UTM
-
Security
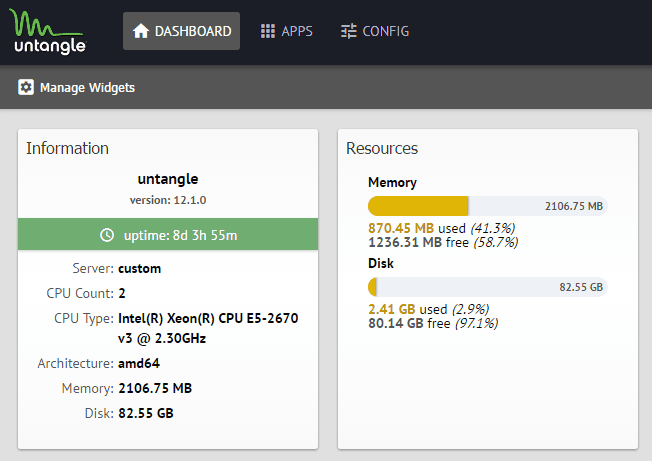
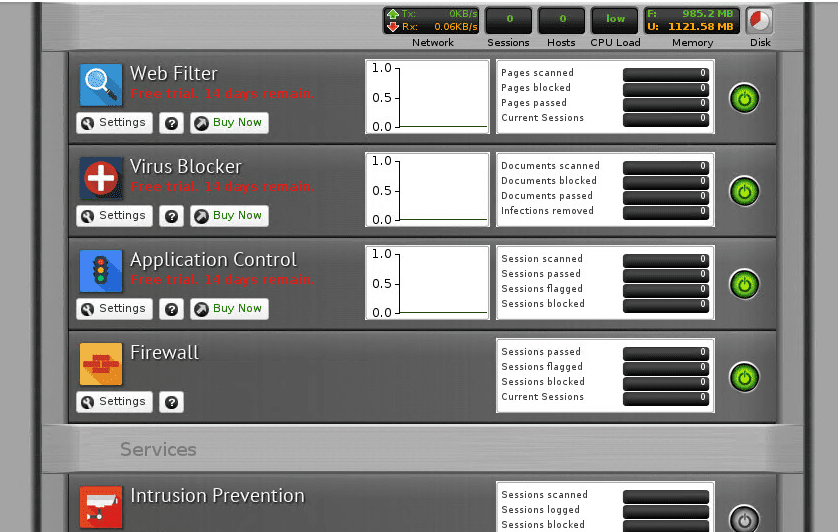
Untangle 12.1 Review and Impressions
So virtual firewalls and appliances are all the rage these days and there are many options to choose from. Historically, I have used a variety of different firewall/UTM platforms. I have always been a fan of the Untangle product as…
-
Networking
How to Configure Untangle site to site VPN
In working on a DR project utilizing two Untangle virtual appliances, I had the need to setup a site to site VPN connection between the Untangle firewalls. The OpenVPN documentation is fairly decent on the Untangle site, however, the information…
-
Security
Sophos XG UTM firewall virtual appliance install and configure
So the other day I received the announcement from Sophos they had released their “next generation” firewall appliance that would be providing the way forward for current 9.x users. Sophos did mention they are keeping both code branches however and…
-
Security
How to Increase Home Network Security
Let’s face it, these days, our digital security is under attack just about anywhere we are and access our data. However, we may not think about security when we are at home. After all, home is our private place, our…
-
Security
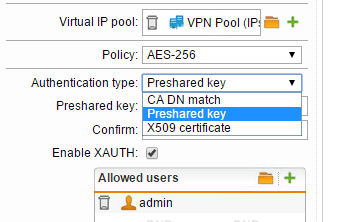
How to connect Shrew Soft VPN client to Sophos IPsec VPN
So far I have really been impressed with the features and power of the Sophos UTM appliance. I have ran it both in a software based applianced running on a whitebox atom powered machine and also in a VMware virtual…
-
Security
Sophos UTM vs Untangle
UTM or Unified Threat Management devices are becoming more and more popular as businesses and corporations have realized in the past couple of years that a simple tradition firewall of allows and denies is not adequate any longer. Hackers and…
-
Security
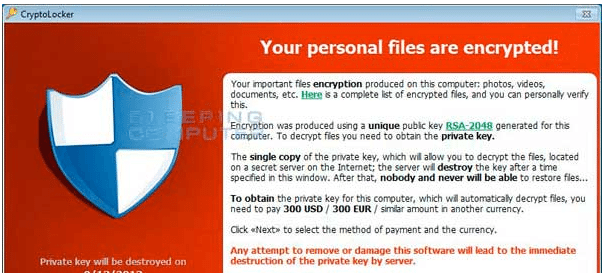
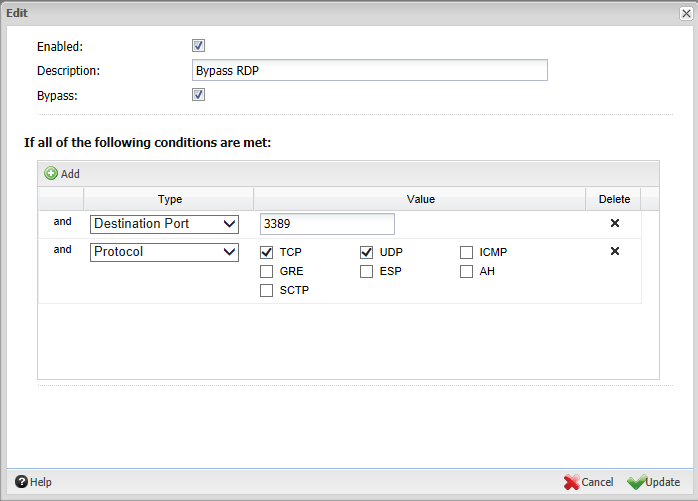
How to use Untangle to help prevent Cryptolocker infections
Cryptolocker is probably one of the most malicious and feared malware infections in quite some time. Most malware infections are a nuisance at most and a good sweep by a spyware utility such as malwarebytes will clean up the infection…
-
Security
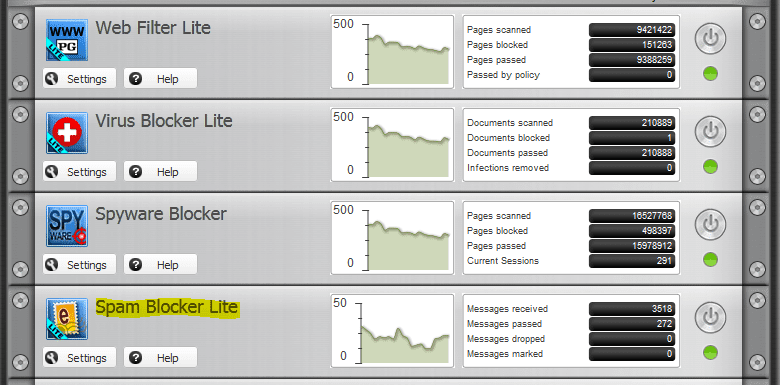
How to find an infected network host sending SPAM messages
A very challenging situation in a network environment where you may have several or even hundreds of network hosts is finding a specific host that is infected with malware. Many variants of malware may send SPAM messages from the infected…
-
Networking
How to configure and implement network QoS using Untangle
In today’s networks, connectivity is an essential part of successful communication in businesses an enterprise environments. Even though bandwidth is cheap these days, it is still a priority for network administrators to prioritize and limit mission critical traffic and non…
- 1
- 2