How to find and block abusive BYOD devices on your network
With the ever growing popularity of smartphones and tablets and the availability and affordability of these devices, more and more people are bringing them to work. Especially in smaller to mid sized businesses, bandwidth is still a premium that most can’t afford to waste. If you find that you have a sluggish network or download/upload speed isn’t what it should be, it is time to bring out a few tools that can help to identify offending BYOD devices on your network. Let’s list some things that you as a network admin will need. Using the following tools let’s take a look at how to find and block abusive BYOD devices on your network. You will need the following free utilities (if using free firewall, dhcp utilities, etc).
- iftop utility running on a device sitting as a bridge on your network
- nmap – network identification utility
- DHCP tool of your choice with reservation capability
- firewall – anything of your choice here with capability to block traffic either by source address or MAC address (for our example we are using Untangle in its free trim).
Let’s see how we can use the above utilities to effectively squash a bandwidth hog on the network
IFTOP
Iftop is a great utility that let’s you see effectively what traffic and hosts are using bandwidth in and out of your connection. Simply having an Untangle box in between your router and internal network serving as a bridge will allow you to see the data in order to identify problem hosts. However, it doesn’t have to be Untangle. It could be some other sort of Linux box running in between to capture data. As long as all traffic passes through the device you should be good to have the information you need.
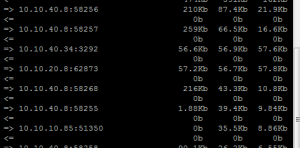
Using the following command we can effectively see traffic on the eth0 interface, IP addresses only and which ports they are connecting to:
iftop -i eth0 -n -P
The command above will display output similar to the following. Also, see our tutorial here about more details using iftop with Untangle.
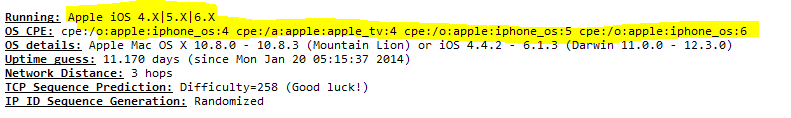
Once you identify the culprit IP address, you can either look in DHCP and find the hostname, or if the hostname does not show up, which is common with non domain joined hosts, like iPhones, Androids, and other mobile devices, you can use nmap to correctly identify what you are dealing with. The GUI nmap utility for Windows can be download here – called Zenmap. When running an intense scan on a specific IP address which is best for narrowing down on the identity, you will see a result set among other information which contains something similar to the following:
Notice how we see the OS type is Apple/IOS family. Now we know there most likely is someone with an iPhone or iPad streaming or doing some other bandwidth intensive activity. Now, we can move forward with blocking.
DHCP
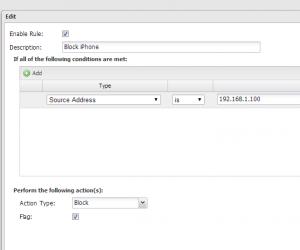
Since our free Untangle Firewall doesn’t have the option to block via MAC address, we are going to use the ability of DHCP to assign a reservation to the IP address which will essentially always hand the same IP to the MAC address specified. This way we can create a firewall rule in Untangle which targets the specific IP address which we can block against. If you are running a hardware firewall appliance or some other vendor firewall that can block based on MAC address, this will eliminate the DHCP step to the equation.
Untangle or other Firewall
Once we have the IP address or MAC address identifier sorted out to identify our offending host, we can now implement the rule to block their traffic. By using the Untangle Firewall, it is as simple as creating a rule to block all traffic coming from a certain source address. Something like the following would work:
Final Thoughts
Network admins are going to have to be ever more perceptive about which devices are connected on their networks. With the growing popularity of BYOD devices, employees are putting companies more and more at risk with unauthorized traffic. Granted having network policies in place to deal with these connections in general is certainly the right thing to do, the steps above will help those smaller to mid sized environments without the more costly infrastructure in place, to deal with those users and their devices.