Active Directory Users and Computers: Ultimate Management an Security Guide

There are many tools to manage Active Directory. Let’s take a look at using Active Directory Users and Computers (ADUC) and see how you can use it to manage and secure your AD DS environment.
Table of contents
- What is Active Directory Users and Computers (ADUC)?
- Accessing Active Directory Users and Computers
- Managing User Accounts
- Managing Computer Accounts
- Organizing Active Directory Objects with Organizational Units (OUs)
- Delegating Permissions and Managing Group Policy
- Group Policy
- Working with Groups and Group Scopes
- Securing Active Directory Objects
- Enabling Advanced Features
- AD Administrative Center
- Lightweight Directory Services Tools (AD LDS)
- Understanding Active Directory Sites and Services
- Using Active Directory Tools for Role Administration
- Active Directory Module for Windows PowerShell
- Monitoring and Troubleshooting Active Directory Performance
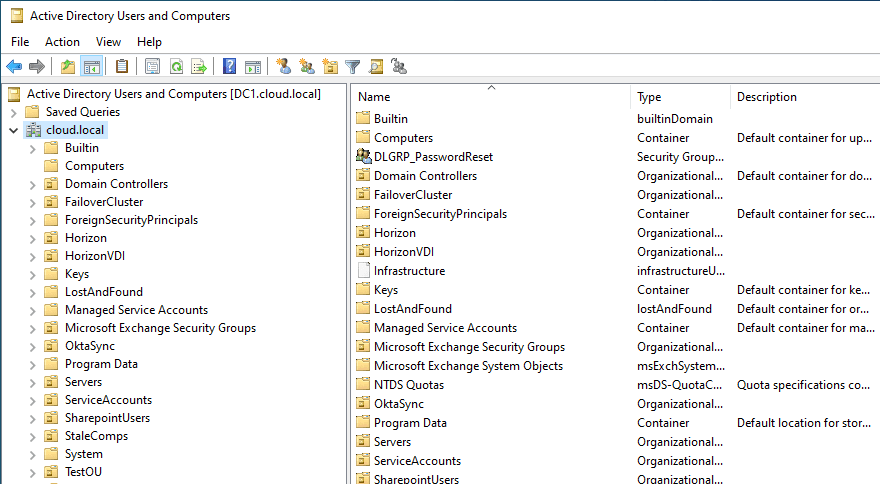
What is Active Directory Users and Computers (ADUC)?
Active Directory Users and Computers is the traditional de facto standard tool for admins that need and have tasks in managing your AD environment. It provides admins the GUI they want to use for managing AD and allows you to configure, create, delete, etc, user accounts, groups, change object properties, reset user accounts, and add member servers to your Windows domain.
Installing Active Directory Domain Services (AD DS) and Remote Server Administration Tools (RSAT)
Before using ADUC, we need to install the Active Directory Domain Services on a Windows Server. This means that we add the AD DS role through Server Manager. After you add the role, you configure your Active Directory domain, by creating the domain, DNS settings, etc.
Next we need to install the Remote Server Administrator Tools (RSAT) on your workstation to manage Active Directory objects. Note, this is installed on your DC as part of the installation of AD DS. RSAT when installed on your workstation, does install Active Directory Users and Computers, Active Directory Administrative Center, AD DS tools, and lightweight directory tools (AD LDS).
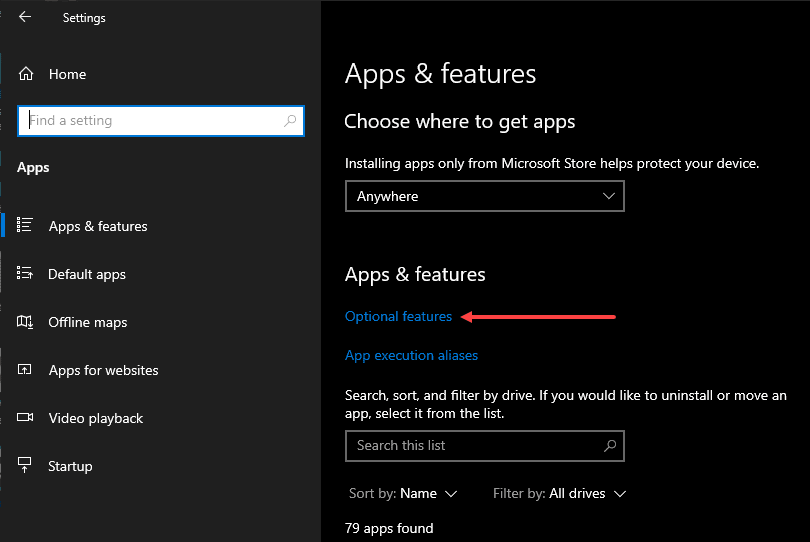
To install RSAT, press Windows key + I to navigate to settings. Under Apps & features, click Optional features to manage optional features in Windows 10 & 11.
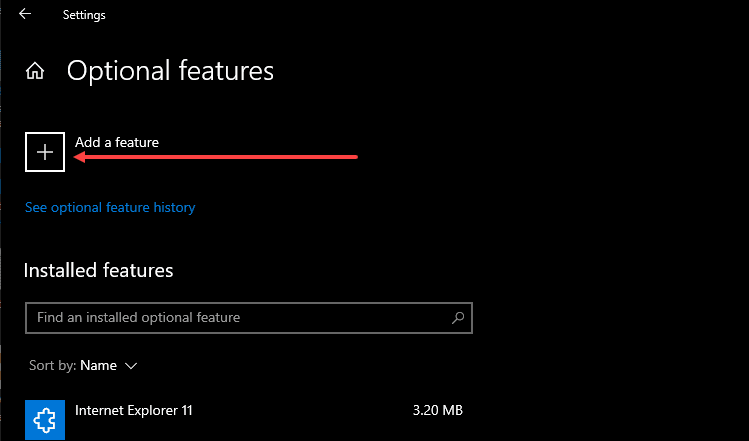
Click the + sign under Add a feature.
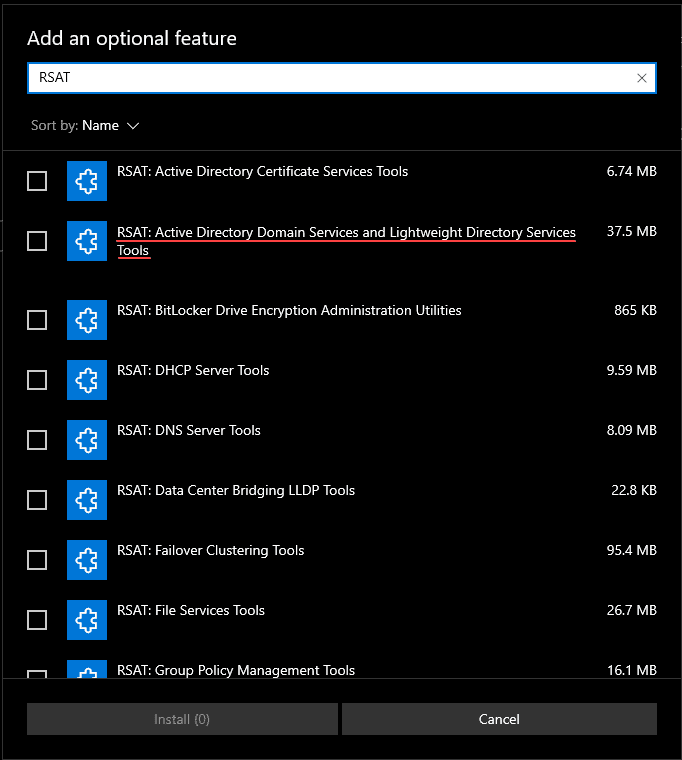
Type in “RSAT” in the search bar. You will see all the RSAT modules for installation on your end user workstation for use. For Active Directory Users and Computers, you will want to install RSAT: Active Directory Domain Services and Lightweight Directory Services Tools.
Accessing Active Directory Users and Computers
Click the Start Menu, and find “Windows Administrative Tools.” Then navigate and click on “Active Directory Users and Computers” and click to open the console. Also, you can launch the tool ADUC by using the command dsa.msc from a run, command, or PowerShell prompt, which is how I like to launch it.
Managing User Accounts
User accounts when it comes to Active Directory AD DS are the objects that allows the users to access resources. To create a new user account, right-click the OU where you want the account to reside, and select “New” and then followed by “User.”
You will just want to follow the wizard and input the information, such as the what the user’s full name and user logon name need to be, and click “Next.” Set a password and configure the password settings, then click “Finish” to create the account.
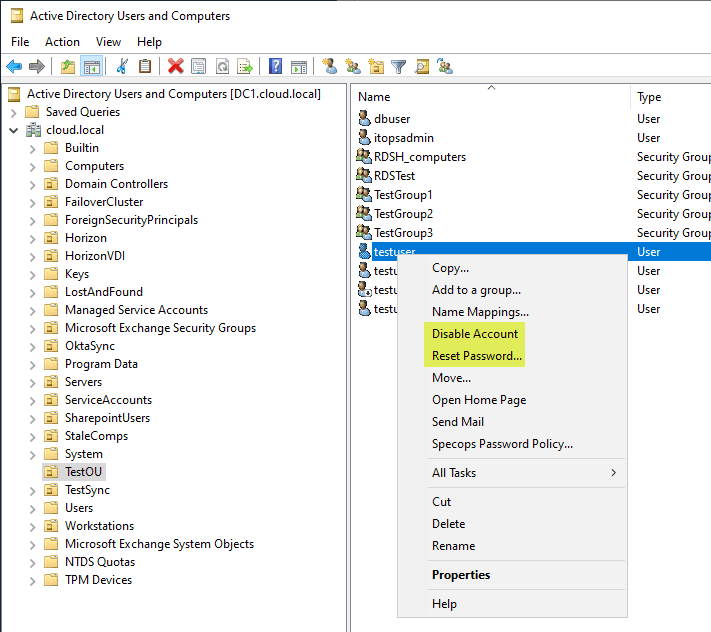
Disabling involves right-clicking the user object, and select “Disable Account.” To reset a user account password, right-click the account and choose “Reset Password.”
Managing Computer Accounts
Computers create a computer account in the domain when they are joined when you join them with the AD join process. These accounts manage the computers within the domain. To create a new computer account in the domain environment, right-click the OU where the computer should be, select “New,” and then choose “Computer.” Enter the computer’s name and click “OK.”
To reset a computer account password which is sometimes needed, right-click the computer object and select “Reset Account.” This operation generates a new password for the computer account, which must be synchronized with the computer’s local password.
This is a process that can be needed but you almost never have to do manually. However, during disaster recovery and other processes, resetting the computer account may be necessary.
Organizing Active Directory Objects with Organizational Units (OUs)
Organizational Units are container objects. They are used by admins to manage and organize Active Directory objects in Active Directory domains. OUs can contain users, computers, groups, and even other OUs. You can create a hierarchy of OUs, and this helps streamline the process of trying to managing your Active Directory domain.
Delegating Permissions and Managing Group Policy
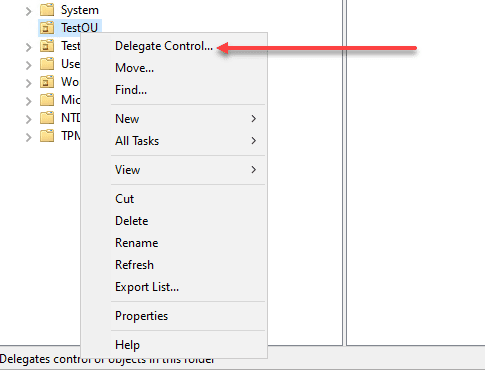
Delegating permissions may be something you need to do. For example giving rights to other administrators or users, right-click an OU or another AD object and select “Delegate Control.” Follow the wizard to assign permissions to the user who needs to be able to do a certain function or task, like reset passwords.
Group Policy
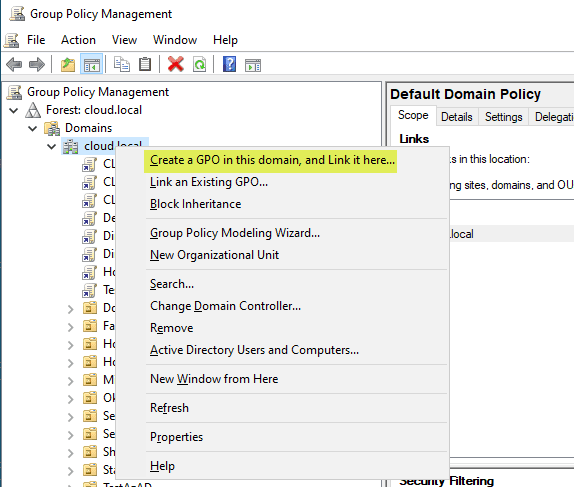
Group Policy is an important component of Active Directory as it allows admins to easily create structured policies for actions and features in the domain. To create a new Group Policy object (GPO), right-click an OU, select “Create a GPO in this domain, and Link it here,” and give the GPO a name.
You can then configure the settings within the Group Policy Management Console.
Working with Groups and Group Scopes
There are three group scopes:
- domain local – Domain local groups can contain users and groups from any domain within the forest
- global – global groups can only contain users and groups from their own domain
- universal – Universal groups can contain users and groups from any domain within the forest and are available for use in other domains
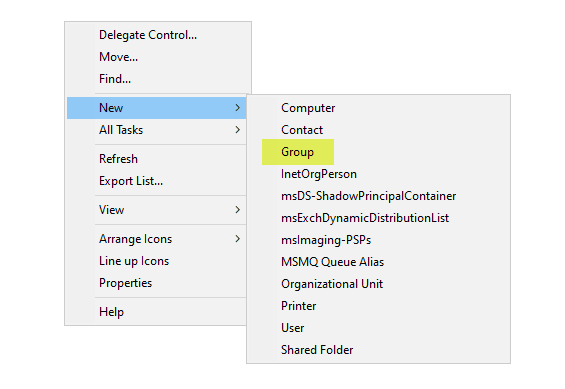
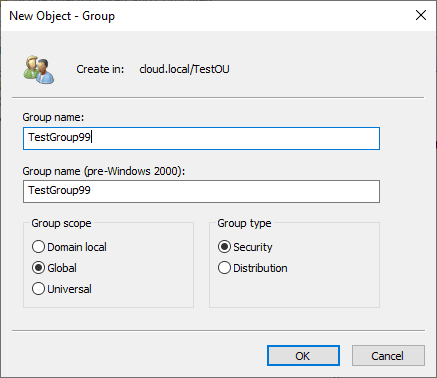
To create a new group, right-click the OU where the group should reside, select “New,” and then choose “Group.” Enter the group’s name, select the group scope, and click “OK.”
To add users to the group, double-click the group object, navigate to the “Members” tab, and click “Add.”
Securing Active Directory Objects
Securing and protecting your Active Directory objects from compromise or security issues is important for keeping things secure. Ransomware gangs often use compromised AD environments to infiltrate the environment.
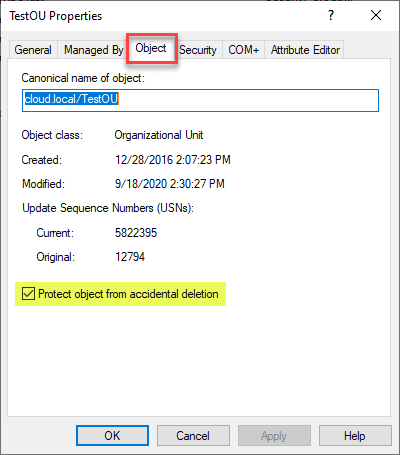
To secure an AD object, right-click the object and select “Properties.” Navigate to the “Object” tab and check the box for “Protect object from accidental deletion.” This option prevents the object from being deleted without proper authorization.
Enabling Advanced Features
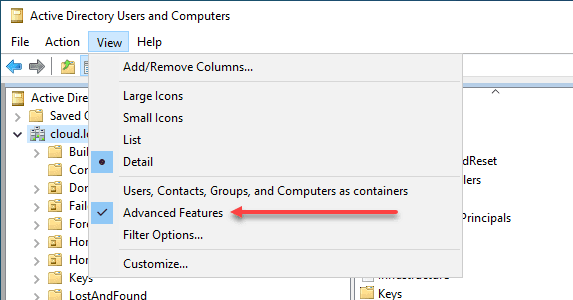
To access advanced features within the ADUC console, click “View” in the menu bar. Then you can select “Advanced Features.” This provides you as an admin with access to additional properties and settings for AD objects.
AD Administrative Center
Active Directory Administrative Center is another good management tool that you will want to know about for your AD env. It provides a more modern and intuitive interface than ADUC. I am surprised this didn’t take off more than it has with managing AD, but it is something to know about if you want to use it for management.
It is designed to simplify managing AD objects. It also supports new AD features that you can manage and configure, such as the Active Directory Recycle Bin and Fine-Grained Password Policies. To access the Administrative Center, navigate to “Windows Administrative Tools” in the Start Menu and click on “Active Directory Administrative Center.”
Lightweight Directory Services Tools (AD LDS)
Active Directory Lightweight Directory Services (AD LDS) is a directory service that provides a simple and scalable solution for directories when needed with certain solutions or in certain use case scenarios AD LDS tools can be used with AD DS tools to manage directory-enabled applications like VMware Horizon. To install AD LDS tools, open the Control Panel, click on “Turn Windows features on or off,” and check the box for “Active Directory Lightweight Directory Services Tools.”
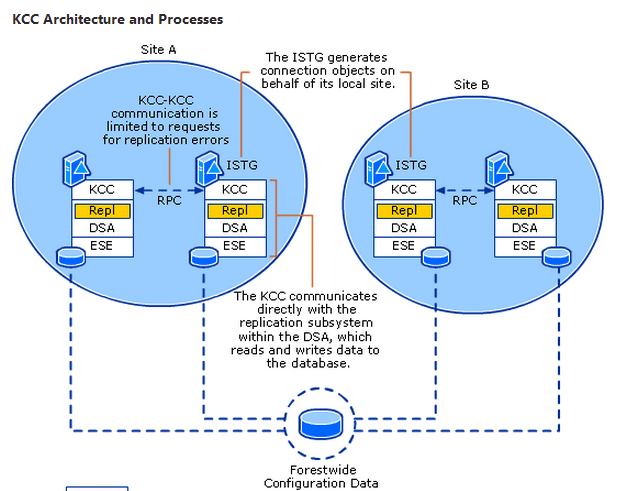
Understanding Active Directory Sites and Services
An AD site represents a physical location with a network that is used for one of your AD sites. Managing sites and domain controllers is part of what admins need to do as day to day operations, including configuring site links, subnets, and replication schedules.
Using Active Directory Tools for Role Administration
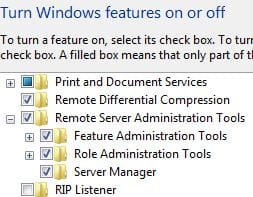
These tools include DNS Server Tools, DHCP Server Tools, and more. To install Role Administration Tools, navigate to the Control Panel, click on “Turn Windows features on or off,” and expand “Role Administration Tools” to select installing the features you need to install for management. These are great to have on your management workstation or PAW.
Active Directory Module for Windows PowerShell
The Active Directory module for Windows PowerShell offers cmdlets, administrators can automate repetitive tasks in AD and perform bulk operations on AD objects. To install the module, open Server Manager, click “Add Roles and Features,” and select the “Active Directory module for Windows PowerShell” feature.
Active Directory PowerShell commands
Import the Active Directory module:
Import-Module ActiveDirectoryCreate a new user account:
New-ADUser -Name "John Doe" -GivenName "John" -Surname "Doe" -SamAccountName "jdoe" -UserPrincipalName "[email protected]" -Path "OU=Users,DC=example,DC=com" -AccountPassword (ConvertTo-SecureString "P@ssw0rd!" -AsPlainText -Force) -Enabled $trueCreate a new Organizational Unit (OU):
New-ADOrganizationalUnit -Name "Sales" -Path "DC=example,DC=com"Add a user to a group:
Add-ADGroupMember -Identity "Group Name" -Members "User Name"Disable a user account:
Disable-ADAccount -Identity "User Name"Get a list of all users in an OU:
Get-ADUser -Filter * -SearchBase "OU=Users,DC=example,DC=com"Move a user account to a different OU:
Move-ADObject -Identity "CN=User Name,OU=SourceOU,DC=example,DC=com" -TargetPath "OU=DestinationOU,DC=example,DC=com"Reset a user’s password:
Set-ADAccountPassword -Identity "User Name" -NewPassword (ConvertTo-SecureString "NewP@ssw0rd!" -AsPlainText -Force) -ResetFind all users with a specific attribute (e.g., title):
Get-ADUser -Filter 'Title -eq "Manager"' -Properties TitleModify an attribute for a user (e.g., phone number):
Set-ADUser -Identity "User Name" -OfficePhone "+1 (555) 123-4567"These examples demonstrate various tasks that administrators can perform using the Active Directory module for Windows PowerShell, allowing for efficient management of AD objects.
Monitoring and Troubleshooting Active Directory Performance
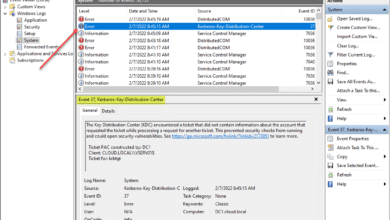
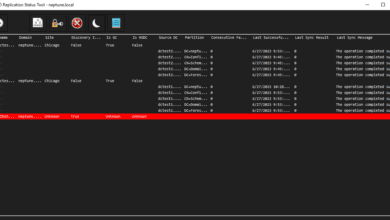
Monitoring for AD include tools like Performance Monitor, Event Viewer, and Repadmin. These help administrators keep up with the health of their AD environment and identify issues with the AD environment, replication, etc.
Wrapping up
Microsoft Active Directory users and computers is the tool we have used for years now to manage AD. It provides all of the features and tools that admins need to keep AD managed and configured. There are other things you can use like PowerShell and other role services to help with managing AD like DNS management DHCP, etc.