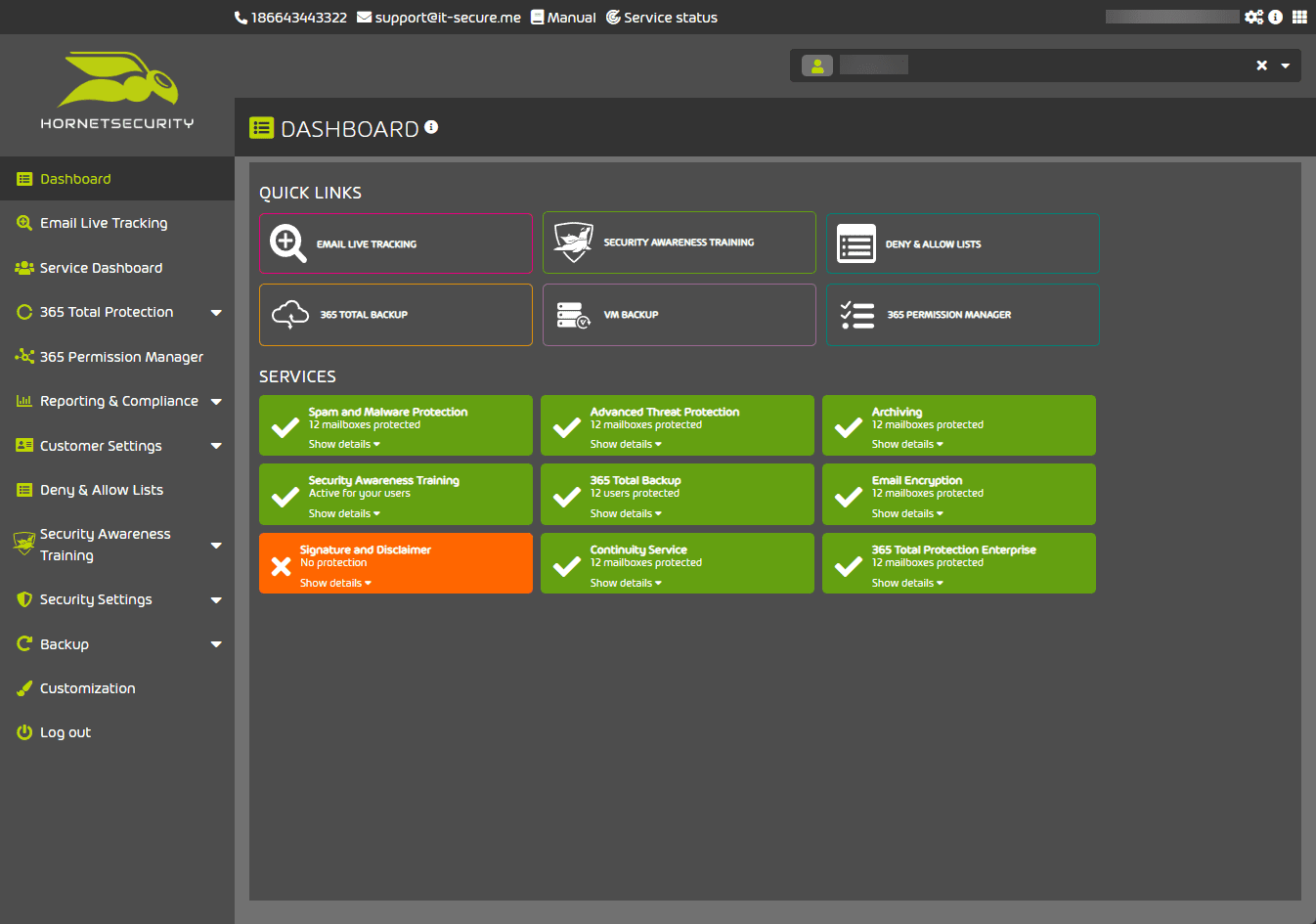
When you first login to the Hornetsecurity 365 Total Protection solution, you will see the overview dashboard.
The Dashboard gives you a landing page to view your organization’s operations and allows admins to see the protection enabled or disabled at a glance quickly. Depending on the available services included with your solution, you will see the various tiles listed under the Quick links.
Modules
From here, you can quickly navigate the various modules in the solution. Modules include:
Email Live Tracking
Security Awareness Training
Deny & Allow Lists
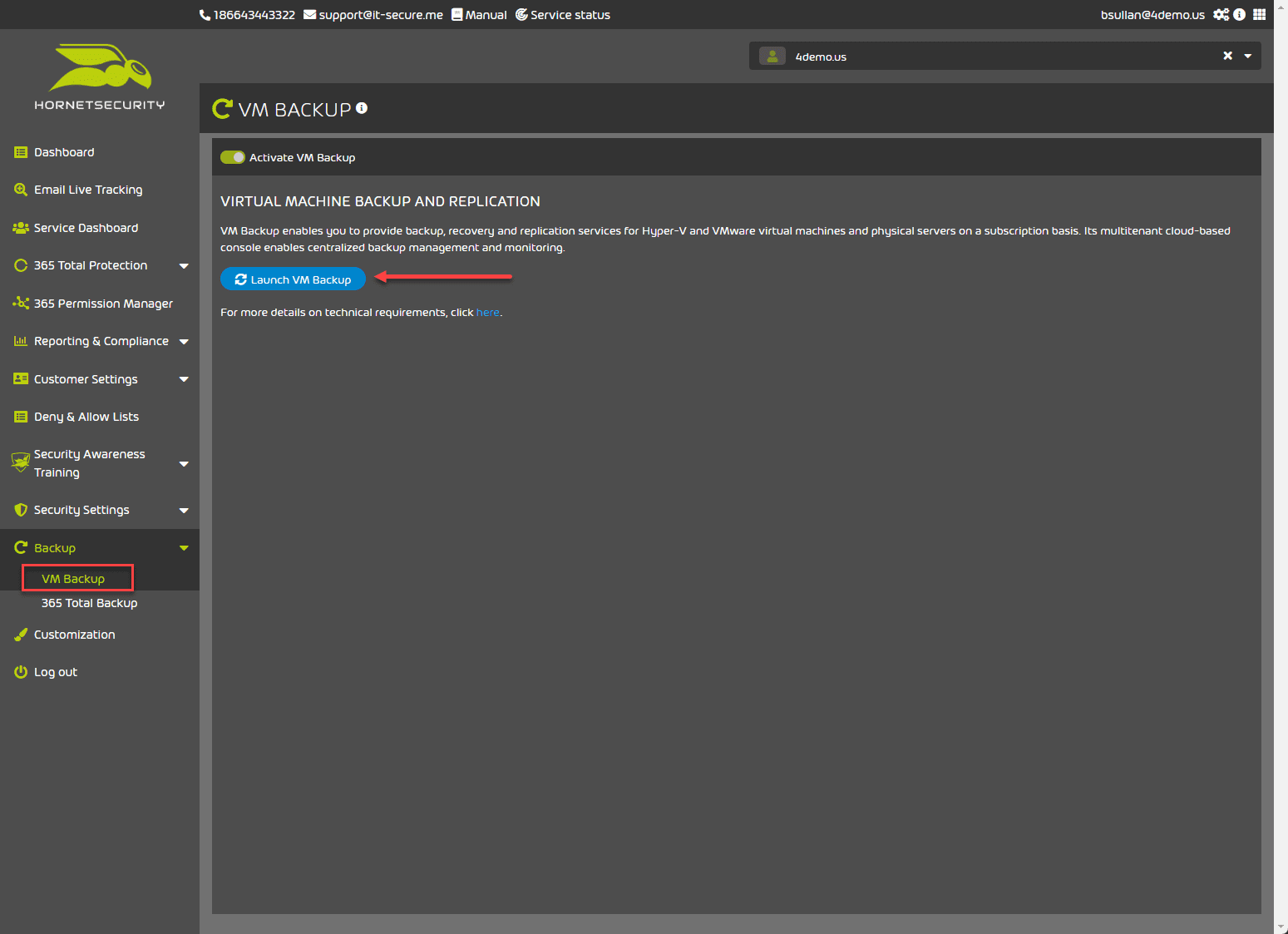
365 Total Backup
VM Backup
User Modules
Users will see:
Email Live Tracking
Deny & Allow Lists
Email Live Tracking
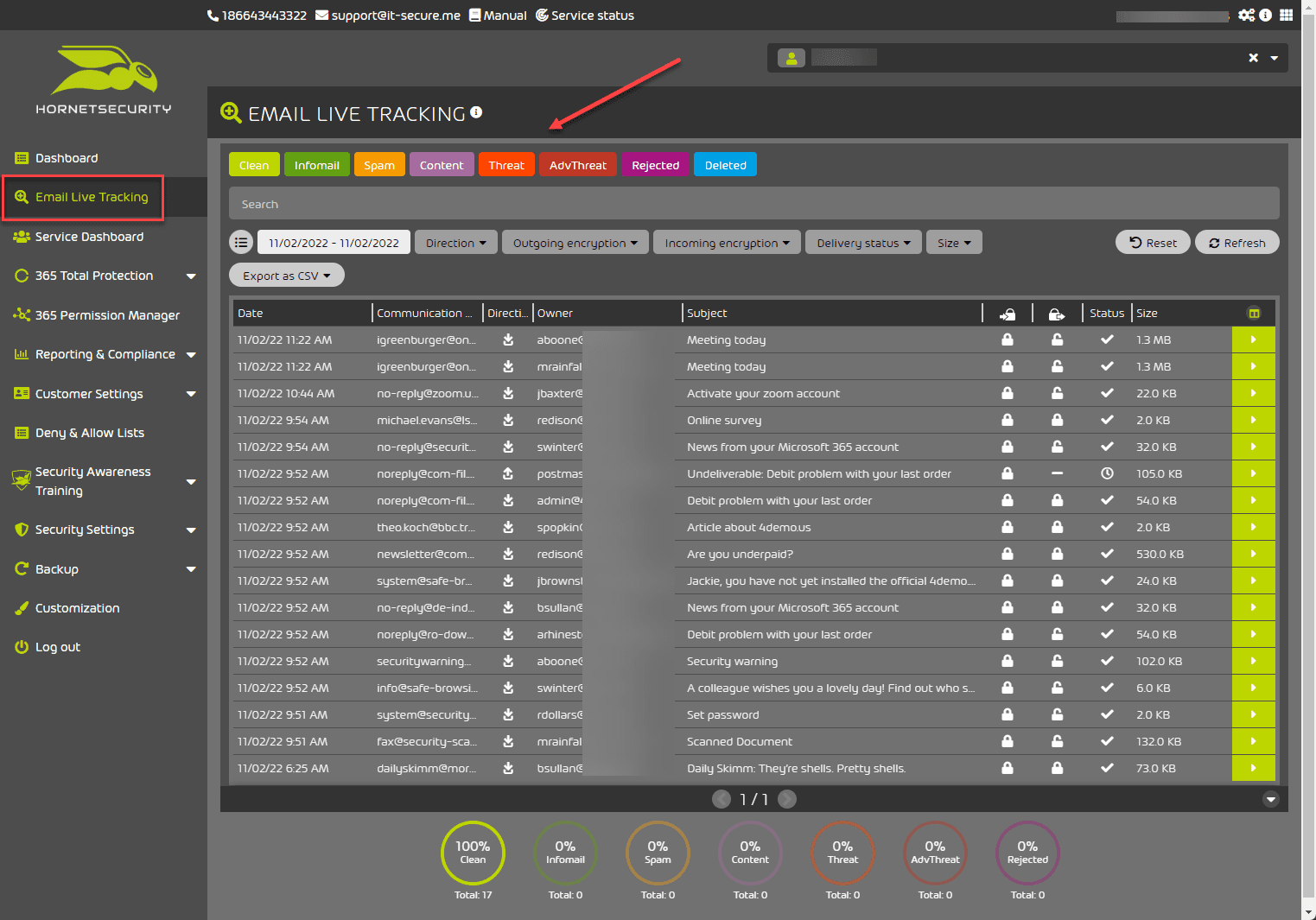
Below is a look at the Email Live Tracking dashboard. As you can see it provides an easy way for administrators to see the Live state of email traffic. It allows easily selecting or deselecting the various types of threats and viewing the resulting emails.
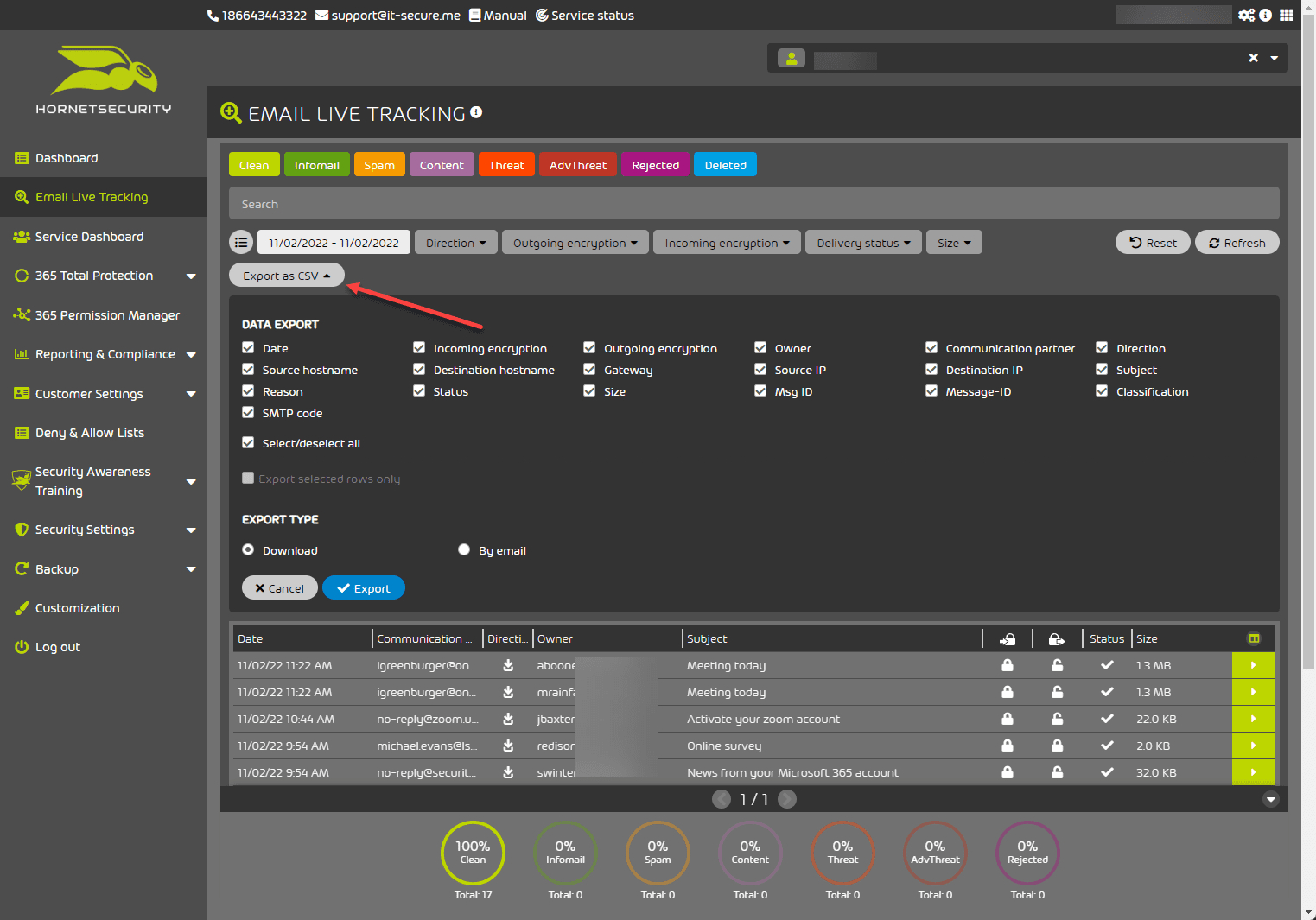
If you click on the Export to CSV option, you can export your Email Live Tracking results to a CSV file.
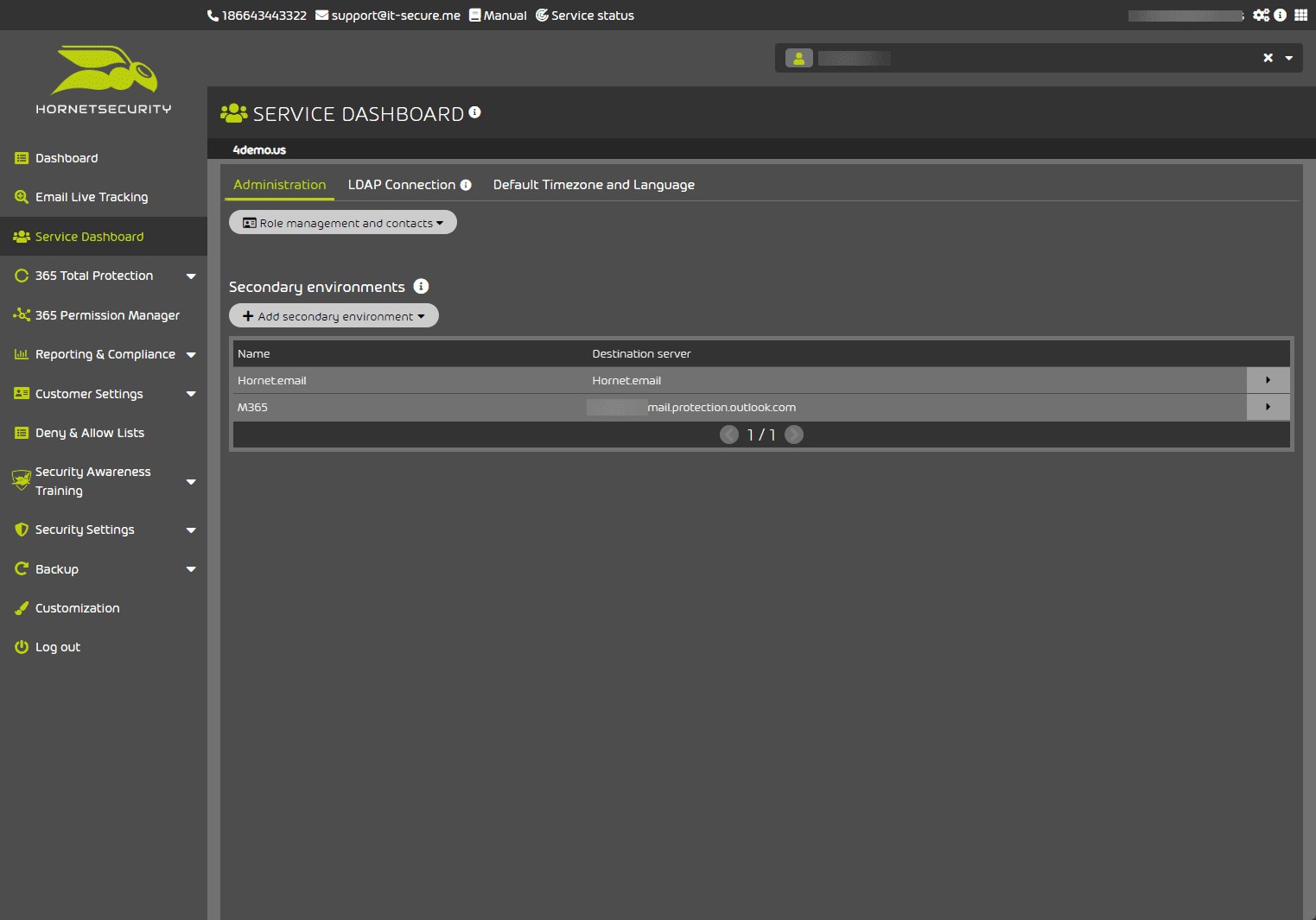
Service Dashboard
On the service dashboard, you can configure the administrative contacts, LDAP connection, and Timezone information as well as Secondary environments.
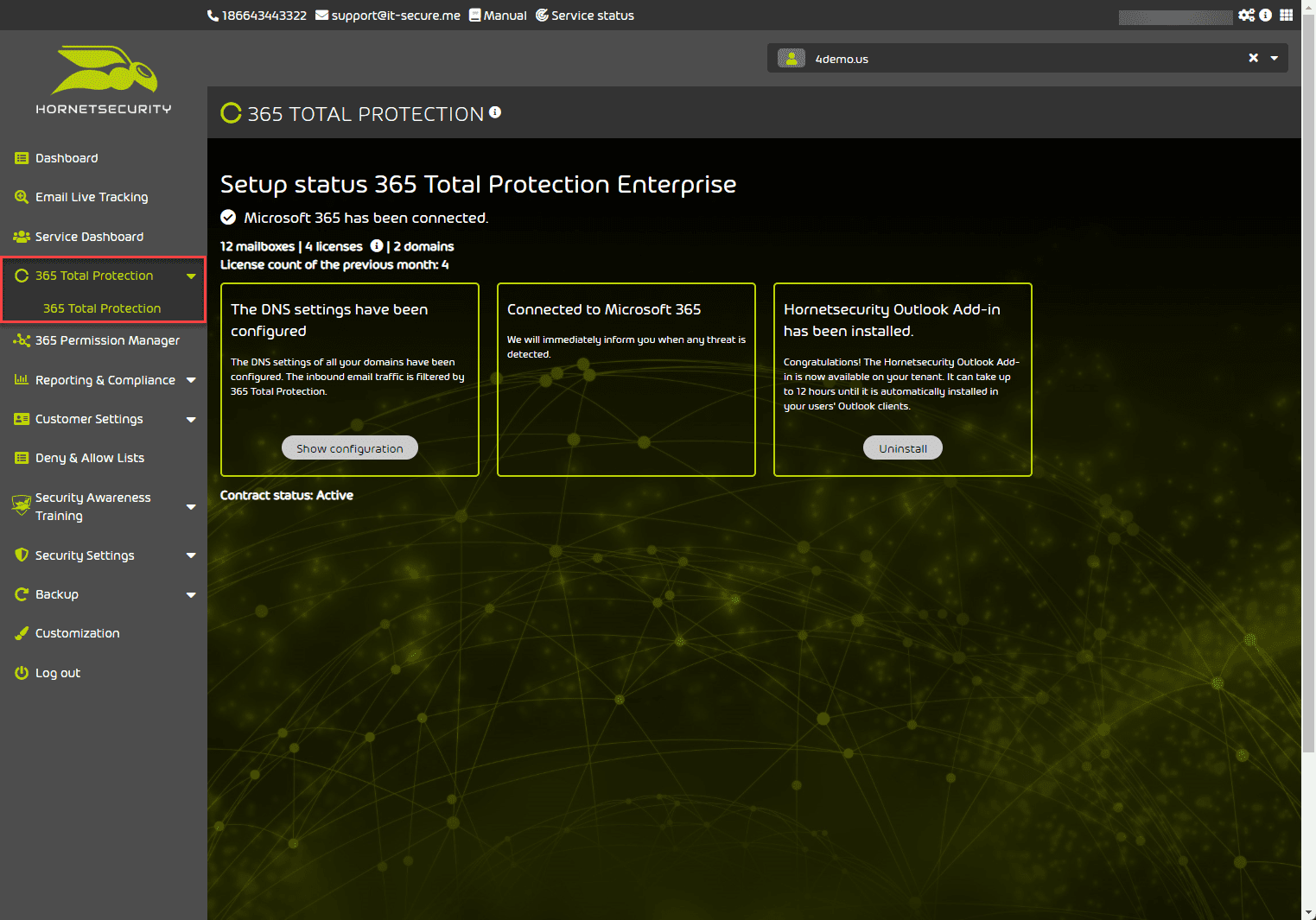
365 Total Protection configuration
Under the 365 Total Protection menu option, you can view the configuration and any steps that need to be completed to successfully implement the 365 Total Protection configuration.
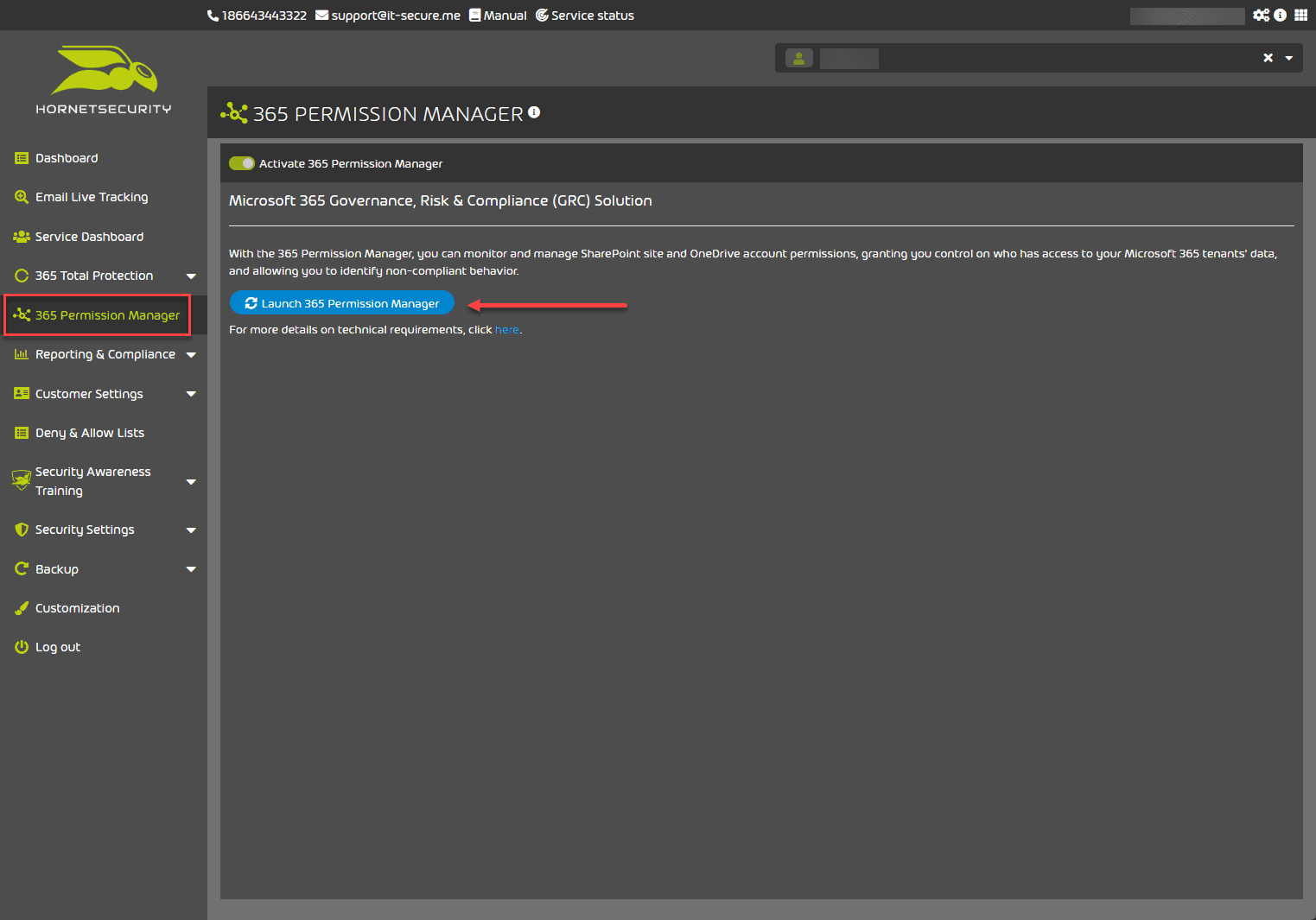
365 Permission Manager
On the permissions manager page, you can monitor and manage SharePoint site and OneDrive account permissions, granting you control over who has access to your Microsoft 365 tenants’ data, and allowing you to identify non-compliant behavior.
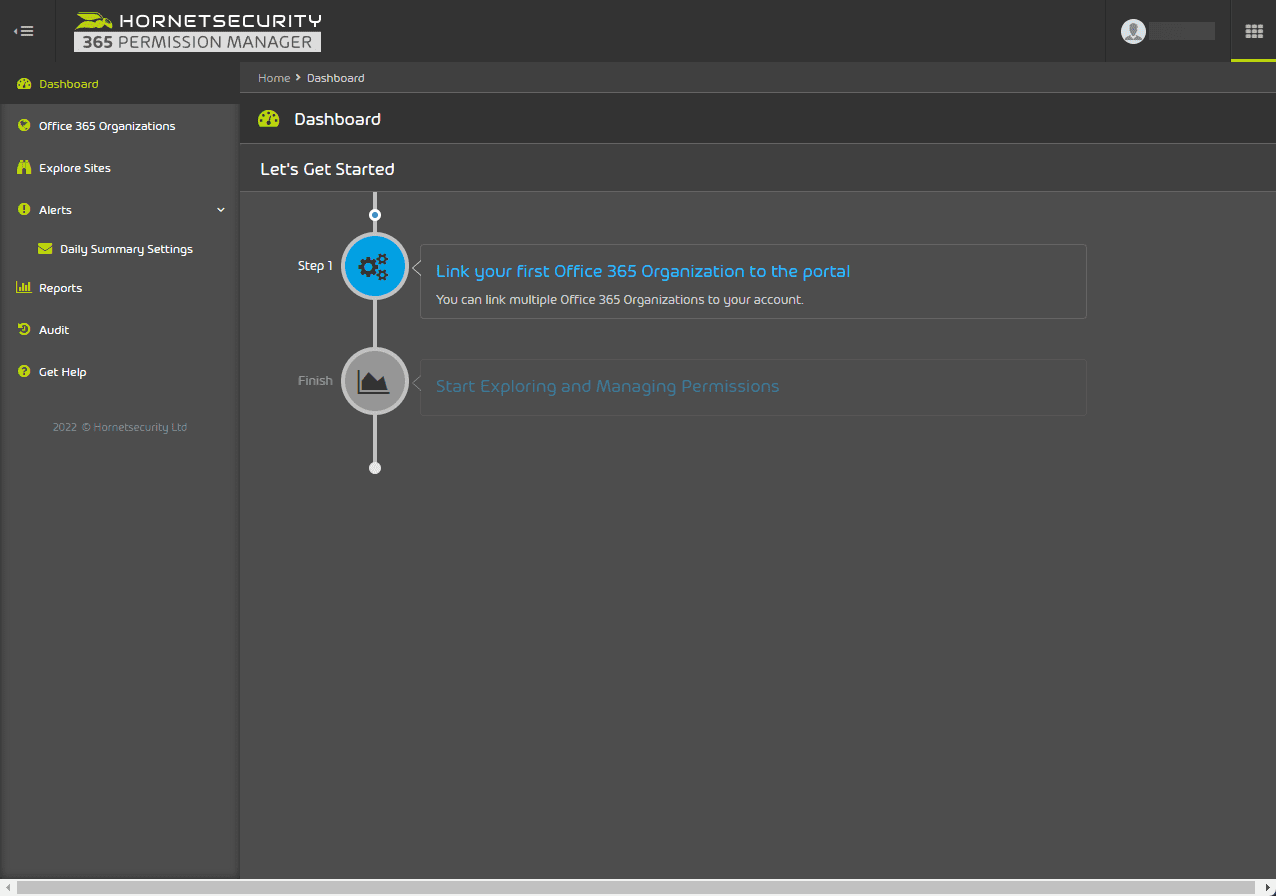
Launching the Permissions Manager allows linking your Office 365 organization to the permissions manager and explore and manage permissions in the Microsoft 365 environment.
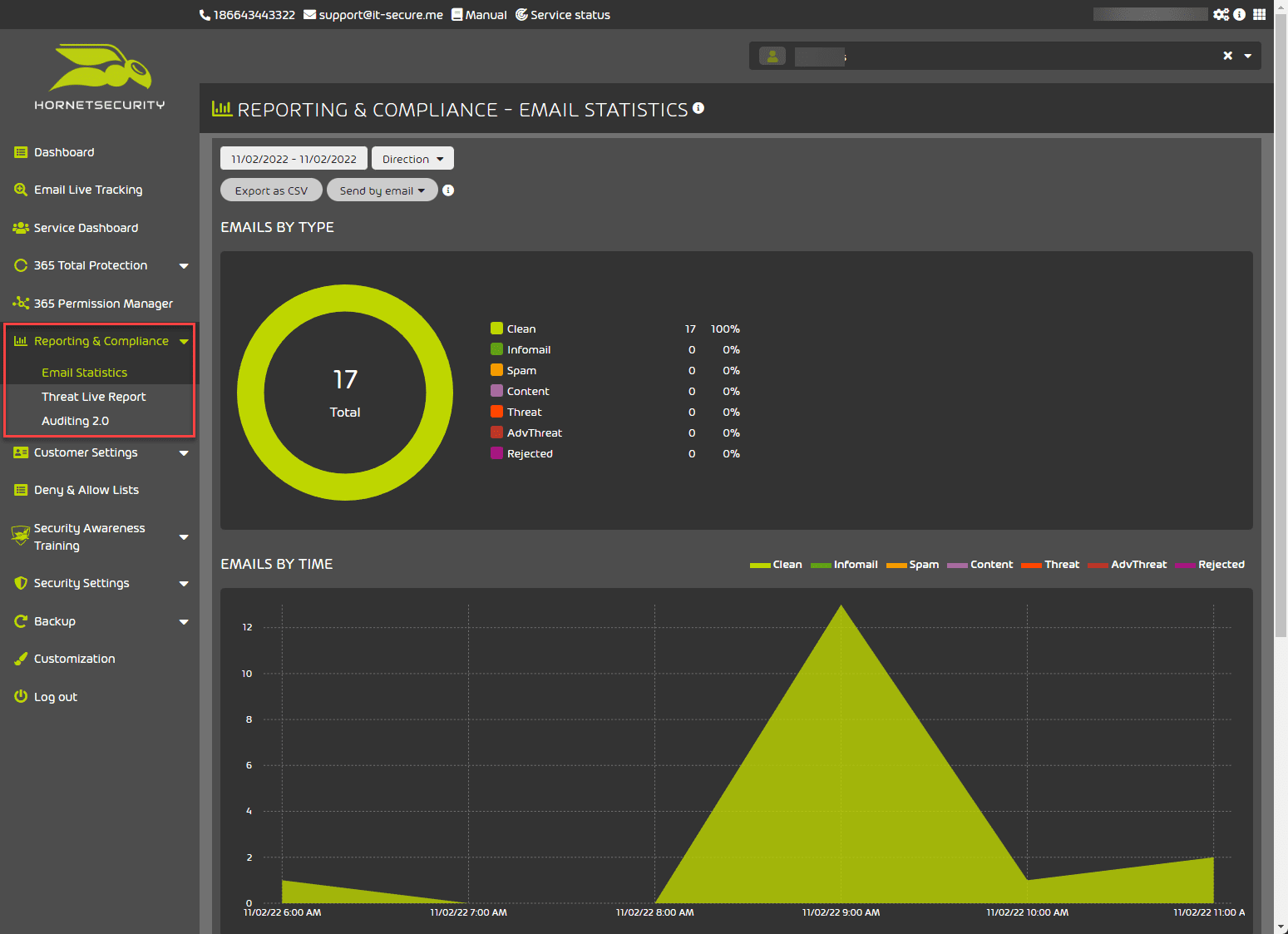
Reporting and Compliance
Below, you can see the reporting and compliance – email statistics page where you can see the number of emails classified by type, including clean, infomail, spam, content, threat, advthreat, or rejected.
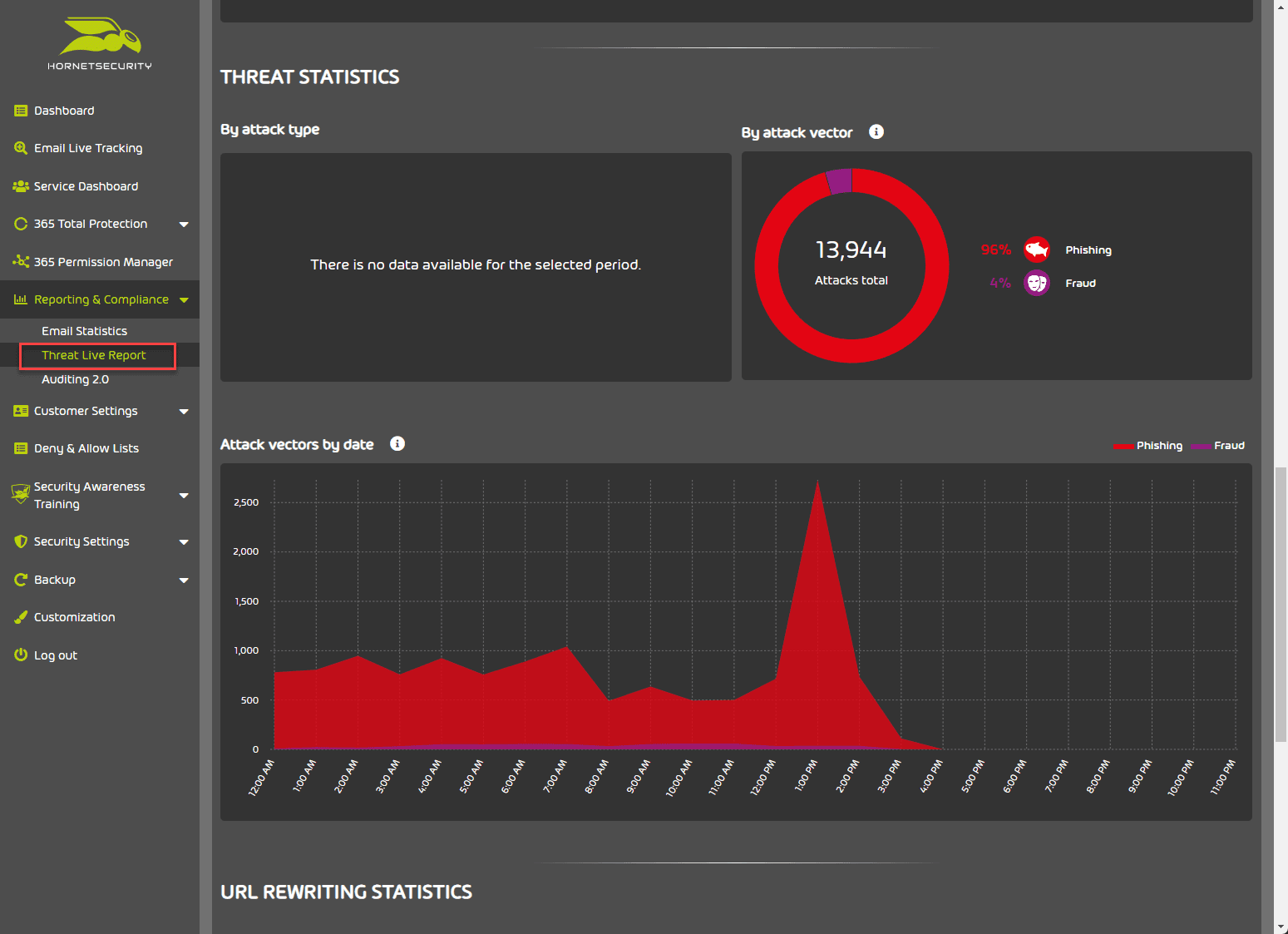
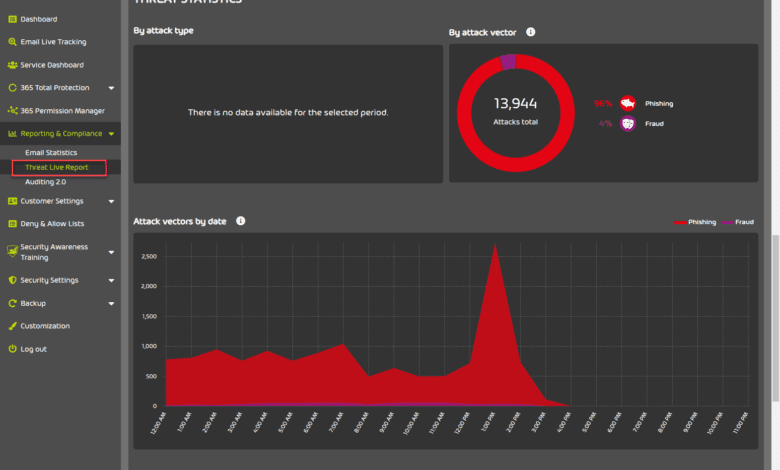
Threat Live Report
Under the Threat Live Report, you can see the live threats in your organization and the type and attack vector being used.
Below is a look at the Threat statistics dashboard.
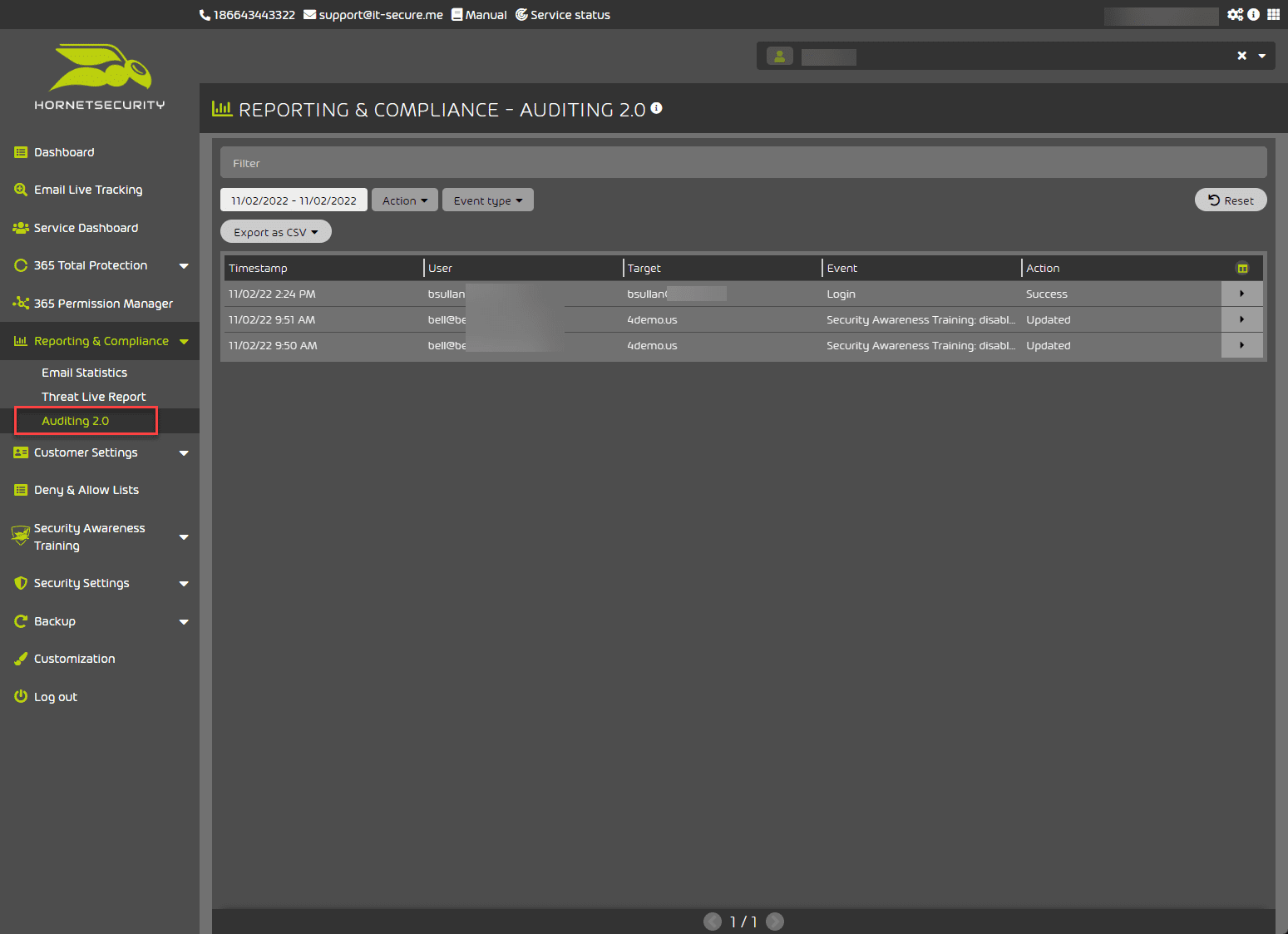
Below is the Reporting & Compliance – Auditing 2.0 dashboard. Here you can see auditing and compliance activities.
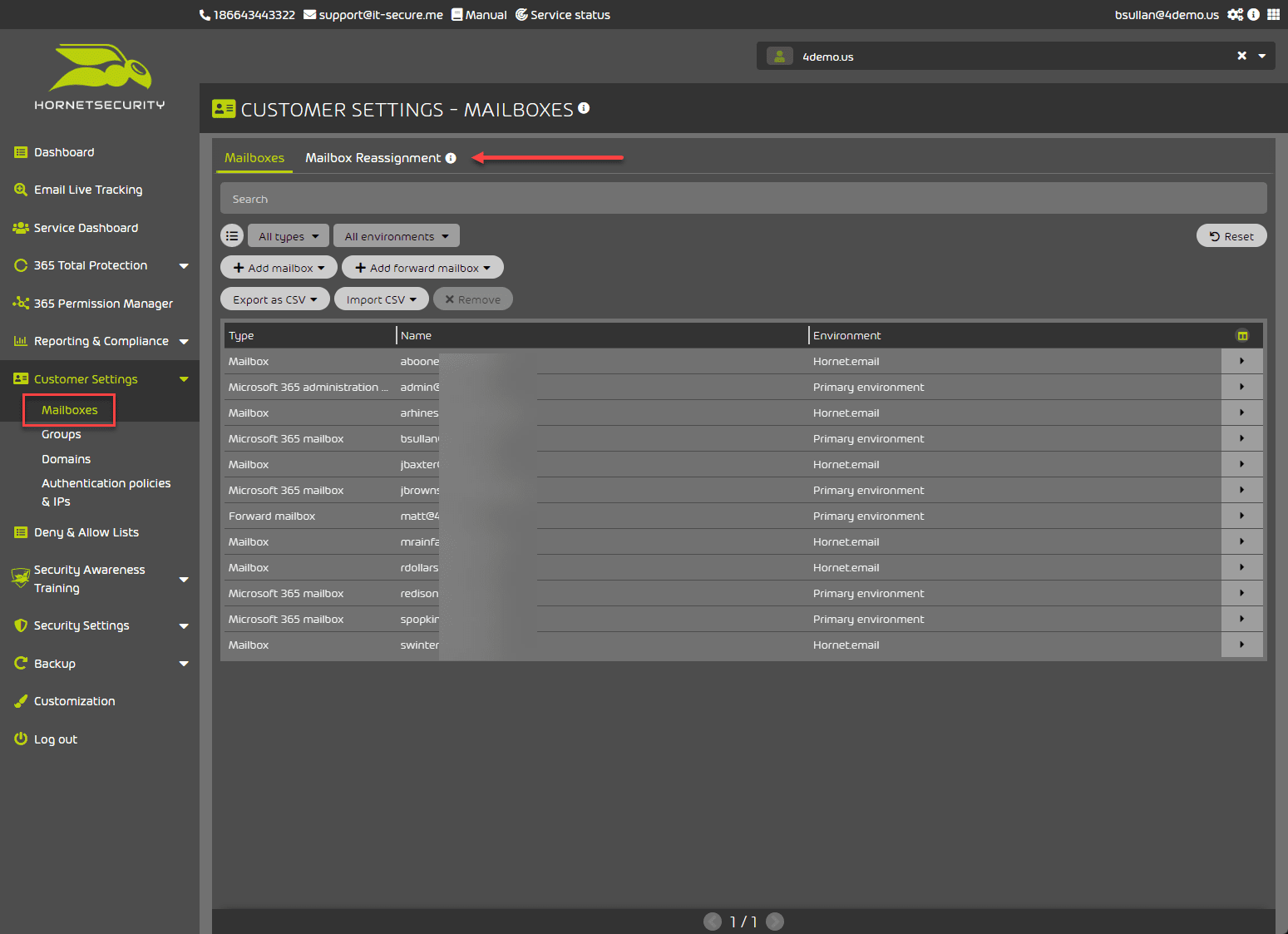
Customer settings – Mailboxes
On the customer settings mailboxes menu, 365 Total Protection allows you to easily grant access to the email archive of former employees or deleted users, making the offboarding process much more seamless.
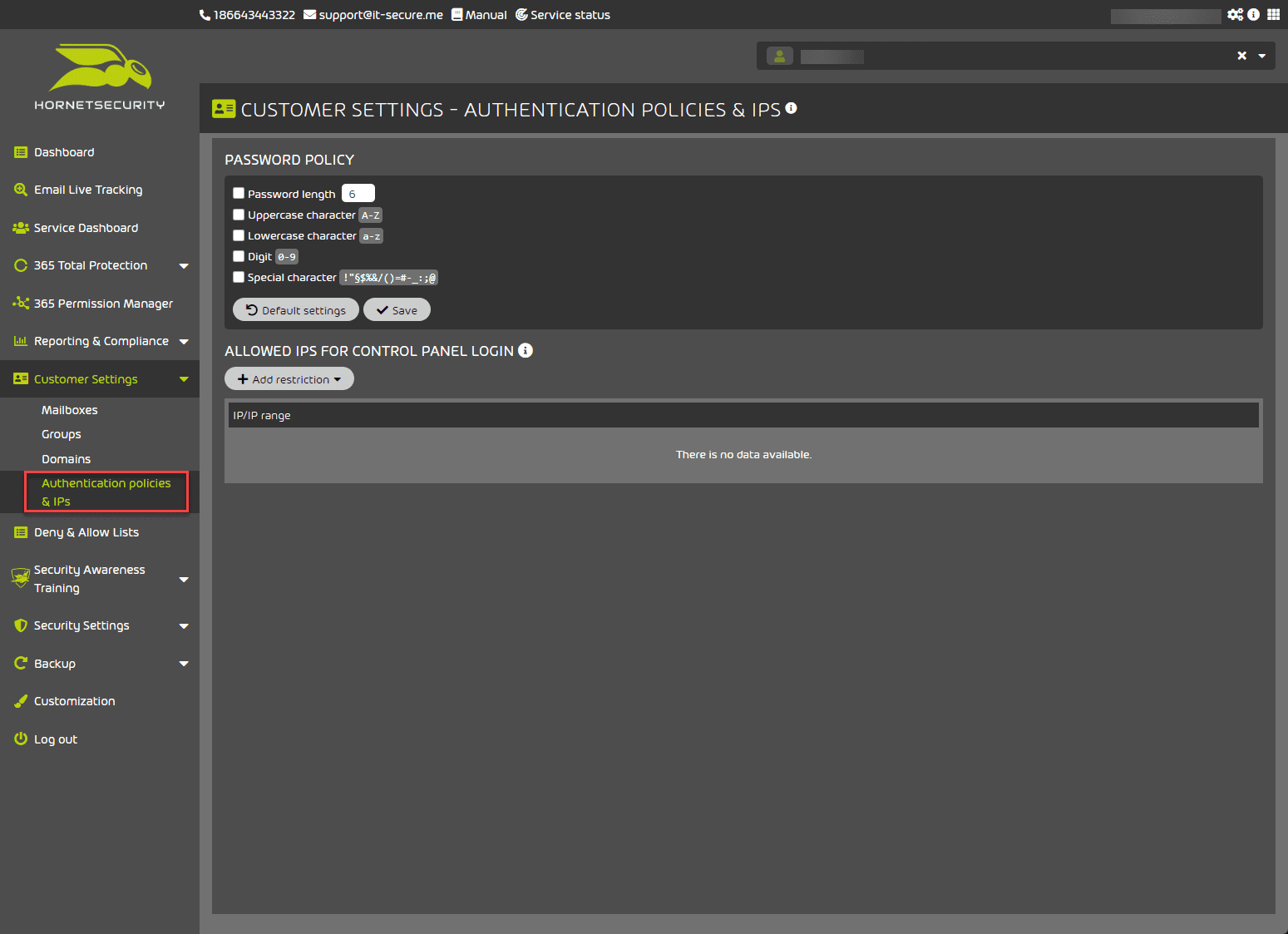
Also, under the customer settings screen, you can control mailboxes, and groups, add domains and authentication policies, and allow IPs for the Control Panel.
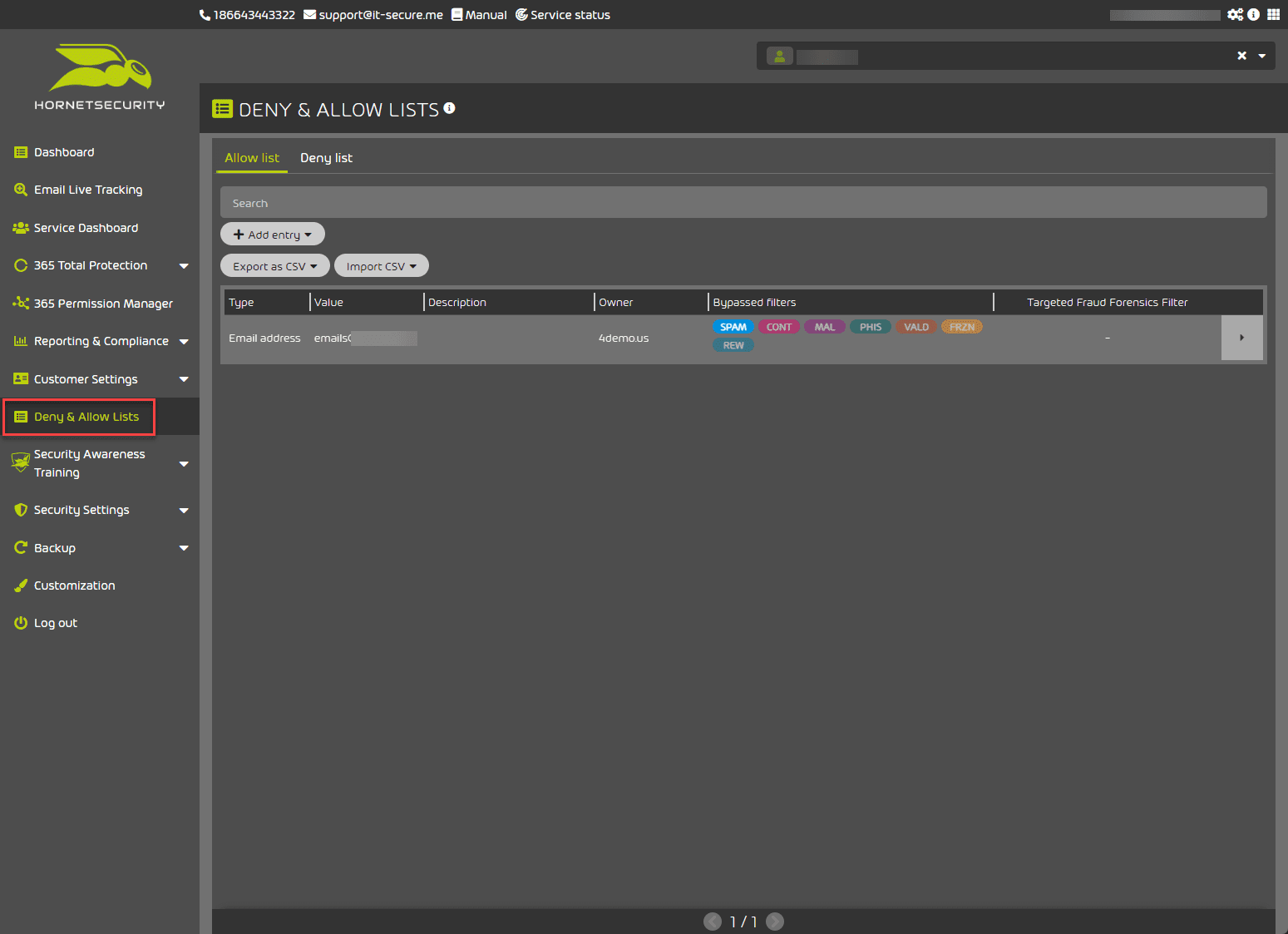
Deny & Allow Lists
On the Deny and Allow Lists section of the solution, you can enter emails that are allowed and not classified as SPAM or other filtered types, and you can also add emails to the Deny List. This gives administrators and users granular control over emails they can allow or deny based on their preferences or other needs.
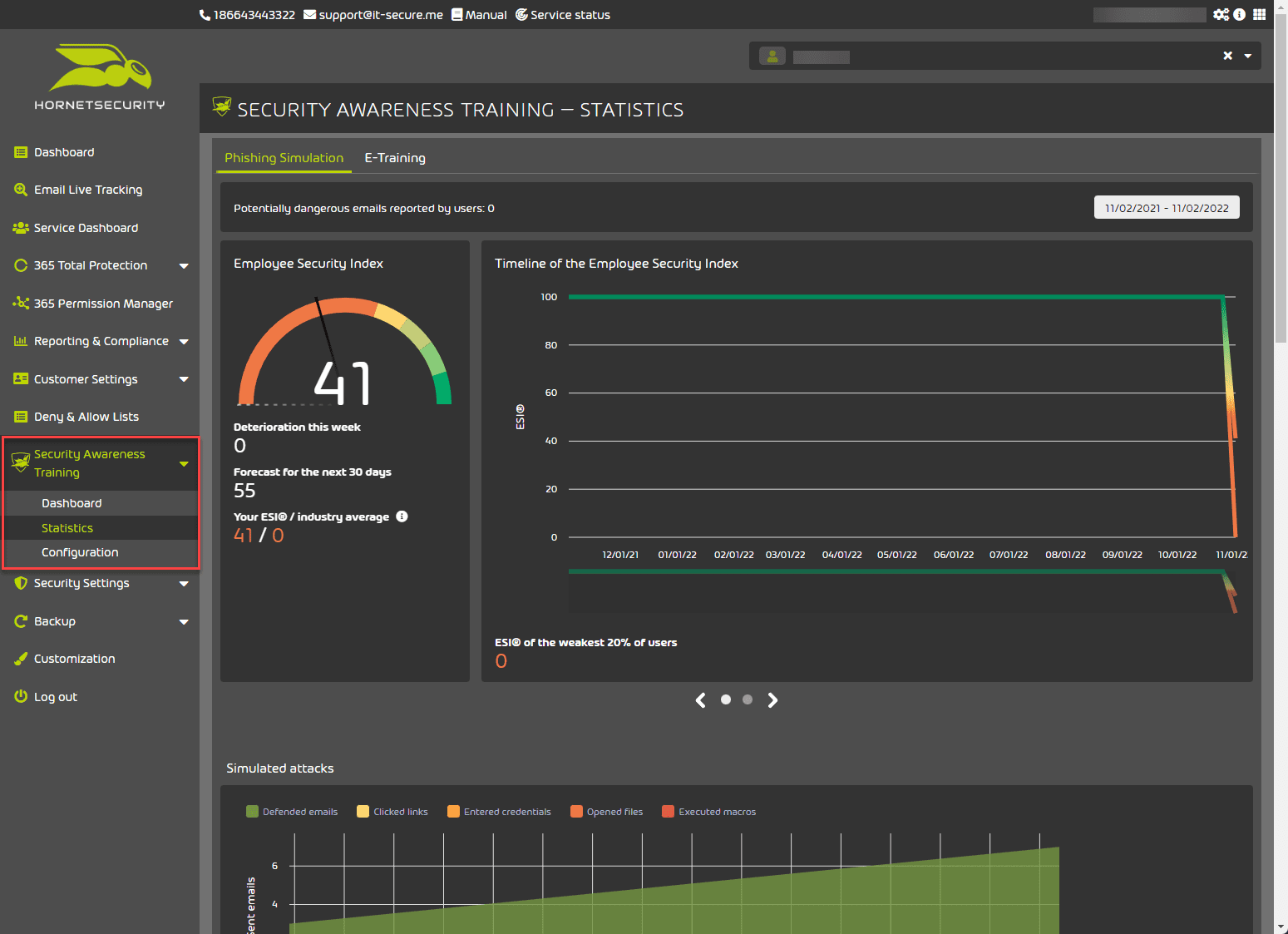
Security Awareness Training
The Security Awareness Training module uses eLearning and simulates phishing attacks to help users understand and learn the risks of these attacks. It helps condition users to reliably recognize and take appropriate actions when they are subject to these types of cyberattacks.
365 Total Security provides a patented measuring mechanism that measures the security behavior of all users and individual groups. it calculates the Employee Security Index (ESI) and Trainings KPI.
The core of the entire solution is known as the Awareness Engine. Based on the results, the Awareness Engine evaluates the user’s security behavior and decides which users will receive additional training or simulated attacks. Administrators can also manually assign these types of training materials to users.
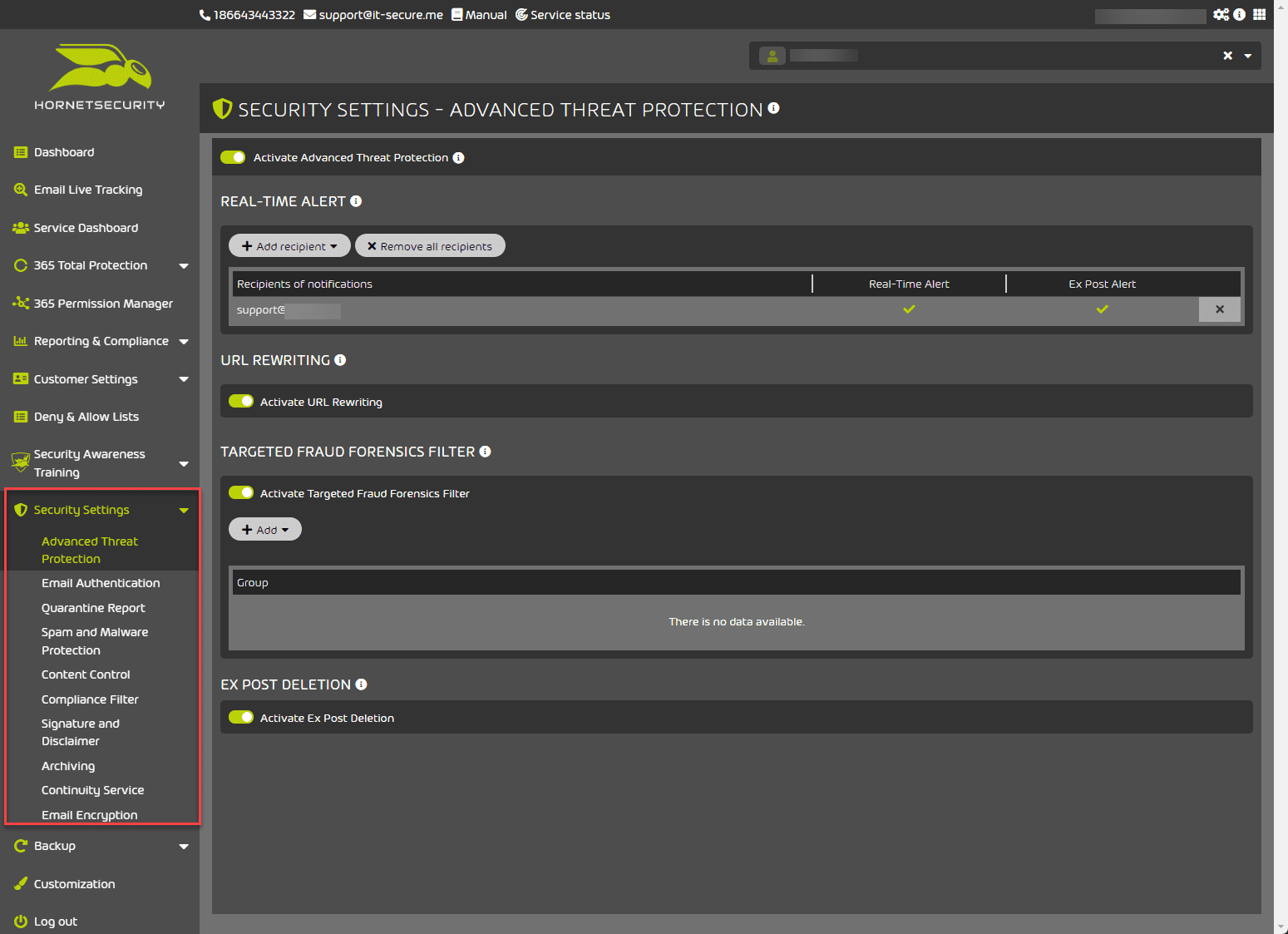
Security Settings
Under the Security Settings, administrators will find a wide range of security protections for Microsoft 365, allowing them to bolster the overall cybersecurity posture of their email environment.
Advanced Threat Protection – The Advanced Threat Protection (ATP) protects companies against attacks that target them individually or other tailored attacks. It provides a forensic analysis engines ensure that attacks are stopped immediately. It helps companies to have detailed information about the attacks.
Email Authentication – The Email Authentication component offers customer-level administrators different methods to authenticate email senders.
Quarantine Report – Quarantine Report Allows customer-level administrators to configure quarantine reports for the users of their domains. The Quarantine report helps to inform users about all emails categorized as Spam and Infomail, as well as emails in quarantine so further action can be taken
Spam and Malware Protection – Spam and Malware Protection blocks SPAM and emails containing viruses and other malware before they enter a mailbox. Furthermore, newsletters and other types of infomail can be detected and rejected.
Content Control – Content Control allows customer-level administrators to manage the handling of attachments of incoming and outgoing emails.
Compliance Filter – With the Compliance Filter, administrators can define their own rules for filtering emails in their organization.
Signature and Disclaimer – Signature and Disclaimer controls the automated and centralized provision of email signatures and disclaimers, helping businesses meet their compliance and other objectives related to email
Archiving – Archiving Allows administrators to archive the incoming and outgoing emails for their domains to align with data retention requirements
Continuity Service – The Continuity Service is an additional email service that guarantees continuous email functionality in the event of an email server failure, providing high availability to the solution
Email Encryption – In the Email Encryption module, administrators define encryption policies. It allows controlling email traffic encryption of their domains and managing their users’ S/MIME certificates
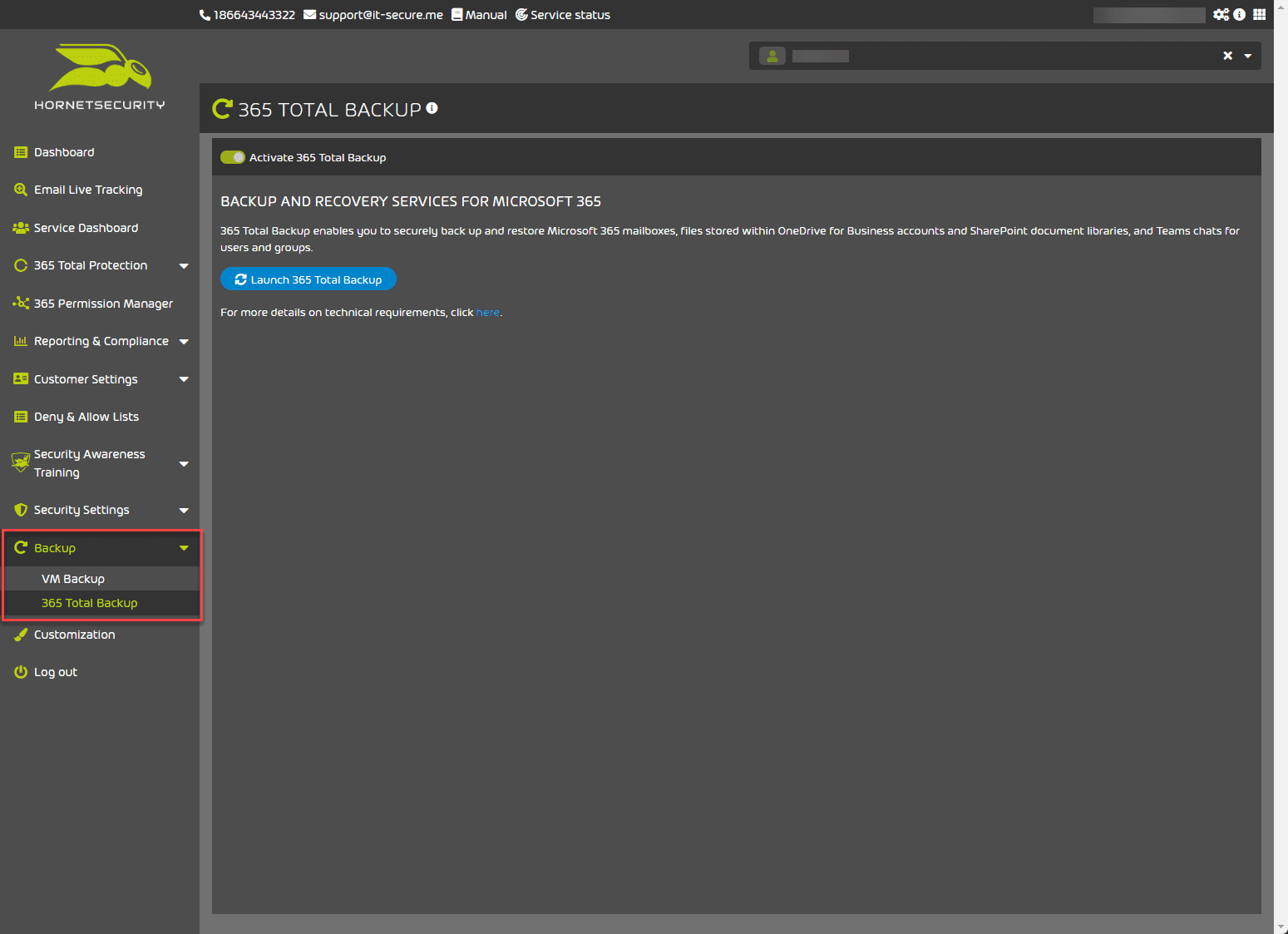
Backup
Backing up your Microsoft 365 environment is critical. Companies are using a wide range of services inside the Microsoft 365 environment. Data must be protected across the range of services used in the Microsoft 365 environment.
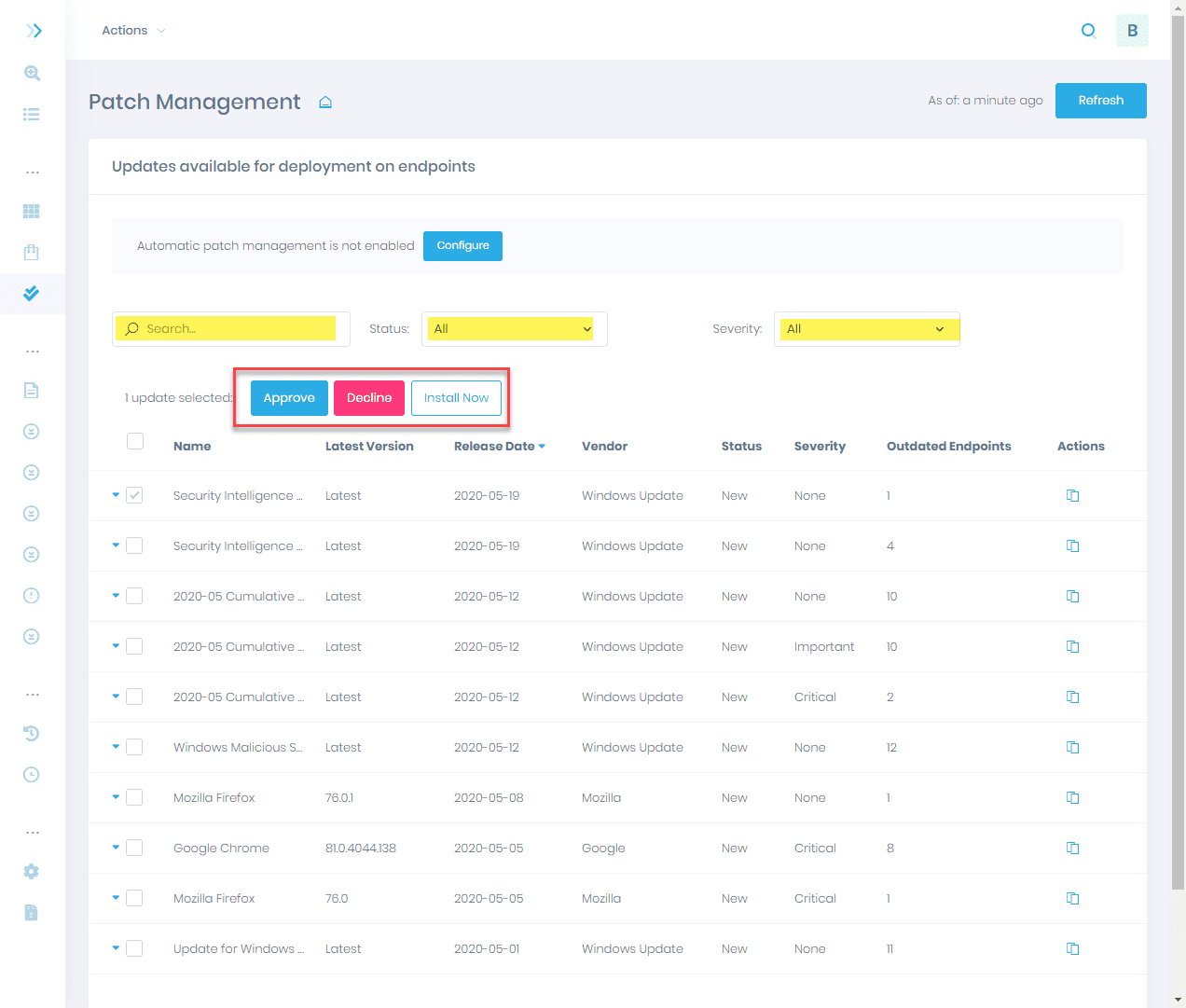
One of the excellent features of the Hornetsecurity 365 Total Protection solution is the backup features and functionality. With the 365 Total Protection solution, organizations can back up and recover their Microsoft 365 mailboxes, OneDrive accounts, SharePoint document libraries, and Teams and provide VM backup from the Total Protection console.
Generally, customers are still managing on-premises virtual machines that must be protected in addition to their cloud and SaaS environments. It is great to see the 365 Total Protection solution allows customers the capability to protect their on-premises virtual machines in addition to their cloud SaaS data.
365 Total Protection licensing
There are different levels of the 365 Total Protection solution. These include the following:
365 Total Protection Business
365 Total Protection Enterprise
365 Total Protection Enterprise Backup
If you would like to see the differences between the different licensing types, check out the comparison of the different products here:
Office 365 security – protect your company with 365 Total Protection (hornetsecurity.com)
365 Total Protection FAQs
Do you need to back up and protect your cloud SaaS data? While many feel that protecting cloud SaaS data is redundant, having an enterprise backup of your critical cloud SaaS data allows businesses to have a completely separate copy of their cloud SaaS data outside the cloud SaaS environment. It means you own the data and can restore it outside the environment. Failing to have a backup or losing access to your cloud SaaS data means you lose access to your data. With a backup, you retain access to your cloud SaaS data regardless of access to the cloud SaaS environment.
What is 365 Total Protection from Hornetsecurity? The 365 Total Protection solution is a cloud-based email security and backup solution allowing organizations to effectively protect their Microsoft 365 data from attacks and provide data loss prevention for critical data. The service is SaaS-based, meaning businesses have no infrastructure to maintain.
What features are provided with 365 Total Protection? Customers get powerful email filtering, security, backups, and the ability to back up on-premises virtual machines with the solution, even with the enterprise license with backups.
Is 365 Total Protection a hybrid solution? It can protect resources, both in the cloud and on-premises. It allows organizations to protect key on-premises resources running in legacy virtual machines and simultaneously protect their modern cloud SaaS data.
Wrapping Up
Attackers continue shifting their focus on cloud environments and the data they contain. Cloud ransomware, malware, and data loss are all threats that today’s businesses must overcome.
The 365 Total Protection solution from Hornetsecurity has many powerful features for securing and protecting your Microsoft 365 email environment. These include company disclaimers, email archiving, eDiscovery, forensic analyses, ATP sandboxing, real-time threat reporting, malware alerting, and automated backups.
You can sign up for a free trial of the solution here: Office 365 security – protect your company with 365 Total Protection (hornetsecurity.com)