VMware vCenter Server VCSA Remote Code Execution Exploited in the wild – VMSA-2021-0010 CVE-2021-21985
As a reminder to everyone and the danger of having unpatched systems, it is sobering to hear that the vCenter Server vulnerability tracked as CVE-2021-21985 is being actively exploited. I had read the article here over the weekend showing the vulnerability was actively exploited and vCenter Servers connected to the net were easily compromised. As a sanity check, I thought it would be a good idea to go over some best practices with vCenter Server and also how to patch the critical vCenter Server vulnerability CVE-2021-21985 and how this can be done. Let’s look at VMware vCenter Server VCSA Remote Code Execution Exploited in the wild – VMSA-2021-0010 CVE-2021-21985.
VMware vCenter Server access best practices
It is still shocking to me and many others in the community that read reports of vCenter Servers connected to the Internet. However, obviously, this is a real thing happening in the wild in many more environments than would seem possible. Folks, this is never a good idea and only asking for trouble, even if we were not dealing with CVE-2021-21985. You are drastically increasing your attack surface by placing a vCenter Server where it is accessible from the Internet.
Also, secondary to never placing your vCenter Server on the Internet, it is not even good practice to place your vCenter Server where it is accessible on the same internal LAN. If an attacker makes it into your network, the first thing they are going to do is start performing reconaissance and seeing what they have access to connect to from a network perspective.
If your vCenter Server is on the same network as everything else, it makes it easily found and of course a major target of compromise. You want to segment your network in such a way that vCenter Server is not accessible by general nodes on the network such as client workstations, etc.
VMware vCenter Server VCSA Remote Code Execution Exploited in the wild – VMSA-2021-0010 CVE-2021-21985
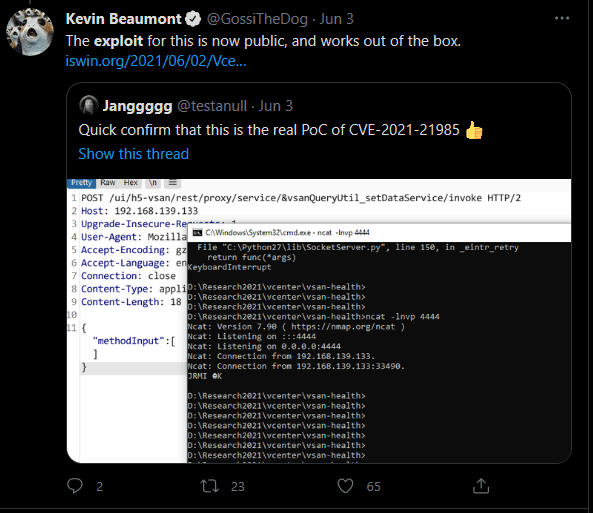
The big question with any exploit is always, “is it exploited in the wild?” As the CVE-2021-21985 rates a 9.8 out of 10, we all figured it was a good possibly that it would be exploited quickly. That definitely seems to be the case. Take note of the article ran on Ars Technica:
It doesn’t take but a quick search on the Twitterverse to see the exploit in action:
There was another post highlighted by the Ars Technica article that seemed to display a one-click exploit of the vulnerability as well, making this one extremely dangerous.
Patch vCenter Server VCSA for CVE-2021-21985
VMware has drastically improved the process to patch the VCSA appliance and makes this process very painless. It does not interrupt the running of normal workloads, so you should be able to do this during the middle of the day. There are a few best practices and things to consider before running the patch of vCenter Server. What are these? This is my list that I like to run through:
- Take a snapshot of the VCSA appliance from the ESXi host level before running the upgrade
- Take a backup of the VCSA appliance from the appliance level VAMI interface
- Quiesce your backup jobs beforehand and make sure these are fully stopped and any lingering snapshots are allowed to roll off from the backup iteration
- Pause your monitoring and other software that relies on vCenter Server
- I also like to disable HA on vSphere clusters that are prior to vSphere 7.x
There are a couple of ways I use to upgrade your vCenter Server Appliance VCSA. These include:
- Use the VAMI interface to perform the upgrade
- Manually patch the VCSA appliance using the patch ISO
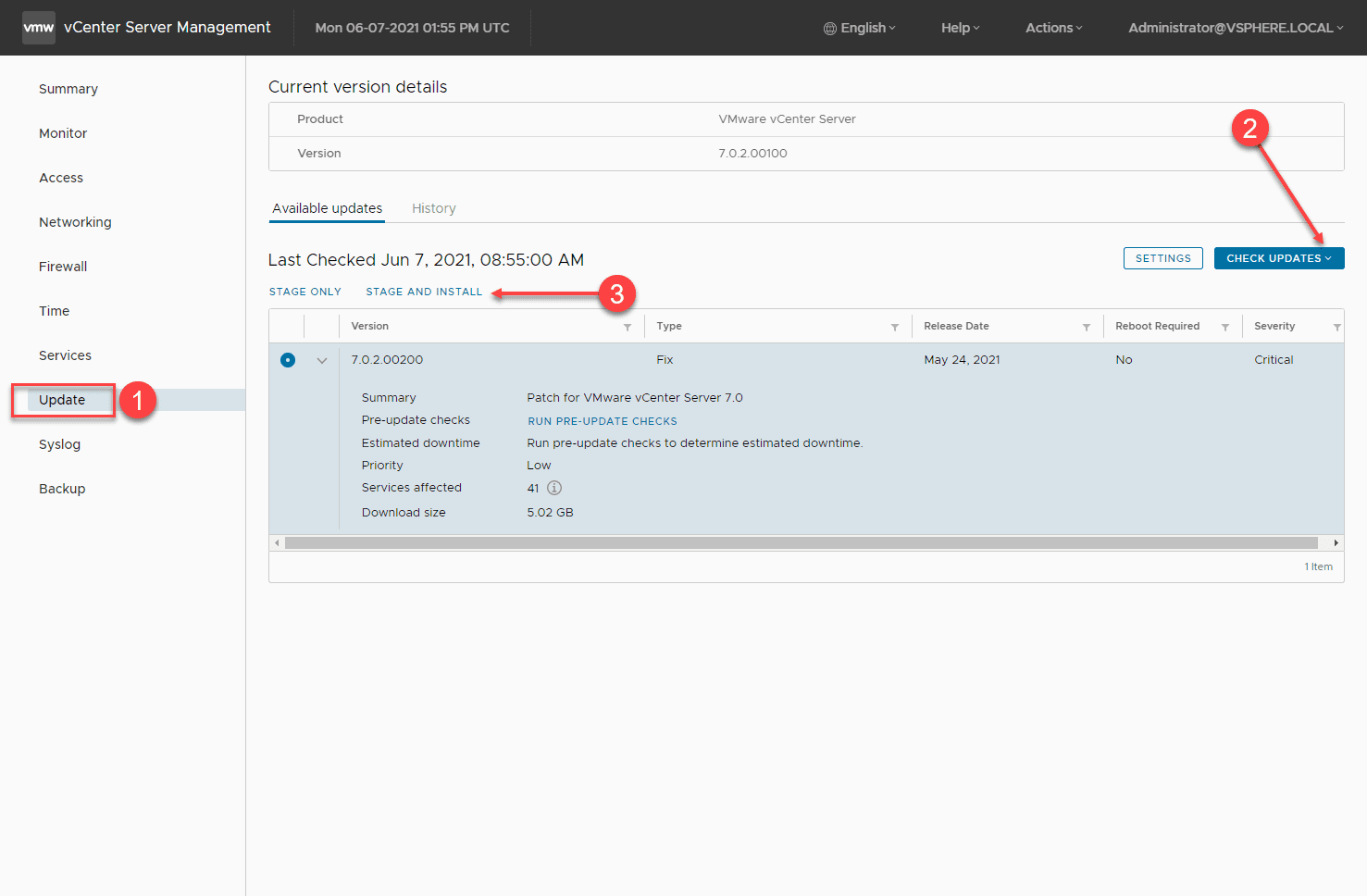
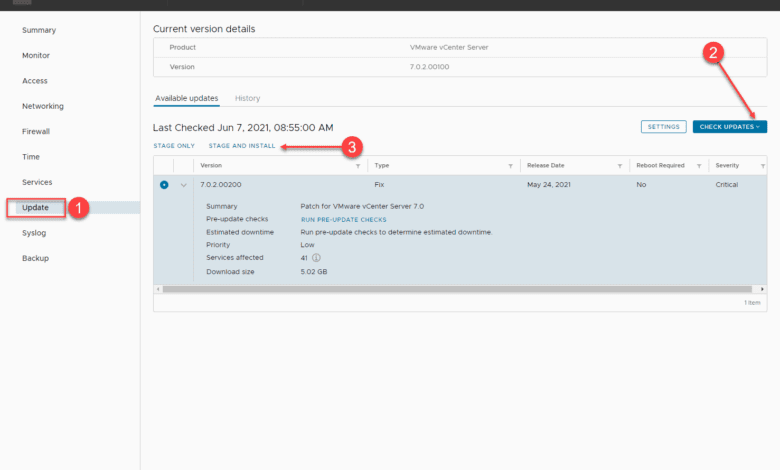
1. Use the VAMI interface to perform the upgrade
This is the most common way to get your VCSA appliance upgraded and requires the fewest steps to do so. As long as your vCenter Server has Internet connectivity (egress connectivity), you can simply login to the VAMI interface and kick off the upgrade of the appliance straight from the interface. The update will be automatically pulled down from the online patch repository and applied to the VCSA appliance.
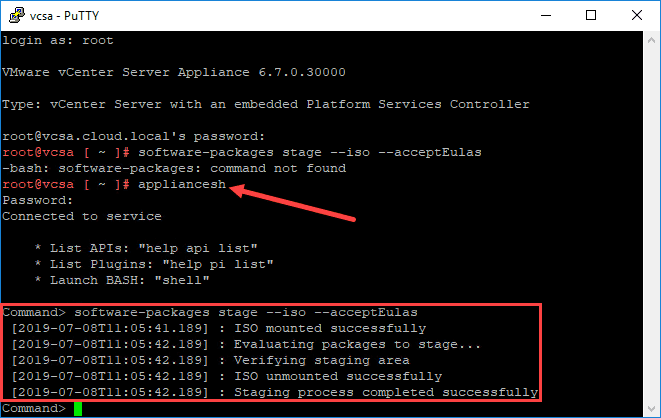
2. Manually patch the VCSA appliance using the patch ISO
I have written about this method before, so I won’t go through all of the steps to do this. It involves manually pulling down the VCSA patch ISO from the online VMware patch repository, mounting the ISO to the VCSA appliance, and then applying the patch using some command line statements from an SSH shell. This is a great method that comes in handy especially when your vCenter Server does not have direct Internet connectivity.
Summarizing
The news this vulnerability is exploited in the wild so soon and with such ease makes this all the more critical to give attention to. Unfortunately for many, if they have not already patched this critical vulnerability, their vCenter Servers have probably already been popped if they are found on the public-facing Internet.
We are in a day and age where we can no longer ignore or assume a security flaw is a lower priority than other operational tasks. We must give this flaw and others that come along their due diligence to avoid becoming the victim of major compromise of business-critical data. Hopefully this post covering VMware vCenter Server VCSA Remote Code Execution Exploited in the wild – VMSA-2021-0010 CVE-2021-21985
Links for reference: