Terrascan: Cloud Compliance and Security Scanner for IaC

Terrascan is a cool utility that provides a code analyzer that helps to make sure your infrastructure as code is secure and compliant.
Table of contents
What is Terrascan?
Terrascan, is an open-source project by Tenable (from the acquisition of Accurics). It is designed with the purpose of scanning infrastructure as code. It helps developers and devops engineers mitigate security issues before these are used in the infrastructure as code deployment.
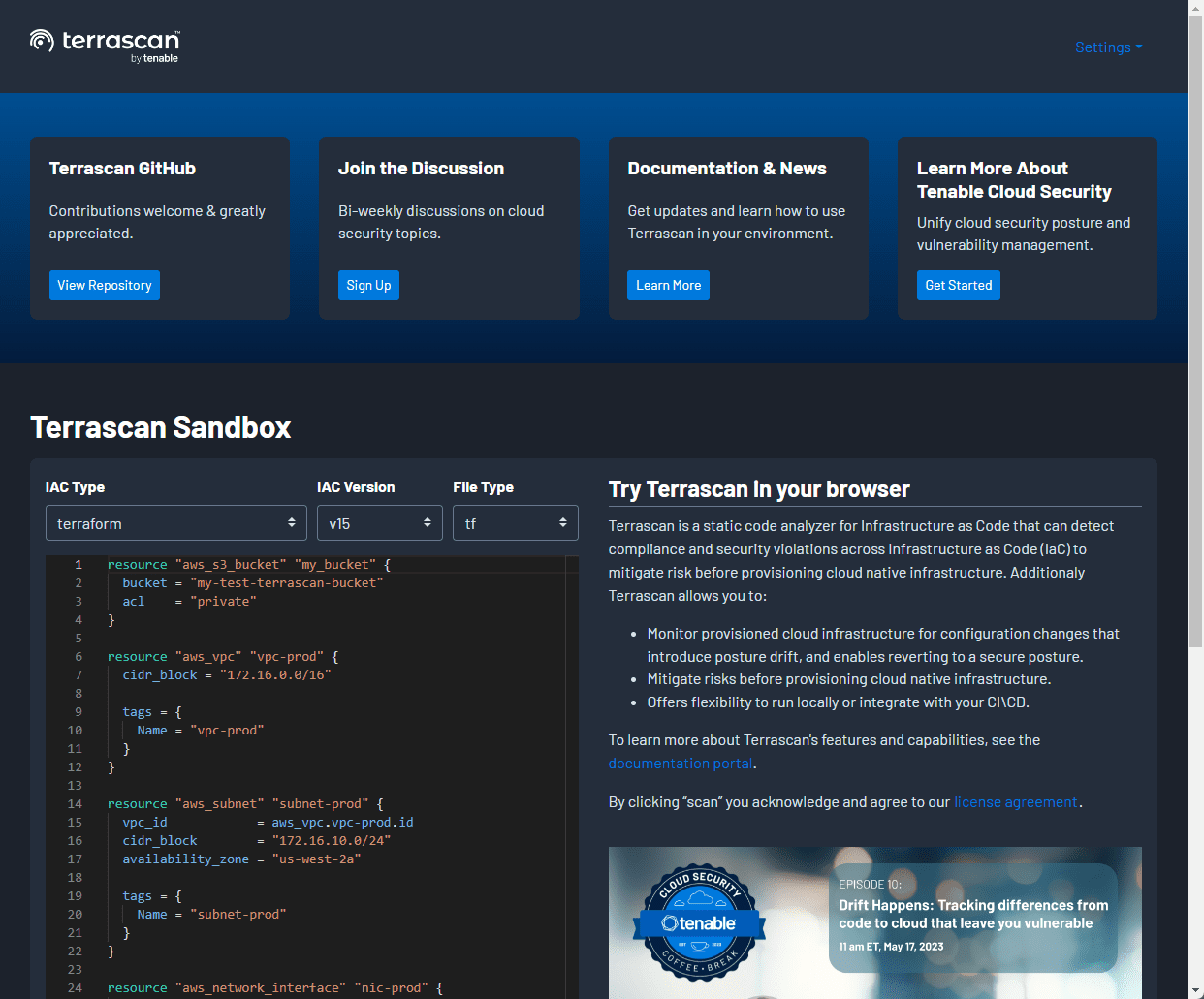
Cloud sandbox
You can try out the Terrascan cloud sandbox to get a feel for how the tool works and what the results look like. To visit the cloud sandbox, visit the URL here:
Terrascan’s Features and Capabilities
Terrascan has many features. It supports the IaC tools that most are using like Terraform, Kubernetes, Dockerfile, and others. With it, you can detect compliance and security violations across infrastructure as code and work on keeping your security posture for IaC secure.
You can also use the built-in policies.. These are designed to detect common security violations across infrastructure. That could include such things as insecure configurations and other things that aren’t desirable in your code.
You can also write and use custom policies. Custom policies allow users to enforce their specific compliance and security requirements. If the built-in policies don’t cover what you need them to, the custom policies will likely be what you want to look at.
In addition, it provides the following features:
Scans across your infrastructure as code (IaC) to identify misconfiguration
Keeps an eye on cloud infrastructure to spot configuration changes that may affect security
It detects potential security vulnerabilities and compliance and security violations
It allows mitigating risk before
code is used in production which is a great benefitYou can run terrascan locally or put it in as part of your CICD pipeline.
Installing Terrascan and Setting Up a Terrascan Sandbox
To get started, you first need to install it. The installation process is simple and can be done either locally or in a container environment. Once installed, you might consider setting up a Terrascan sandbox. This is a safe environment where you can test and understand Terrascan’s features and capabilities without affecting your actual cloud infrastructure.
To install as a native exe:
curl -L "$(curl -s https://api.github.com/repos/tenable/terrascan/releases/latest | grep -o -E "https://.+?_Darwin_x86_64.tar.gz")" > terrascan.tar.gz
$ tar -xf terrascan.tar.gz terrascan && rm terrascan.tar.gz
$ install terrascan /usr/local/bin && rm terrascan
$ terrascanTo install via brew:
brew install terrascanWe will also look at installing it with a Docker container below.
Leveraging Continuous Monitoring and Remediation
By adding this to your CI/CD process as a step in the pipeline, you can have your code scanned each time the pipeline runs in your development branch so that when developers or devops engineers check in code, they can have the code scanned and remediated from errors or security issues.
When it detects a security issue, it will alert and fail the pipeline if you have your pipeline setup for it to fail if the scan fails.
Leveraging Terrascan to Detect Compliance
Terrascan can detect compliance and security violations before your code is deployed is one of Terrascan’s standout features. With Terrascan, you can ensure that your cloud-native infrastructure is provisioned following industry and company-specific security and compliance best practices. This helps to mitigate risks before provisioning resources.
How Terrascan Helps to Mitigate Risk in Cloud Native Infrastructure
It allows you to mitigate risk before provisioning cloud-native infrastructure. It does this by:
Evaluating your IaC scripts and identifying potential security violations and compliance issues before the infrastructure is provisioned
It helps in avoiding ‘posture drift.’ Posture drift happens when configuration changes introduce vulnerabilities into an otherwise secure environment.
It continuously monitors provisioned cloud infrastructure, helping identify and address these changes promptly, allowing you to maintain a secure posture.
Revert and Mitigate risks using Terrascan
Terrascan allows you to revert configuration changes that introduce security violations, enabling you to restore your security posture quickly. This combination of proactive risk mitigation and reactive remediation capabilities makes Terrascan an essential tool in provisioning secure cloud-native infrastructure.
Running Terrascan as a Docker container
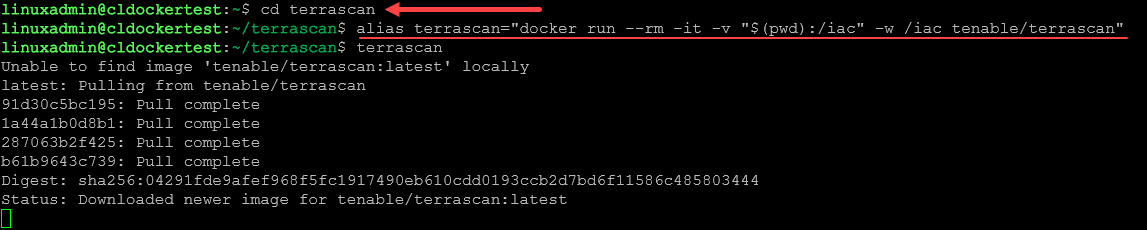
You can easily test out the solution by running it inside a Docker container by using the following to setup an alias to an interactive version of the terrascan container ran interactively.
As you can see below, we are setting up an alias to the docker run command, setting up a new container on the fly and running it interactively. The “$(pwd):/iac” directive tells terrascan to look at the current directory of focus from the shell command line for IaC code files like “.tf” files for Terraform.
$ alias terrascan="docker run --rm -it -v "$(pwd):/iac" -w /iac tenable/terrascan"I made a simple “terrascan” folder to run from, but you can run the command from anywhere as long as you have the alias configured. You just need to know where you are in the command line tree is where it will look for files.
On the first run of the terrascan command alias, we will see the Terrascan container pull down.
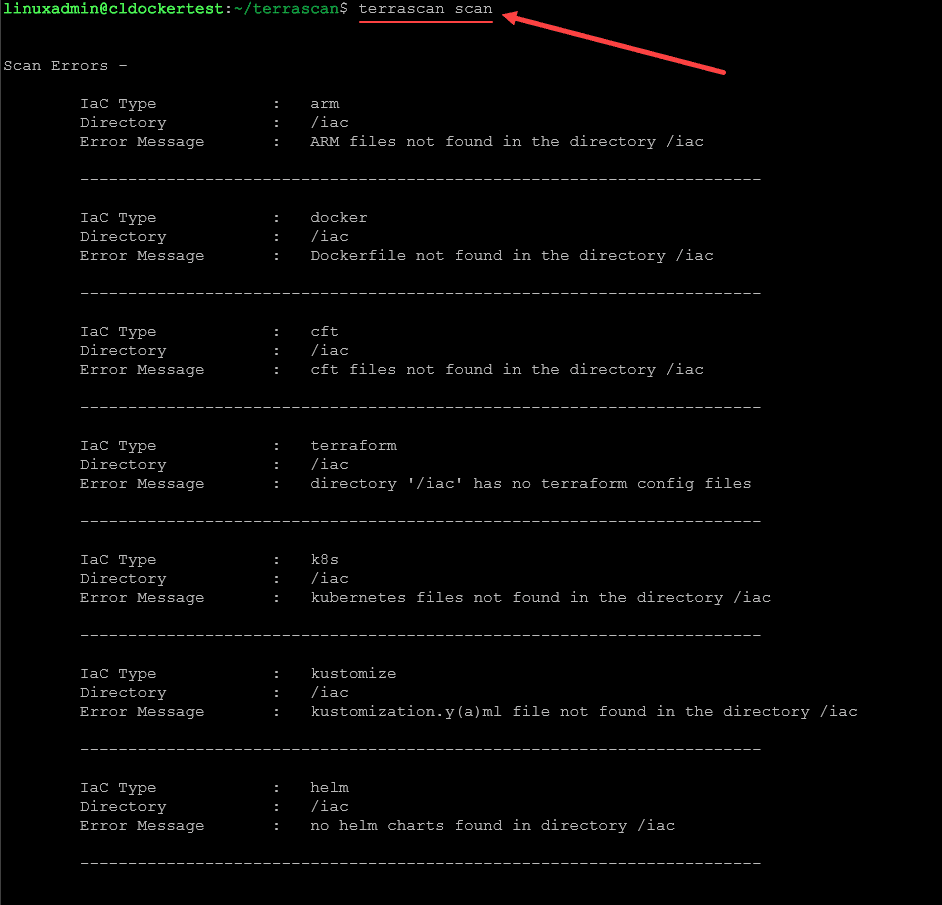
To run a scan, use the command:
terrascan scanWithout any files present, the command runs, but will note it didn’t find anything.
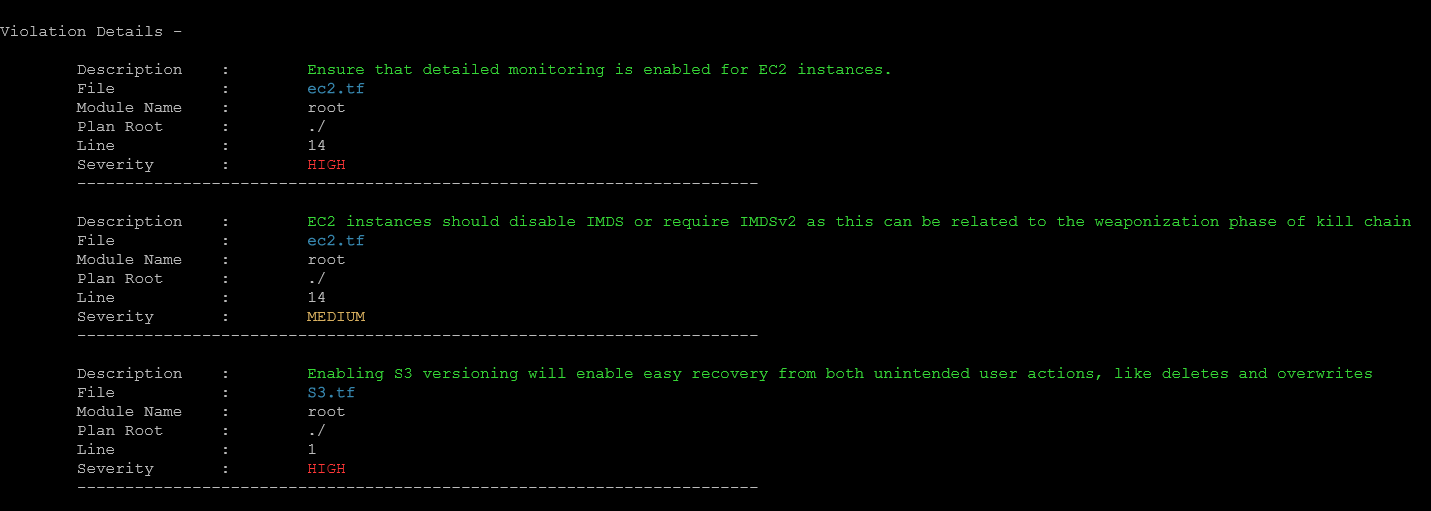
After adding some Terraform files to the directory where I am running terrascan scan command, we have files to work with and we can see it has findings that need to be addressed.
Wrapping up
Terrascan and other tools like it are a great way to make sure you don’t have things like code smells and security issues in your infrastructure as code environment and devops code. It is a great idea to have this setup as a step in your pipeline to automatically scan code as a step in the pipeline. That way you can have this process automated.