How to Choose the Best CASB
With the tremendous cybersecurity threats present in the world today, organizations are certainly focusing their attention on how IT resources and their data can be protected. This is especially true with organizations who have resources that are located in the public cloud. Many are moving to the public cloud for a wide array of resources and the modern enterprise datacenter is looking at housing less business critical applications than before. Since the inception of “cloud” as a term, security has been a concern among enterprises. I know since I have been in working in the enterprise environment, it has been interesting to see this major shift in where resources are located. Security has always been a concern, however, now most businesses accept that “everyone” is located in the cloud, so cloud and particularly public cloud environments from Amazon, Microsoft, and Google, have garnered everyone’s trust. While cloud has certainly matured since the early days, organizations still must be vigilant with cloud security. What mechanisms or technologies can organizations today utilize to ensure hybrid networks that stretch from on premise to public cloud are secure? By using a Cloud Access Security Broker (CASB), on-premise security policies can be enforced with public cloud infrastructure. What is a CASB exactly? What information is helpful to organizations on how to choose the best CASB for securing cloud resources? We will look at a great example of a powerful CASB that can secure public cloud.
What is a Cloud Access Security Broker (CASB)?
A tremendous technical challenge for businesses today moving to the cloud is succeeding in enforcing the same types of security policy that exist on-premise in their public cloud environment. Since public cloud infrastructure is not directly controlled by the tenant, this can create obstacles to cybersecurity policy, control, and best practices. CASBs can enable organizations to enforce security policy in the public cloud and effectively control the attack surface.

At a high level, Cloud Access Security Brokers or CASBs serve as an effective mechanism to enable public cloud administrators to be able to secure cloud-based resources in the following way:
- Proactively protect against threat vectors
- Gain visibility into activity in the public cloud coming from both external and internal sources
- Effectively control use of public cloud resources with granular policies
- Data loss protection and Data leak prevention
At a more specific level, CASBs can:
- Enforce enterprise security policies – Typically includes:
- Access Control
- Mobile Device Management – MDM
- Control sharing of data
- Manage and enforce compliance
- Control or prevent data from being shared without authorization outside of the business public cloud environment
- Disallow downloading or uploading data to the public cloud – Preventing data exfiltration from an sanctioned cloud service (company public cloud environment) to another cloud service (a personal cloud service used by the employee)
- Enforce policy based on the device used for access or a particular user account or group
- Make sure encryption is utilized
- Create and send alerts based on security events
- Scan and audit for PUPs (potentially unwanted programs) that have been installed which have access to company data
- Protect against malware threats, especially ransomware
- Prevent leakage of sensitive data or personally identifiable information
Different Types of CASBs
There are many options available for CASB implementations that can be utilized for protecting cloud environments. In particular there are couple of types of CASBs – firewall/proxy based, and API-based CASBs. What are differences between the two. Is one type of implementation superior to another?
Firewall/Proxy Based CASB
When thinking about a firewall/proxy based CASB we can easily think about its operation like a traditional firewall. Traditional firewalls sit in the perimeter and are the inline entry and exit point for network traffic coming in and leaving an enterprise network. Firewall/proxy based CASBs operate in a similar way. It scrutinizes all traffic that is destined for the cloud-based environment. So, we can see the following characteristics associated with a firewall/proxy based CASB.
Advantages:
- Traditional approach
- Able to offer real time statistics
- Sits in line between on-premise/Internet traffic and the cloud environment
There are however a couple of issues that quickly come to light with firewall/proxy based. Since all traffic is traversing the firewall/proxy based CASB, this type of solution does not scale very well in terms of performance. Another drawback is certain devices do not support this type of connectivity.
Disadvantages:
- It does not scale very well from a performance and number of users standpoint
- Certain devices do not support connecting via the proxy-based cloud entry point.
Is there a better solution for implementing a CASB to secure cloud resources?
API Based CASB
Today’s world of automation and interacting with programming interfaces is dictated by applications interacting with APIs. In particular RESTful (Representational State Transfer) APIs allow client/server based architecture to be used to interact with infrastructure in a programmatic way. There are 6 guiding principles to RESTful programming:
- Client/server based
- Stateless
- Cacheable
- Uniform interface
- Layered system
- Code on demand
Vendors who make use of RESTful APIs can produce much more powerful systems in both the enterprise and cloud environments.
API based CASBs take advantage of the inherent strengths found with RESTful architecture and programming. Today’s public cloud environments by Amazon, Microsoft, and Google have myriads of public APIs that are able to be consumed by third-parties interacting with the respective public cloud environments. This allows an API based CASB to be a much more native implementation of CASB functionality. In fact, it is as if it is part of the public cloud environment itself. So, rather than being a single “device” or in line mechanism, it becomes a much more powerful security mechanism that is “integrated” into the public cloud environment.
There are other tremendous benefits to utilizing an API based CASB. Since there isn’t a single firewall/proxy based entry point and it is integrated with the cloud, there are no proxy configuration settings that must be implemented from the end user device standpoint. Additionally, performance scaling concerns are not an issue since there is no single entry point and the native integration with the public cloud allows performance that scales infinitely. API based CASB configurations offer benefits as well when it comes to “machine learning” as the data that is gathered from threats, attacks, and other information gleaned from connections flowing through the API based CASB, allow the solution to analyze the data, to “learn” what certain patterns mean. With time, the API based CASB gets better at mitigating attacks.
Advantages:
- Infinite performance and scaling possibilities
- Much more modern approach
- Can take advantage of machine learning
- Is “part” of the cloud environment
- End user devices do not need to be configured with proxy settings
- Cannot be bypassed by an end user attempting to use VPN connections or other network trickery
Disadvantages:
- Not really a huge disadvantage, however, the statistics are not as real time as firewall/proxy based solutions
API Based CASB Example
There are many great companies out there in the security space. However, a great example of an API based CASB offering really great functionality and helping to secure cloud environments is a company called Spinbackup. I have been following their work for a while now and they are really making waves in the public cloud space with protecting Google G Suite environments. Spinbackup not only protects Google G Suite data, but also allows organizations the ability to implement provides cybersecurity functionality by utilizing its powerful API based CASB features.
I have covered a review of Spinbackup in a previous post that you can read here. However, to highlight the cybersecurity features a bit more since thinking about CASBs protecting public cloud environments, let’s look closely at some of the cybersecurity features you get with their solution to protect G Suite environments.
Spinbackup Cybersecurity API based CASB
True to the strengths, features, and functionality of an API based CASB solution, Spinbackup’s cybersecurity solution does not rely on configuring proxy settings within end user devices. It provides native integration by way of installation from the G Suite marketplace and allows businesses to have true data loss and data leak protection.
- Third-party apps control
- Third-party apps are scanned and access can be revoked to applications making unauthorized use of company data
- Ransomware Protection
- State of the art ransomware protection utilizing machine learning that allows not only automatic discovery of ransomware processes but also automatic remediate of data that has been affected
- Sensitive Data Control
- Allows organizations to protect against leaking sensitive data such as credit card numbers and other sensitive data
- Insider Threats Detection
- Discover insider threats from employees either knowingly or unknowingly leaking data outside the organization.
- Custom Policies
- Allows for granular control of various cybersecurity policies throughout the G Suite organization
- Automated cybersecurity alerts
- This allows G Suite administrators to be proactive when gaining visibility to cybersecurity events
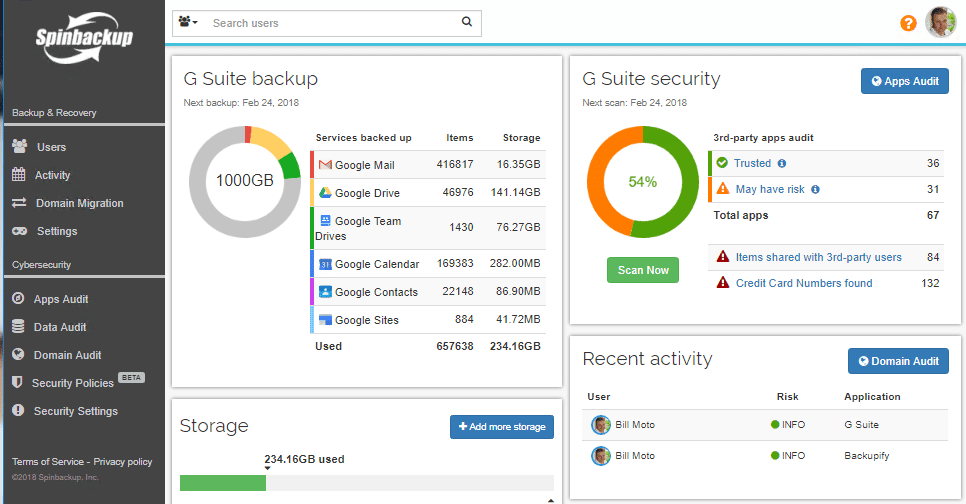
What is great about Spinbackup’s solution is they are unique in the marrying of the two solutions (backup and cybersecurity) within one product. Additionally, with the Spinbackup dashboard, all information is presented in an extremely intuitive, “single pane of glass” view so that all the pertinent information regarding not only cybersecurity but also backups is at your fingertips.

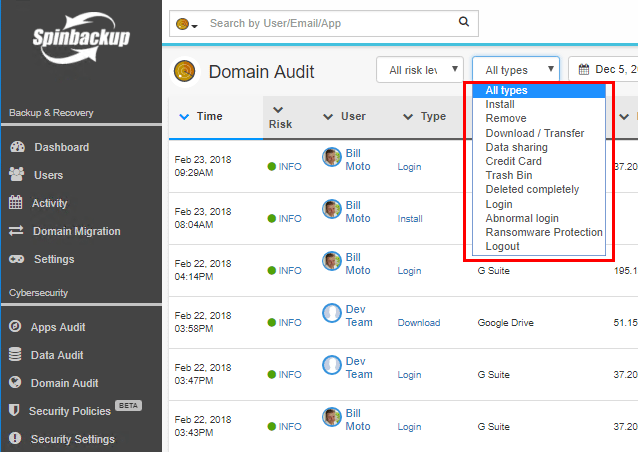
The domain audit dashboard allows quickly seeing all the cybersecurity threats found in your G Suite environment. These can be sorted by Risk level, and type.
Concluding Thoughts
Securing public cloud environments and enforcing the same policies, compliances, and user access can be an extremely difficult challenge for organizations. Cloud Access Security Brokers solve many of the difficult cybersecurity challenges faced by hybrid infrastructure utilized by today’s businesses. Most have a presence in public cloud with business critical data or services. There are many choices in deploying CASB implementations. The question is – how to choose the best CASB? Between firewall/proxy based and API based CASBs, the API based solutions are more powerful. Spinbackup is a great example of an API based CASB solution that helps businesses meet the demanding security challenges they face in public cloud environments such as Google G Suite. By leveraging these types of solutions, you have access to infinite scale, zero configuration on end user devices and the ability to make use of machine learning patterns to provide a living and breathing security solution that proactively protects your organization.