Check Windows 10 for SeriousSAM and HiveNightmare Vulnerability Fix
***Update*** – Check out the link to my PowerShell remediation script below.
Well, it has been quite a year so far in many ways. Including the fun we have had as system administrators is the seemingly record number of zero-day bugs that have been found in Microsoft Windows. We are on the heels of the PrinterNightmare debacle, currently with no patch, and we now have a new zero-day bug – “SeriousSAM or HiveNightmare.” Announced in the past few hours, SeriousSAM or HiveNightmare allows someone in the underprivileged USERS group to do things they shouldn’t. Let’s take a look at Check Windows 10 for SeriousSAM and HiveNightmare Vulnerability Fix workaround and see what this entails from an admin perspective and the fallout of doing so.
What is SeriousSAM and HiveNightmare?
Typically when underprivileged users in the common Users group on a machine try to do things that only an administrator should be able to do, like read sensitive registry settings, they can’t. However, with SeriousSAM and HiveNightmare, that is exactly what they have been discovered to be able to do.
A set of overly lax security permissions have been found to exist on multiple system files. Specifically, the files found in the C:\Windows\System32\config foldercontain files such as SYSTEM, SECURITY, SAM, DEFAULT, and SOFTWARE. With the SeriousSAM and HiveNightmare zero-day, underprivileged users have permissions to these sensitive files, meaning an attacker can read senstive credentials and other information if they know what they are doing.
An attacker who successfully exploited this vulnerability could run code using the very high-level SYSTEM privileges. It means they could install programs; view, change, or delete data; or create new accounts with full user rights. An attacker must have the ability to execute code on a victim system to exploit this vulnerability.
Proof of concept code is already out on Github to do this. Take a look here:
Check Windows 10 for SeriousSAM and HiveNightmare Fix
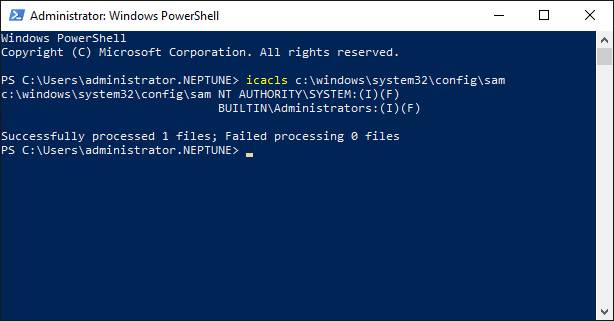
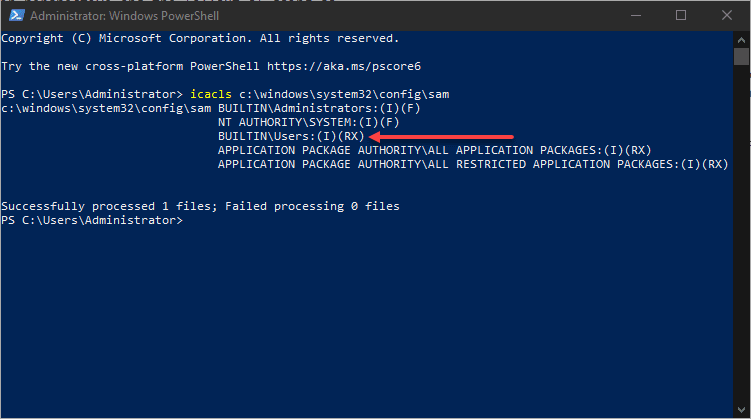
How do you check to see if your machines are affected by the SeriousSAM and HiveNightmare vulnerability? Actually, you can do that with a simple icacls query shown. The workstation below has the vulnerability as you can see the underprivileged BUILTIN\Users:(I)(RX) permissions in place.
icacls c:\windows\system32\config\samEven Microsoft’s new Windows 11 client operating system is affected by this zero-day bug. The current list of affected operating systems include the following that have been identified:
- 1809 ISO-June21 – 20H2
- 1909 ISO-June21 – 20H2
- 20H2 ISO-orig – 21H1
- 21H1 ISO-June21 – 11 Insider (Windows 11)
There are actually a couple of Windows Server releases as you can see on the currently blank (patches) that are listed on the official CVE page from Microsoft:
Jul 20, 2021Windows Server, version 20H2 (Server Core Installation)-Elevation of PrivilegeImportant–CVE-2021-36934Jul 20, 2021Windows 10 Version 20H2 for ARM64-based Systems-Elevation of PrivilegeImportant–CVE-2021-36934Jul 20, 2021Windows 10 Version 20H2 for 32-bit Systems-Elevation of PrivilegeImportant–CVE-2021-36934Jul 20, 2021Windows 10 Version 20H2 for x64-based Systems-Elevation of PrivilegeImportant–CVE-2021-36934Jul 20, 2021Windows Server, version 2004 (Server Core installation)-Elevation of PrivilegeImportant–CVE-2021-36934Jul 20, 2021Windows 10 Version 2004 for x64-based Systems-Elevation of PrivilegeImportant–CVE-2021-36934Jul 20, 2021Windows 10 Version 2004 for ARM64-based Systems-Elevation of PrivilegeImportant–CVE-2021-36934Jul 20, 2021Windows 10 Version 2004 for 32-bit Systems-Elevation of PrivilegeImportant–CVE-2021-36934Jul 20, 2021Windows 10 Version 21H1 for 32-bit Systems-Elevation of PrivilegeImportant–CVE-2021-36934Jul 20, 2021Windows 10 Version 21H1 for ARM64-based Systems-Elevation of PrivilegeImportant–CVE-2021-36934Jul 20, 2021Windows 10 Version 21H1 for x64-based Systems-Elevation of PrivilegeImportant–CVE-2021-36934Jul 20, 2021Windows 10 Version 1909 for ARM64-based Systems-Elevation of PrivilegeImportant–CVE-2021-36934Jul 20, 2021Windows 10 Version 1909 for x64-based Systems-Elevation of PrivilegeImportant–CVE-2021-36934Jul 20, 2021Windows 10 Version 1909 for 32-bit Systems-Elevation of PrivilegeImportant–CVE-2021-36934Jul 20, 2021Windows Server 2019 (Server Core installation)-Elevation of PrivilegeImportant–CVE-2021-36934Jul 20, 2021Windows Server 2019-Elevation of PrivilegeImportant–CVE-2021-36934
However, a quick check of a recently built Windows Server 2019 server in the lab environment yields the following results. So it looks like indeed it is only the client operating systems in just a few quick spot checks.
Workaround for the SeriousSAM and HiveNightmare vulnerability
Microsoft has officially released the workaround of the SeriousSAM and HiveNightmare vulnerability as the following:
Restrict access to the contents of %windir%\system32\config
Command Prompt (Run as administrator): icacls %windir%\system32\config\*.* /inheritance:e
Windows PowerShell (Run as administrator): icacls $env:windir\system32\config\*.* /inheritance:e
Delete Volume Shadow Copy Service (VSS) shadow copies
- Delete any System Restore points and Shadow volumes that existed prior to restricting access to %windir%\system32\config.
- Create a new System Restore point (if desired).
Impact of workaround Deleting shadow copies could impact restore operations, including the ability to restore data with third-party backup applications. For more information on how to delete shadow copies, see KB5005357- Delete Volume Shadow Copies.
Note You must restrict access and delete shadow copies to prevent exploitation of this vulnerability.
Wow! So if you see the fact that you have to delete Shadow Copies, it is concerning to know you essentially have to blast your backups after you fix the vulnerability and then create new System Restore points. This will definitely take some work across most organizations if they are leveraging the System Restore functionality or any other third-party backup solution on their clients that use VSS.
***Update – My PowerShell remediation script for the vulnerability
Check out my follow up post with the automated PowerShell remediation script that makes performing the steps on your Windows 10 or 11 PC easy.
Video overview of the SeriousSAM and HiveNightmare Vulnerability
Concluding
This is another major security issue for Microsoft after they have still not been able to fully patch the PrinterNightmare zero-day as of yet in a satisfactory way. It will be interesting to see how this vulnerability unfolds and how Microsoft officially wants to patch this critical vulnerability. Hopefully this Check Windows 10 for SeriousSAM and HiveNightmare Vulnerability Fix post will help any to see how they can at least identify their workstations as vulnerable.