Enable Two-Factor Authentication for VMware Horizon UAG
Are you finding yourself ramping up efforts on remote workers lately due to Coronavirus? Are you working on ramping up VMware Horizon environments to enable your remote workers. From a security standpoint, you want to make sure you secure your logins through your UAG appliance with 2 factor authentication. How do you enable two-factor authentication with VMware Horizon UAG? Duo offers a great way to do this fairly easily with their duo authentication proxy. Let’s take a look at how to enable 2-factor authentication for VMware Horizon UAG connections and see how to secure your logins with MFA. While this is not a difficult process, there is a lot of conflicting documentation and bits and pieces out there. Hopefully this post will help others who may be struggling to put it altogether.
Duo Authentication Proxy Horizon Architecture
Just a brief overview here so you can quickly understand how the Duo two-factor authentication proxy works.
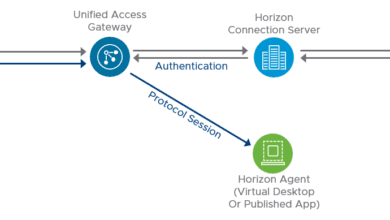
We will configure the UAG appliance to use RADIUS authentication. The Duo authentication proxy serves as an interim RADIUS server that intercepts the RADIUS request. Duo sends your users an automatic authentication request via Duo Push notification to a mobile device or phone call after successful primary login.
So, Duo first sends the authentication request to another RADIUS server on your network (NPS) or to a domain controller to first verify the login is correct. If so, then the duo authentication proxy sends the sends the push notifcation, text, or call to the mobile device of the end user configured in Duo to use the VMware Horizon application.
Now that we have this flow of how authentication works from UAG to the duo authentication proxy, we can proceed with setup.
Installing Duo Authentication Proxy
Installing the Duo authentication proxy is fairly easy. Simply stand up a Windows or Linux box to host the service. I chose a Linux box for the lab environment.
The steps below are for installing on Linux, however, you can find the Windows installation instructions here: https://duo.com/docs/radius#install-the-duo-authentication-proxy
Install the Prerequisites
There is not much to install to get Duo authentication proxy up and running. Just a note here, I am installing on Ubuntu Server 18.04 with all the updates applied at the time of this writing.
apt-get install build-essential python-dev libffi-dev perl zlib1g-dev
Download the Duo Authentication Proxy Installation
Download the installation package for the authentication proxy.
wget https://dl.duosecurity.com/duoauthproxy-latest-src.tgz
Installation
For the below, I had downloaded my installation file to the /tmp directory, so for me, I was working out of here.
tar xzf duoauthproxy-latest-src.tgz cd duoauthproxy-version-src make cd duoauthproxy-build ./install
Setup VMware Horizon Duo Application
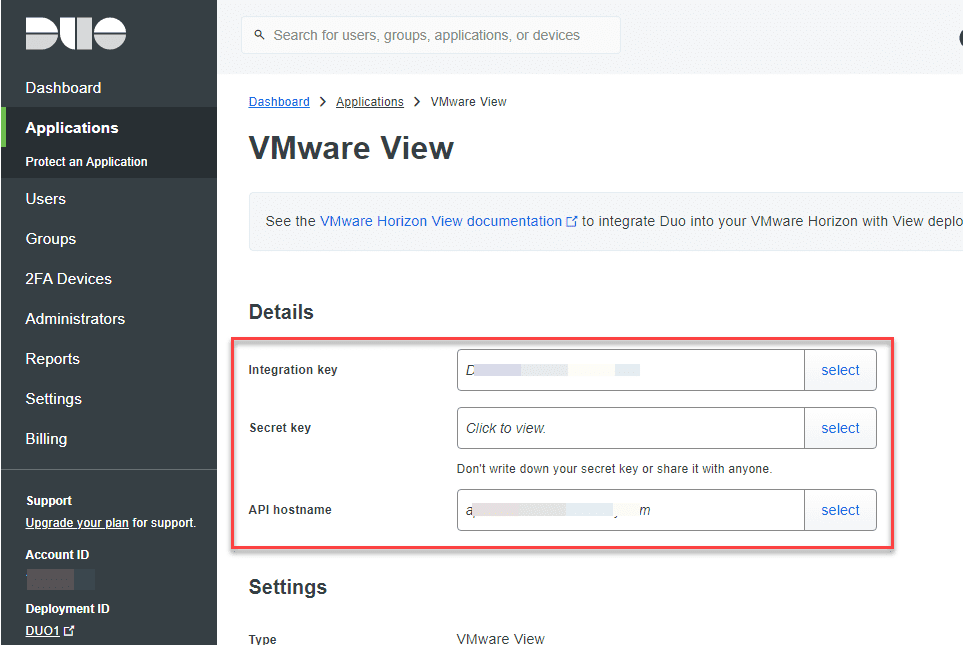
You will need to setup a VMware Horizon Duo application. This is an “in the box” application that is already available. Just add the application to your account. This is available in the free accounts as well. This is the version I am using at home and for the lab.
Create the new application and take down the information that is displayed under the Details section. The three pieces of information you will need for your Duo Proxy are the:
- Integration key
- Secret key
- API hostname
Update the Duo Authentication Proxy Configuration File
The configuration file that we are interested in updating for our duo authentication proxy is found here:
- /opt/duoauthproxy/conf
- Filename: authproxy.cfg
Below is the working config that I have working in my lab environment.
; Complete documentation about the Duo Auth Proxy can be found here: ; https://duo.com/docs/authproxy_reference ; MAIN: Include this section to specify global configuration options. ; Reference: https://duo.com/docs/authproxy_reference#main-section ;[main] ; CLIENTS: Include one or more of the following configuration sections. ; To configure more than one client configuration of the same type, append a ; number to the section name (e.g. [ad_client2]) [radius_client] host=<your RADIUS server IP> secret=<secretkey> ----- this is the one you will configure between Duo and your upstream RADIUS server ; SERVERS: Include one or more of the following configuration sections. ; To configure more than one server configuration of the same type, append a ; number to the section name (e.g. radius_server_auto1, radius_server_auto2) [radius_server_auto] ikey=<your DUO ikey> skey=<your DUO skey goes here> api_host=<your DUO api_host> radius_ip_1=<your UAG IP> radius_secret_1=<secretkey> ----- this is the one you configure in UAG failmode=secure client=radius_client port=1812
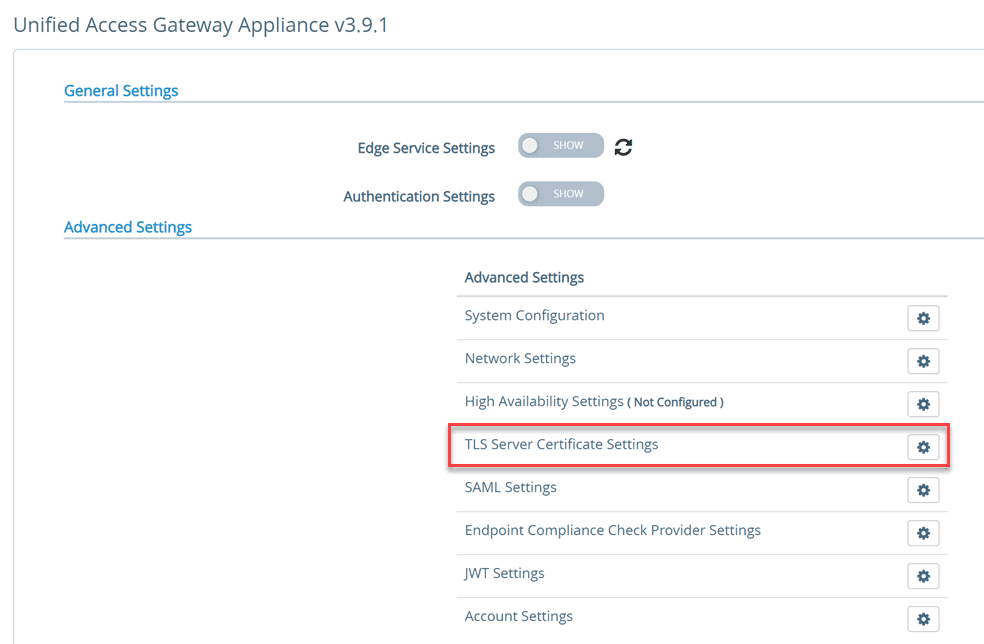
VMware Horizon UAG RADIUS Configuration
Now, let’s configure our UAG appliance to use RADIUS authentication. We will configure RADIUS on the UAG to point to the Duo authentication proxy.
Click the settings cog to configure.
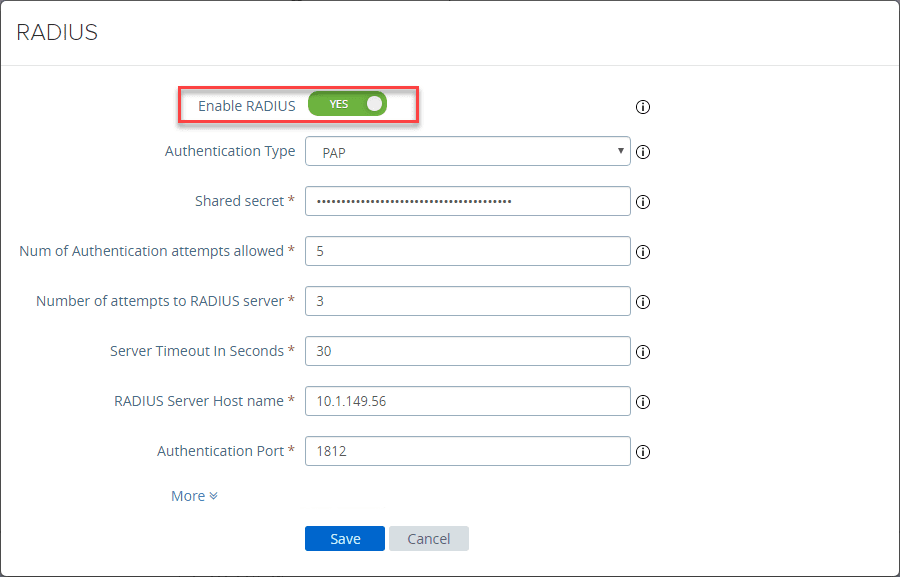
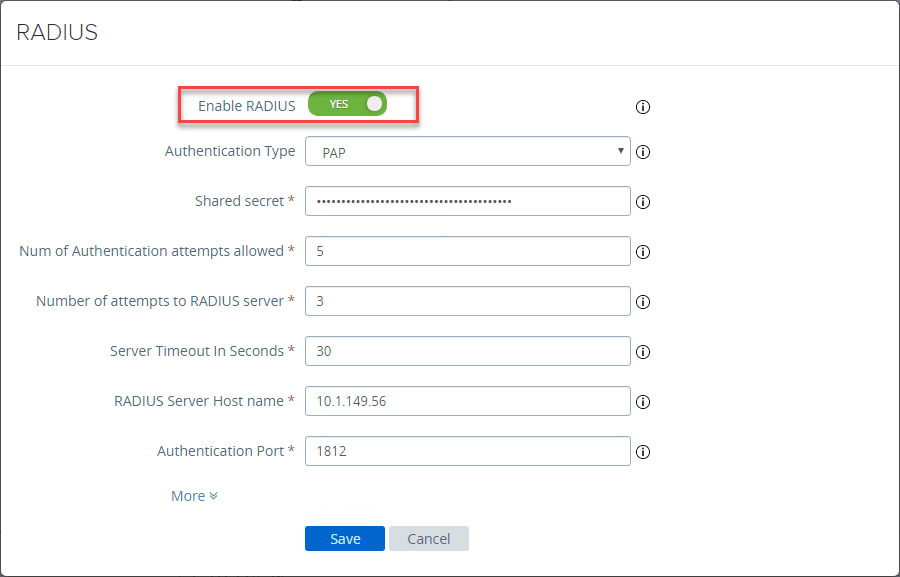
Toggle the Enable RADIUS button. Configure the settings here including the Shared secret. This will be the value you place in the radius_secret_1= value under the [radius_server_auto] section of the Duo authentication proxy configuration file.
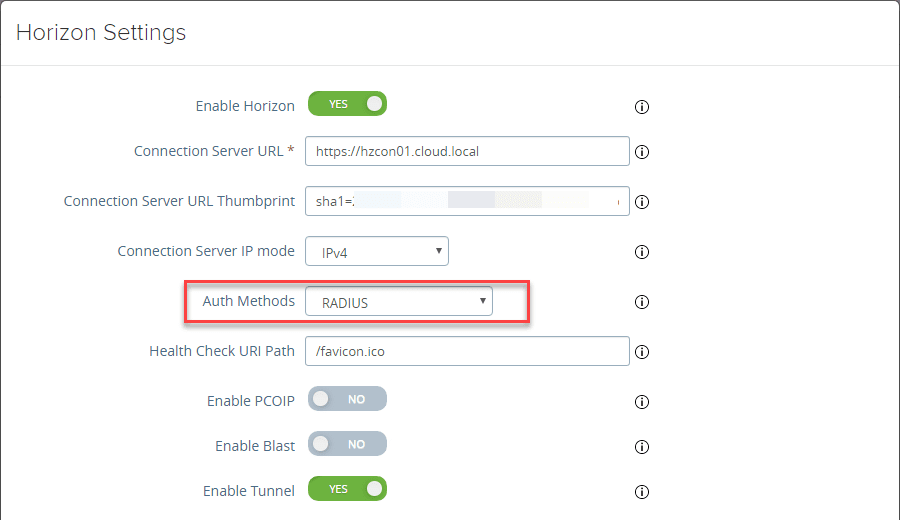
Under your Horizon Connection Server configuration, under Auth Methods, choose RADIUS.
Wrapping Up
That is it! This is all you need to do to Enable Two-Factor Authentication for VMware Horizon UAG. Now you can test the connection by logging into your UAG via the Horizon Client or the Web Client. Sit back and enjoy two-factor authentication on your UAG fronted Horizon infrastructure.