Install VMware VCSA vCenter Appliance Photon OS Security Patches
Current VCSA Security Patches
The following are patches that the first security update for VCSA 6.5 Update 1 from VMware contains:
| Release Date | Build Number | Patch Name | Affected Package | New Package Versions | CVEs Addressed |
|---|---|---|---|---|---|
| 21 September 2017 | 6671409 | 6.5 U1a (security fixes for PhotonOS) |
Linux
Httpd Pycrypto Linux Ncurses |
4.4.77-1
2.24.27-1 2.7a1-3 4.4.79-1 6.0-5 |
CVE-2017-11473 |
Install VMware VCSA Security Patches GUI
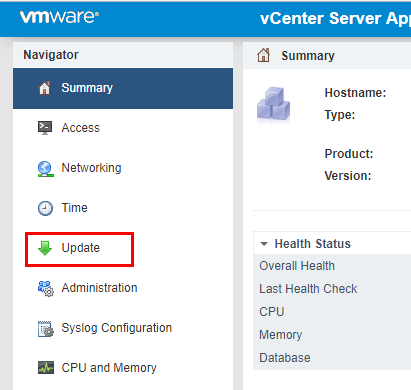
The method that most will be familiar with in patching a VCSA appliance is from the GUI interface. We can get to the Update functionality by browsing out to the VAMI interface https://<your vcenter IP>:5480. Choose the Update menu option.
Select the Update option.
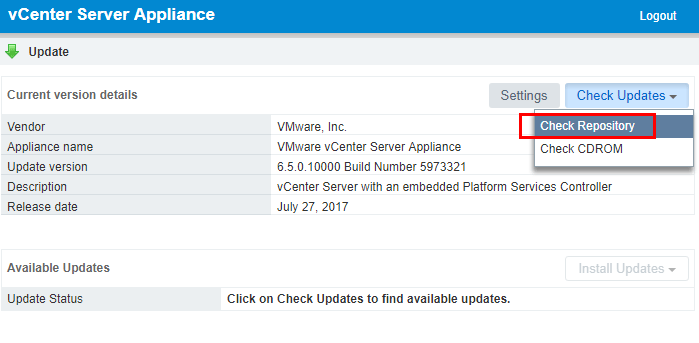
Under the Check Updates menu, click the Check Repository option. This will pull updates from the online VCSA update repository.

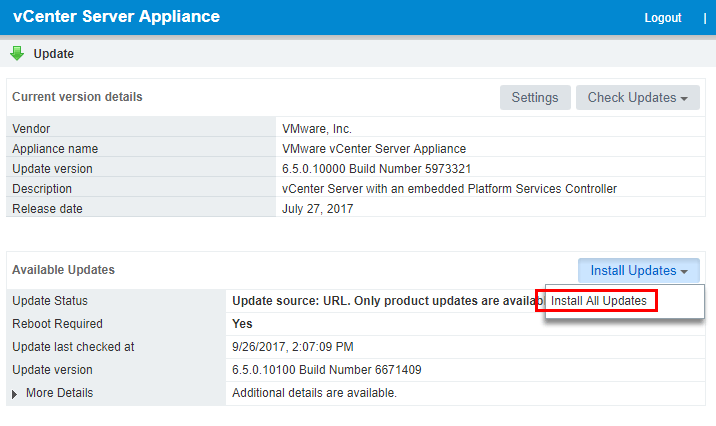
As shown below, the 6.5.0.10100 Build Number 6671409 update is available. We can choose to Install All Updates.
We will be presented with the EULA for the update. Click the Accept button.
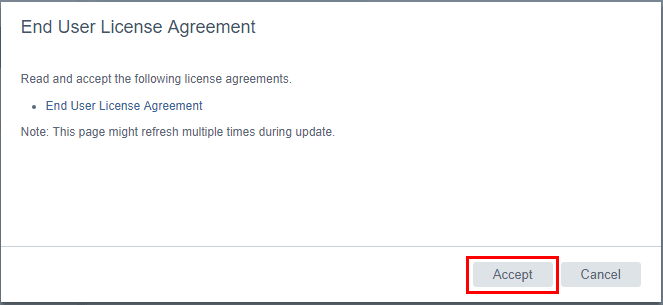
You can choose whether or not you want to join the CEIP program by checking or unchecking the box. Then click the Install button.
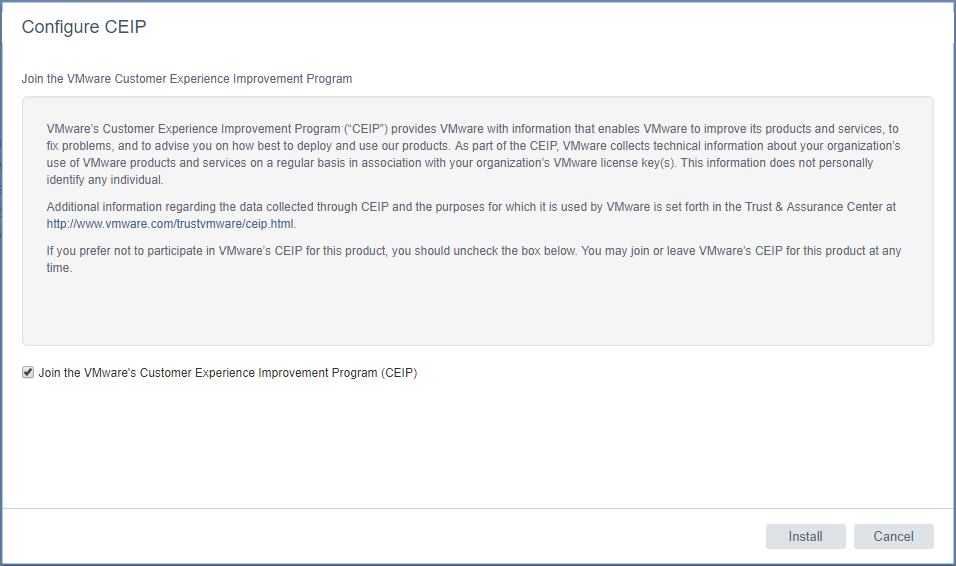
The patches are staged for installation.
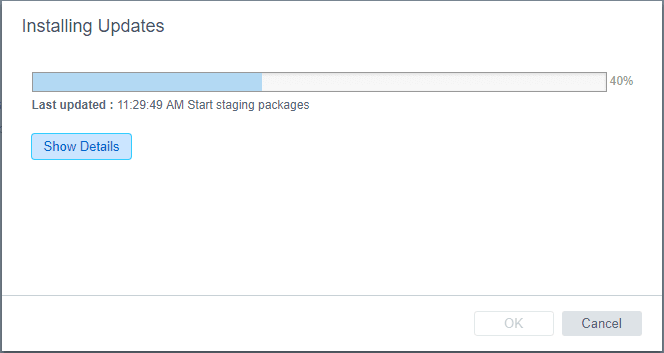
The update process runs a few pre-install scripts. You can select the Show Details button to reveal the specifics of the process.
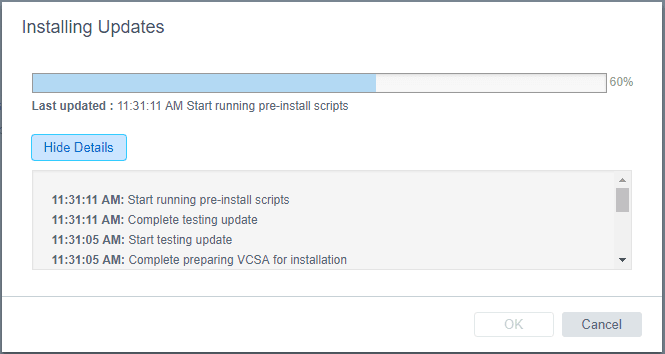
The packages will begin updating after the pre-install scripts run.
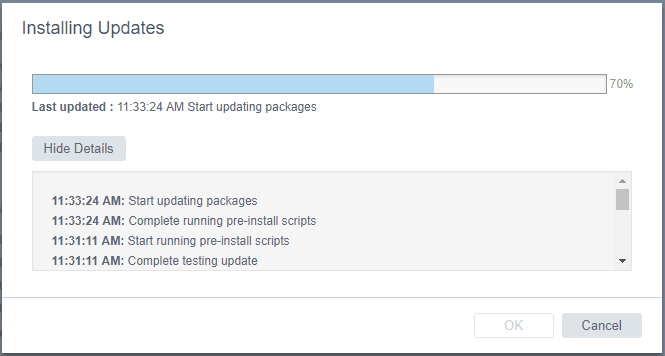
After the update is finished, you will see the message that a reboot is required to complete installation.
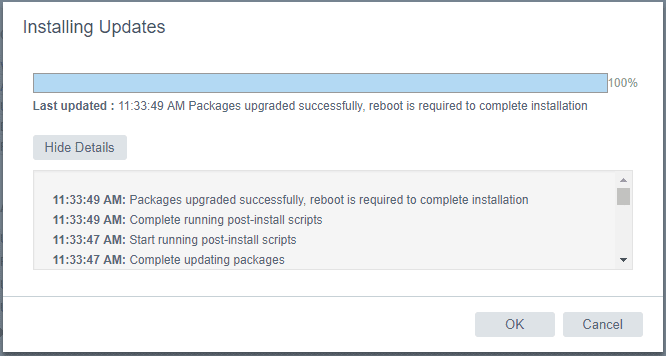
If we go back to the Update menu, we will see the current build number is showing now, however, we still see the reboot directive.
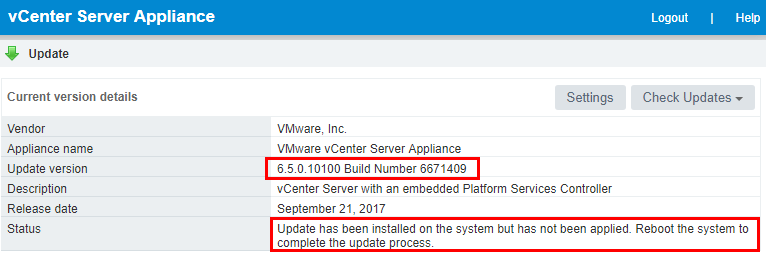
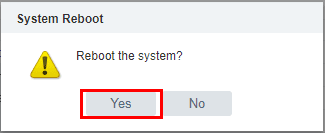
We can easily reboot from the VAMI interface, by going to the Summary tab and selecting the Reboot option.
Select Yes on the reboot the system directive.
Install VMware VCSA Security Patches Command Line
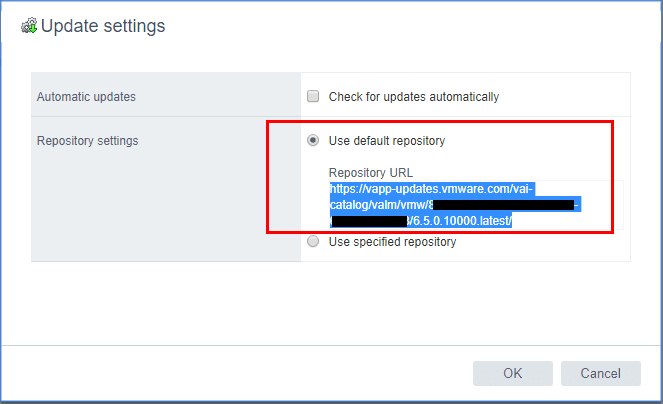
A very easy and powerful way to install patches to VMware VCSA appliance is by using the command line. We can pull the updates directly from the VMware online repository as well. We can find the URL for patching from the online repository by logging into the VCSA VAMI interface https://<your vcenter IP>:5480 and choosing Update >> Settings. Under the Repository Settings you will see the URL for the online repository. We can copy that and use it from the command line.
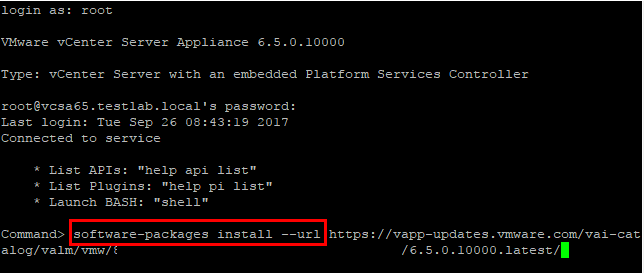
Login via SSH to your VCSA appliance. Make sure your shell is set to the default appliance shell. We will use the software-packages install –url command to stage and install the patches. We use the URL we copied from the VAMI interface Update settings.
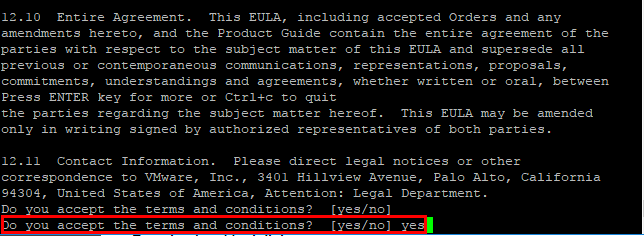
We will see the EULA presented from the command line. You can also use the following command to accept the EULAs automatically:
software-packages install --url --acceptEulas
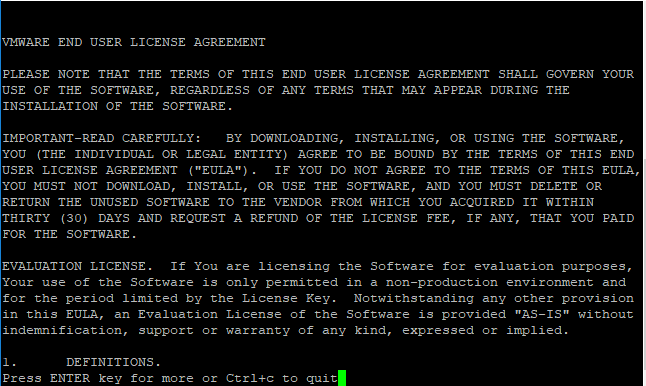
After the EULA, we type out yes to the “Do you accept the terms and conditions?” question.
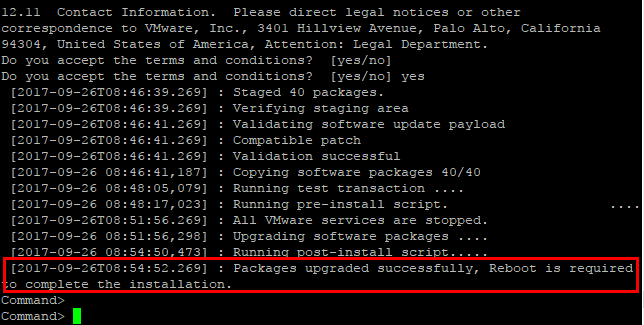
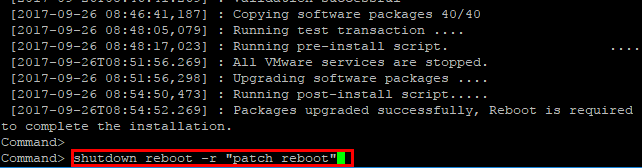
After the reboot of the VCSA 6.5 appliance, we will have the latest patches/security patches installed.
Takeways
The new security posture from VMware regarding the Photon OS is a welcomed change for all wanting to stay current with security updates and patching known or zero day vulnerabilities. The VMware Photon OS is a great platform that is allowing VMware to be more agile and aggressive with development and patching on all fronts. With the new monthly updates, all can Install VMware VCSA vCenter Appliance Photon OS Security Patches and stay current with the platform. As shown the updates can easily be applied using the VAMI GUI or by command line.