What Is VMware Service-Defined Firewall Released?
Security is perhaps one of the most talked about and exciting areas of IT operations today as it is constantly evolving and making use of new technologies to stop the “bad guys” from compromising business-critical systems and data. With the VMware NSX software-defined network product, VMware has been able to start introducing revolutionary capabilities in the enterprise to allow organizations to effectively microsegment network environments. Since the very first implementation of NSX and basic microsegmentation, the product has continued to evolve. On Tuesday, March 5, 2019 at the RSA conference, VMware made an exciting announcement of a new internal firewall called the “Service-Defined Firewall” that is set to revolutionize how security is taken care of internally. Let’s take a look at What Is VMware Service-Defined Firewall Released and see how it works, what is is made up of and how it could be a game changer for security in the enterprise.
The Problem with Perimeter Firewalls
Why the release of Service-Defined Firewall? Today’s complex, application-centric environments have evolved past the capabilities of the archaic and traditional perimeter firewall. Even so-called “next-generation” firewalls are based on the old principle that the firewall sits on the perimeter and keeps the “bad stuff” out of your network. They filter based on an unlimited number of unknown hosts. However, this is no longer effective with modern threats to today’s application environments and the bad guys can often get into a network. Today’s security model and operations needs to run off the principle that the “bad guys” have already got into your network. How to you prevent or at least make their movement through your network as difficult as possible? This lateral movement once inside a network is something the perimeter firewall has no defenses against. Once inside, the bad guys all too often can move around freely and with little deterrence.
Let’s look briefly at the following three limitations of traditional firewalls:
- Perimeter firewalls filter traffic from unknown hosts
- Perimeter firewalls typically use port blocking mechanisms
- Perimeter firewalls create network performance bottlenecks
Perimeter firewalls filter traffic from unknown hosts and are limited to layer 7 packet inspection inspecting north/south traffic from the WAN inward. The perimeter firewall has no contextual understanding of the trffic generated by the “good” applications within the network and what good behavior and network traffic looks like. It is much easier and more beneficial to determine good behavior instead of bad behavior. Perimeter firewalls are constantly trying to determine bad behavior.
Typical firewalls use techniques that involve port blocking to allow or disallow network communication. When moving laterally (east/west) inside the network, attackers will often use trusted communication ports to move through the environment. This means that port blocking by itself is not effective against these laterally moving attacks.
An additional downside to perimeter firewalls is they create what VMware calls “network choke points”. If using perimeter firewalls to filter traffic through “zones” and different interfaces, this creates a point that traffic is hair-pinned to these “choke points”. This creates performance issues for network traffic required to pass through these specific network points. Placing a firewall in front of every host is just not a feasible or valid option.
Organizations battling today’s real security challenges and application-centric environments need a new way of securing applications and internal resources for which a perimeter firewall is just not well-suited. In steps VMware’s new solution called the Service-Defined Firewall.
What is VMware Service-Defined Firewall Released?
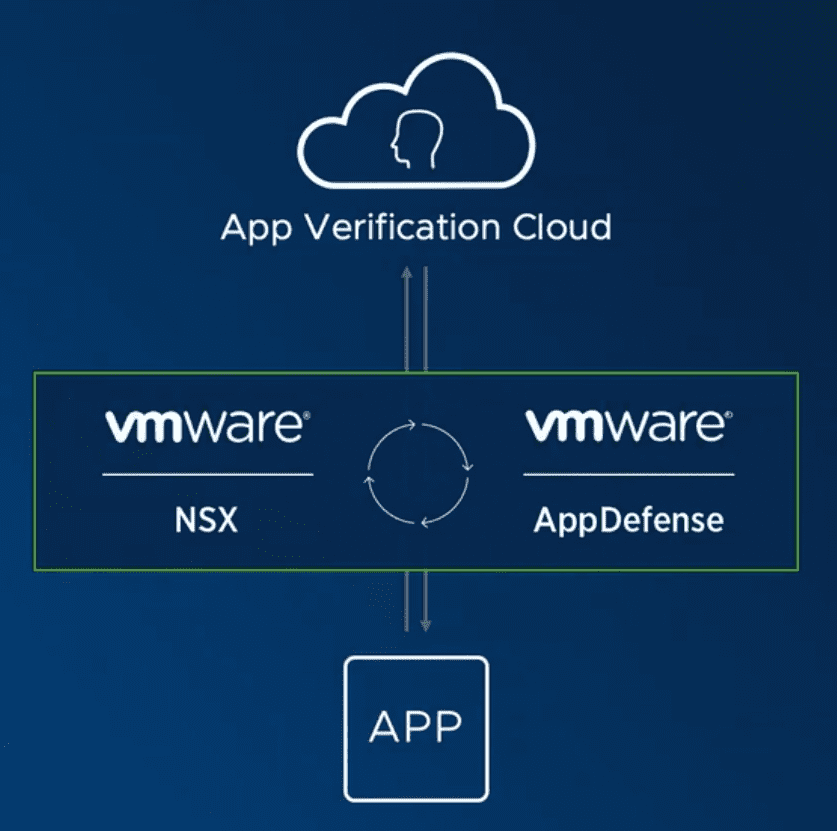
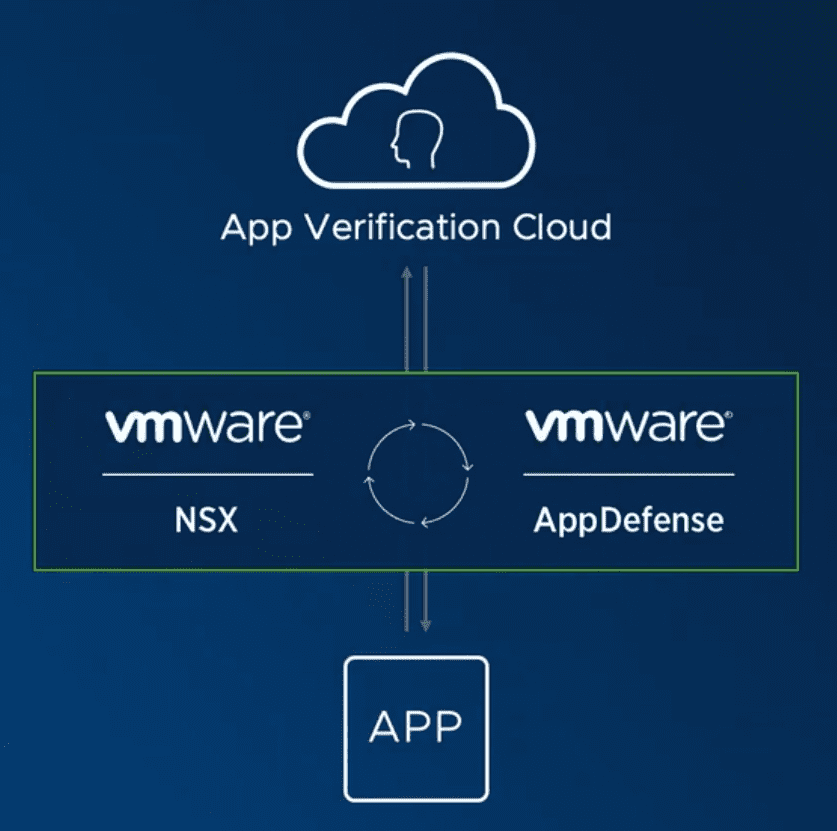
VMware’s new Service-Defined Firewall released is made up of the convergence and utilization of two VMware products on the market, VMware NSX Data Center and VMware AppDefense. VMware Service-defined Firewall has the advantage of deep visibility into the hosts and services that generate network traffic.
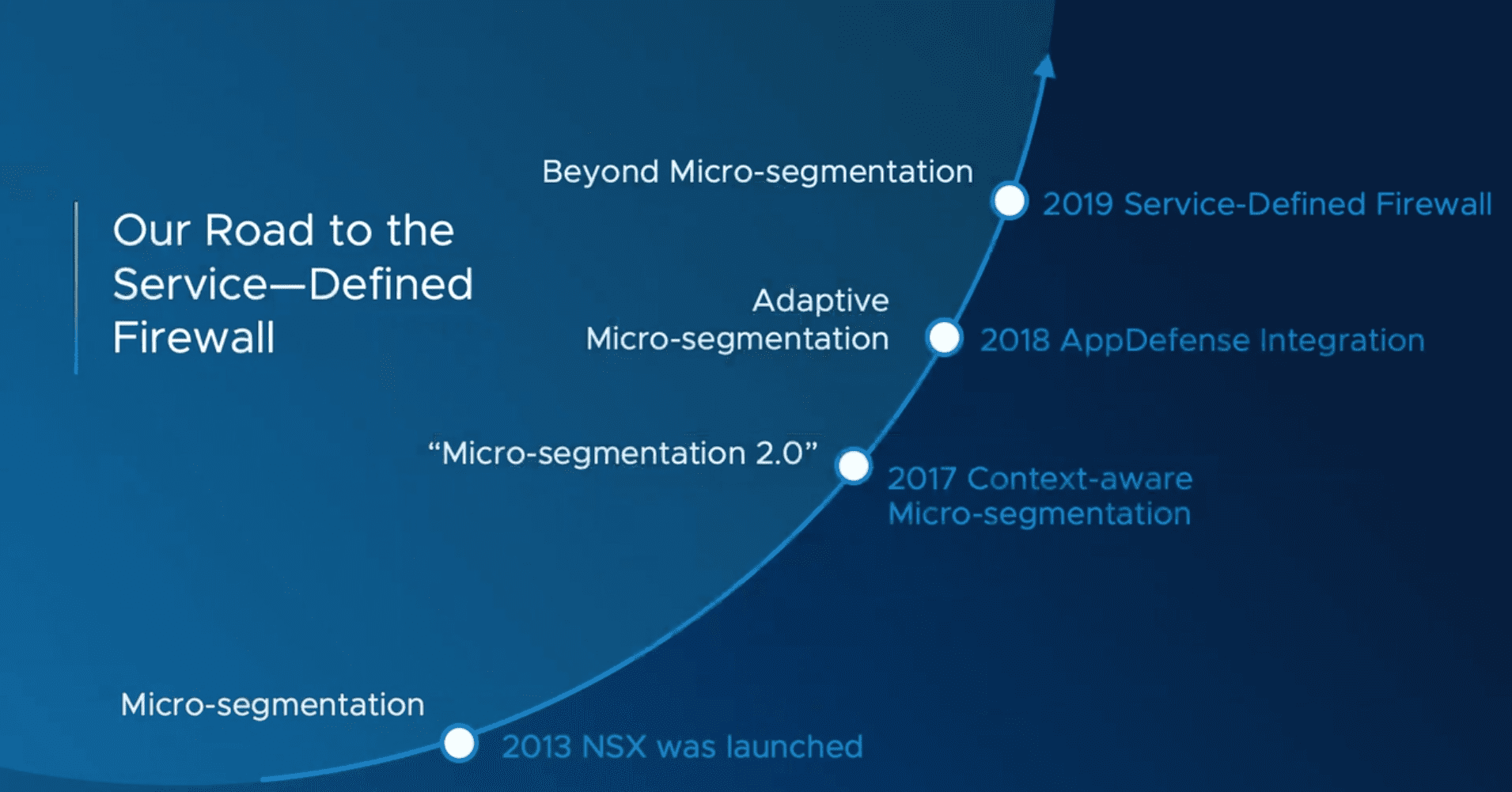
VMware’s NSX product has been around since 2013 but has been evolving with every iteration into a more capable and powerful product. In 2017, Context-aware micro-segmentation was introduced and was branded as “Micro-segmentation 2.0”. In 2018, AppDefense Integration was released and allowed micro-segementation to be “adaptive”. Now, in 2019, the Service-Defined Firewall takes the product beyond just simple microsegmentation and allows security to be adaptive and sport true security intelligence in the following ways:
- Deep Application Visibility and Control
- App Verification Cloud
- Automated and Adaptive Policies
With the Deep Application Visibility and Control aspect of the Service-Defined Firewall, VMware has enabled the Service-Defined Firewall to be much more than a common Layer 7 firewall with packet inspection. The Service-Defined Firewall has visibility not only into L7 packet inspection but also into the behavior of the application. Understanding the correlation between the behavior of the application and being able to allow or deny network communication and traffic based on that behavior, including understanding the topology, allows truly bolstering the true end-to-end application security posture.
Customers running on the VMware hypervisor have millions upon millions of workloads that run inside of vSphere. VMware has built the App Verification Cloud that leverages machine learning along with human intelligence and allows building a fingerprint if you will of known good application behavior and what that looks like exactly. With VMware’s massive footprint across the enterprise space, VMware is able to profile and identify known good behavior and know what this looks like so that security policies can be easily created to match this known good behavior and block any mutation or variation of that profile.
Automated and Adaptive Policies – VMware’s Service-Defined Firewall is able to take the heavy lifting out of the process of configuring and adapting the security policies based on changes in application services even if these changes happen rapidly. Using the powerful machine learning App Verification Cloud, VMware’s Service-Defined Firewall can automatically create the needed rules and block traffic that falls outside of the known good footprint of normal behavior for the application.
This is a Software-driven Approach to security that does not rely on any specific hardware or appliances that customers may be used to seeing when it comes to security. Today’s fast-paced environments are being driven by software as it is allowing operations, security, and other initiatives to move more quickly than ever before. The Software-driven Firewall is just that – driven by software which makes it extremely powerful.
Watch the Service-Defined Firewall in action where VMware shows how the Service-Defined Firewall is used to block a real attack as it happens on a 3-tier application.
VMware Service-Defined Firewall Resources
- VMware Official Service-Defined Firewall Overview
- Validation Report of the Service-Defined Firewall by Verodin
- Service-defined Firewall Solution Overview PDF
- SANS Adaptive Micro-Segmentation White Paper
Final Thoughts
VMware is killing it IMHO with the NSX and AppDefense product lines. They are creating solutions that are pushing the envelope of security and allowing enterprises to meet up with the complex challenges being presented across today’s hybrid and software-defined environments. So when looking at What Is VMware Service-Defined Firewall Released we see that it is a very powerful combination of the latest advancements in NSX Data Center technology and AppDefense that allows organizations to effectively secure internal application resources in an adaptive way. This is a tremendously powerful solution that will no doubt redefine the security landscape of organizations making use of VMware solutions to both run and secure internal resources.









